This MetaDefender Endpoint release includes various features and enhancements across Windows (v7.6.2510) and Linux (v15.6.2510) platforms, in addition to OPSWAT Media Validation Agent (OMVA) (v2.0.18) and MetaDefender Endpoint Validation (v3.1.2510). The new additions are designed to enhance endpoint security and compliance, optimize performance, and make it easier for MetaDefender Endpoint users to stay protected against peripheral and removable media threats.
What’s New in MetaDefender Endpoint
Redesigned Malware Scan Screen
We have redesigned the Malware Scan screen for a more intuitive and informative user experience. The updated interface now features clickable tabs that display real-time information on file status, malware detection, vulnerabilities, data loss prevention, and country of origin details for easy review. These new tabs make it easier than ever to navigate and monitor security posture with quicker access to detailed insights and decision making.
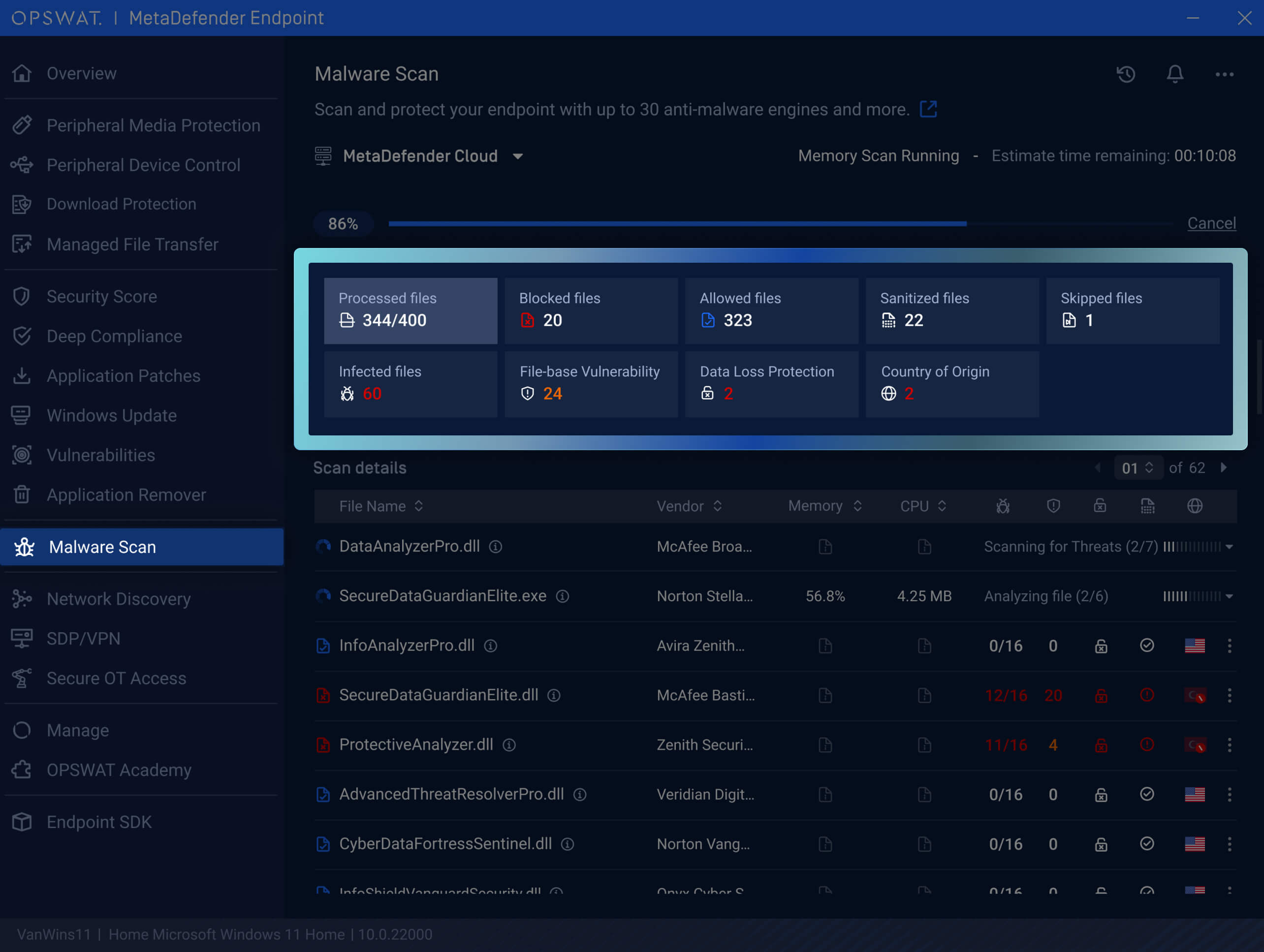
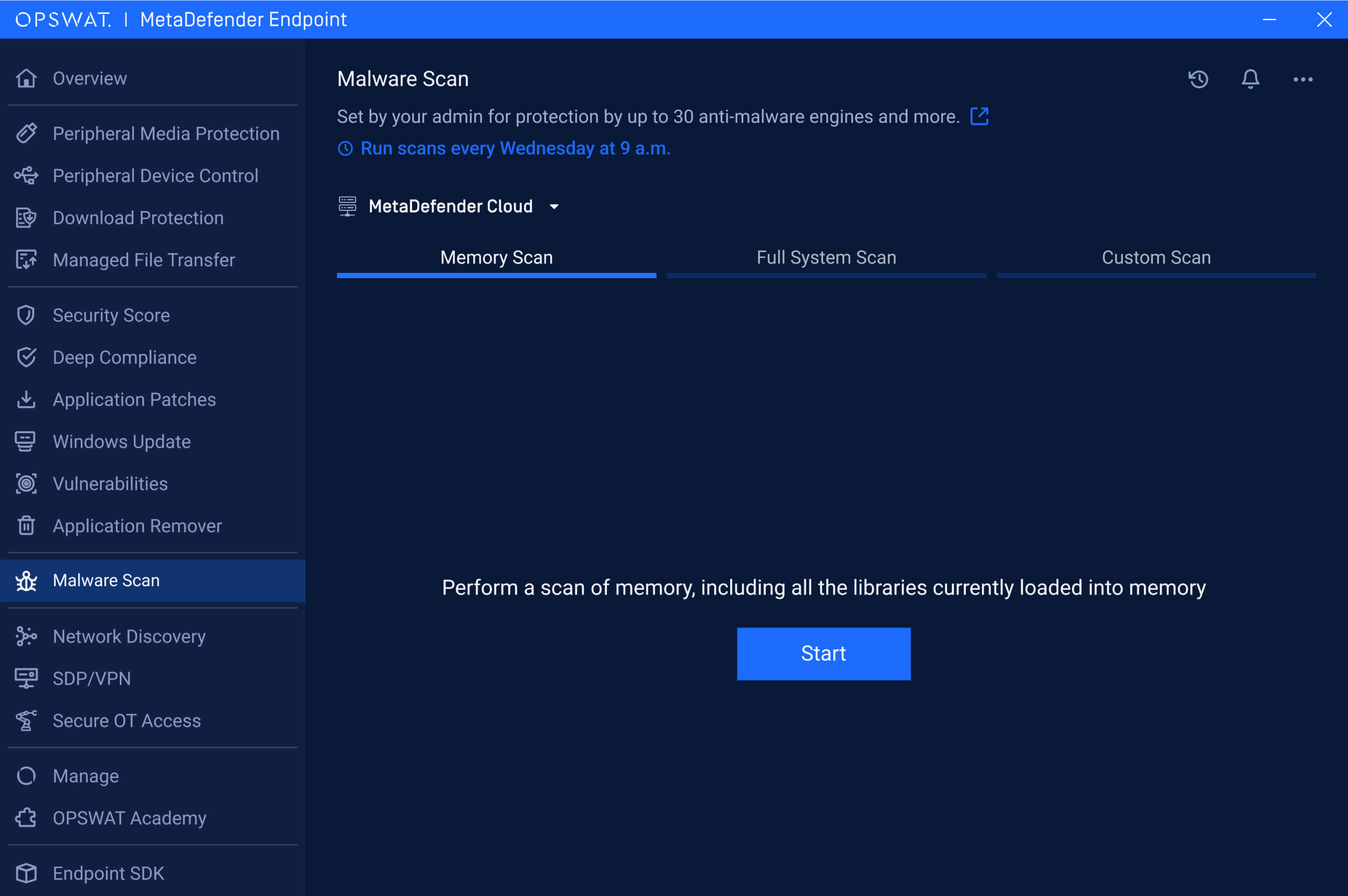
This new update also includes a new notification header within the Malware Scan screen to inform users when their device is part of a scheduled scan routine configured by administrators. This update provides clear, direct, and non-intrusive notification, increasing transparency, and ensuring that users are aware of routine security activities taking place on their devices.
Enhanced Protection with Admin-Approved Path for Data Retrieval
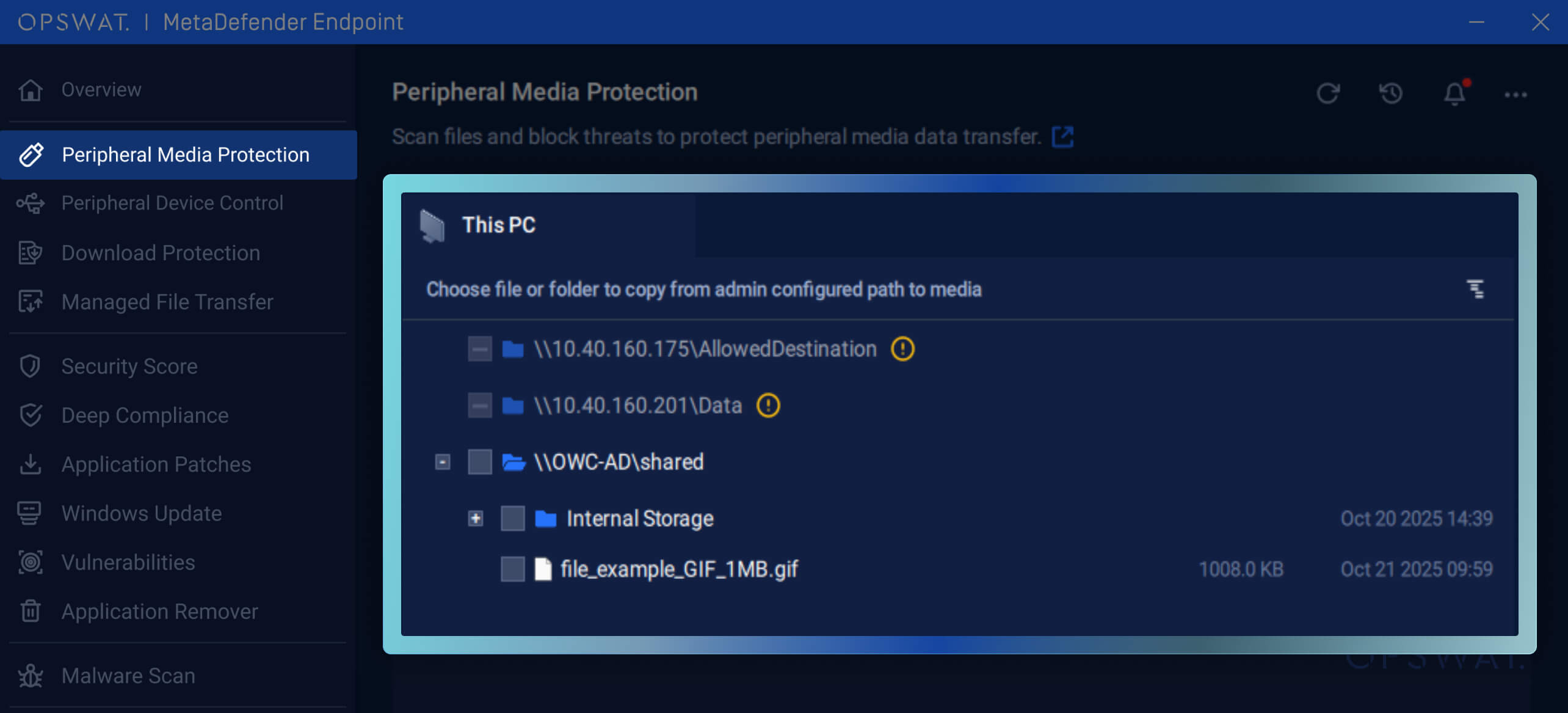
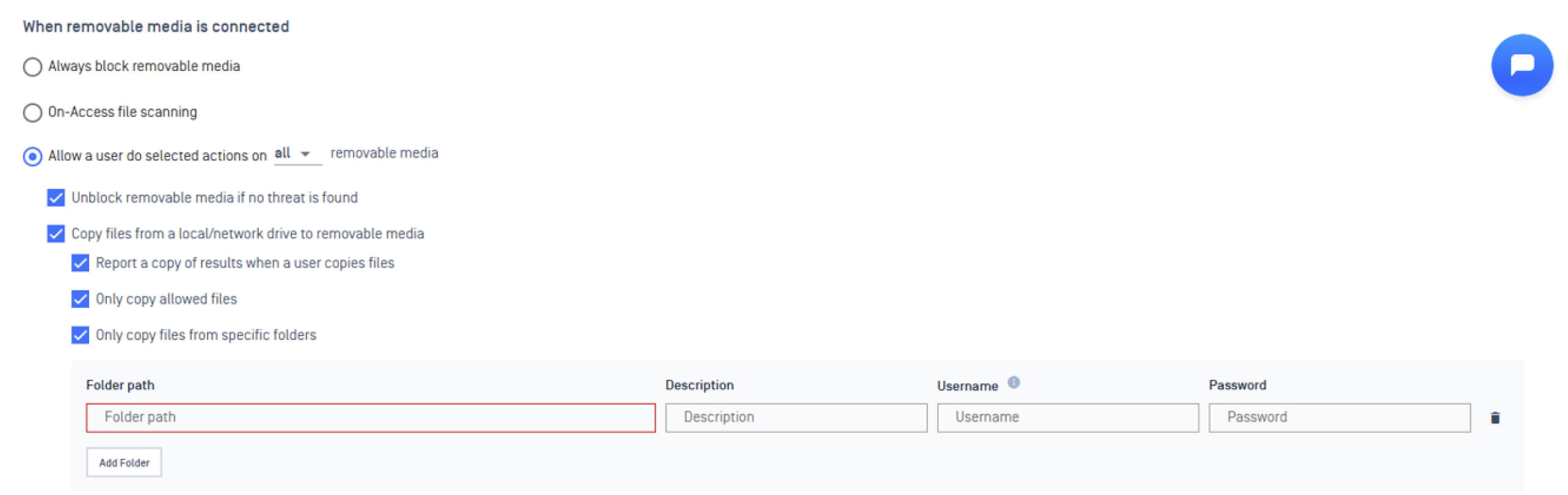
To strengthen peripheral and removable media protection and reduce the risk of unauthorized data exposure, we introduce controlled file access for users copying files to external drives to help organizations enforce data handling policies and strengthen control over the use of removable media.
This enhancement enables users to only select files from predefined paths configured by administrators to copy to removable media drives. Because browsing and copying files outside of those specified directories is restricted, this feature significantly reduces the risk of accidental or unauthorized data transfer.
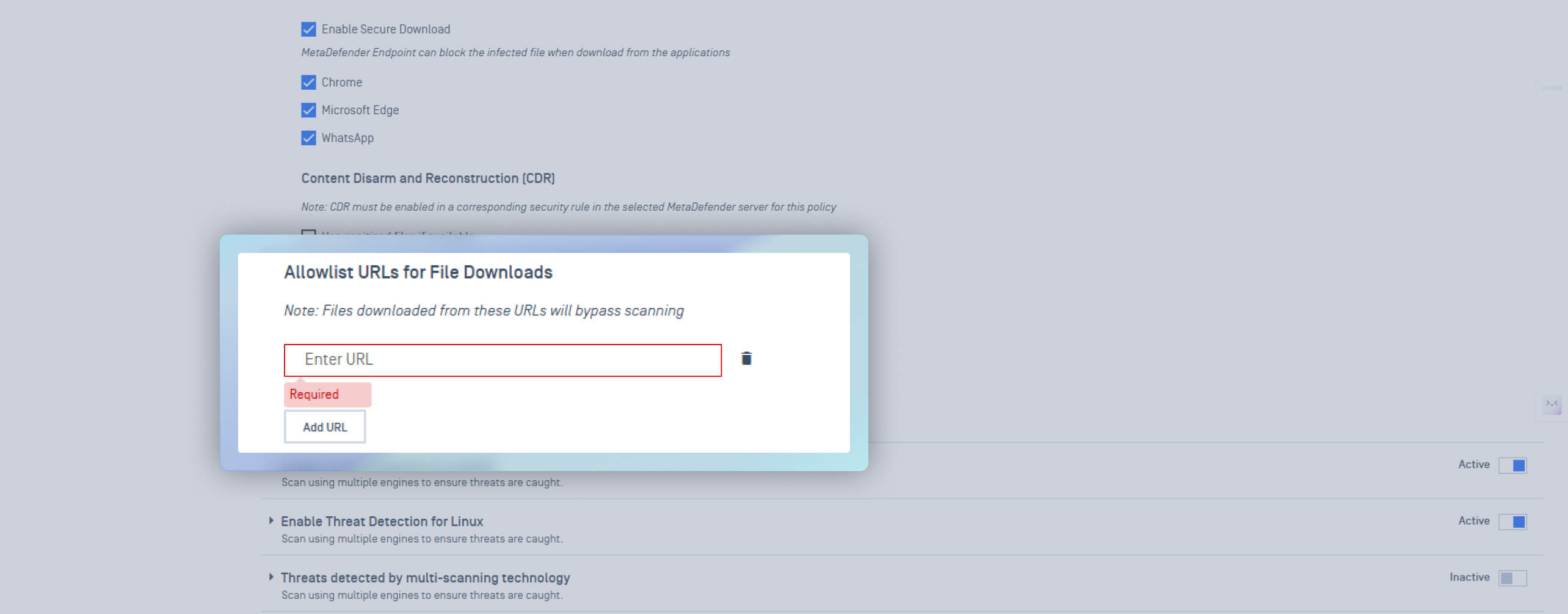
Strengthened Download Protection with Allowlisting Download URL
To provide greater flexibility while maintaining security, support for URL allowlisting has been added to the Download Protection feature. This enables administrators to specify trusted URLs or domains from which users can download internal or approved resources.
Files downloaded from the allowlisted sources are automatically trusted and exempted from additional scanning. This new addition helps streamline workflows without compromising security, enabling organizations to facilitate secure access to internal resources while enforcing strict controls over internet downloads.
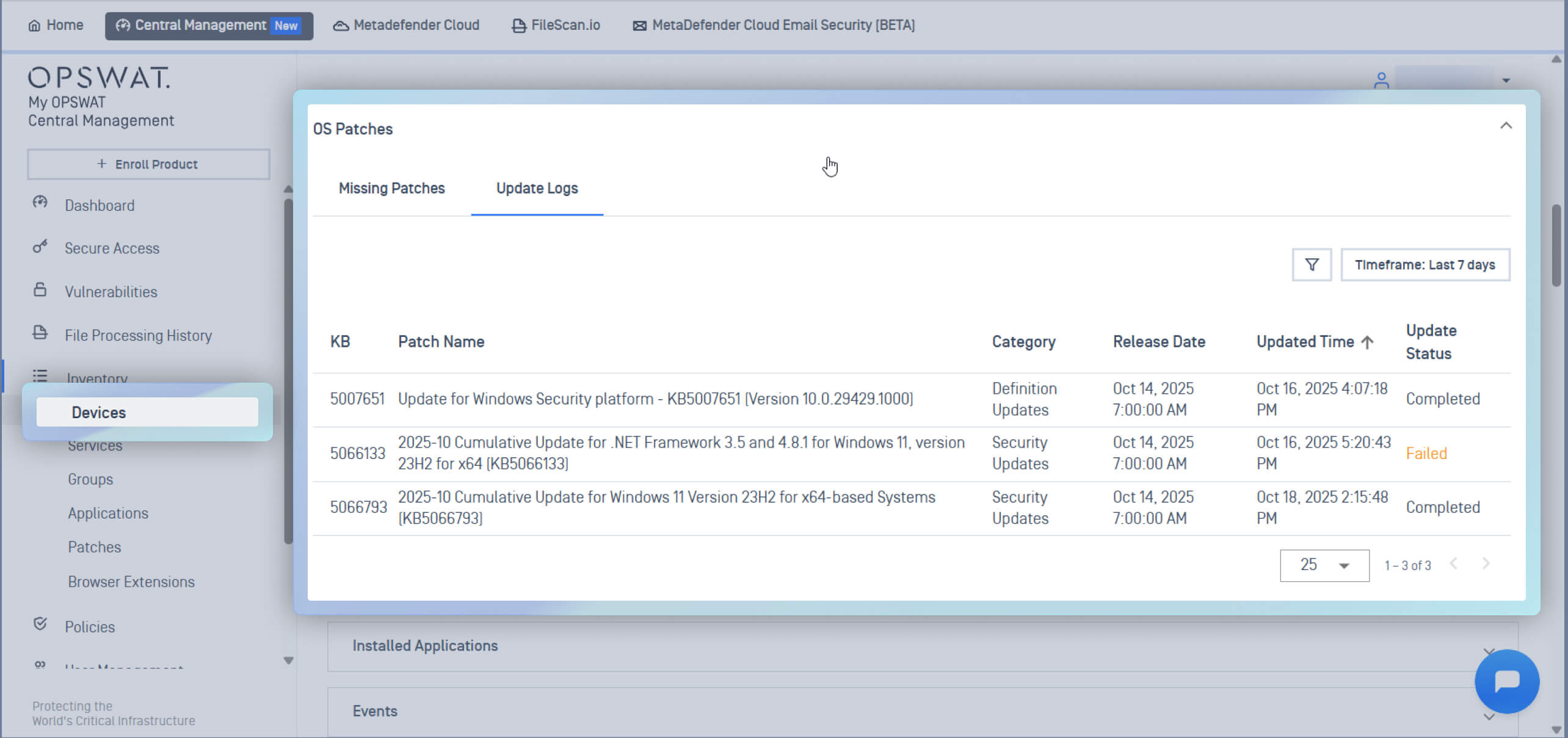
Improved Visibility with Installed Patch History
The newly implemented Installed Patch History feature gives administrators clear visibility into all installed patches on each endpoint. This critical feature supports compliance and risk management efforts with quick verification, historical auditing, and ensuring that no gaps in patch coverage are overlooked.
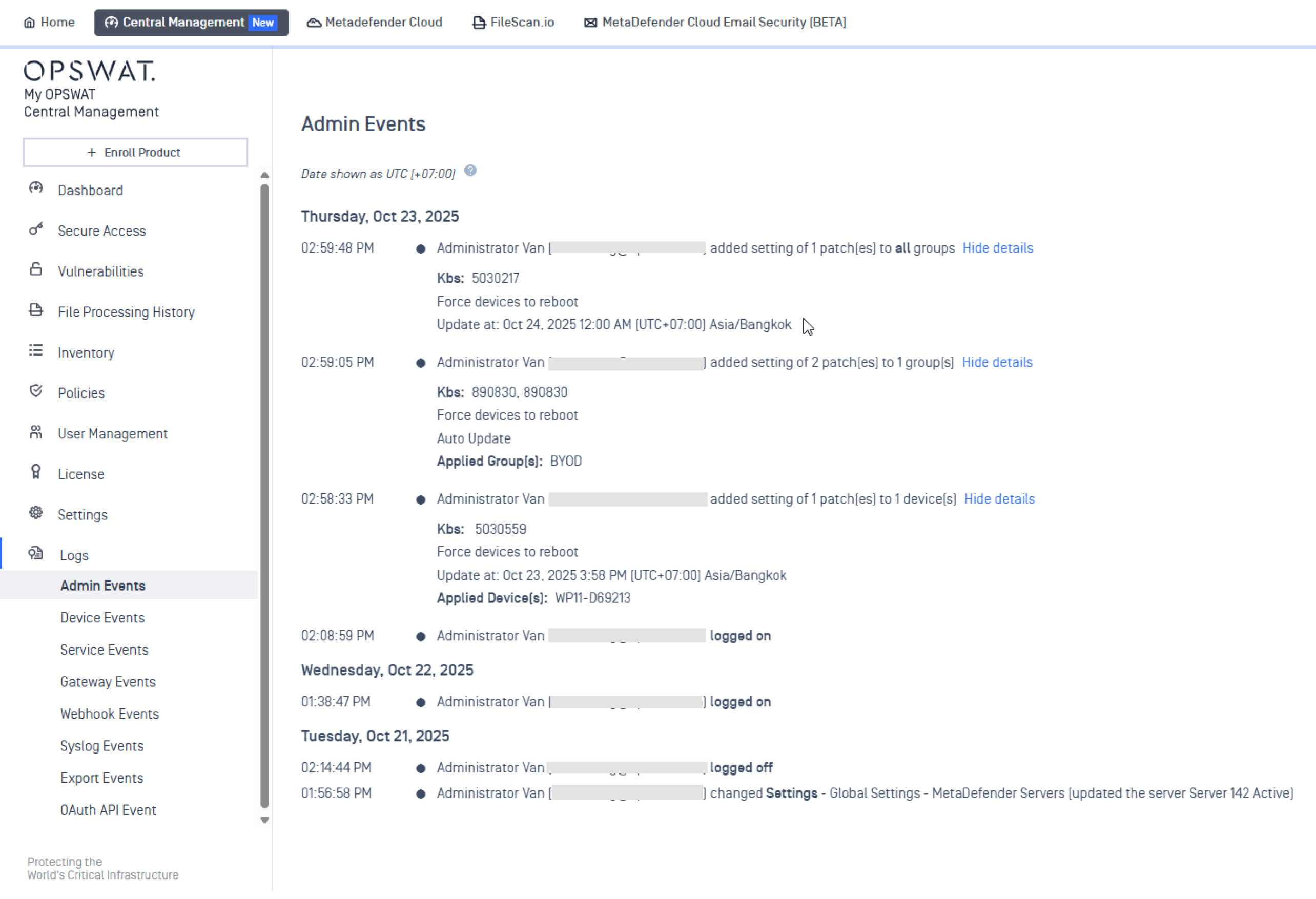
Enhanced Patch Management with Admin Audit
This release introduces the Patch Management Admin Audit feature, providing administrators with centralized recording of all patch actions. All patch information is now logged and easily reviewable, including who uploaded a patch package, the status of the uploads, and which patch was delivered to whom.
This level of transparency helps meet regulatory requirements, and enables security teams to identify anomalies and ensure patching policies are followed consistently.
Patch Integrity Assurance and Verification During Uploads
In this release, we introduce a new mechanism that enables administrators to upload patch packages directly to the management console via My OPSWAT™ Central Management. During the upload process, administrators will receive immediate validation confirming whether the package is valid and untampered to help prevent accidental installation of corrupted or malicious updates.
Streamlined Patch Deployment for All Missing Patches
MetaDefender Endpoint administrators can now deploy all missing patches to a device at once, helping reduce manual intervention and saving time while ensuring critical endpoints are fully protected. This feature also enables faster response to vulnerabilities and supports maintaining a stronger security posture across the organization.
Customizable Sanitized File Naming
Administrators now can customize the naming convention of sanitized files, offering greater flexibility in managing sanitized content. With this feature, organizations can define file name formats that align with their internal policies and operational requirements for improved traceability and consistency.
Device-Based Reboot Control
This release also introduces a new device reboot control feature for greater flexibility and operational precision. It enables administrators to remotely designate a specific device for rebooting to help maintain system compliance, reduce downtime, and effectively enforce security protocols.
This capability is particularly valuable during incident response and policy enforcement, ensuring that updates or critical configuration changes take effect immediately without relying on user action.
Background Auto-Update for Applications and OS
MetaDefender Endpoint now supports automatic background updates for applications and operating systems, regardless of the user interface or tray icon visibility. Administrators can choose to show or hide the MetaDefender Endpoint interface, including selecting which tabs are visible to users. However, even when the user interface is hidden, application patching and OS updates continue to run seamlessly in the background, ensuring systems remain up to date and secure without requiring user interaction or visibility into the process.
Silent-Mode Patching: Ability to Hide all Popups and Notifications
The new release gives administrators extra control over the user interface by enabling them to hide all popups, alerts, and notifications from MetaDefender Endpoint based on configurable policies. This is ideal for high-security, controlled environments where minimal user interaction, distraction-free workflows, and stealth enforcement of security policies are critical.
When toggled off, no messages or prompts will be displayed to end users, including cases when the system forces reboot or closes applications. These actions will still be carried out as usual, but entirely in the background.
What’s New in MetaDefender Endpoint Validation
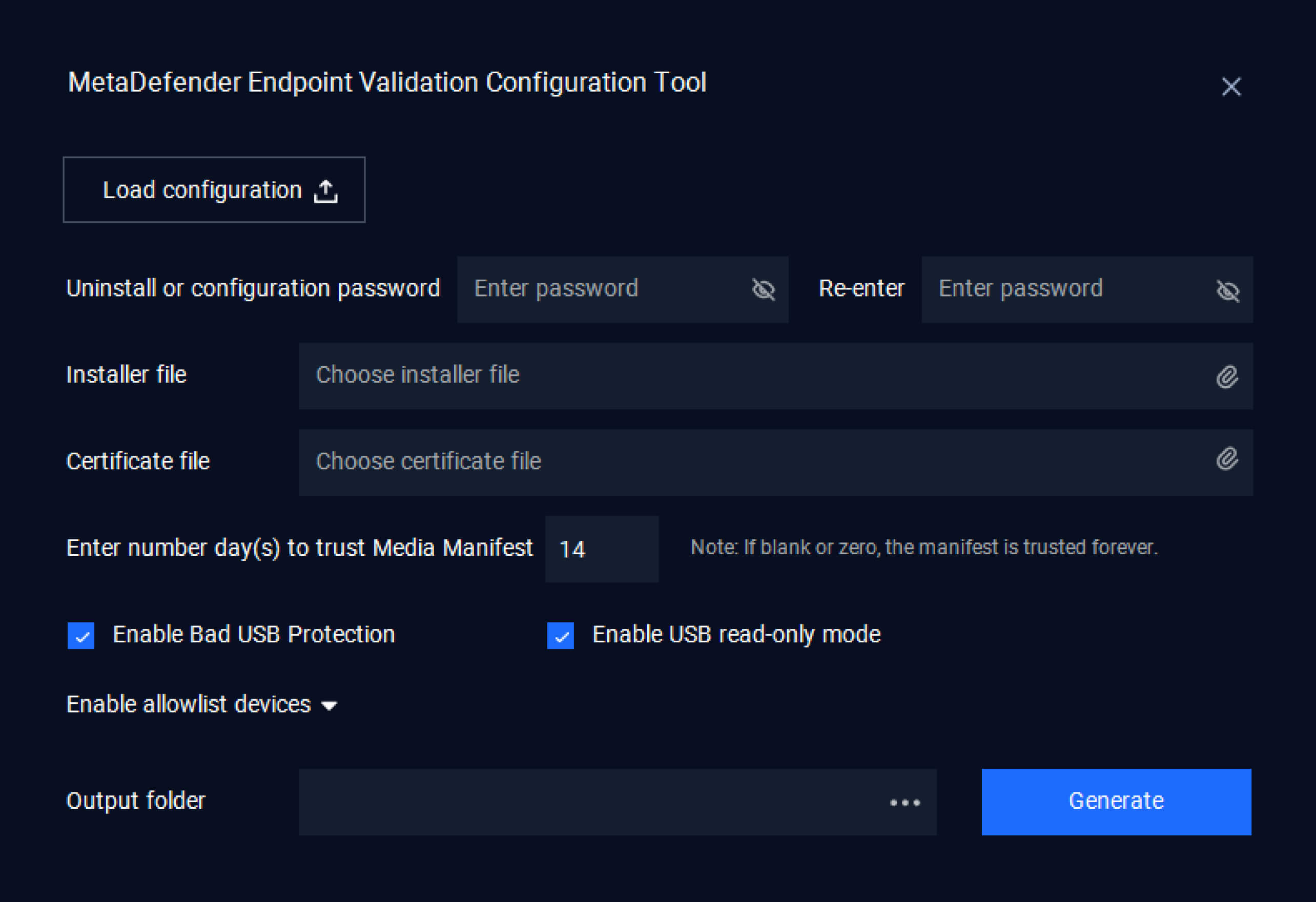
Read-Only Mode for Enhanced Protection
We’re pleased to introduce read-only mode in MetaDefender Endpoint Validation, a new capability designed to prevent data from being written to USB storage devices. When this mode is enabled, users can access and read files after successful validation, but cannot copy, modify, or write data to the removable storage media.
This mode helps significantly reduce the risk of data leakage, preserves all existing validation and blocking capability and functionality and can be easily enabled or disabled via the MetaDefender Endpoint Validation configuration tool.
Next-Level Peripheral and Removable Media Protection
Discover why worldwide organizations, institutions, and entities trust MetaDefender Endpoint to protect critical endpoints. Talk to an expert today to learn more.

