- Introduction
- Understanding Phishing: The What and Why
- The First Line of Defense: Policy and People
- Technical Countermeasures: The Role of Technology in Prevention
- OPSWAT's Real-Time Anti-Phishing Technologies
- Legal and Compliance Aspects
- Incident Response: Preparing for When Prevention Fails
- The Road Ahead in Phishing Prevention
Introduction
Phishing attacks remain the number one attack vector, exploiting vulnerabilities and posing significant financial and operational risks to critical infrastructure organizations. In 2021, a phishing email played a pivotal role in the Colonial Pipeline ransomware attack, which caused fuel shortages across the U.S. This high-profile incident highlighted just how vulnerable even critical infrastructure can be to such cyberattacks.
For CISOs and IT security teams, preventing phishing attacks is paramount. With threat actors constantly evolving their tactics, a robust, multi-layered security strategy is necessary to prevent attacks from bypassing native defenses.
In this blog, we’ll explore key strategies for phishing prevention, with a particular focus on advanced anti-phishing technologies, including OPSWAT’s Real-Time Anti-Phishing solution.
Understanding Phishing: The What and Why
Phishing is a form of social engineering where attackers trick individuals into revealing sensitive information, such as credentials, PII (Personally Identifiable Information), or banking and payment details. These attacks often impersonate legitimate entities to increase their chances of success. There are several types of phishing:
- Generic Phishing: Mass phishing emails sent to large numbers of recipients.
- Spear Phishing: Highly targeted attacks personalized to a specific individual or organization.
- Whaling: A form of spear phishing aimed at high-level executives, attempting to gain access to sensitive corporate information.
Why does phishing still succeed in fooling its victims? Phishing preys on human trust and the perceived legitimacy of fraudulent emails. Attackers have become adept at mimicking emails from trusted sources, making it harder for employees to distinguish phishing from legitimate messages.
Phishing remains the most common cause of security breaches, responsible for 36% of breaches globally. The success of phishing attacks often results from a combination of human error and inadequate email defenses, underscoring the need for both technological and human layers of security.
The First Line of Defense: Policy and People
Security policies and training programs are essential components of a phishing prevention strategy. However, they have significant limitations that need to be addressed.
Security Policies
Effective security policies lay the groundwork for email protection. These policies should cover essential topics like password management, email usage, and reporting suspicious messages. Organizations should also mandate multi-factor authentication (MFA) for all users.
Employee Training and Awareness Programs
The evolving nature and sophistication of phishing attacks, especially those involving social engineering, cannot be fully detected or prevented by relying solely on employee training. Employees will always be the weakest link in the defense chain, and even the most well-trained individuals can fall victim to a carefully crafted phishing campaign.
In addition, phishing training does not account for unknown phishing tactics, which are emerging at a rapid pace. Attackers are constantly refining their methods, and there is no guarantee that today’s training materials will protect employees from tomorrow’s attacks. While phishing simulations are a valuable tool, relying solely on them is not enough. What organizations need is a multi-layered solution that includes real-time detection and mitigation capabilities.
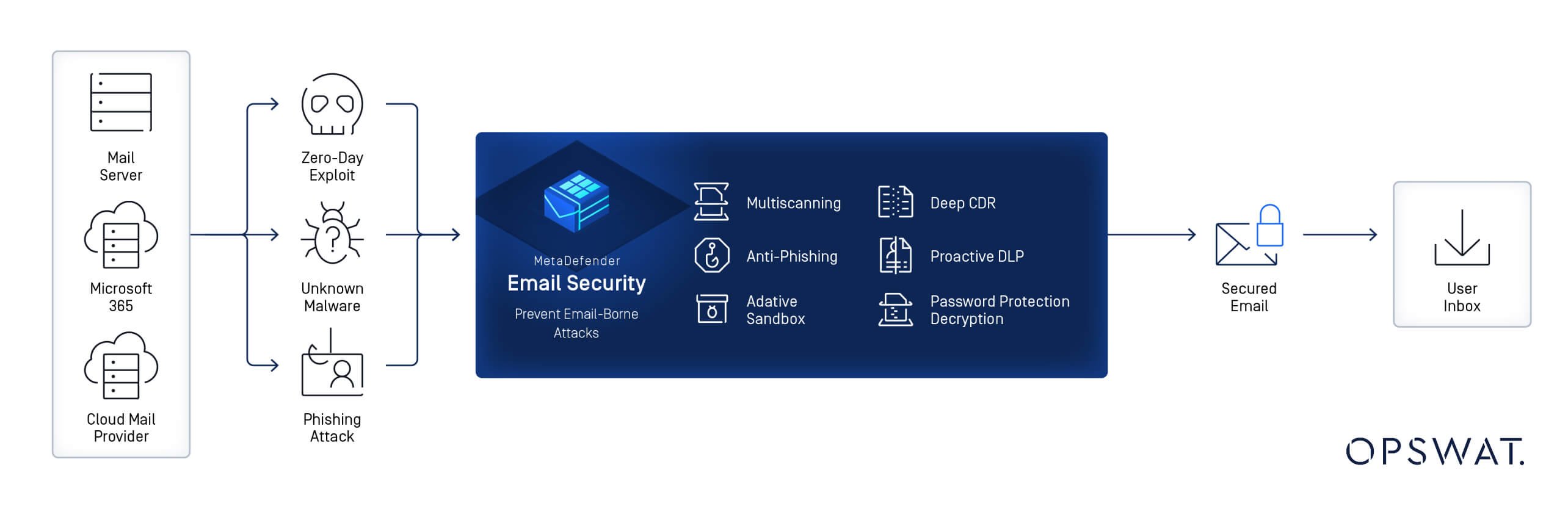
Technical Countermeasures: The Role of Technology in Prevention
Given the limitations of employee training, advanced technological defenses are required to catch phishing attempts that would otherwise slip through the cracks.
While authentication protocols like DMARC, SPF, and DKIM are effective at verifying the legitimacy of email senders, they are not foolproof. Attackers can exploit misconfigurations or use techniques such as domain spoofing to bypass these defenses.
While Microsoft 365 (M365) offers strong built-in defenses for detecting common phishing, malware, and file-based exploits, it is not fully equipped to prevent more advanced, unknown, or highly targeted attacks. Threat actors are continuously evolving their tactics, and sophisticated phishing campaigns can slip past the native security measures of M365.
To ensure comprehensive protection, organizations need to bolster their email security with advanced defense layers. OPSWAT’s Real-Time Anti-Phishing technology provides this necessary enhancement by adding advanced features like time-of-click analysis and multi-layered detection powered by machine learning. These capabilities significantly reduce the risk of phishing emails bypassing security and reaching employees’ inboxes, safeguarding the organization from high-risk, sophisticated threats.
OPSWAT's Real-Time Anti-Phishing Technologies: A Critical Layer of Defense
Let’s explore how OPSWAT’s Real-Time Anti-Phishing technology enhances native security measures. Here’s how it works:
1. 99.98% Detection Rate for Phishing and Spam Attacks
OPSWAT’s solution delivers an exceptionally high 99.98% detection rate for spam and phishing attacks, significantly reducing the number of phishing emails that reach employee inboxes. This high accuracy rate comes from a combination of advanced heuristics and machine learning algorithms, which can detect even the most sophisticated phishing tactics.
2. Time-of-Click Analysis
One of the most effective features of OPSWAT’s anti-phishing solution is Time-of-Click analysis. Unlike traditional email defenses that check links only at the time of email delivery, OPSWAT continuously checks link reputation in real-time using over 30 trusted online sources. This means that even if a link is weaponized after an email is delivered, OPSWAT’s Time-of-Click analysis can block the malicious link before the user clicks on it.
3. Multi-layered Detection
OPSWAT’s anti-phishing solution leverages multilayered detection techniques, combining machine learning algorithms, behavioral analysis, and advanced heuristics to detect phishing attempts in real-time. This approach ensures that even new and previously unseen phishing attacks are flagged and quarantined before they can cause harm.
With OPSWAT’s solution in place, organizations gain a robust, multi-layered defense that addresses the gaps in Microsoft 365’s native email security, significantly improving their ability to prevent phishing attacks.
Legal and Compliance Aspects
Organizations that fail to adequately protect against phishing attacks not only expose themselves to security risks but also potential legal consequences.
For organizations handling sensitive data, such as those in healthcare or finance, compliance with regulations like GDPR and HIPAA is essential. GDPR mandates strict data privacy measures for companies that manage EU citizens' personal data, while HIPAA outlines security standards for protecting patient information. Falling victim to a phishing attack can lead to costly penalties under these regulations.
To meet these regulatory standards, companies need to implement comprehensive phishing protection strategies that go beyond basic email filtering. OPSWAT’s advanced anti-phishing technologies help organizations align with these regulations by providing the real-time protection required to meet compliance standards.
Incident Response: Preparing for When Prevention Fails
Even with the best defenses in place, no system is 100% foolproof. A well-prepared incident response plan ensures that your organization can respond quickly and effectively when a phishing attack does slip through.
- Identification: Rapid detection and acknowledgment of a phishing attack
- Containment: Isolating affected systems to prevent further spread
- Eradication: Removing malicious emails and any associated malware
- Recovery: Restoring normal operations and addressing any data breaches
- Post-Incident Review: Learning from the incident to improve defenses and prevent future attacks

Organizations should regularly update their incident response plans and conduct post-incident reviews to ensure continuous improvement.
The Road Ahead in Phishing Prevention
Preventing phishing attacks requires a proactive, multi-layered approach that integrates advanced technologies with continuous employee training. While traditional email defenses like those offered by Microsoft 365 can catch basic phishing attempts, they are insufficient to stop advanced, targeted attacks. OPSWAT’s Real-Time Anti-Phishing technology provides the added layer of security necessary to block even the most sophisticated phishing campaigns.
By adopting a multi-layered solution that combines cutting-edge technology with human awareness, organizations can bolster their defenses against phishing attacks. Now is the time for businesses to assess their email security posture and invest in solutions that provide real-time protection and adaptability, keeping their sensitive data safe from evolving threats.
Ready to protect your organization from phishing attacks with real-time defenses?
Learn how OPSWAT’s Anti-Phishing solutions can provide the security you need to prevent even the most sophisticated attacks. Contact us today to upgrade your email security posture.

