March was a very busy month for the Gears team. We had three releases: Des Moines, Missouri, and now Arkansas! Although we speculated there would be only two releases in March, we ended up finding time for a third! An interesting fact about Arkansas is that like California, it contains a city named Mountain View. Though, instead of being home to Google, the Arkansas edition of Mountain View is home to one of the largest producers of handmade dulcimers in the world [1].
Released in March:
- Exempting Devices
- Open API for Device Management
- Data Retention Controls
- Lost/Unseen Devices
- Applications Blocklisting
- Windows XP Support Returns
- Improved VM detection
- Bug fixes and performance enhancements
Exempting Devices
Making exceptions is, unfortunately, a normal part of IT and security operations. And while it may be considered a last-resort, there should still be an elegant way of handling it. With this in mind, we've created a straightforward policy exemption mechanism for Gears devices.
Additionally, because exempt devices can potentially create security holes in your network, we've made it easy to audit exemption events, find exempt devices, and reverse the exemption.
While in an exempt state, devices will respond to the registry API and REST API as if they were compliant. Despite this, all compliance issues will continue to be reported in the device details and API detailed responses.
Exempting a device from Gears policy
Devices can be exempted in the Gears cloud UI, or by using the Gears cloud APIs. To exempt a device using the Gears management UI, the process is simple:
- Log into Gears cloud
- Open the details page for a non-complaint device
- Find the 'Exempt' button in the top-right
- Choose to exempt the device from all issues or critical issues only
The devices_action API can be used for programmatically managing device exemption state.
Reversing an exemption
- Log into Gears cloud
- Open the details page for an exempt device
- Find the 'Exempt' button in the top-right
- Choose to Unexempt the device
Finding exempt devices
In the device list view, an exempt device will be highlighted with a

symbol. Filters can also be used to show only exempt devices.
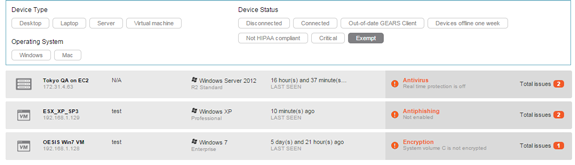
Filtered list of exempt devices (Click to enlarge)
Correspondingly, the Gears REST API is updated with a new key, "exempt" in the devices and device detail methods.
Audit log for tracking exemptions
Gears allows multiple administrators to manage a single account, so it's important that administrators can track actions taken by each other. To this point, exemption actions have been added to the Administrator Events section of the event log.
Any actions taken to exempt or unexempt a device will appear in this log, along with the name of the logged-in administrator who performed the action. For better visibility, two new filters are provided as well.
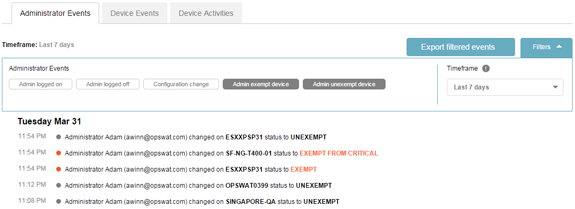
Audit log of exemption events (Click to enlarge)
Remediation page
To prevent any user confusion, a new remediation page state was created to clearly communicate to users that they have issues but are temporarily exempted by the administrator. Like the rest of the remediation page, the messaging can be fully customized in the WYSIWYG editor.
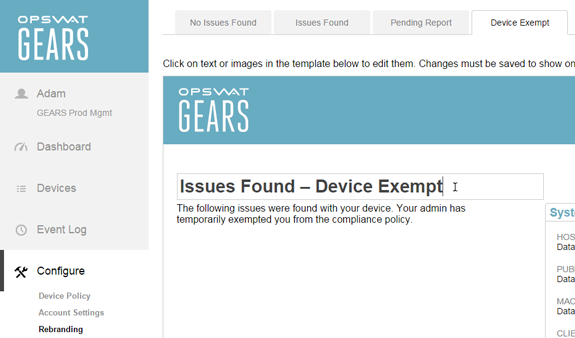
Editing text of the Exempt state remediation page
Open API for Device Management
Gears is a security platform, not just a service. This philosophy is evident in our technical partnerships with leading security applications and appliances. OPSWAT certifies security applications in 15 different categories, for over 1500 products. Additionally, Gears integrates with SSL-VPN and NAC products from industry leaders such as Pulse Secure, Cisco, SonicWALL, Portnox, PacketFence and others. Additionally, we provide a set of robust Open APIs for integration with the Gears cloud.
Today we have taken our platform philosophy to the next level. We are officially releasing the first version of Gears Open API for device management. This commitment to openness will enable the Gears community to grow and benefit from collaboration and customization.
These APIs are designed for developers to quickly, easily, and freely (as in beer) create their own custom agent to work with the Gears cloud. With clear documentation and free accounts up to 25 devices, any developer should be able to quickly create their own custom agent.
Gears Devices API (Click to enlarge)
This initial set of API methods provides a base level of functionality that will continue to grow as we receive feedback and add new methods over time. This initial set consists of 6 core API methods.
- Register a Device
- Delete a Device
- Get Device Details
- Update Device Details
- Send Device Heartbeat
- Send Custom Report
Authenticating to use the new device APIs is documented separately. It is designed for ease of use without sacrificing security. In general, the authentication requires the following steps:
- Create a free Gears account at www.opswatgears.com
- Log in and go to the Account Settings page
- Create an Access Token for a group of agents (see screenshots below)
- Configure the agent to pass this Access Token when calling the registration API
- Programmatically retrieve the Access Key for an individual device given in the response to the registration API
- Provide the Access Token and Access Key in all additional API calls
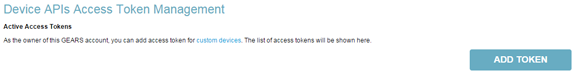
Token creation step 1: Creating a device access token (Click to enlarge)

Token creation step 2: Entering a tag for this access token
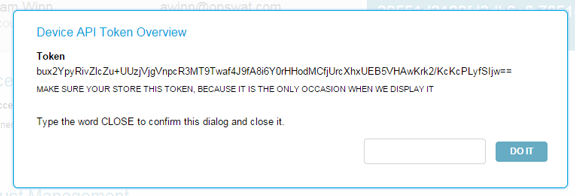
Token creation step 3: The generated access token
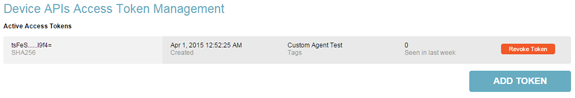
Access token added to list (Click to enlarge)
Access to the Open API for Devices is available now. Look for additional features and methods to be added continually.
Data Retention Controls
Adding and removing devices is a normal (and sometimes hectic) part of managing a network. We understand this and strive to make Gears as easy as possible for users to onboard themselves (account associations are embedded in the installer) to minimize the burden on IT. Additionally, if a user uninstalls Gears, we will automatically detect the event and remove the device from the account. With all of these devices coming and going, it can introduce noise into management logs. This situation doesn't apply to everyone, but when it does it can be frustrating. To that point, we have introduced an adjustable data retention mechanism for device deletion.
Gears users can adjust the default behavior for log retention when a device is deleted. The default behavior is 'Archive', in which a deleted device's logs are stored in Gears cloud for the duration of the data retention period (30 days for standard accounts). The alternative option is 'Purge' mode, where a device deletion event causes all related log files in Gears cloud to be wiped out.
For the most flexibility, this setting is adjustable separately for managed and guest devices.
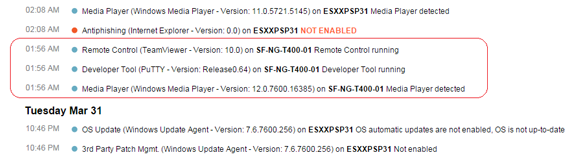
(1) Logs for device 'SF-NG-T400-01' before deletion (Click to enlarge)

(2) Setting the retention mode to 'purge'

(3) User deletes the device and a record is created in the Device Events log (Click to enlarge)
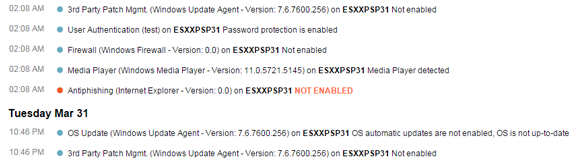
(4) Entries for SF-NG-T400-01 are retroactively removed from the Device Activities log (Click to enlarge)
In addition to providing these controls for log retention, we now display each account's Data Retention Length value. The default is 30 days for all accounts (free and paid), with increased durations available as an upgrade.
Lost Device Cleanup
If you have an existing Gears account, you may have noticed your device count decreased on March 31st. No need to panic. This decrease is the result of our newly released Lost Device cleanup feature. While perhaps unnerving at first, it's actually a long awaited request from many of our oldest users that we believe will be beneficial for everyone using Gears. In short we now automatically cleanup any devices which have not been seen in a certain amount of time. The default duration is equal to your data retention length (typically 30 days). Controls are provided to shorten this window to 1, 7, or 14 days, configurable separately for managed and guest devices.
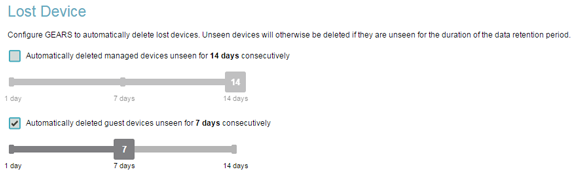
Unseen duration is configurable separately for guest and managed devices (Click to enlarge)
When a device is cleaned-up, it will free up a license token so that you aren't consuming license tokens for inactive devices. Unlike our typical 'delete' command, these devices will not automatically uninstall their Gears agent, so presuming they come online again in the future they will automatically be repaired with your account and show up in the device list.
When a device is removed by this feature, the retention of log files will respect your choice of 'purge' or 'archive' mode.
Application Blocklisting (beta)
With the innumerable amount of applications available for users to install on their system (knowingly or not), it is critical that IT and security groups have visibility and control. Concerns like Shadow IT, riskware, grayware, potentially unwanted applications, and potentially unsafe applications are very real and can increase the chances of a breach, infection or other harmful event.
Prior to now, Gears had a feature for detecting and restricting the use of public file sharing software (typically peer-to-peer / torrent). Our new application controls have not reduced that functionality at all — rather they are an expansion of the same concept applied to many other categories of software.
Usage is simple. Log in to Gears and go to the Device Policy page, you will then see a list of software categories. For each category you can report if it's installed or running, and remediate with automatic uninstallation or process killing.
Reporting
Gears, using the OESIS Framework, rapidly detects and categorizes installed applications on the system, as well as observing which are actively running. This information is encrypted and sent to Gears cloud where it is added to the database for that device. You then set your Unwanted Application policy to match certain application categories, and whether you care if they are simply installed or running, or both. Additionally you can mark these items as critical issues for finer control over secure access integrations.
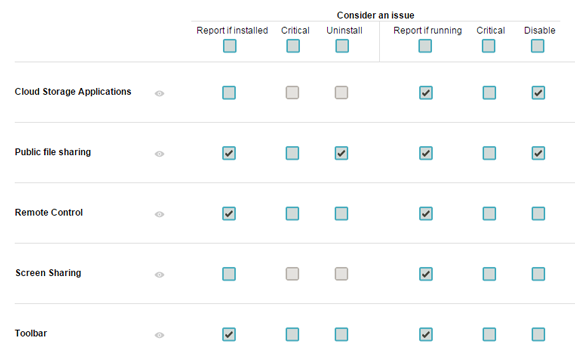
Unseen duration is configurable separately for guest and managed devices (Click to enlarge)
After configuring the device policy, additional issue categories will appear in the dashboard and device views.
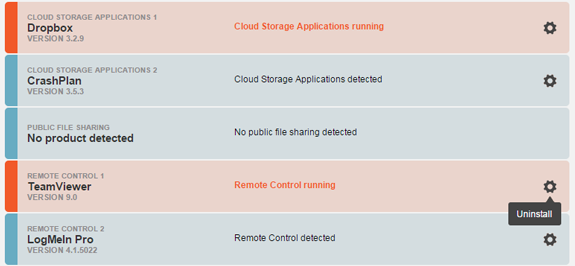
Applications in orange are issues. Blue are compliant. Manually-triggered Uninstall is available (Click to enlarge)
The remediation page is updated for each category of unwanted software. Note that in the current release, the remediation page will not show an issue if the application is running, only if it is installed. This will be added in the next update.
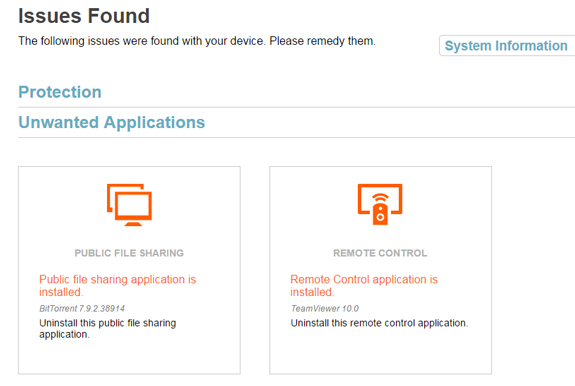
The remediation page provides clear instructions to the user (Click to enlarge)
This new feature is labeled beta, but it is fully tested and ready for production use. We have only decided to label it as beta because additional capabilities will be added in the next few releases. Expect to see granular per-application controls, as well as powerful searching and filtering added very soon.
Windows XP Support Returns
Perhaps better known as the OS that will not die, Windows XP continues to show a strong market-share. We strongly discourage the use of Windows XP since Microsoft discontinued issuing security updates. For this reason, if users cannot upgrade their system it is imperative that their security configuration is otherwise as strong as possible — including anti-malware protection, antiphishing protection, personal firewall, etc.
Gears will only run on an installation of Windows XP with all available Windows updates installed.
Improved VM Detection
Gears allows device policies to be customized per device type. Among those devices types is virtual machine. In this release, we have dramatically improved our VM detection algorithm. We now reliably detect VMs using any number of different hypervisors, including VMWare, Xen, Parallels, etc.
This feature is most popular for users who wish to provide exemptions for policies such as disk encryption for virtual machines.
The Other Stuff
- To make the critical issue feature more useful, we've added a 'critical issue' filter to the device list
- The Windows installer size has been reduced by 1.5MB, and the Gears.exe memory usage is decreased by up to 10MB
- Bug fixes and stability improvements all around

