In late June 2025, Cisco disclosed two critical remote code execution vulnerabilities: CVE-2025-20281 and CVE-2025-20282. These vulnerabilities affect its ISE (Identity Services Engine) and ISE-PIC (Passive Identity Connector). Both vulnerabilities carry a maximum CVSS score of 10.0 and, if exploited, could allow remote, unauthenticated attackers to execute arbitrary code with root privileges.
While both vulnerabilities pose significant risk, CVE-2025-20282 is especially notable for its reliance on a commonly overlooked threat vector: file uploads.
CVE-2025-20282: What You Need to Know
CVE-2025-20282 impacts Cisco ISE and ISE-PIC 3.4, allowing unauthenticated remote attackers to upload arbitrary files to an affected device and then execute them with elevated privileges. The root cause? A lack of file validation checks during the upload process.
According to Cisco’s advisory:
“A successful exploit could allow the attacker to store malicious files on the affected system and then execute arbitrary code or obtain root privileges on the system.”
Unlike CVE-2025-20281, which stems from improper API request validation, CVE-2025-20282 is a classic example of improper file input handling, which is a critical security gap that can be mitigated through well-established file upload security practices.
OWASP’s File Upload Guide Emphasizes File Validation
The OWASP File Upload Cheat Sheet has long emphasized the importance of validating files before they’re allowed into any environment. Core recommendations include:
- Validating file types and extensions
- Scanning for file-borne malware
- Restricting upload locations
- Implementing CDR (Content Disarm & Reconstruction)
In the case of CVE-2025-20282, not enforcing proper file validation allowed attackers to place malicious files in privileged directories, effectively bypassing basic safeguards.
This is exactly the kind of risk that OPSWAT’s MetaDefender Platform is built to stop.
Enforce File Security Best Practices with OPSWAT MetaDefender®
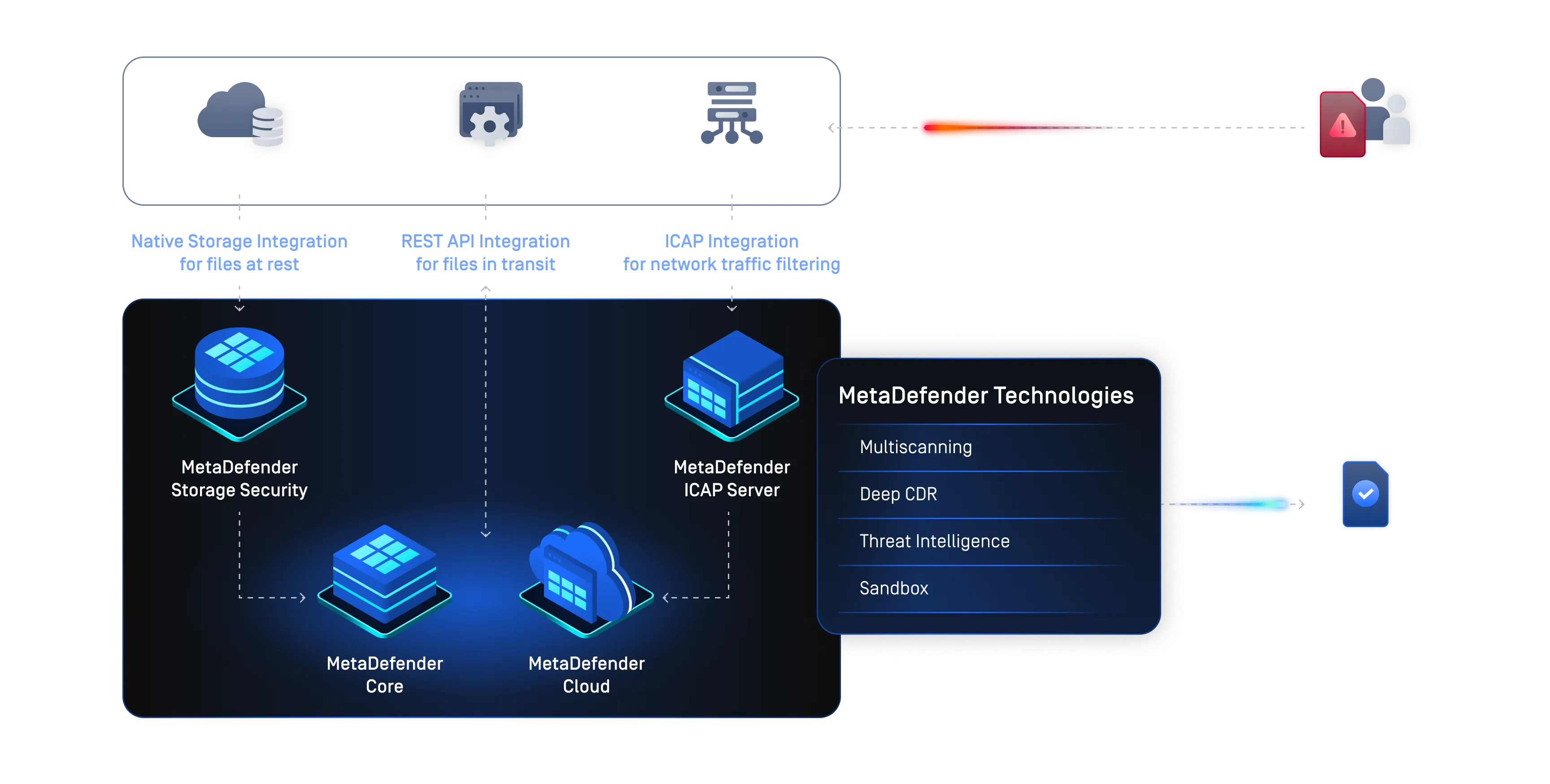
The MetaDefender for File Security solution, when strategically deployed at file upload and transfer points, prevents zero-day vulnerabilities like CVE-2025-20282 from being exploited by stopping malicious files before they reach the target system.
MetaDefender for File Security is powered by industry-leading, multi-layered technologies including:
- Metascan™ Multiscanning: Scans files using 30+ anti-malware engines
- File Type Verification: Confirms the true file type, regardless of extension
- File-Based Vulnerability Assessment: Detect application vulnerabilities before they are installed
- SBOM: Identifies files and source code containing components with known CVEs
- Policy Enforcement: Automatically blocks or quarantines files that fail inspection
Use Case: File Upload Security

When MetaDefender for File Security is placed in front of a file upload workflow (like Cisco ISE’s web-based interface), it ensures:
- Files are scanned and validated before they’re accepted
- Unknown or unauthorized file types are blocked to prevent spoofing
- Malicious payloads are detected and removed
- PII (Personally Identifiable Information) and sensitive data are detected using AI-powered models, then blocked or redacted
- Security policies are enforced consistently
Whether files are uploaded manually by users or via automated systems, OPSWAT eliminates the gap that CVE-2025-20282 exploits, validating the file before the system ever sees it.
Patch and Prevent
Cisco has released patches for both vulnerabilities:
- CVE-2025-20281: Fixed in ISE 3.3 Patch 6 and 3.4 Patch 2
- CVE-2025-20282: Fixed in ISE 3.4 Patch 2
While there is currently no evidence of active exploitation, the risk remains high. Organizations using Cisco ISE should immediately apply patches and consider how secure their file upload workflows truly are.
With CVSS 10.0 vulnerabilities now linked to file upload mechanisms, it’s clear: malware scanning alone is not enough, and file validation is non-negotiable.
File Validation Is Not Optional
CVE-2025-20282 isn’t just a Cisco problem. It’s a reminder that any system accepting file uploads is a potential target.
By implementing a file upload defense layer that combines malware scanning with file extension validation like MetaDefender for File Security, organizations can close this gap with:
- Pre-upload scanning: Protect against malicious files at the perimeter
- Multi-layered file analysis: Provides extensive threat detection and prevention
- Zero-trust enforcement at the file level: Prevent unsafe content from entering organizations’ environments
If you’re looking to harden your infrastructure against the next zero-day attack, or prevent exploitation of known vulnerabilities, start with file security.
Learn more about how OPSWAT MetaDefender for File Security protects file upload, transfer, and storage workflows and get tailored solutions for your organization.

