OPSWAT continuously improves our Proactive DLP (Data Loss Prevention) features and policy configurations to meet the diverse needs of our customers’ data protection requirements.
We are excited to announce that we have implemented a powerful new feature that automatically protects organizations from secret leaks.
A built-in secret detection feature was added to the Proactive DLP engine (version 2.13.0) in MetaDefender Core. It alerts you when a secret is found in your source code, whether it be API keys or passwords accidentally left in source. The built-in secret detection identifies secrets from Amazon Web Services, Microsoft Azure, and Google Cloud Platform.
This feature compliments the recently announced Advanced Detection Policy which enables customers to write complex rules that prevent files containing secrets like AWS Key ID or Microsoft Azure access key from being visible to attackers.
We demonstrate below how you can prevent the leak of secrets in your source code by using the new secret detection engine built into Proactive DLP using the MetaDefender Jenkins plugin.
Secret detection occurs with two methods.
1. Configure MetaDefender Core to Detect Secrets Utilizing DLP
From the MetaDefender Core UI you can enable the secret detection feature by heading to Workflow Management -> Workflows -> “name of the workflow” -> Proactive DLP -> Detect Secret.
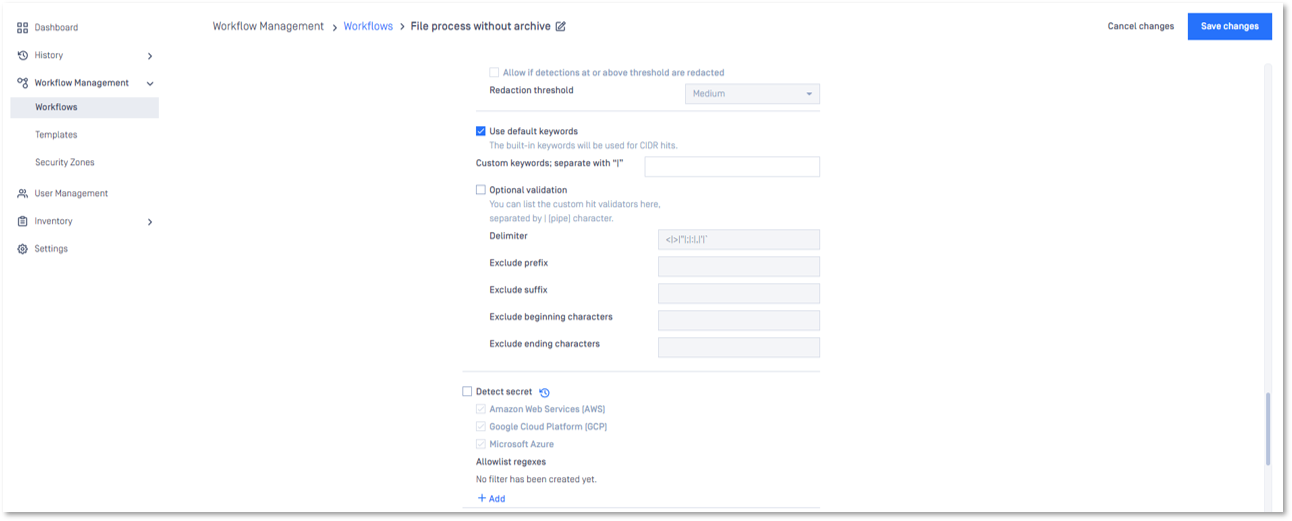
Here is a scenario where there are four hardcoded secrets in the demo file. We used the MetaDefender Core UI to upload and scan the demo file.
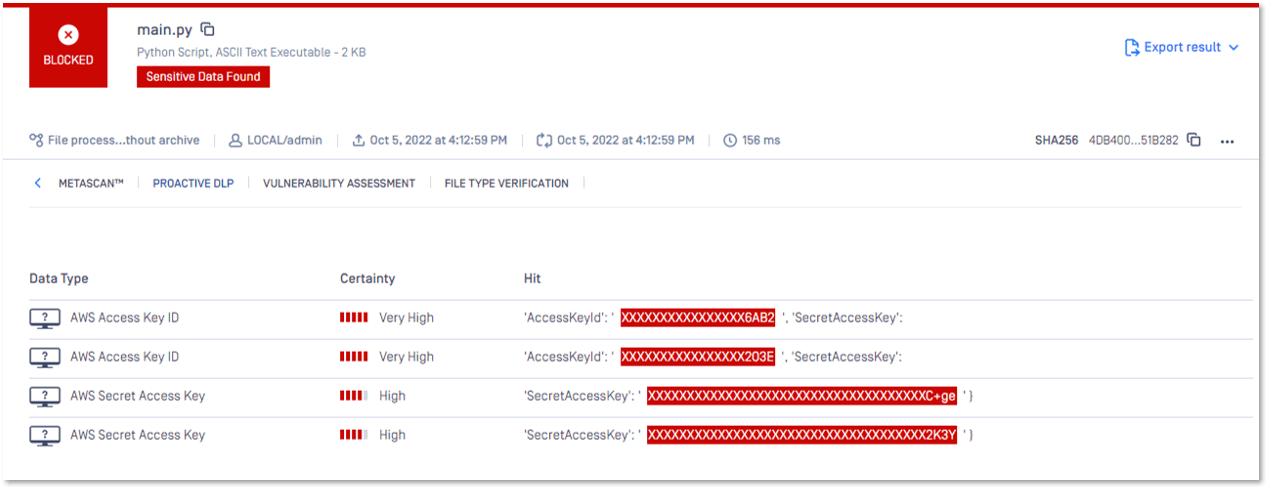
Proactive DLP successfully identified the secrets in the source code and blocked the file to prevent the leakage of the secrets.
2. Utilize the TeamCity or Jenkins plugin to scan a Repository
MetaDefender plugins for TeamCity and Jenkins secure your CI/CD pipeline protecting your source code and artifacts from different types of threats including secret leakage. You are notified when there are potential issues via built-in, automated fail-safes that prevent the leakage of sensitive information.
We’ll look at how MetaDefender Jenkins plugin uses the secret detection engine to scan a build for any secrets that may be present.
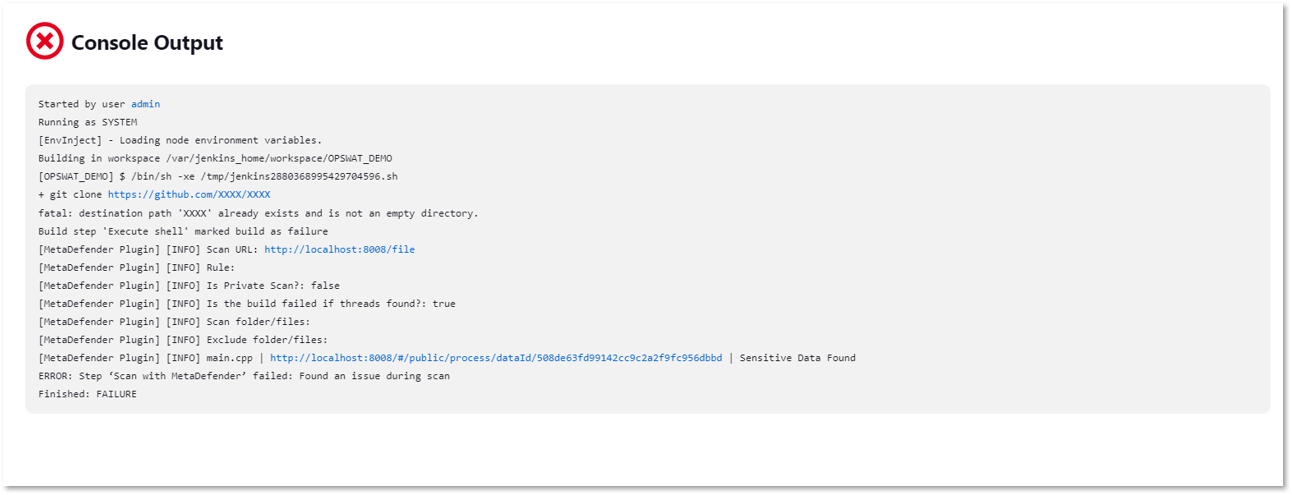
To demonstrate the effectiveness of our secret detection, our developers left a secret in a test file. The build process using Jenkins failed when it detected a secret in the example file. In the error message, it was stated “Sensitive Data Found.”
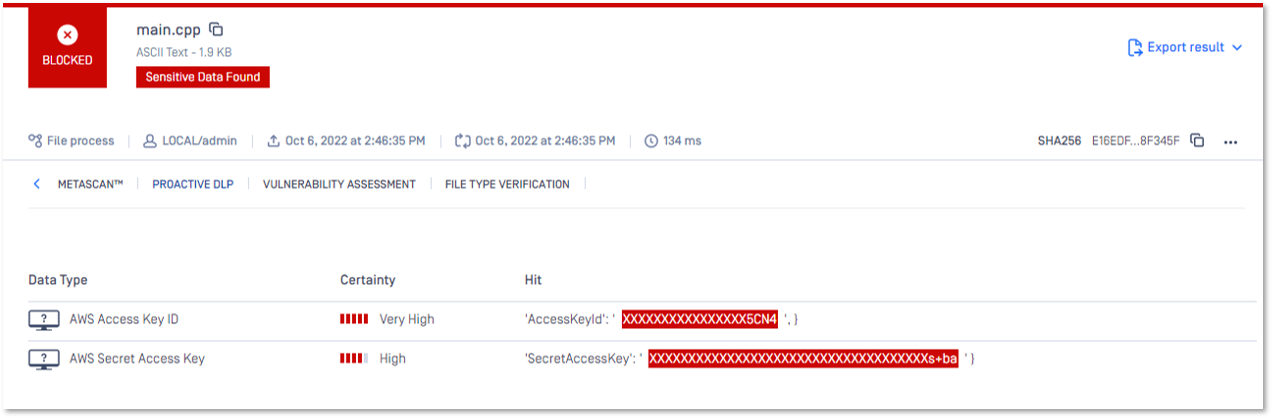
Proactive DLP was able to successfully identify the secrets contained in the source code and made sure the leakage of these secrets was prevented by notifying the developer before the leak occurs.
Learn more about how OPSWAT Proactive DLP prevents sensitive and regulated data from leaving or entering your organization’s systems.
Contact one of our critical infrastructure cybersecurity experts for more information and assistance.

