Emotet, Qakbot, Remote Access Trojan (RAT)—what do they have in common? —They were all delivered through Microsoft Office OneNote files.
When Microsoft disabled macros by default in 2022, attackers shifted to using non-macro-based delivery mechanisms—and the unassuming OneNote file was the perfect substitute.
Are OneNote Files Secure?
OneNote is a popular productivity app in the Microsoft Office suite used by millions of people worldwide. Because of its versatility, OneNote has become a convenient tool for notetaking, information management, and, unfortunately, malware distribution.
OneNote uses a proprietary file type, denoted by the file extension .one, which allows users to format notes with rich text, digital handwriting, and objects, including images and multimedia. Although OneNote files are not malicious, hackers exploit their complexity to deliver malware by embedding malicious commands in the file. These commands can download malware on the user’s device, leading to devastating consequences such as data loss, compromised devices, identity theft, or financial fraud.
OneNote is becoming more popular and accessible, unfortunately people are unaware of the security risks. This lack of awareness makes it easy for attackers to embed malicious commands in OneNote files and trick users into installing malware.
Attack Techniques: OneNote Malware Distribution Campaigns
Threat actors use various social engineering techniques to spread malware using OneNote files. Their ploys usually involve email phishing and disguising a malicious payload under a legitimate OneNote component.
Images
Security researchers identified a campaign in February 2023 that uses a malicious image to distribute the Qakbot (also known as QBot) malware. Attackers tricked users into double-clicking on a design element in the OneNote document. When a target double-clicked the element, an embedded file executed a series of commands that downloaded and installed malware on the target device. This campaign is one example of attackers luring unsuspecting users into downloading malware on their systems through OneNote files.
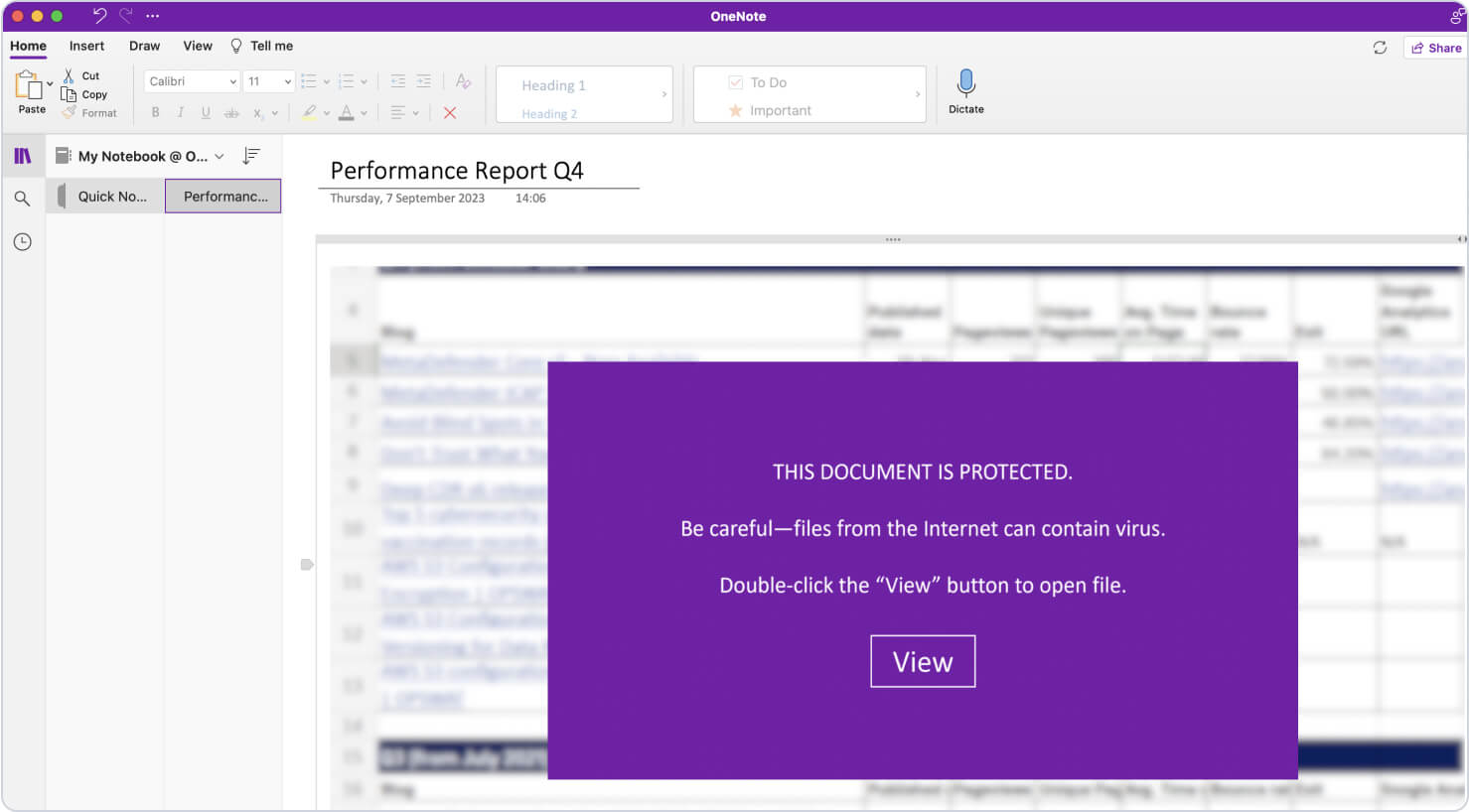
Sample image of how attackers can hide a malicious script under a message in OneNote
Attached files and email phishing campaign
In another campaign, attackers sent reply-chain emails with malicious OneNote attachments disguised as legitimate documents (e.g., guides, invoices, and other documents). Using a similar technique as above, the attacker hid a heavily obfuscated VBScript in these attachments, and when executed, it downloaded and installed the Emotet malware on the victim’s device as a dynamic-link library (DLL). Emotet malware is highly dangerous because it runs quietly on the compromised device, stealing confidential information (emails, contacts) or awaiting commands from the control server, such as downloading additional payloads.
In response to OneNote attacks, Microsoft has blocked users from opening an embedded file with a dangerous extension starting Version 2304 in April 2023. OneNote displays a dialog restricting the user’s ability to open the file, but the user can still open it by clicking “OK”.
Embedded hyperlinks
Besides exploiting attached files, attackers can use URLs, hyperlinks, or images in OneNote files to deliver malware. Their social engineering tactics vary, but the ultimate goal is to have the victim execute a malicious payload.
Prevent OneNote Malware Delivery with Content Disarm and Reconstruction
OPSWAT Deep Content Disarm and Reconstruction (Deep CDR) technology treats every file and file component as potential threats. When dealing with complex files such as OneNote, it is important to ensure there are no malicious components obscured from sight—whether it is a script hidden behind an image, a disguised hyperlink, or malware buried in one of the notebook’s tabs. Learn about all file types that Deep CDR supports.
Deep CDR inspects the OneNote file and any attachments, images, or other components. Then recursively sanitizes them and removes any potentially malicious content. In the same scan, OPSWAT Metascan technology leverages multiple antivirus engines to detect malware inside the file.
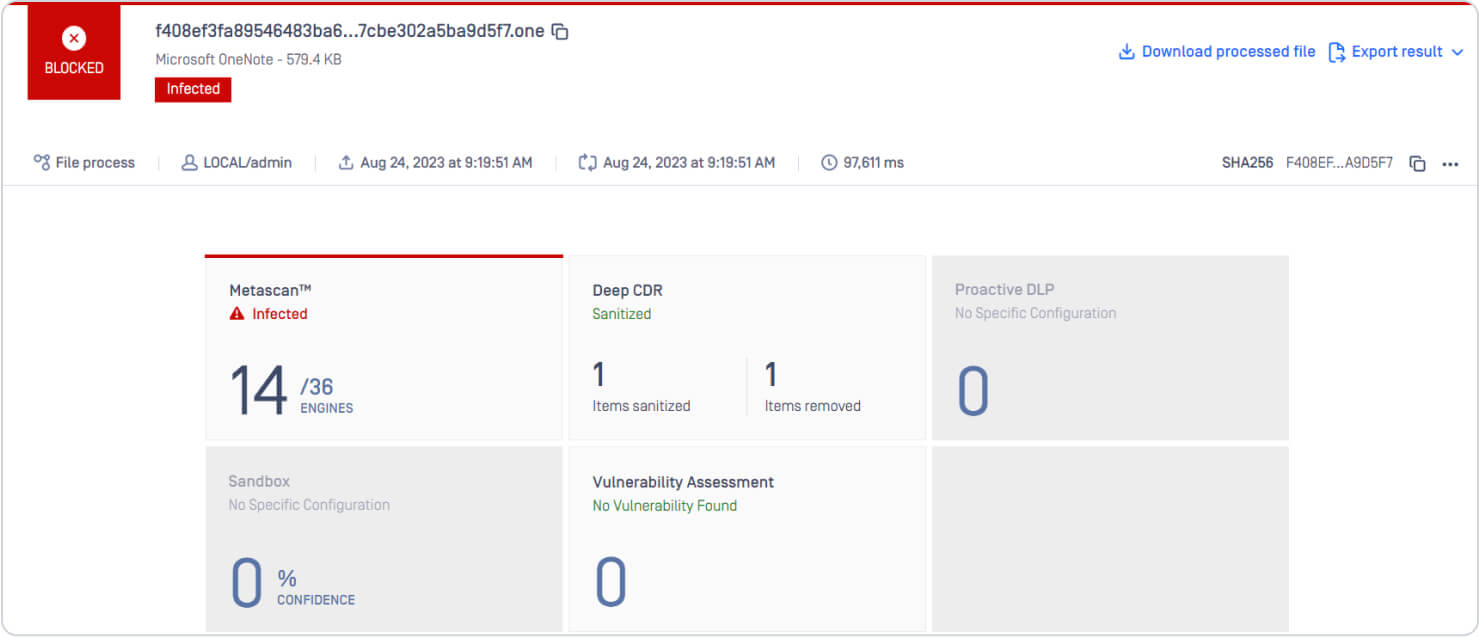
Deep CDR detects malicious object in OneNote file
Finally, Deep CDR regenerates a safe OneNote file, free of malicious objects, while retaining the file’s original functionality. Deep CDR removes all known and unknown threats, leaving the file safe to use.
Below is the MetaDefender Core scan result:
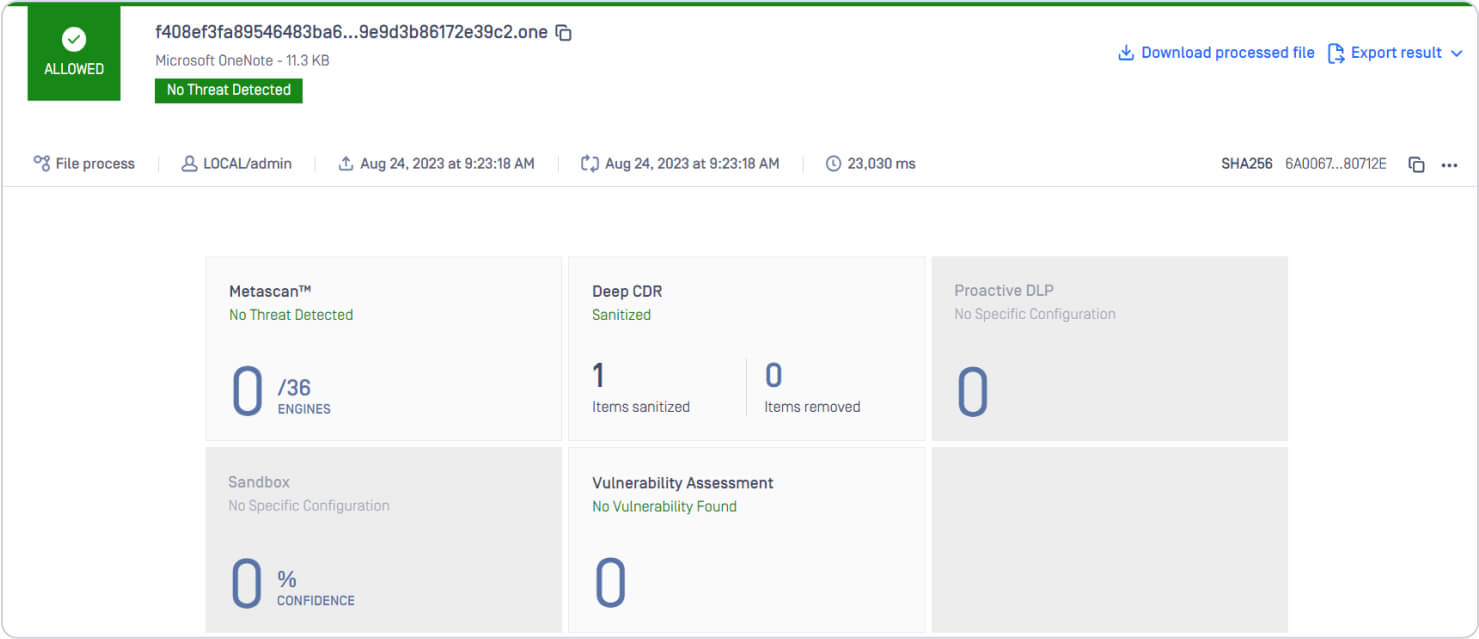
The regenerated file by Deep CDR is safe to use
One Final Note: Best Practices to Safeguard Your Files
To prevent cyberattacks abusing OneNote files, consider implementing the following security measures:
- Exercise caution with emails and attachments: Be cautious when receiving emails with OneNote attachments, especially from unknown or suspicious senders. If the source is unverified or appears suspicious, avoid opening the attachment.
- Keep software updated: Hackers often exploit vulnerabilities in software applications to install malware on devices. Even though Microsoft has constantly enhanced protection against vulnerability exploits, cyber attackers can still target organizations that use older, unpatched software versions. To combat this, keep your operating system, antivirus software, and all relevant applications updated. Regularly applying software updates ensures protects your system against known vulnerabilities.
- Be cautious with links within OneNote files: Similar to email attachments, be cautious when opening links within OneNote files. These links may lead to malicious websites that can infect your device with malware. Only open links from trusted sources and ensure the website you are visiting is legitimate and secure.
- Antivirus protection: Use reputable antivirus software to scan every incoming file for known and unknown malware. To improve efficiency, using multiple antivirus engines will increase the malware detection rates compared to using one single engine. Learn about OPSWAT Multiscanning technology.
- Remove all potentially malicious objects: Security measures such as Deep CDR help organizations protect themselves from advanced and evasive malware technologies, including both known and unknown threats, zero-day threats, and undetectable and obfuscated malware. Treating every file as a potential threat reduces the risk of inadvertently executing harmful code.
To learn more about OPSWAT threat detection and prevention technologies, contact one of our technical experts.

