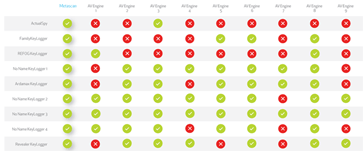
The detection of advanced threats and all of the inherent complexities continues to be heavily featured in the media (see here and here).The definition of an advanced threat varies depending on who is doing the talking, but typically it entails malware that actively takes steps to evade detection, whether through self-modification or by inserting itself into otherwise innocuous files or processes. Advanced threats are typically targeted at specific individuals or organizations, and can leverage a wide range of assets for entry, including: servers, user devices, kiosks, networks, or people.
Why Focus on Advanced Threats?
 The malware landscape continues to evolve over time as the arms race continues between virus writers and anti-malware software vendors. Every new advance by either side triggers a response by the opposing side. As a result, both malware and the software to detect and eliminate malware have become increasingly sophisticated. There has also been a shift in the goals of the people who are producing malware. In the past, many virus writers were either producing malware for fun or as a hobby, sometimes to demonstrate their skills and other times to make a political or social statement. With these goals in mind, malware was written with the intention of being very noticeable and spreading to as many endpoints as possible.
The malware landscape continues to evolve over time as the arms race continues between virus writers and anti-malware software vendors. Every new advance by either side triggers a response by the opposing side. As a result, both malware and the software to detect and eliminate malware have become increasingly sophisticated. There has also been a shift in the goals of the people who are producing malware. In the past, many virus writers were either producing malware for fun or as a hobby, sometimes to demonstrate their skills and other times to make a political or social statement. With these goals in mind, malware was written with the intention of being very noticeable and spreading to as many endpoints as possible.
In recent years, there has been a lot more malware produced with the aim of generating revenue for the malware writer. The general public, as well as corporations, have become much more dependent on the Internet for their business and day-to-day activities, which has brought great gains to productivity, but has also opened new attack vectors for malware and larger potential rewards to exploiting security vulnerabilities. Since there is much more money to be made, malware production has become much like any other commercial software development. Teams of developers now work on writing malware full time, which means the final product is much more sophisticated than what an individual would previously produce in their spare time. This growth is highlighted in the latest Verizon 2014 Data Breach Investigations Report (DBIR) with the explosion of the hacking and malware categories since 2009.
With more of the world dependent on digital systems, there is also more malware being developed for the purposes of sabotage. This malware can be targeted at specific systems, and can remain undetected on other systems where it does not cause any damage as it waits to be spread to the target systems. Stuxnet is a good example of a virus that was developed to target very specific systems and likely evaded detection in part because it did not attack any systems besides those narrowly targeted.
Although a single anti-malware product can protect individuals and organizations from most of the malware that was written in the past, as well as less sophisticated malware that are still being developed, they do not do as well against the more advanced threats that are circulating today. The sophistication of the malware means that simple hashcode signature matching is unlikely to detect an advanced threat, because the malware is always changing. It is also much less likely that any individual antivirus engine vendor will discover a threat early, because the malware itself is targeted and not as widely spread and some malware even targets specific anti-malware engines to avoid detection. Finally, there is more potential for significant financial costs resulting from the very first time the malware is used against an individual or organization, and signature matching anti-malware detection is not effective against zero-day attacks.
How to Combat Advanced Threats
The best way to detect and prevent advanced threats is to have multiple layers of protection so that even if a single layer is defeated the threat will be stopped by one of the additional layers. This in-depth defense can take several forms such as leveraging multiple products that are performing a similar action, but each in their own unique way. For example, multiple anti-malware software products that scan in concert. This is one of the ways that Metascan tackles the problem of detecting advanced threats. The multiple anti-malware engines within Metascan all have their own ways of detecting malware, and most of them use some sort of heuristic analysis in addition to the signature detection. By scanning with different anti-malware engines that are using their own proprietary heuristics to detect malware it is much less likely that advanced threats will be able to evade detection.
For certain types of files, there is also the option of scanning the files multiple ways. Archive files, as well as many office document types, allow for files to be extracted. For these files, both the original file as well as each extracted file can be scanned utilizing multiple anti-malware engines.
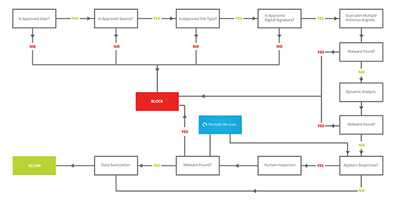
Another method to protect against advanced threats is to have a multi-step workflow where threats can be identified at each step in the process. Files can be flagged as potentially malicious based on their type or properties; and the files can be blocked even if an anti-malware scan comes up clean. Portable executables (PEs) can have their headers scanned for suspicious characteristics, or all executables can be blocked as potentially dangerous. Alternatively, only executables that are digitally signed by a recognized digital certificate can be allowed. Files can also be filtered based on their source, so anything coming from suspicious IP addresses or domains is blocked. In addition to using static analysis, dynamic analysis methods, such as sandboxing, can optionally be used to detect threats. Neither are perfect (see our previous blog post comparing the two) however static and dynamic analysis, utilized in conjunction, can provide an in-depth defense for an organization. Also, since dynamic analysis is usually much more intensive on computing resources than static analysis, the combination of both can be significantly cheaper to implement than dynamic analysis alone.
Even after all detection methods have been exhausted, additional steps can be taken to prevent infection by advanced threats. One method is to strip out embedded objects from files using data sanitization, which eliminates any malware that is embedded in the original file. This ensures that even if all the available detection methods fail malware will still be prevented from getting through an organization’s security defenses.
Below is an example of a data workflow that utilizes multiple layers of security with different detection methods to detect and prevent advanced threats:
In summary, the best way to combat threats that are sophisticated and targeted is by employing multiple methods of detection, making it as difficult as possible for malware to evade detection by all the available methods. Even if an advanced threat is able to get by most of the security layers, it only takes detection by a single anti-malware engine to block the threat, ensuring the entire system remains free of malware.