Securing More Than Files
Cyberattacks today don’t stop at the file. Attackers exploit hidden infrastructure, compromised vendors, and rapidly shifting domains to bypass traditional defenses. To combat this, security needs layers—not just layers of tools, but layers of intelligence.
Today, we are proud to introduce MetaDefender InSights Threat Intelligence, a new engine within MetaDefender Core that serves as the connecting dot in comprehensive threat prevention strategies. By integrating curated, real-time threat intelligence with MetaDefender Core’s industry-leading Deep CDR™ and Adaptive Sandbox technologies, we deliver a truly multi-layered defense that blocks threats before they execute, while they remain hidden, and where they originate.
How Adding InSights Threat Intelligence Transforms Your Defense
MetaDefender Core already sets the standard for file security with Deep CDR (stripping malicious code) and Adaptive Sandbox (analyzing behavior). Now, InSights Threat Intelligence adds a critical third layer: Malicious IP/Domain blocking.
How It Works
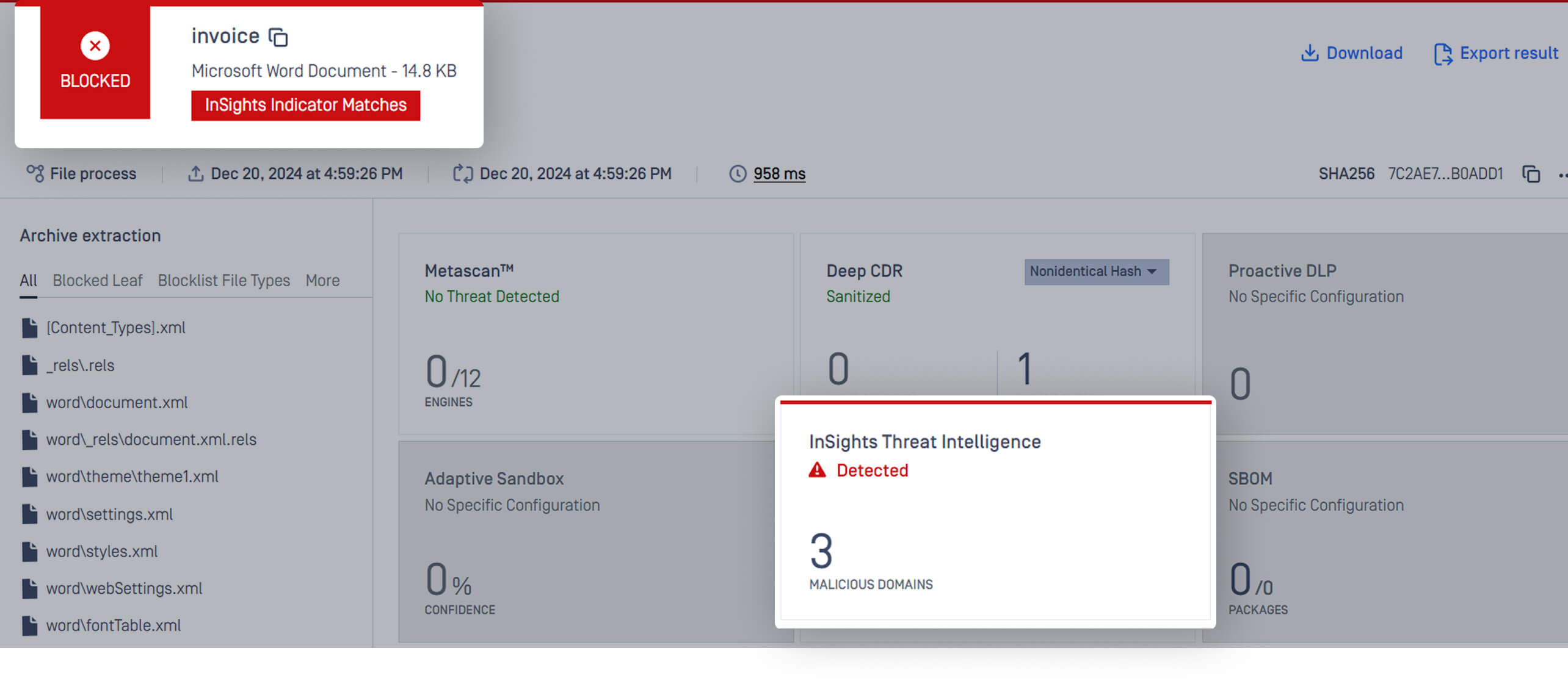
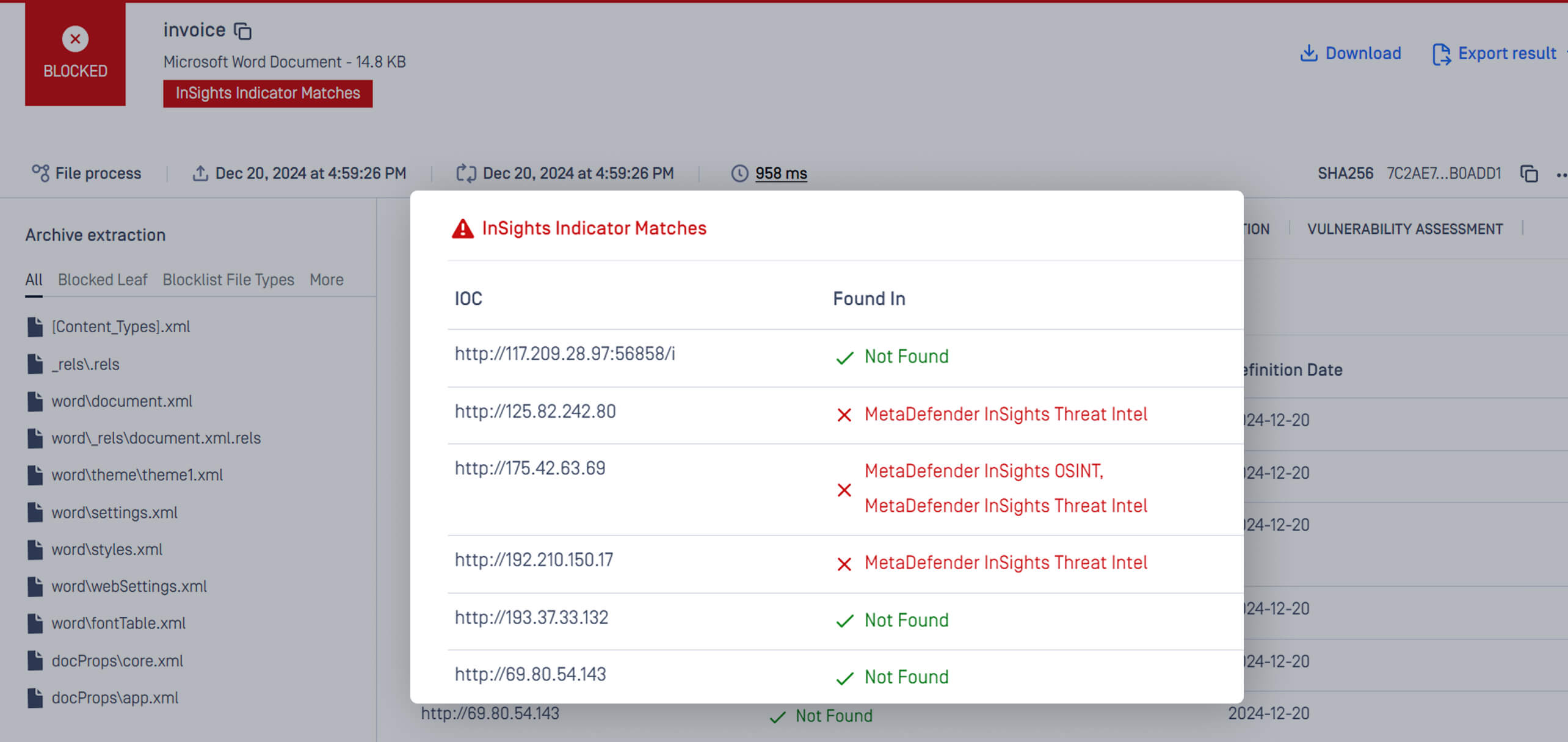
InSights Threat Intelligence scans documents for hidden malicious domains and IPs within milliseconds. It cross-references IoCs (indicators of compromise) against a global feed aggregating data from hundreds of trusted sources, ensuring you stay ahead of adversarial tactics. When a threat is detected, files are blocked at the point of entry—stopping attacks at the source.
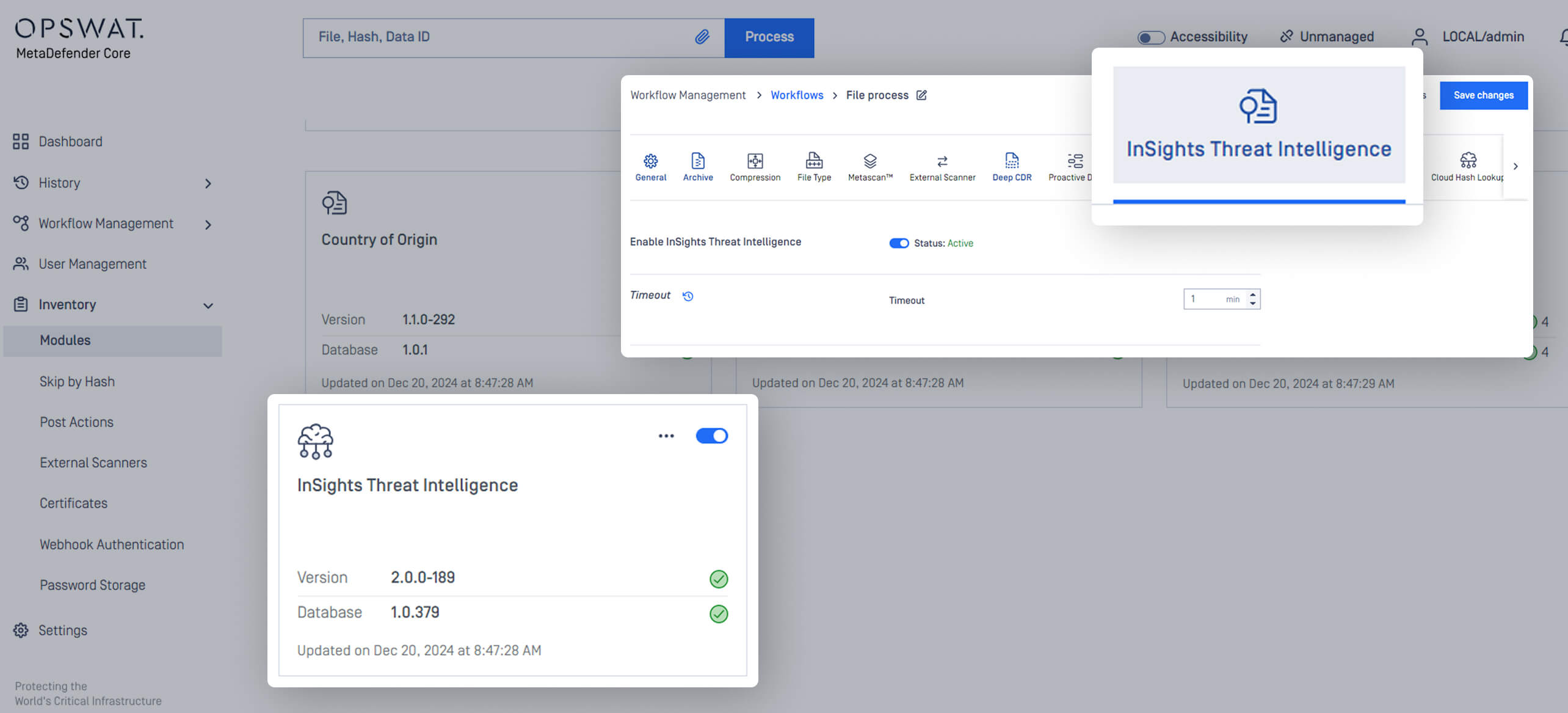
Configure InSights Threat Intelligence Engine in MetaDefender Core
Process a File With Malicious IPs/Domains
Provide the List of IOCs in the Scan Result
Key Features
Detect Hidden Threats
Identify malicious domains, IPs, and links embedded in documents, even after file sanitization.
Near Real-Time Blocking
Automatically quarantine high-risk files before they reach users or critical systems.
Enriched Deep CDR & Adaptive Sandbox
Augment Deep CDR and Adaptive Sandbox with threat context to prioritize risks and reduce false positives.
Continuous Threat Feeds Update
Track emerging adversarial infrastructure with dynamically updated intelligence feeds.
Air-Gapped Environment Support
Operate securely in isolated networks with manual or scheduled threat updates, protecting offline critical infrastructure from evolving threats.
Why InSights Threat Intelligence Stands Apart
While traditional tools focus on post-delivery detection, InSights Threat Intelligence enables organizations to:
Block zero-day exploits and phishing campaigns by targeting the infrastructure behind attacks.
Automate manual processes—like threat hunting and low-value investigations—to free up SOC teams.
Stay ahead of rotating domain/IPs and emerging exploit kits with live intelligence updates.
Align with NIST, CISA, and industry mandates by auditing third-party files and vendor communications.
Get Started Today
InSights Threat Intelligence isn’t just about neutralizing malicious content, it’s about dismantling the adversary’s playbook. Whether you’re managing complex security operations or defending a small network, InSights Threat Intelligence gives you the ability to make informed decisions and respond quickly.

