Despite the headlines, advisories, and the billions of dollars poured into cybersecurity, one glaring issue continues to fester at the heart of OT & CPS (cyber-physical systems): insecure industrial protocols.
The operational backbone of our energy grids, water treatment plants, oil and gas, and manufacturing facilities is still built on communication standards like Modbus, DNP3, OPC DA, PROFINET, etc.
These protocols were engineered decades ago, long before cyberthreats were part of the conversation, and were designed for performance, not protection. They assume complete security and system uptime, require no authentication, transmit in plaintext, and they are still running mission-critical systems around the world.
This is not a hypothetical risk. It’s a systemic one.
Trust by Default: A Weaponized Design Flaw
Legacy industrial protocols were born in a different era—one where the logic of physical isolation (air gaps) served as the dominant security model. Cybersecurity was neither a requirement nor a design objective. As a result, these protocols have no built-in authentication, authorization, or encryption mechanisms.
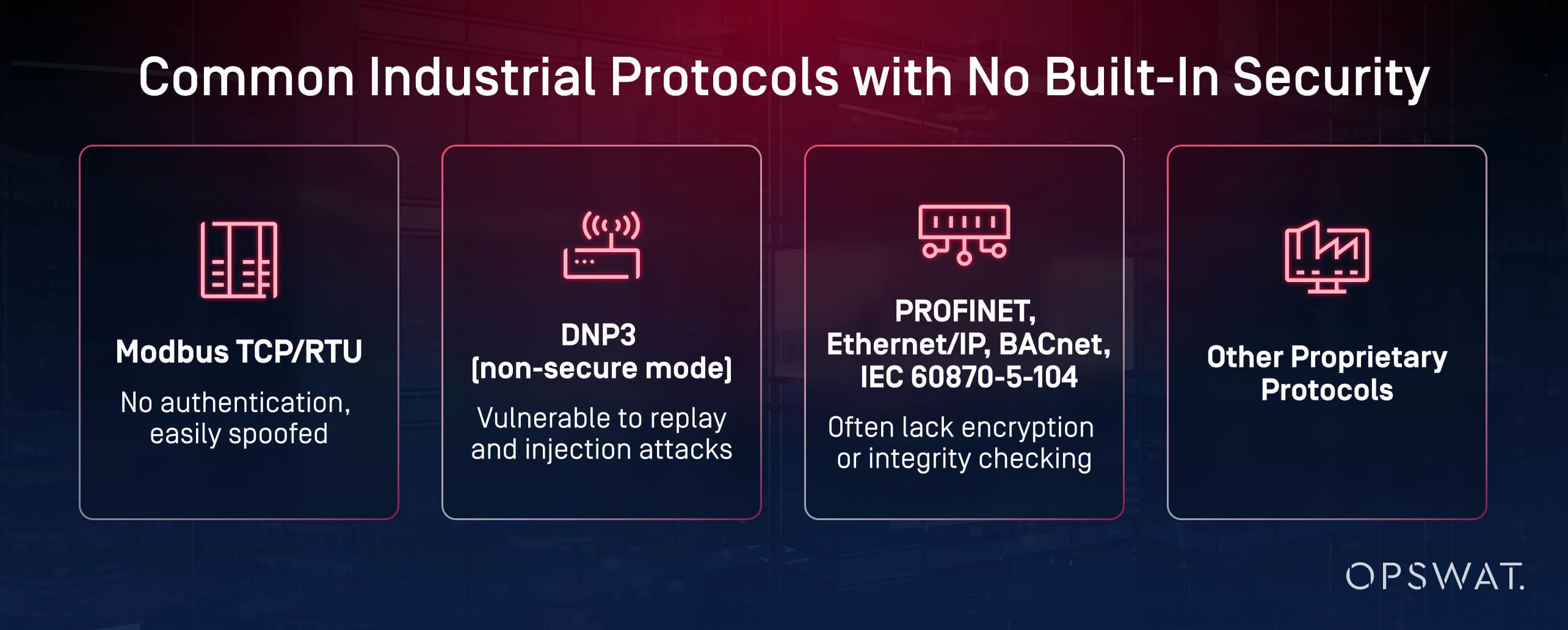
Here’s a closer look at what that means in real terms:
- Modbus TCP/RTU: Sends and receives commands with no authentication. An attacker can impersonate a master device and change actuator values.
- DNP3 (in non-secure mode): Vulnerable to replay and injection attacks; lacks robust integrity checks.
- PROFINET, EtherNet/IP, BACnet, IEC 60870-5-104: Offer minimal or optional security, with little to no data integrity or confidentiality guarantees.
- Proprietary protocols that vary in security implementation, often lacking foundational protections.
These security vulnerabilities may not be highlighted during normal operation. But under the scrutiny of a threat actor—particularly one with resources, time and intent—they become glaring vulnerabilities.
Real-World Impact: Protocol Exploits in Action
Security teams often prepare for zero-day exploits, but in OT, attackers frequently rely on "zero-effort" exploits—abusing protocol behavior that was never secure to begin with.
Consider the following scenarios:
Spoofing & Replay Attacks
Without authentication or integrity checks, attackers can capture legitimate traffic and replay it to manipulate processes or disrupt operations.
Man-in-the-Middle Attacks
Man-in-the-Middle Attacks: Intercepted OT traffic can be modified in transit, such as falsifying pressure readings or altering control commands.
Unauthorized Control
An intruder gaining access to the network can directly issue commands to PLCs (programmable logic controllers), bypassing safety protocols.
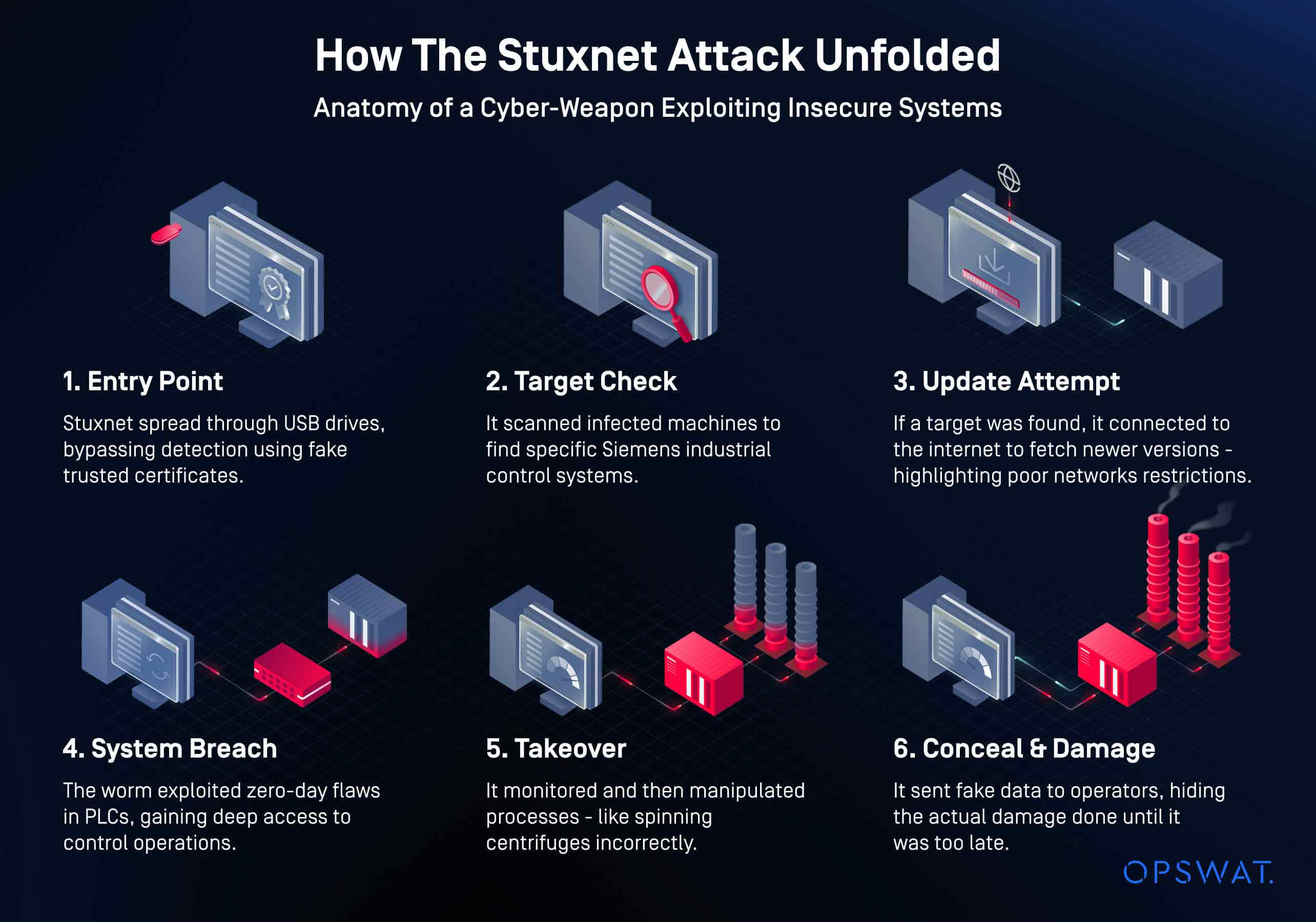
The Stuxnet worm is the most well-known and cited example—but it’s far from the only one. In recent years, multiple electric grid operators, water utilities, and energy companies have reported attacks that trace back to abuse of native protocol behavior.
The 2021 attack on a Florida water treatment facility involved a remote access compromise, but the ability to issue unauthorized commands relied on a protocol with no verification mechanism.
Why Traditional Defenses Fall Short
Traditional firewalls are still deployed today to secure legacy environments and protocols, but they can still be compromised. Even if these protocols could be made more secure, the infrastructure that makes modern life possible consists of billions of sensors, controllers and other end points that cannot be updated without a full replacement. As a result, operators must rely on additional layers of cyber defense to enforce perimeter security. While these are important, they do not mitigate the fundamental risks posed by insecure protocols.
- They don't rewrite protocol logic: Modbus will still transmit unauthenticated, plaintext commands—even behind a firewall.
- They rely on known signatures: DPI tools can’t detect new or low-level protocol abuses without heuristic or behavioral engines.
- They enable bi-directional traffic: Which opens the door to command injection, lateral movement, and staging for further attacks.
Most importantly, they assume the protocol can be secured by monitoring, not that it should be contained by design.
Towards Protocol-Aware Isolation
What’s needed isn’t just more inspection. It’s containment. It’s enforcing network segmentation at a fundamental level—ideally at the physical layer or with tightly governed logical controls.
Protocol-aware isolation mechanisms such as unidirectional gateways (data diodes) and protocol break solutions offer a more secure approach. They allow operations teams to keep necessary data flows—historian updates, sensor logs, event alerts—without exposing control surfaces to external or less-trusted networks.
This ensures alignment with national, regional, and industry-specific regulatory mandates, along with operational resilience. When insecure protocols can’t be rewritten or replaced, they must be segmented, filtered, and isolated by systems purpose-built for the job.
A Practical Option: MetaDefender NetWall
For environments where insecure protocols are unavoidable, MetaDefender NetWall provides hardened isolation and transfer solutions:
✓ Optical Diodes: Enable one-way, physically enforced data flows with no return path—ideal for air-gapped zones.
✓ Unidirectional Security Gateway: Allows controlled, validated unidirectional data exports from OT to IT, over a protocol break.
✓ Bilateral Security Gateway: Supports secure communication for applications that require a data response like MS SQL—enabling safe remote control or vendor access.
Discover how MetaDefender NetWall optical (data) diodes and security gateways can give you the critical advantage when it comes to securing your high security environments.

