Since the 20th century, the Made in America moniker has been associated with higher quality goods when compared to imported alternatives, at least when these goods are targeted at the American consumer. For manufactured or assembled products, it's hard to know when this label indicates that the product was actually made in the United States. For cyber-attacks, which carry no label, it's even more difficult to track their origin. This happens for many reasons, the most obvious one being this: Cybercriminals strive to remain anonymous, and their 'products' rarely carry telltale signs of their origin.
The topic of geolocating cybercriminals has been elevated to international politics with the Obama administration's decision to impose sanctions on North Korea in response to the Sony Pictures hacking incident. Hopefully, the FBI's assessment is accurate, because as recent as February 4th, it is still unclear that North Korea was the sole culprit.
Arkady Bukh recently published a story on the geography of cybercrime. In the article he points to the Enigma Software study that ranks the USA as #1 in multiple categories: Share of malicious computer activity, malicious code rank, phishing websites hosted, attack origin rank. Unfortunately, the site does not say when or how often the report is updated. It's interesting to note that most people, even those in the cybersecurity field, would not correctly guess the rest of the list (aside from China at #2). One metric not available in the report is the financial impact of these crimes.
As noted Mr. Bukh, Russia comes in at only #12 on this list but is well known to be the source of some of the highest quality and most costly cybercrimes in history. In 2013, Reuters produced a similar piece on the topic, reaching some of the same conclusions.
It's very interesting to compare these cybercrime statistics with a geographic distribution of antivirus vendors:
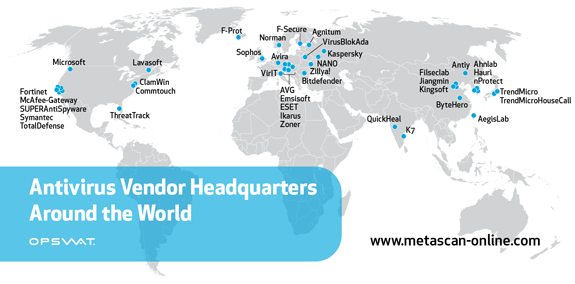
Click to enlarge and to see vendor names.
The highest density of antivirus vendors is in the former USSR, China, and the USA. In general, these groupings align with the geographic sources of malware. One could assume that the conditions that foster the creation of malware may also foster the growth of anti-malware companies.
To maximize their protection, consumers and businesses should take advantage of antivirus scanning from at least three main geographic regions. Scanning high-risk files with an anti-malware engine from the USA, Russia or Eastern Europe, and from China can provide increased rate of detection especially for new or unknown malware. This is due in part to the nature of signature-based detection and whether malware sample sharing between anti-malware companies takes place.
OPSWAT offers multiple free products that make this type of scanning easy. Metascan Online can be used for scanning files on demand and is also available as a browser plugin. Gears, for Windows and Mac, is a tool that uses Metascan Online to perform a quick daily system scan. Gears is free for up to 25 devices.

