Defining Air-Gapped Networks
An air-gapped network is a security architecture in which computers or networks are physically or logically isolated from unsecured systems, including the public internet. This separation, commonly known as an “air gap,” prevents unauthorized access, ensuring sensitive data and systems remain protected from external cyberthreats.
Often used in environments that demand maximum protection, such as classified networks or OT (operational technology) systems in critical infrastructure, air-gapped systems offer one of the most secure network designs available.
Air Gap vs. Network Isolation: Key Differences
While network isolation can involve the segmentation of networks through software-defined boundaries like VLANs or firewalls, air-gapped networks remove connectivity entirely. This physical disconnection eliminates inbound or outbound traffic paths, making air-gapped systems more resilient to external compromise.
Industry Terminology Explained
Air-gapped networks are common in high-security environments such as classified government systems, OT environments, and ICS (industrial control systems). These networks often support infrastructure where downtime or data breaches could have catastrophic consequences.
Terms like “high side/low side” refer to the separation between trusted and untrusted environments, with air gapping ensuring no direct bridge between the two.
How Do Air-Gapped Networks Work?
Air-gapped networks operate by enforcing either physical or logical separation from unsecured systems. These measures ensure that no direct communication—wired or wireless—exists between the isolated system and external networks.
One common architecture involves using hardware-enforced unidirectional gateways, such as data diodes, to allow information to flow out of the air-gapped environment without allowing any inbound data flow.
Physical Isolation & Network Segmentation
Physical isolation refers to the complete disconnection of systems from any network that might introduce risk. This may involve placing systems in shielded rooms or removing any wireless or Ethernet interfaces entirely.
Network segmentation can complement physical isolation by creating strict internal boundaries between systems based on sensitivity and function.
Unidirectional Data Flow & Data Diodes
Unidirectional data flow, often enforced by data diodes, allows for one-way transfer of information from a higher-sensitivity environment to a lower-security zone without a return path. Data diodes, in particular, use hardware-level enforcement to prevent return traffic, eliminating the risk of backchannel communication.
These devices are essential in environments like power grids, where operators need access to real-time telemetry without introducing external threats.
For more on how data diodes compare to other security tools, see Data Diodes vs. Firewalls.
Security Benefits of Air-Gapped Networks
Air-gapped networks alone are not perfect, but they generally offer protection against external cyberthreats. Because they are disconnected from external systems, they reduce risks from threats that depend on internet access, including many types of malware, ransomware, and remote exploitation tools.
Air-gapped systems are often the final line of defense for the most critical operations, from military command centers to nuclear facility controls.
Critical Infrastructure & OT Security
Air-gapped networks play a vital role in securing OT environments like energy plants, water treatment facilities, and transportation systems. In fact, many of the critical infrastructure systems we rely upon most were built prior to the advent of the internet.
Systems that once relied on trucks to drive from substation to substation to collect data still serve us today, even though the internet has continued to evolve and digitize workflows.
These industries depend on predictable, uninterrupted performance. By isolating key systems, operators ensure safety and reliability, even when threats are actively targeting IT-connected components.
To explore this further, read Securing Air-Gapped Environments from Targeted Attacks.
Building and Maintaining Air-Gapped Networks
Deploying and managing an air-gapped network requires careful planning and strict operational discipline. Organizations must decide whether to use physical or logical air gaps, and how to handle data import/export in a secure way.
Backup strategies, known as air gap backups, are also critical. These backups are stored offline or in isolated environments to prevent ransomware from encrypting or deleting them.
Physical vs. Logical Air Gaps
A physical air gap means no network cables, Wi-Fi connections, or other digital bridges exist between the secured system and outside networks. A logical air gap uses software controls like firewall rules or routing restrictions, which can offer convenience but are less secure and vulnerable to misconfiguration or exploitation.
Removable Media & Secure Data Transfer
Air-gapped networks often rely on USB drives, CDs, or other removable media to move data in and out. This process introduces risk. To manage it securely, organizations should:
- Scan all media and transient devices for malware before use
- Use trusted hardware like MetaDefender Kiosk and MetaDefender Drive
- Apply access controls and audit trails to track transfers
Peripheral and removable media remains one of the few practical ways to update or retrieve data from an air-gapped system, but it must be tightly managed to mitigate risk.
Air Gap Attacks & Limitations
Despite their strength, air-gapped networks alone simply are not practical. There needs to be a way to access real-time data; this means that communication between high security and low security networks needs to be implemented—ideally in the form of one-way, hardware-enforced data diodes.
Additionally, air-gapped networks are not invincible. Specialized attacks have successfully breached air-gapped systems using unconventional vectors such as compromised USB devices, electromagnetic signals, or insider threats.
Maintaining these systems can also be resource-intensive and operationally complex.
Notable Air Gap Attack Examples
The most famous air gap attack is Stuxnet, a sophisticated worm designed to target uranium enrichment facilities in Iran. It propagated via infected USB devices and was specifically engineered to alter PLC (programmable logic controller) operations without network access.
Other research has demonstrated ways to exfiltrate data using blinking LEDs, ultrasonic signals, or power fluctuations—highlighting that even isolated systems can be probed under the right conditions.
Limitations & Maintenance Challenges
Air-gapped networks introduce complexity. Updates, patches, and system monitoring require manual processes. Human error, poor media hygiene, or lack of clear security protocols can create unexpected vulnerabilities.
Organizations must balance the benefits of isolation with the operational demands of maintenance and user experience.
Air-Gapped Networks vs. Other Security Approaches
Air-gapped networks are often compared to firewalled environments, network segmentation strategies, and data diode deployments. Each has its place in a robust security posture, but they differ significantly in cost, complexity, and effectiveness.
Air Gap vs. Network Segmentation vs. Data Diode
Feature | Air-Gapped Network | Network Segmentation | Data Diode-Based Security |
|---|---|---|---|
Connectivity | No connectivity | Controlled internal access | One-way external flow |
Isolation Level | High (physical/logical) | Medium (logical only) | High (hardware enforced) |
Use Case | Classified, OT, critical | Enterprise IT, departmental | OT monitoring, forensics |
Cost | High | Medium | Medium to High |
Maintenance Complexity | High | Low to Medium | Medium |
Resilience Against Cyberattacks | Very High | Medium | High |
For deeper insights, explore Bridging the Gap and Firewalls Are Not Enough.
Taking the Next Step
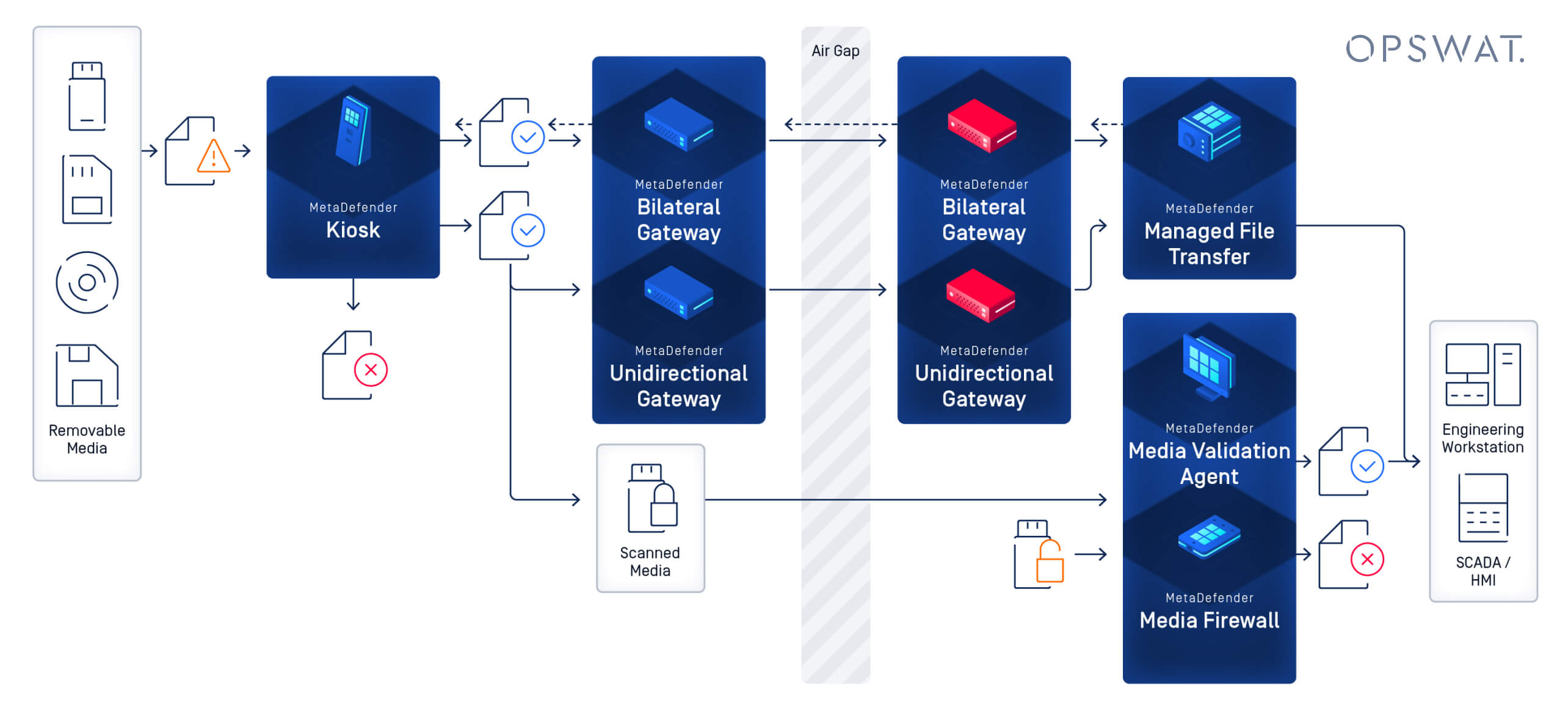
Whether you’re protecting a nuclear control system or simply need to ensure secure file transfers into an isolated lab environment, OPSWAT offers proven technologies for air-gapped environments. Our MetaDefender Optical Diode and MetaDefender Kiosk work together along with MetaDefender Drive and even more layers of the MetaDefender Platform to enforce unidirectional data flow and safe media import/export across critical networks.
OPSWAT is trusted globally to protect what’s critical—discover how we can help keep your air gap secure.
Frequently Asked Questions (FAQs)
Q: What is an air gap?
An air gap is a security concept where systems are isolated from untrusted networks to prevent unauthorized access or data leaks.
Q: How do air gaps work?
Air gaps work by physically or logically disconnecting systems from external networks, often using hardware controls like data diodes.
Q: What are the security benefits of air-gapped networks?
Air-gapped networks offer superior protection from external cyberthreats, reduce the risk of malware infiltration, and are ideal for critical infrastructure.
Q: Are air-gapped networks better than other security approaches?
They are more secure in high-risk environments but come with higher maintenance costs and limited flexibility compared to segmentation or firewalls.
Q: What is an air gap connection?
Technically, there is no “air gap connection” since air-gapped systems are disconnected by design. However, controlled transfers may use removable media or unidirectional gateways.
Q: What is the air gapping technique?
Air gapping is the method of isolating a system by removing all network connections, used in security-sensitive environments.
Q: Why is air-gapping important?
Air-gapping is essential for systems where data integrity and confidentiality are paramount, such as defense, energy, and manufacturing.
Q: What is an air-gapped network?
An air-gapped network is a secure network that is physically or logically isolated from untrusted systems to prevent unauthorized data exchange.

