MetaDefender Software Supply Chain continues to enhance AppSec and DevSecOps teams’ experience and efficiency in securing applications against supply chain attacks. In this v2.5.0 release, we introduce a set of features focusing on simplified vulnerability management and SBOM standardization. These new capabilities make it easier to manage security across containers, binaries, and source code - at speed and scale.
Enhanced UI for Repository and Package Reporting
Optimize vulnerability management and triage issues faster at the repository and package levels.
CVE Search
Identify components impacted by known vulnerabilities.
Webhook-Based Scans for GitLab and JFrog Binaries
Webhook-Based Scans for GitLab and JFrog Binaries
Expanded Remediations in JFrog Artifactory
Address vulnerabilities faster and minimize risk exposure with copying, moving, and deleting binary artifacts.
CycloneDX SBOM Export
Report generation for compliance and standardization.
Repository and Package Reporting: Optimized Vulnerability Management
Our refined interface enables flexible viewing and analyzing threats data in repositories and packages in your projects.
The Reports tab now offers two distinct viewing modes (Repository-level and Package-level) to support both high-level visibility and detailed, component-level insights. Software development teams can gain insights into all discovered packages in the repository, and easily drill down into a particular package for further investigation.
Repository-Level View

This view provides a summary of scanned repositories, including:
- Vulnerabilities, malware, and secrets detected
- Total vs. vulnerable package counts
- License risk status
Clicking into each repository allows you to view a detailed SBOM and scan results.
Package-Level View
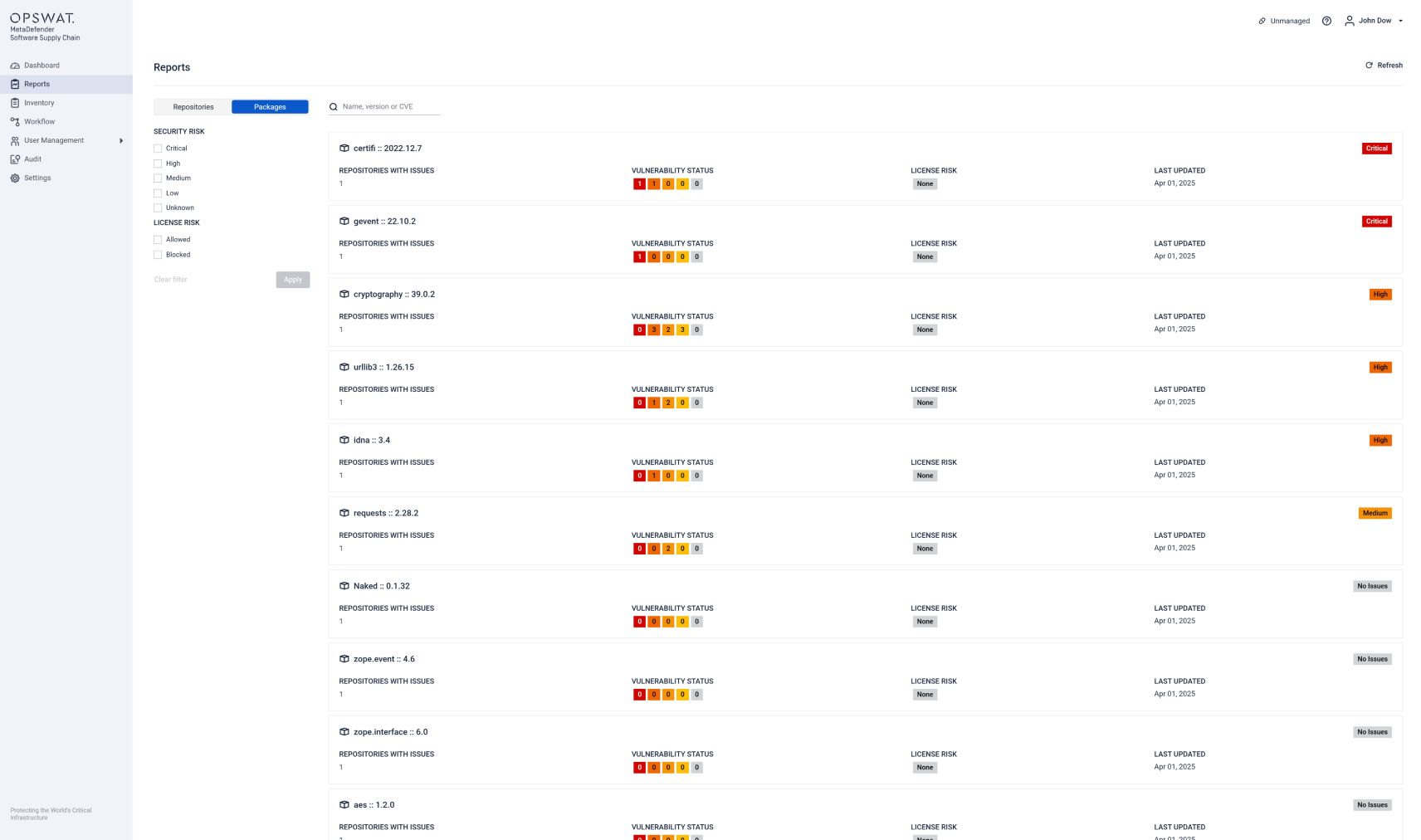
This view focuses on the software packages used in your projects, which displays:
- Package names
- Associated repositories containing vulnerabilities
- Vulnerability status
- License risk classification
- Risk severity levels
Filter Options
You can also filter the scan results by:
- Security risk severity (Critical, High, Medium, Low, Unknown)
- License status (Allowed, Blocked)
- Active connections (Repository, Container, Binary)
These dual perspectives support different roles and workflows between AppSec, DevSecOps, and engineering teams to enable more actionable risk prioritization and tighter collaboration across security and engineering.
CVE Search: Immediate Identification of Known Vulnerabilities

When a new CVE is disclosed, teams can search it directly to determine if any component in their environment is affected, so that they can respond to these threats with minimal delay. Backed by a continuously updated vulnerability database, this feature enables targeted triage without manually correlating CVE references to specific packages or build artifacts.
For teams managing large and complex projects with hundreds of scanned components, this update could enhance incident response workflows and vulnerability disclosure processes.
Enhanced Remediations for JFrog Binaries
In v2.5.0, MetaDefender Software Supply Chain continues to deepen our integration with JFrog Artifactory with enhanced remediation capabilities:
Copy Remediation
Safely transfer verified binary packages between artifact repositories, or isolate suspicious packages to a quarantine repository.
Hard Delete Remediation
Define rules to permanently remove compromised binaries, keeping your repositories clean and minimizing artifact-related risk exposure.
To put this into context, when managing artifacts in a CI/CD pipeline, artifacts initially stored in an “unverified” staging repository can be scanned by MetaDefender Software Supply Chain and moved to a “secure” repository once verified. This helps ensure artifacts are safe and compliant before deployment. By automating this process, teams can eliminate manual steps while maintaining artifact hygiene, traceability, and controlled access across the pipeline.
As a widely-used binary repository manager, JFrog Artifactory plays a central role in many CI/CD pipelines - storing build outputs, hosting third-party dependencies, and managing release artifacts. For DevSecOps teams, ensuring that only verified, policy-compliant binaries are promoted to downstream stages helps supports artifact governance policies, strengthens build provenance, and reduces the risk of artifact-level supply chain threats.
Automate Security Checks with Webhooks for GitLab and JFrog Artifactory
MetaDefender Software Supply Chain now supports webhook-based triggers to automate security scans in response to key development events. This allows security scans to be automatically initiated when specific events occur in JFrog Artifactory or GitLab.
- Trigger a scan immediately after a code commit or pull request.
- Scan source code on push or merge to main branches.
Key Features

- Workflow-specific URLs: Generate a unique webhook URL for each connected repository, enabling easy configuration in GitLab or JFrog Artifactory.
- Event-based Triggers: Automatically initiate scans upon push events or pull request creation to ensure continuous validation throughout the development cycle.
- Centralized Inventory Management: Manage and monitor active webhooks directly from the scanner’s inventory screen for control and visibility.
Benefits
- Integrate continuous validation of new components in CI/CD workflows.
- Real-time visibility into risks – new or updated components are evaluated as soon as they are introduced or modified in the project.
- Reduces manual effort and operational overhead.
- Scalable SDLC security for fast-moving software deployment.
About MetaDefender Software Supply Chain
MetaDefender Software Supply Chain enhances your DevSecOps pipeline by scanning every software library, including open-source third-party components to identify security threats and vulnerabilities. With our detection and prevention technologies, your SDLC is protected from malware and vulnerabilities to strengthen application security and compliance adherence.
Export SBOM to CycloneDX Format
To meet compliance requirements and enable ecosystem integration, development and security teams can export SBOMs (Software Bill of Materials) in CycloneDX format.
This supports the efforts to:
- Simplify SBOM generation in standardized formats.
- Enable submitting SBOMs to regulators or third-party stakeholders.
- Ensure compatibility across tools, ecosystems, and supply chain partners.
- Meet evolving software supply chain security standards without additional overhead.
More to Come
We’re continuing to expand MetaDefender Software Supply Chain’s capabilities to give security and DevSecOps teams the automation, visibility, and control they need to ship secure software at scale. For a tailored walkthrough of these new features, reach out to our cybersecurity experts.
Release Details
- Product: MetaDefender Software Supply Chain
- Release Date: 16 April 2025
- Release Notes: 2.5.0
- Download from OPSWAT Portal
For more information, talk to our cybersecurity experts.

