To provide safe, fast, and efficient malware analysis, we're excited to announce the addition of MetaDefender Sandbox, a next-generation sandbox built on adaptive threat analysis, into MetaDefender Core. This update enhances the already powerful set of features of the MetaDefender platform such as Content Disarm and Reconstruction (Deep CDR), Multiscanning, File-Based Vulnerability Assessment, Data Loss Prevention, and Threat Intelligence.
MetaDefender Sandbox adds unique dynamic analysis technology to MetaDefender. It detects malicious files and extracts "Indicators of Compromise" (IOCs) at lightning-fast speed using advanced, adaptive features like dynamic analysis, static file analysis, reputation services, and YARA signature matching.
MetaDefender provides MetaDefender Sandbox in two different versions: a full-featured Remote Engine and a lightweight Embedded Engine.
MetaDefender Sandbox Remote and Embedded Engine Comparison
There are two types of engines available for the MetaDefender Core Filescan module: the Embedded Engine and the Remote Engine:
- The Embedded Engine contains a "scanner" engine that is directly installed on the MetaDefender Core machine and processes files locally. It is similar to other MetaDefender Core modules such as Metascan and Content Disarm and Reconstruction (Deep CDR).
- The Remote Engine requires a separate Filescan instance and connects to the remote server based on a configurable URL and API key. The server can be on-premises or in-the-cloud.
Both engines include the following features:
- Static File Analysis: File parsers, file certificate validation
- Dynamic Analysis: Microsoft file emulation, PE unpacking, full binary analysis, and JavaScript/VBS emulation
- Reputation Service: Fuzzy hash lookup, Google Safe Browsing
- YARA Signature Matcher
- Community Trends
- Traditional Threat Intelligence Databases
The Remote Engine also includes:
- Static File Analysis: Image text analysis with Optical Character Recognition (OCR)
- Dynamic Analysis: PowerShell script emulation, URL emulation and Phishing detection
- Reputation Services: OPSWAT reputation lookup
- Enhanced reporting capabilities
Click here to see the full feature list.
Deploy MetaDefender Sandbox Engines with MetaDefender
You can automatically deploy Filescan if it is present on the update server and the Internet Module is set to Update Module, MetaDefender Core will automatically download and deploy the engine. There is also an option to deploy manually.
Connect to Filescan Remote Engine
If you’d like to connect to the full-featured Remote Engine, navigate to Inventory -> Modules -> MetaDefender Sandbox and add your API Key and the address you’d like to connect to.
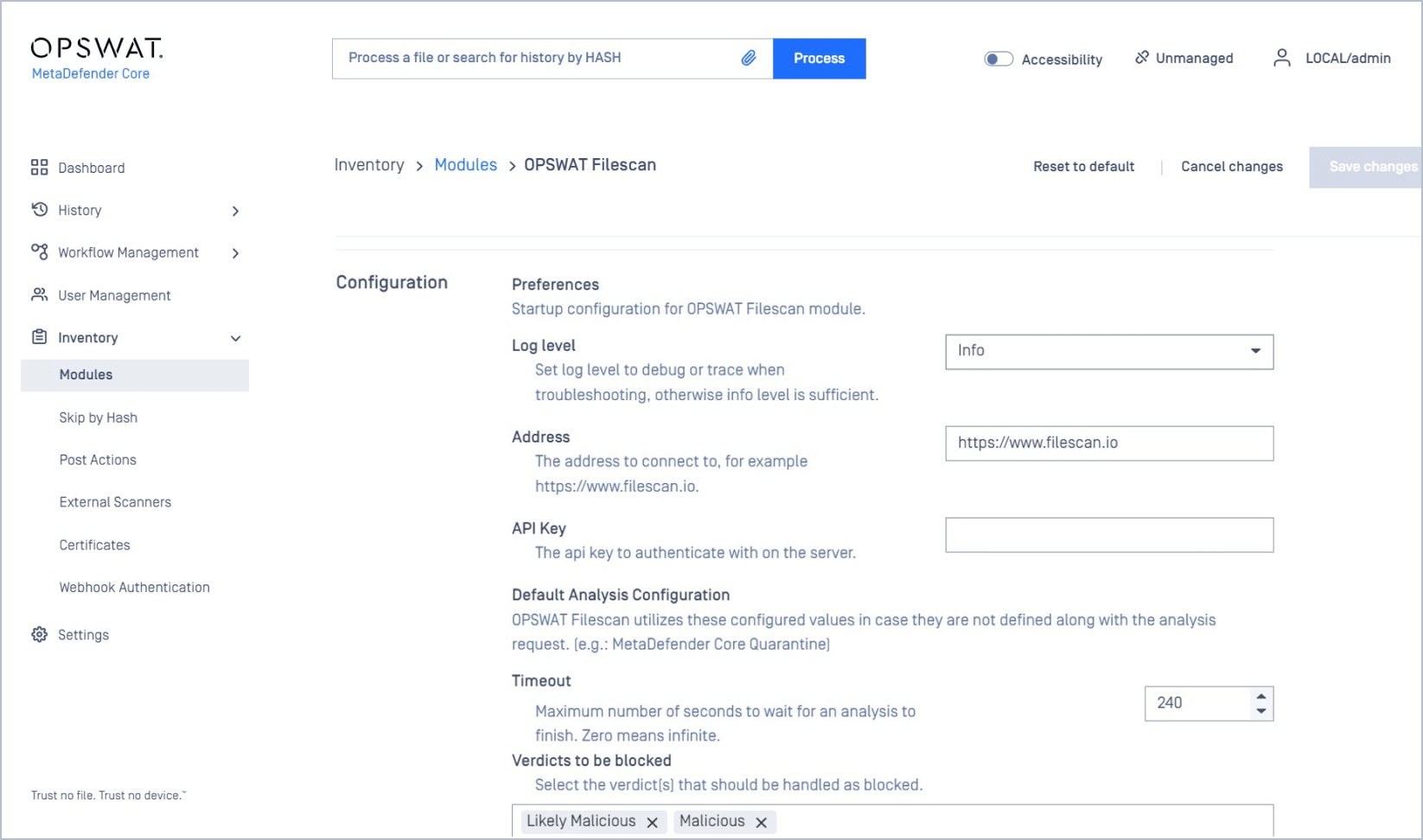
Configure MetaDefender Sandbox Module with MetaDefender
Global Configuration Settings
To globally configure Filescan, navigate to Inventory -> Modules -> MetaDefender Sandbox.
Global configuration settings provide granular control over the features you’d like to use to process and analyze files.
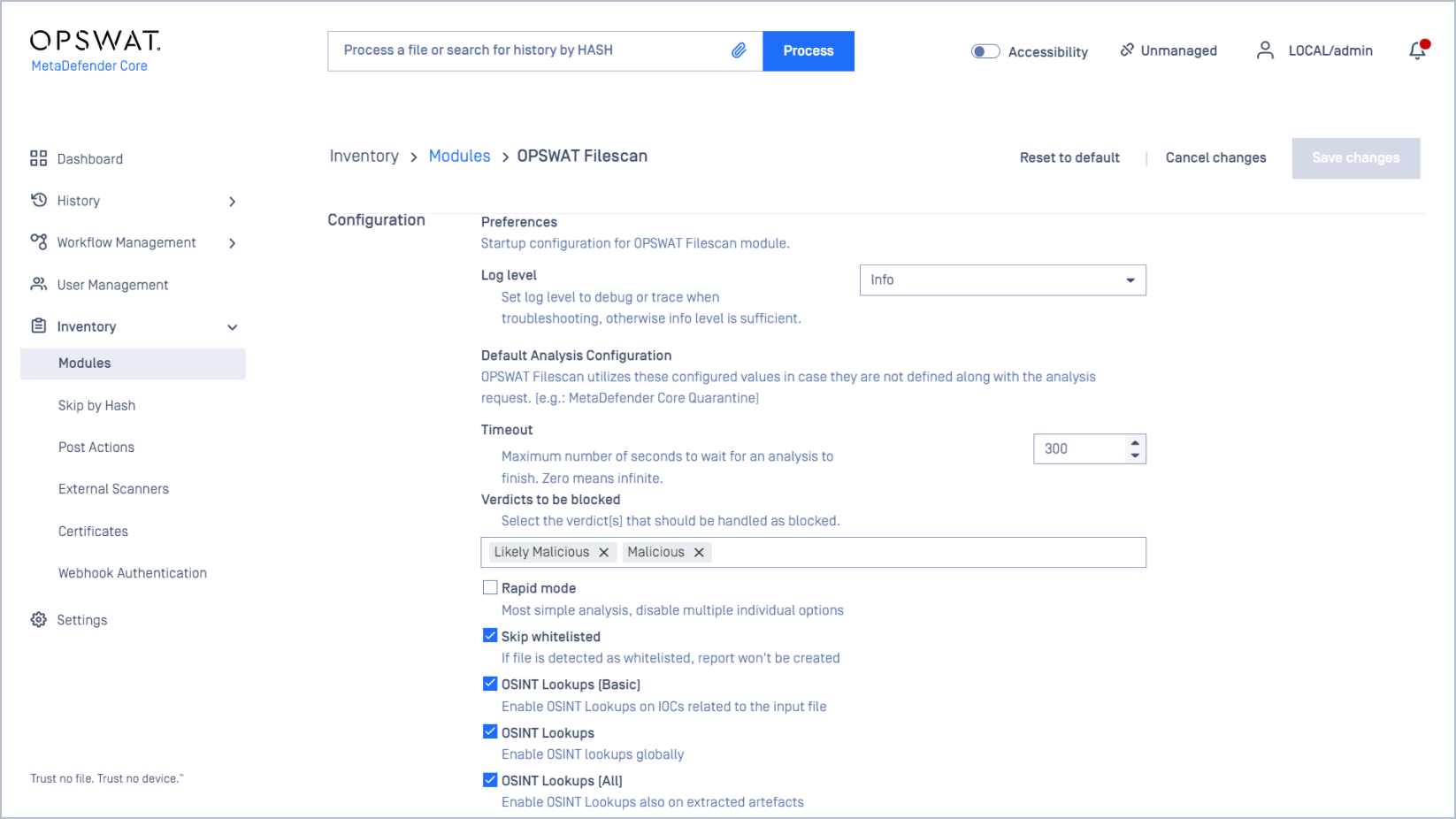
Workflow Configuration
With our Workflow Management, you can create a separate workflow from the global configuration. You can also choose to analyze files with other MetaDefender modules, such as Deep Content Disarm and Reconstruction (Deep CDR), Proactive Data Loss Prevention (DLP), custom block and allowlists, and many more.
To create a custom workflow, navigate to Workflow Management -> New Workflow.
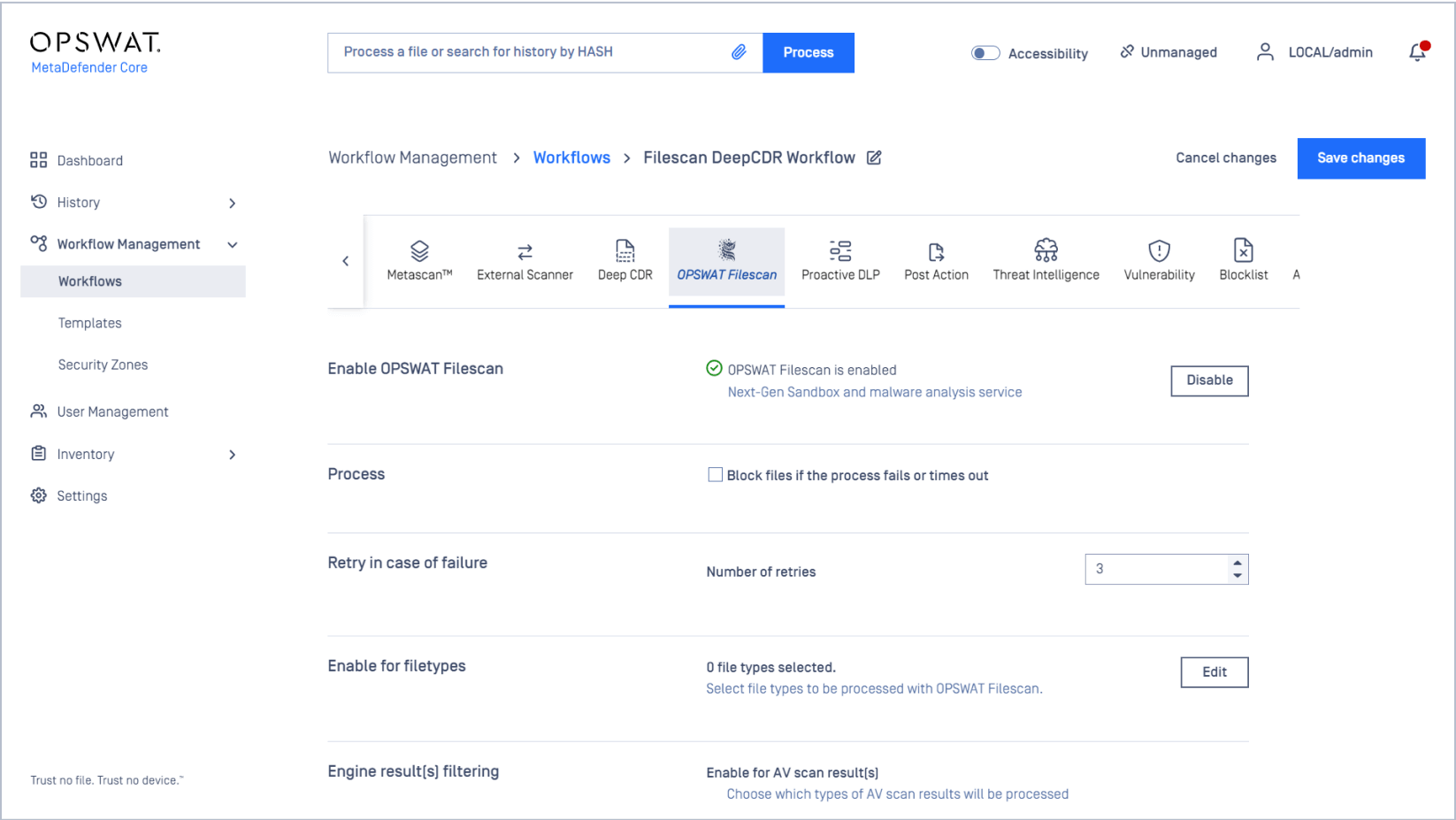
Use MetaDefender Sandbox Engine with MetaDefender
Quarantine Mode & Out-of-Band Analysis
In some scenarios, you may want to send blocked files to quarantine for further analysis.
For instance, if Metascan identifies files as malicious or suspicious, you can send them to Security Operations Centers (SOC) analysts to understand tactics, techniques, and procedures (TTPs) and automatically investigate malware outbreaks.
Digital Forensics and Incident Response (DFIR) teams might want to scrutinize the original files and obtain a comprehensive report from Filescan, which includes Indicators of Compromise (IOCs), additional file details, and more.
You can also sanitize files with Deep Content Disarm and Reconstruction (Deep CDR) and choose to send the original files to Filescan for a thorough inspection. Our out-of-band analysis provides safe files to end-users while offering analysts the tools they need to investigate malware outbreaks.
Navigate to Workflow Management -> Workflows -> Select Your Workflow -> Process -> Quarantine blocked files
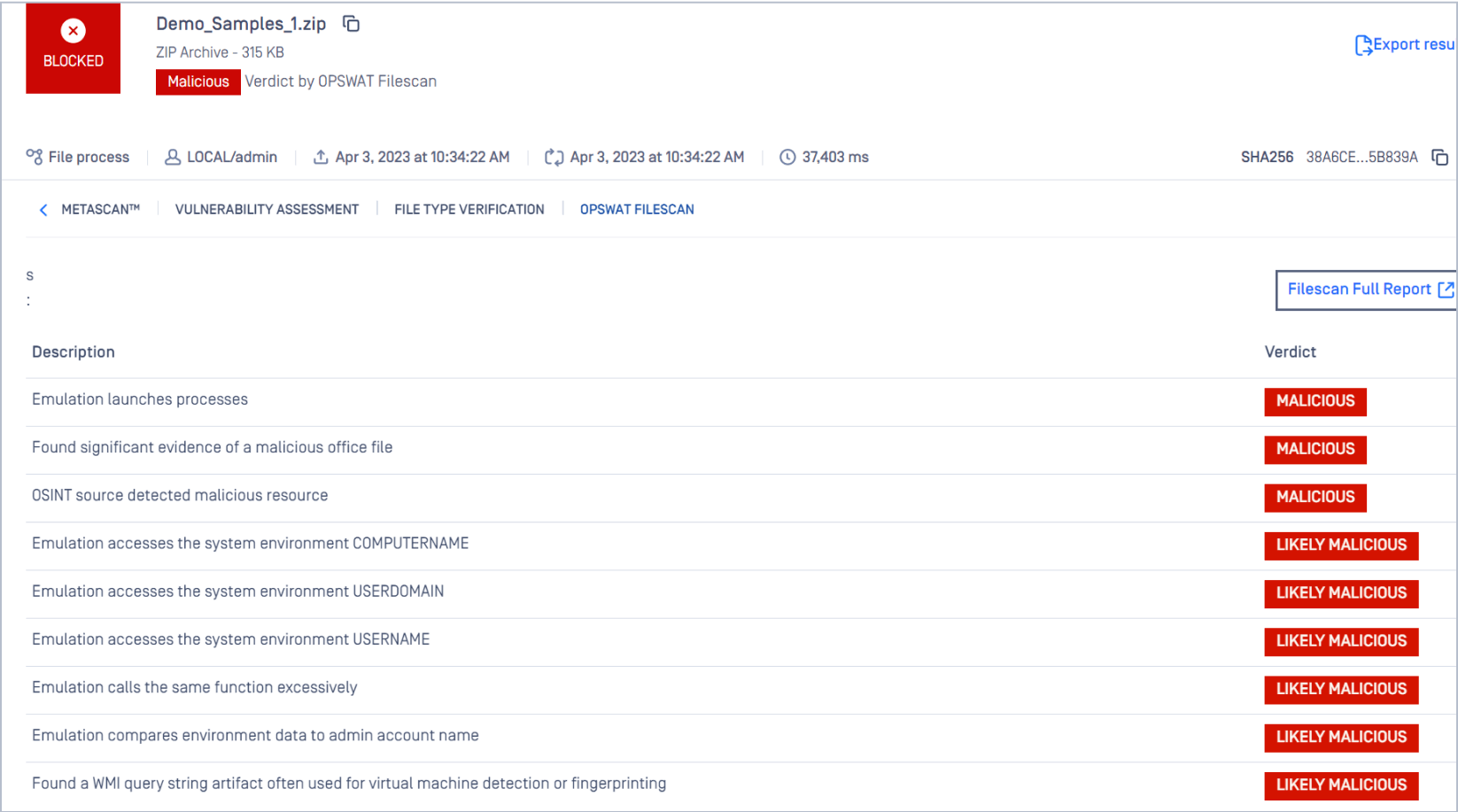
Automatically Process Files with MetaDefender Sandbox
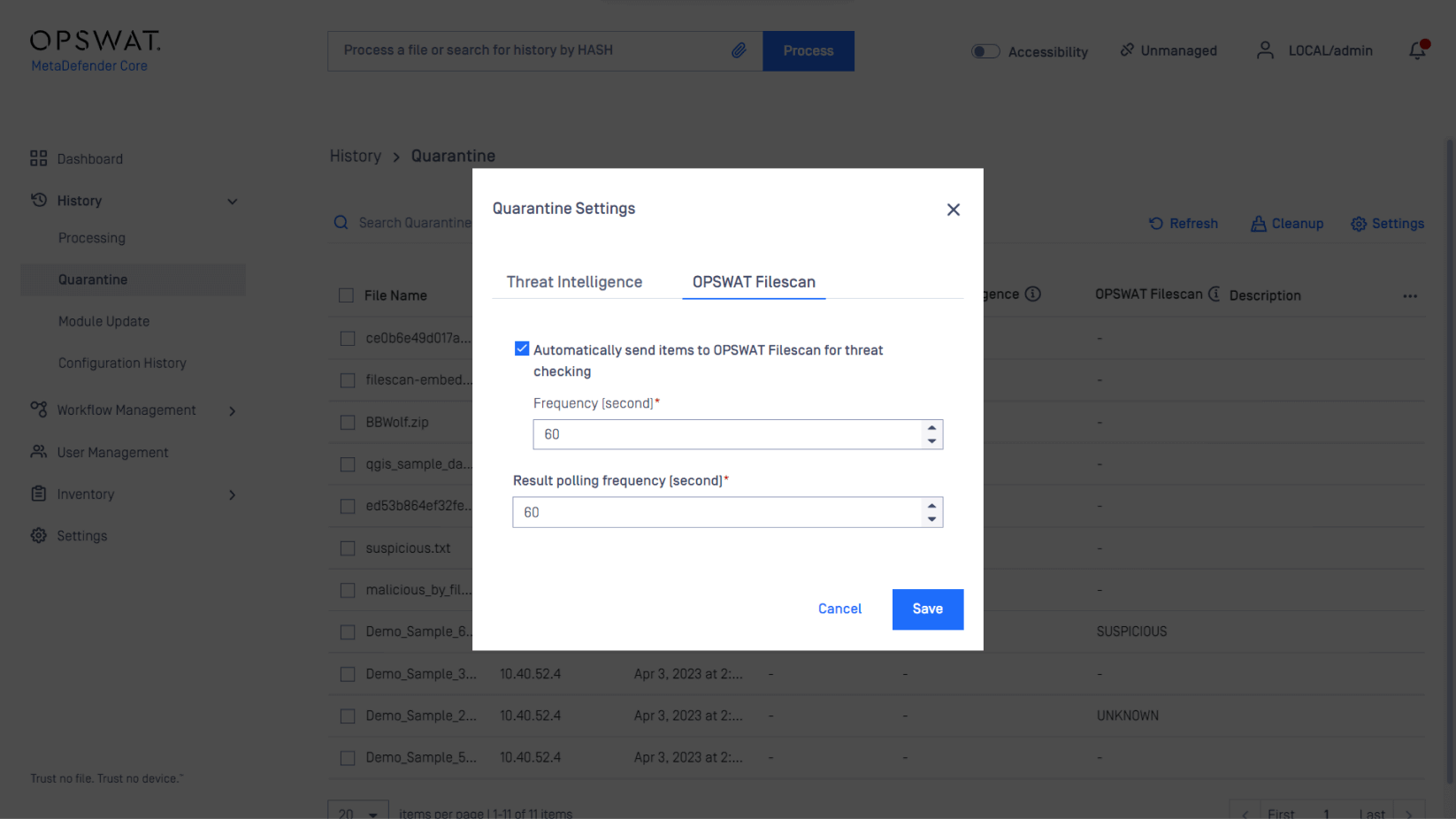
You can automatically scan quarantined files with MetaDefender Sandbox and return in-depth analysis of each file.
Navigate to History-> Quarantine -> Settings -> MetaDefender Sandbox -> Enable Automatically send files to MetaDefender Sandbox.
MetaDefender + Filescan Sandbox Malware Analysis & Detection Features
Our proprietary emulation engines enable dynamic file analysis at scale and incredible speed, enabling you to detect and protect against harmful files quicker and more efficiently.
Adaptive Threat Analysis Feature
Filescan’s dynamic malware analysis emulates Microsoft Office documents, PowerShell scripts, URLs and much more.
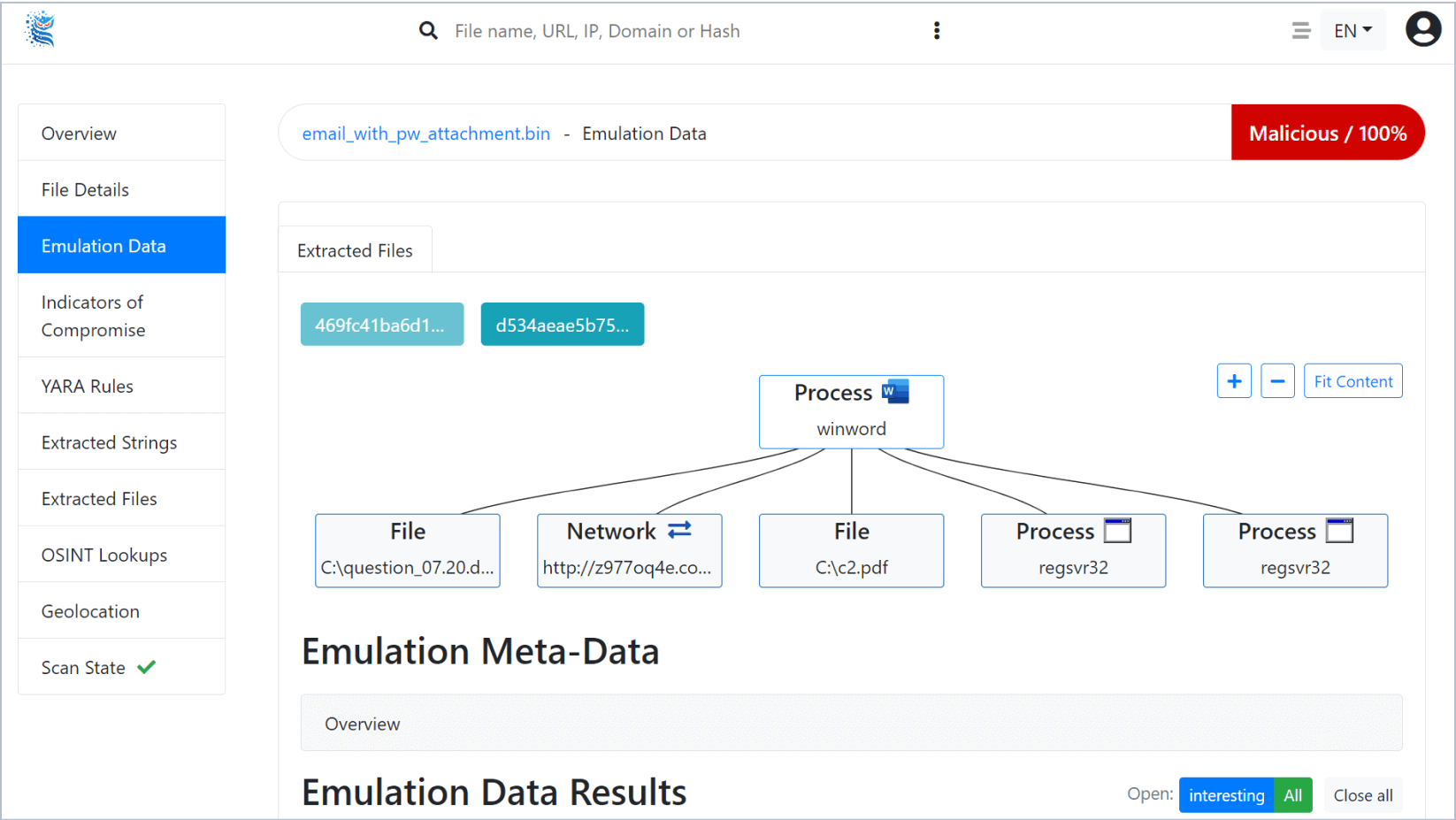
Microsoft Office File Emulation
Emulate Microsoft Office files and detect malicious macros and other hidden threats
URL Emulation & Phishing Detection
Filescan can detect phishing attempts by emulating URLs in real-time, giving you the ability to catch threats before they can do any damage.
Static Analysis Features
This update adds new static malware analysis features, offering enhanced protection against advanced cybersecurity threats.
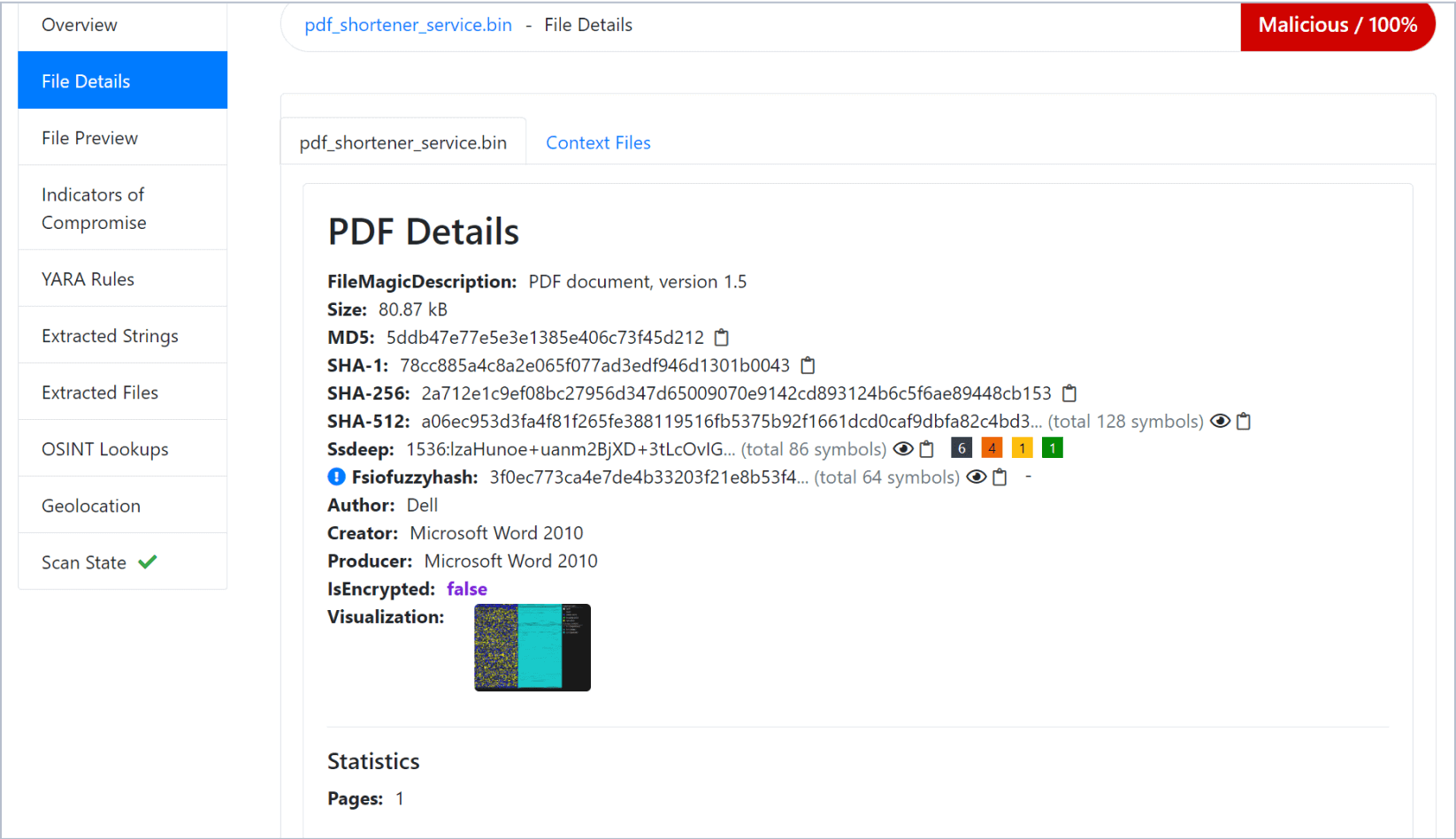
File Parsers
The new File Parsers provide detailed file information, helping to identify and isolate potentially harmful files quickly.
File Certificate Validation
Additionally, File Certificate Validation ensures that only legitimate and approved files run on your network.
Image Text Analysis
Image Text Analysis feature uses Optical Character Recognition (OCR) technology to analyze images and detect any malicious text within them. This feature helps identify text-based threats that could otherwise go unnoticed by traditional security measures.
Reputation Services
Reputation Services is a critical component of OPSWAT's MetaDefender new Sandboxing features, providing advanced threat intelligence to protect organizations against cyberattacks.
Fuzzy Hash Lookup
One of the key features of Reputation Services is fuzzy hash lookup, which allows MetaDefender to compare the digital "fingerprint" of files against known malware hashes.
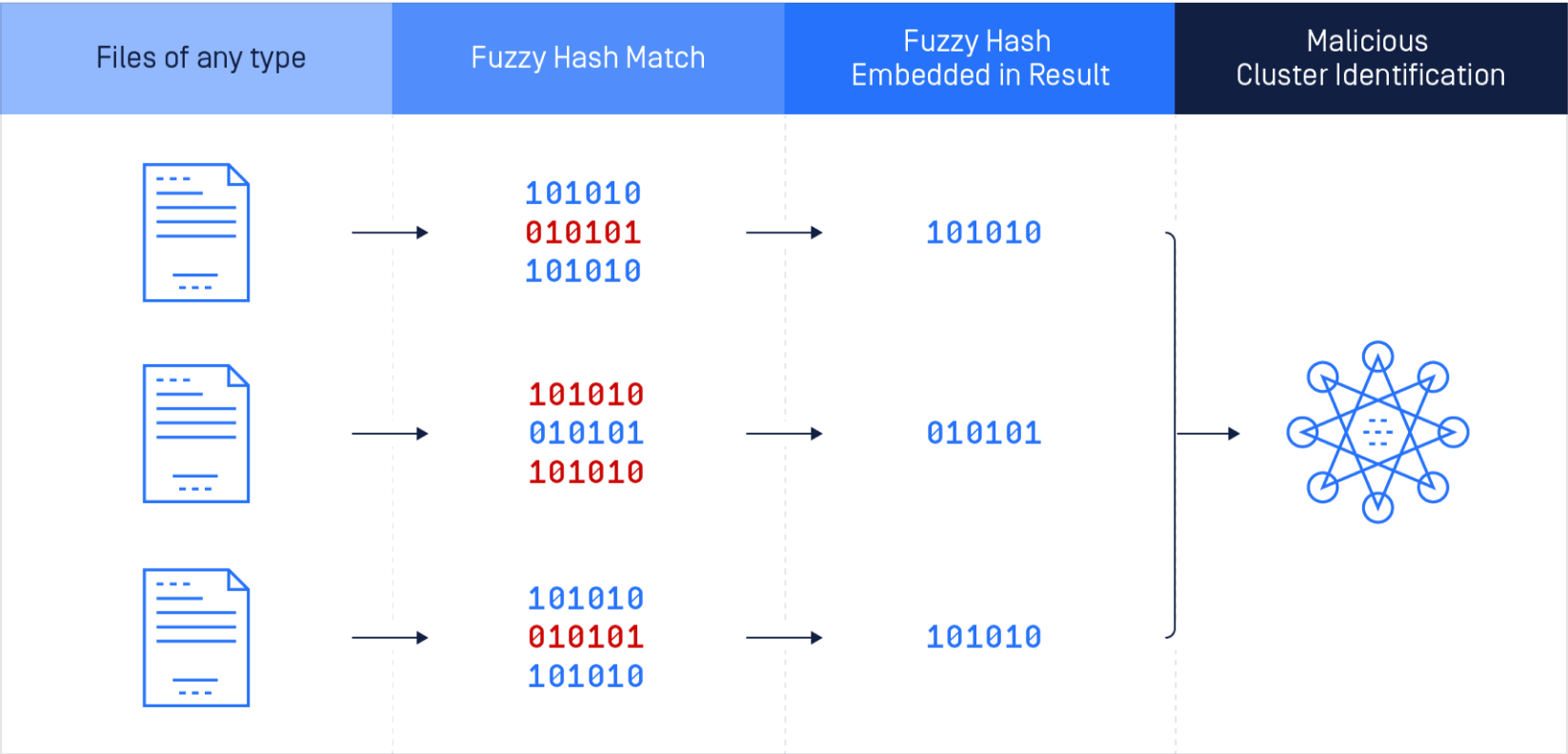
This enables the system to identify and block malicious files, even if they have been slightly modified to evade detection by traditional signature-based antivirus software.
With fuzzy hash lookup, MetaDefender can quickly and accurately identify and quarantine suspicious files, keeping your organization's network and data safe from cyber threats.
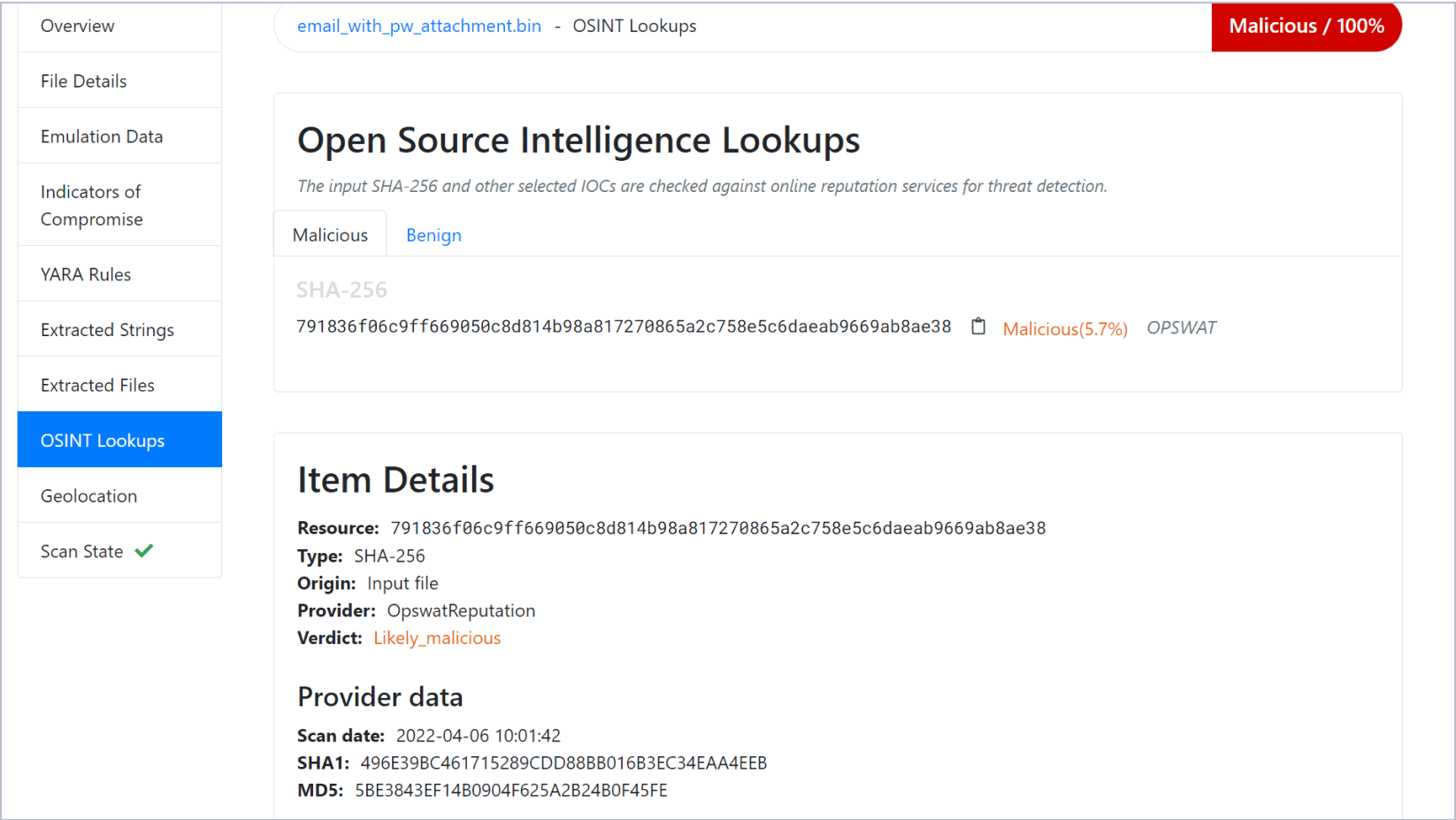
OPSWAT Reputation Lookup
OPSWAT Reputation Lookup provides a score for the file's reputation based on the analysis of our file reputation database with over 40 billion hashes.
This feature is built into the Filescan Remote Engine and is available to Embedded Engine users with an active MetaDefender Cloud license and enabled Threat Intelligence module.
YARA Signature Matcher
The YARA Signature Matcher is a powerful feature of OPSWAT's MetaDefender that uses custom rules to detect and identify malicious files.
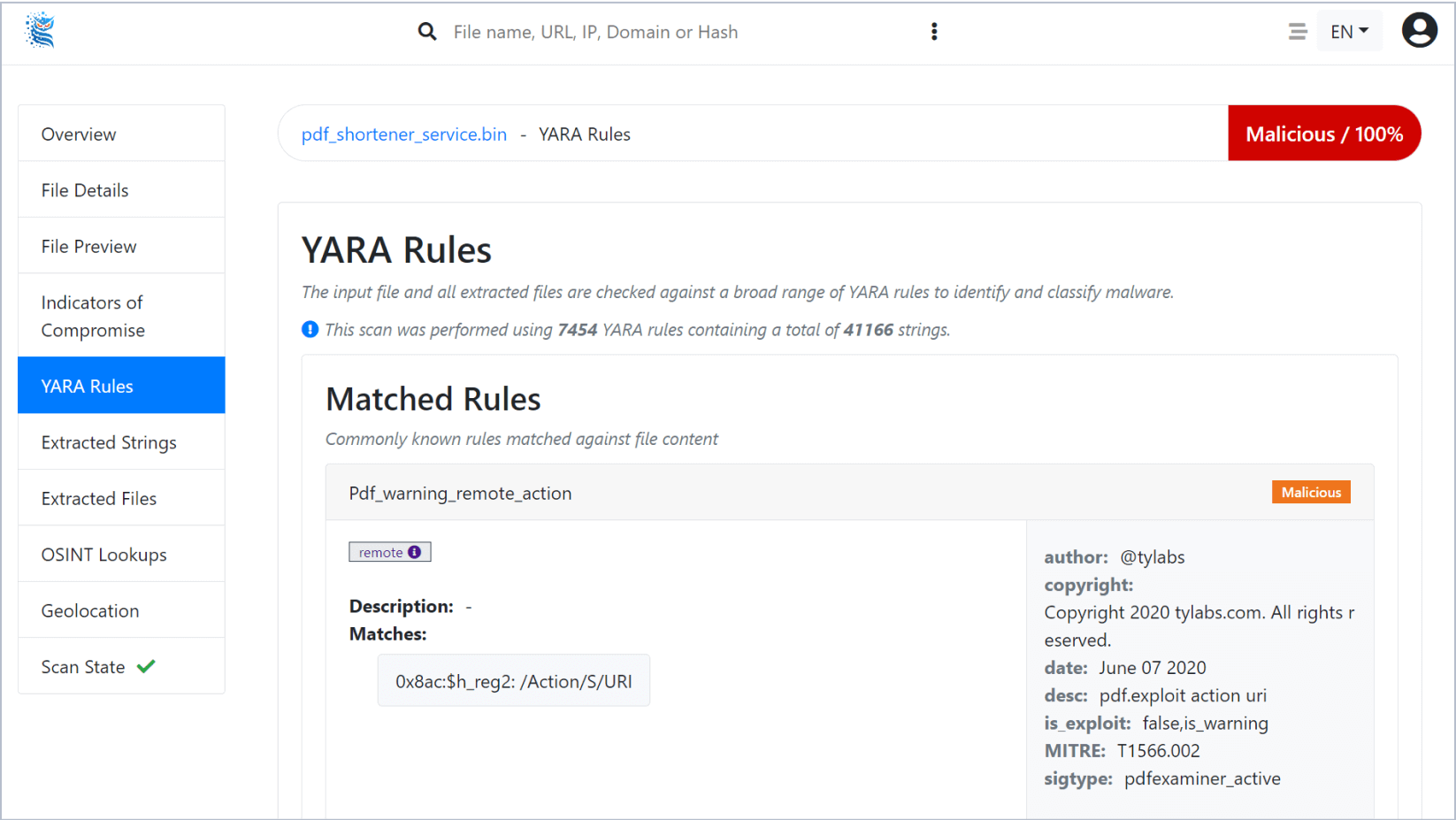
YARA is a flexible pattern matching tool that can be used to create custom rules for identifying specific types of malware. With the YARA Signature Matcher, MetaDefender can quickly and accurately detect, and block known threats, as well as identify new and emerging threats.
Benefits: Powerful, Fast, Efficient, Dynamic Analysis Technology
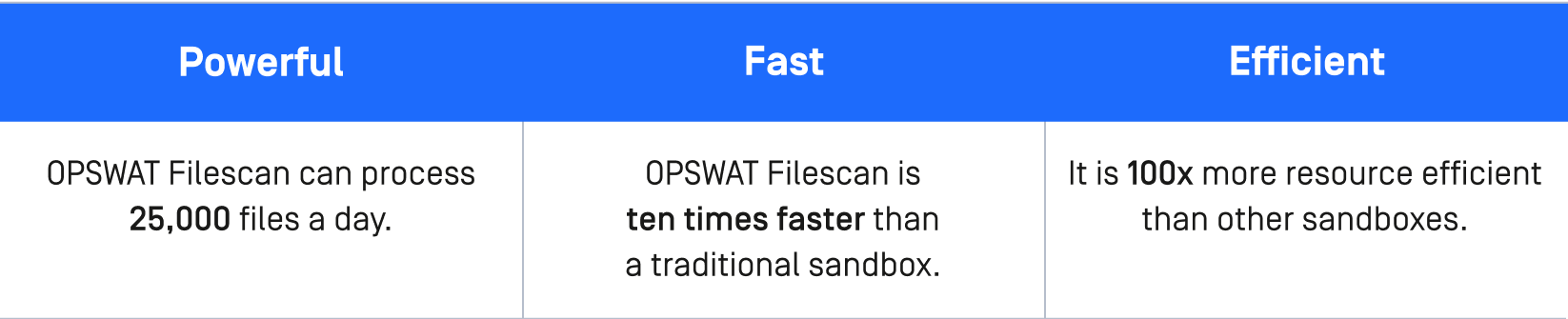
MetaDefender Sandbox is both easy to set up and efficient in its resource usage. In under an hour, MetaDefender Sandbox is up and running to help protect you from malware. Learn more about the technical details here.
Deployment Options
With MetaDefender, you can access Filescan’s fast, dynamic malware analysis both on-premises and in the cloud. For more information on the remote engine deployment, please see the MetaDefender Sandbox datasheet.
Other Enhancements and Updates
For more information, please visit opswat.com/products/metadefender/core or contact our critical infrastructure cybersecurity experts for assistance.
Release Details
Product: MetaDefender Core
Release Date: 7 April 2023
Release Notes: 5.5.0
Download Link on OPSWAT Portal: Download

