In 2025, cybercriminals aren’t just bypassing traditional defenses—they’re turning them into weapons.
A new wave of phishing attacks is abusing trusted services like Google to slip past even the most security-aware inboxes. These messages often pass SPF, DKIM, and DMARC checks. They come from legitimate domains. They carry that reassuring green checkmark in Google Workspace. And yet—they’re malicious.
The problem? Email authentication doesn’t inspect behavior.
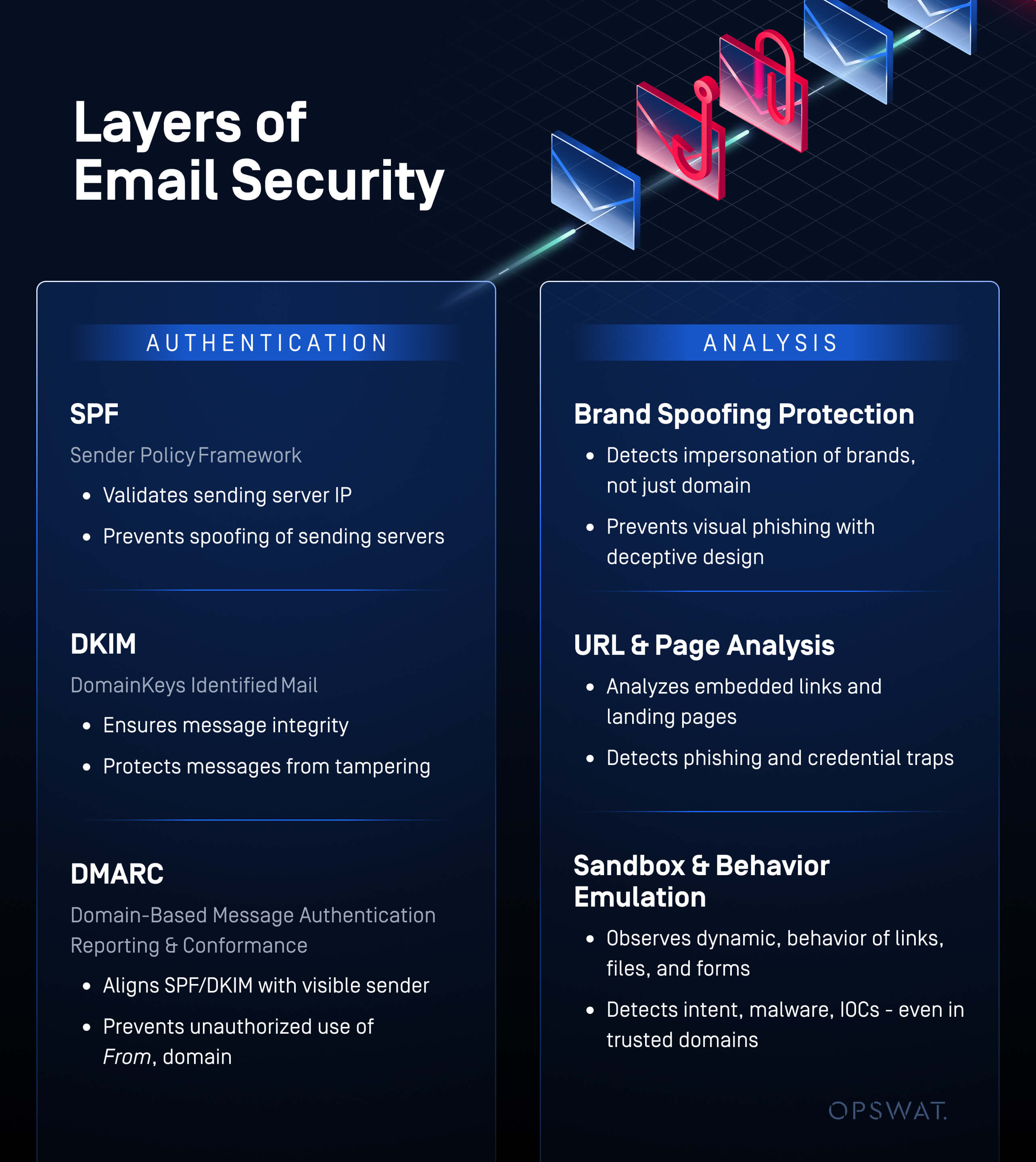
| Security Layer | Category | Purpose | What It Protects |
|---|---|---|---|
| SPF (Sender Policy Framework) | Authentication | Validates sending server IP | Prevents spoofing of sending servers |
| DKIM (DomainKeys Identified Mail) | Authentication | Ensures message integrity | Protects message from tampering |
| DMARC (Policy Enforcement) | Authentication | Aligns SPF/DKIM with visible sender | Prevents unauthorized use of From: domain |
| Brand Spoofing Protection | Zero Trust/Content Trust | Detects impersonation of brands, not just domain | Prevents visual phishing with deceptive design |
| URL & Page Analysis | Zero Trust/Behavioral | Analyzes embedded links and landing pages | Detects phishing and credential traps |
| Sandbox & Behavior Emulation (MetaDefender Sandbox) | Zero Trust/Behavioral | Observes dynamic behavior of links, files, and forms | Detects intent, malware, IOCs — even in trusted domains |
To keep up, enterprise security teams need more than trust-based signals. They need behavior-based detection. And that’s where OPSWAT MetaDefender Sandbox comes in.
Signed, Sealed, and Compromised: The DKIM Replay Loophole
One emerging tactic is a DKIM replay attack—where an attacker reuses a legitimately signed email header but appends malicious content beyond the signed portion.
Here’s how it works:
- DKIM uses a signature to verify that a portion of the message hasn’t been altered.
- But if the l= tag (length) is used, only part of the message is signed.
- An attacker can insert malicious content after that signed portion—leaving the DKIM check fully intact.
- DMARC passes, because it depends on SPF or DKIM to validate the source.
The result? A perfectly authenticated message that delivers phishing content.
OAuth Phishing Abuse: Hijacking Trust from Inside Google Alerts
Another disturbing trend is the abuse of Google’s OAuth infrastructure.
Attackers are:
- Creating fake OAuth apps named things like “Google Security Update” or “Account Review Required”
- Sending Google-signed security alerts notifying users about these apps
- Embedding phishing links in those alerts—backed by Google’s legitimate no-reply domains
The entire phishing lure appears in a Google-branded format, using threaded alerts and domain reputation to disarm users. It’s not spoofed—it’s hosted by Google.
The Green Checkmark Isn’t Enough
It’s a false sense of security. A message that passes SPF, DKIM, and DMARC might still:
- Contain credential harvesting pages
- Use UI tricks to hide login fields
- Exploit whitespace to delay malicious payloads
- Host fake Microsoft or Google login pages on legitimate infrastructure (e.g., sites.google.com)
Email authentication only validates where a message comes from—not what it’s doing.
MetaDefender Sandbox: A Critical Layer of Defense for Email Behavior
OPSWAT’s MetaDefender Sandbox adds critical visibility. Rather than relying on signatures or sender validation, the sandbox emulates email behavior:
- Dynamic Link Inspection – Follows embedded links in a secure environment to evaluate page behavior in real time
- UI and Layout Analysis – Identifies fake login screens, hidden fields, and credential traps
- Phishing Flow Detection – Detects redirections, form submissions, and attacker-controlled endpoints
Because it doesn’t trust email by default, MetaDefender Sandbox detects what authentication-based solutions miss. Even signed, authenticated, and “green-checked” emails can be weaponized. MetaDefender exposes the real intent.
What Enterprises Must Do Now
Phishing is evolving. Your defenses must, too. Here’s how to get ahead:
- Adopt Zero Trust Email Security – Don’t rely solely on headers and metadata. Inspect email content and behavior.
- Add Behavior-Based Sandboxing – Enhance your detection stack with dynamic analysis for links, forms, and payloads.
- Secure Alerts and System Emails – OAuth and domain abuse make even alert emails a potential threat vector.
Inspect What Authentication Alone Can’t See
Discover how OPSWAT MetaDefender Sandbox detects advanced phishing—even from “trusted” sources like Google alerts. Talk to an expert today and discover how you can put our advanced sandbox on the front lines of your email security strategy.

