The 2024 Osterman Global Email Security Report is designed to alert critical infrastructure security teams of key threats and trends that shaped the 2023 email threat landscape.
The report examines how organizations are tackling email security threats, including vulnerabilities in their current defenses, the adoption of advanced security technologies, and the impact of evolving threats on critical infrastructure. It provides insights into best practices, compliance challenges, and recommendations for improving email security posture. It also highlights actionable steps organizations can take to strengthen their defenses in the year ahead.
Let’s explore the four main areas the report addresses, and which technologies can solve the challenges and security gaps you may be experiencing in your organization.
Vulnerabilities and Breaches
The alarming figure that 80% of critical infrastructure organizations experienced at least two email-related security breaches last year highlights the prevalence and effectiveness of modern email threats. These threats include phishing, ransomware, and account takeovers.
Critical infrastructure organizations with 5,000+ employees in this research experienced:
- 28 successful phishing incidents per year
- 27 account compromises
- 22 incidents of data leakage—among other types of email security breaches
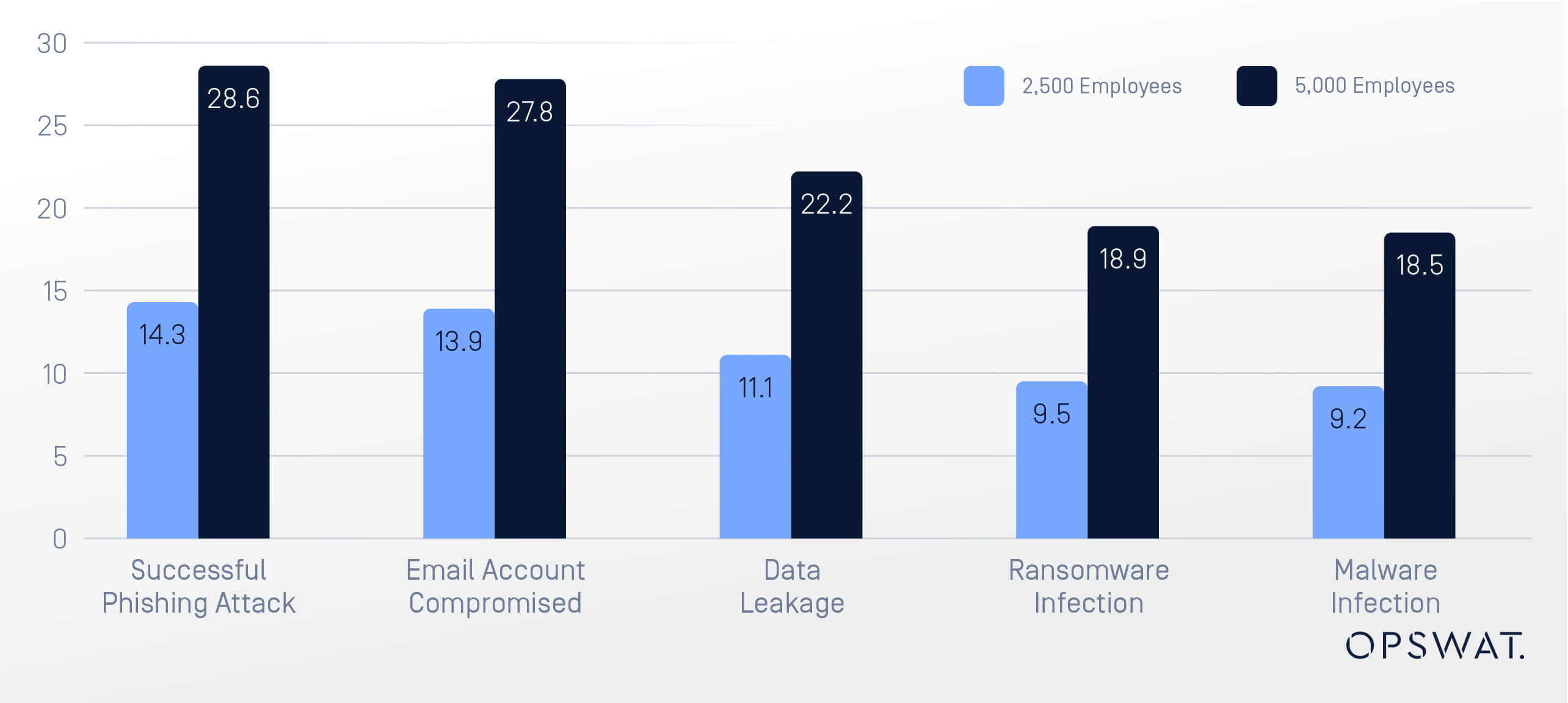
These latest statistics underscore the increasing sophistication of email threats, many of which bypass traditional security measures, resulting in significant operational disruptions and data loss.
It’s also important to point out here that employee training cannot be fully relied upon, as phishing awareness programs often focus on known methods, while cybercriminals continuously evolve their tactics with unexpected approaches.
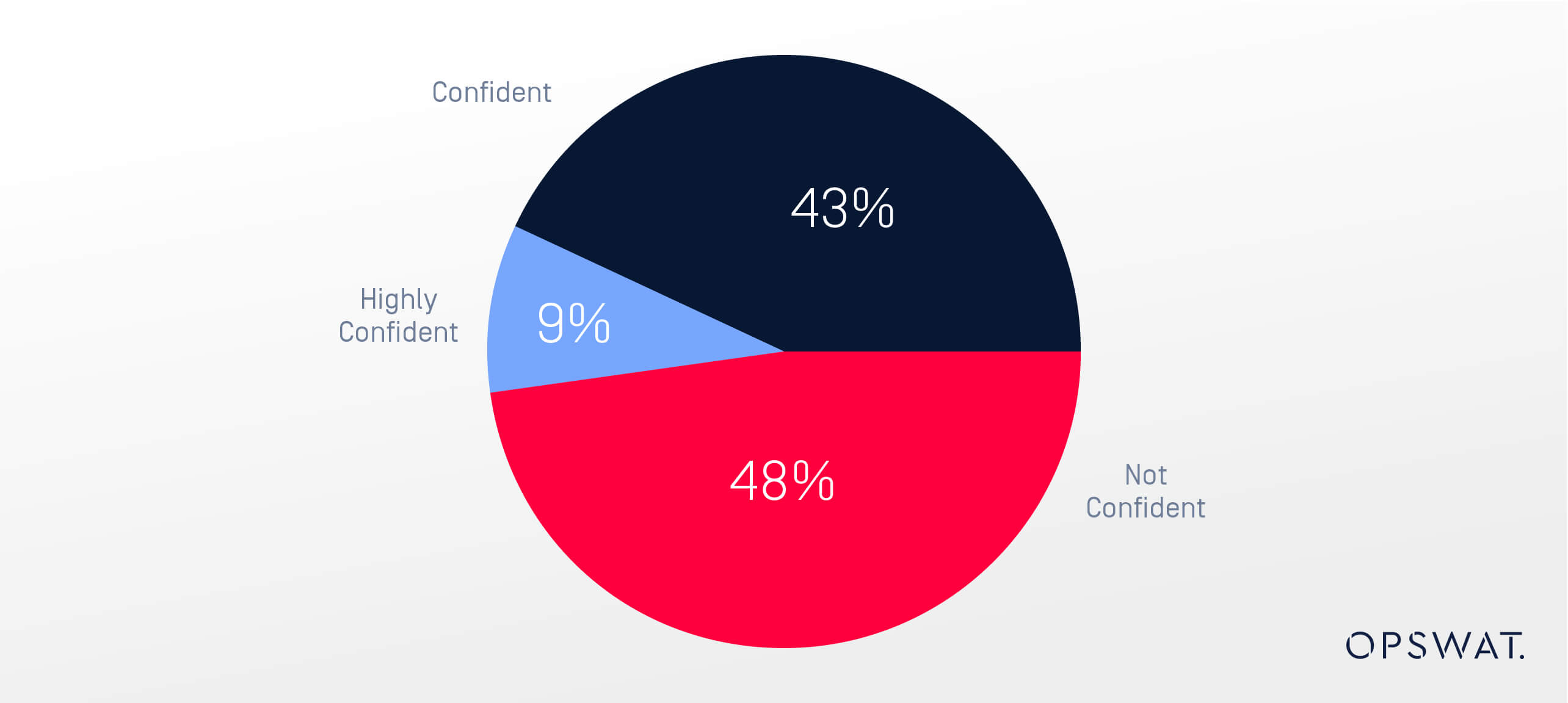
Confidence in Email Security
48% of critical infrastructure organizations reported lacking confidence in their ability to prevent email-based attacks. As almost half of organizations struggle to confidently address security gaps, it means their solutions are either inadequate, they don’t know how to leverage the features or none of the vendors they currently use are comprehensive enough.
More than 63% acknowledged that their email security measures are not "best in class."
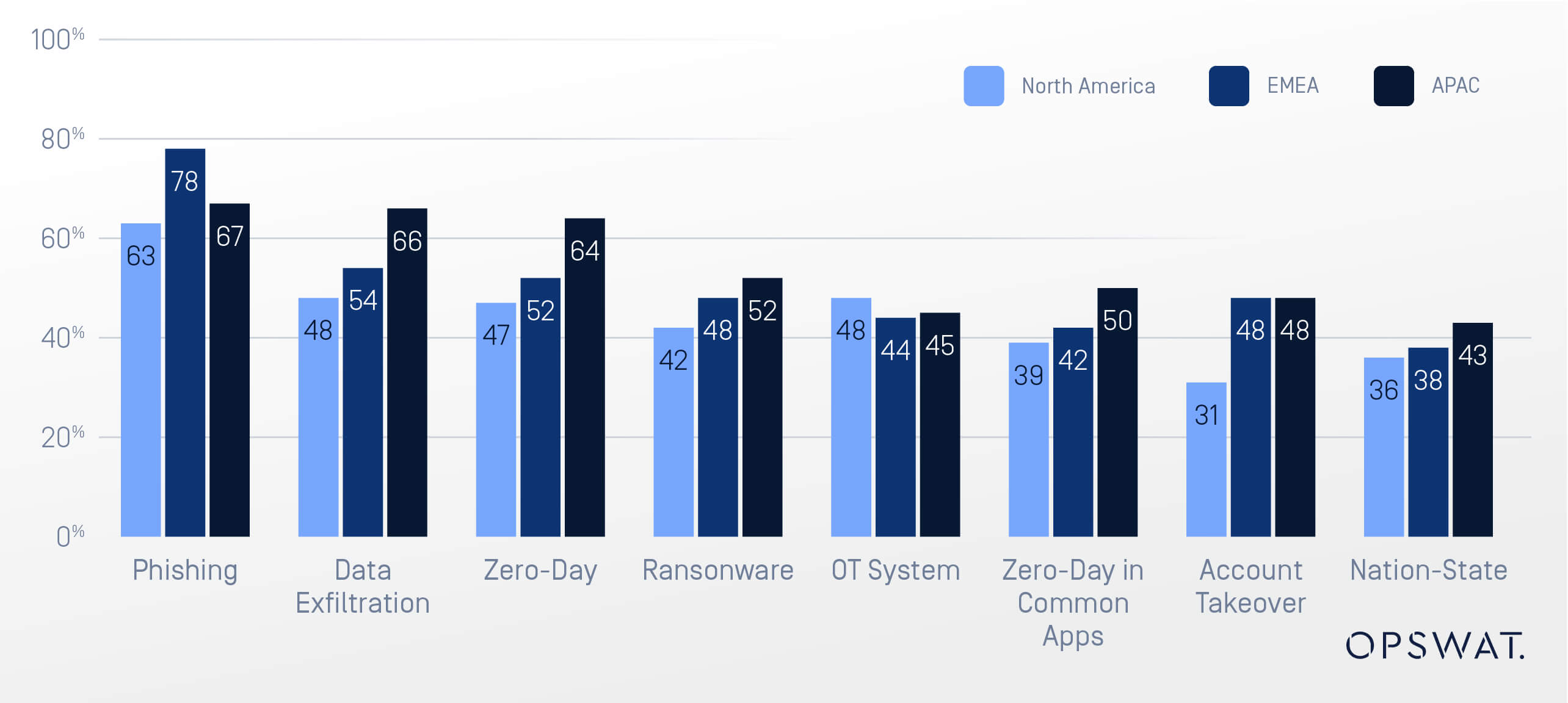
Email Threats Expected to Increase
The threat landscape shows no signs of slowing down. Over 80% of respondents expect the frequency and severity of email-based attacks to remain the same or increase over the next 12 months. Phishing, zero-day malware, and data exfiltration top the list of anticipated attack vectors, reinforcing the need for proactive measures.
On average, 50% of organizations believe the threats posed by multiple email threat vectors will increase over the next 12 months, according to Osterman Research.
The Osterman Report
Necessity of a Multi-Layered Approach
As 75% of cybersecurity threats targeting organizations via email, a more effective multilayered approach to email security is essential. With multiple defense layers, organizations can bolster their email security stack to gain comprehensive email security beyond just relying on native or built-in defenses. Moreover, the report advocates for adopting zero-trust principles and advanced threat-prevention technologies, such as behavioral AI and Content Disarm and Reconstruction (CDR), to stay ahead of attackers.
Proactive Defense Layers
To defend against the evolving email-based threats, OPSWAT offers a range of advanced email security technologies designed to prevent attacks before they reach users.
As the #1 market leader in Deep Content Disarm and Reconstruction (CDR) and Multiscanning technologies, OPSWAT sets the standard for comprehensive email security.
Multiscanning
Leverages multiple anti-malware engines, achieving malware detection rates of up to 99.2%. This layer of defense protects against both known and unknown threats, making it critical for defending against evolving and sophisticated email attacks.
Deep Content Disarm and Reconstruction (CDR)
Proactively sanitizes files by removing potentially harmful code and reconstructing them in a secure format. As 48% of critical infrastructure organizations lack confidence in their current email security stack, OPSWAT’s CDR delivers crucial defense against zero-day file-based attacks and advanced threats that evade traditional detection methods.
Real-Time Sandbox
Analyzes suspicious files in an isolated environment, enabling secure execution and assessment of potentially harmful attachments. Given that 75% of cyber threats targeting critical infrastructure arrive via email, this dynamic analysis adds an important layer of security.
Proactive Data Loss Prevention (DLP)
Protects against unauthorized data exfiltration and ensures compliance with regulatory requirements. With only 34.4% of organizations fully compliant with email security regulations, OPSWAT mitigates the risk of data breaches by preventing sensitive information from leaving the organization.
In Summary
The 2024 Osterman Report informs IT security leaders in critical infrastructure organizations about important questions to consider and how to strengthen their email security posture. As email threats continue to evolve, a multi-layered approach will boost security measures will be essential to safeguard the critical infrastructures we rely on.
Additional Resources
- Download the Osterman Report
- Learn more about MetaDefender Email Security
- Discover more about Multiscanning and Deep CDR

