Application Security
Protect Applications From Advanced Threats
The number and complexity of enterprise applications is growing, expanding your attack surface. Security incidents targeting vulnerabilities in your applications are on the rise. Cybercriminals are increasingly exploiting your legacy web applications, 3rd party open-source software components, productivity documents and files to steal data, intellectual property, and sensitive information.
Prevent Security Issues Across The Application Lifecycle
Application security solutions must provide comprehensive end-to-end protection for your digital ecosystem – during the SDLC, through the agile delivery of the CI/CD pipeline, to the services that manage data in transit and store data at rest, to securing the content in files either uploaded or shared.
OPSWAT Application Security solutions detect malicious payloads, exploitable vulnerabilities, and hidden sensitive information in an easy-to-deploy, use, and monitor platform.
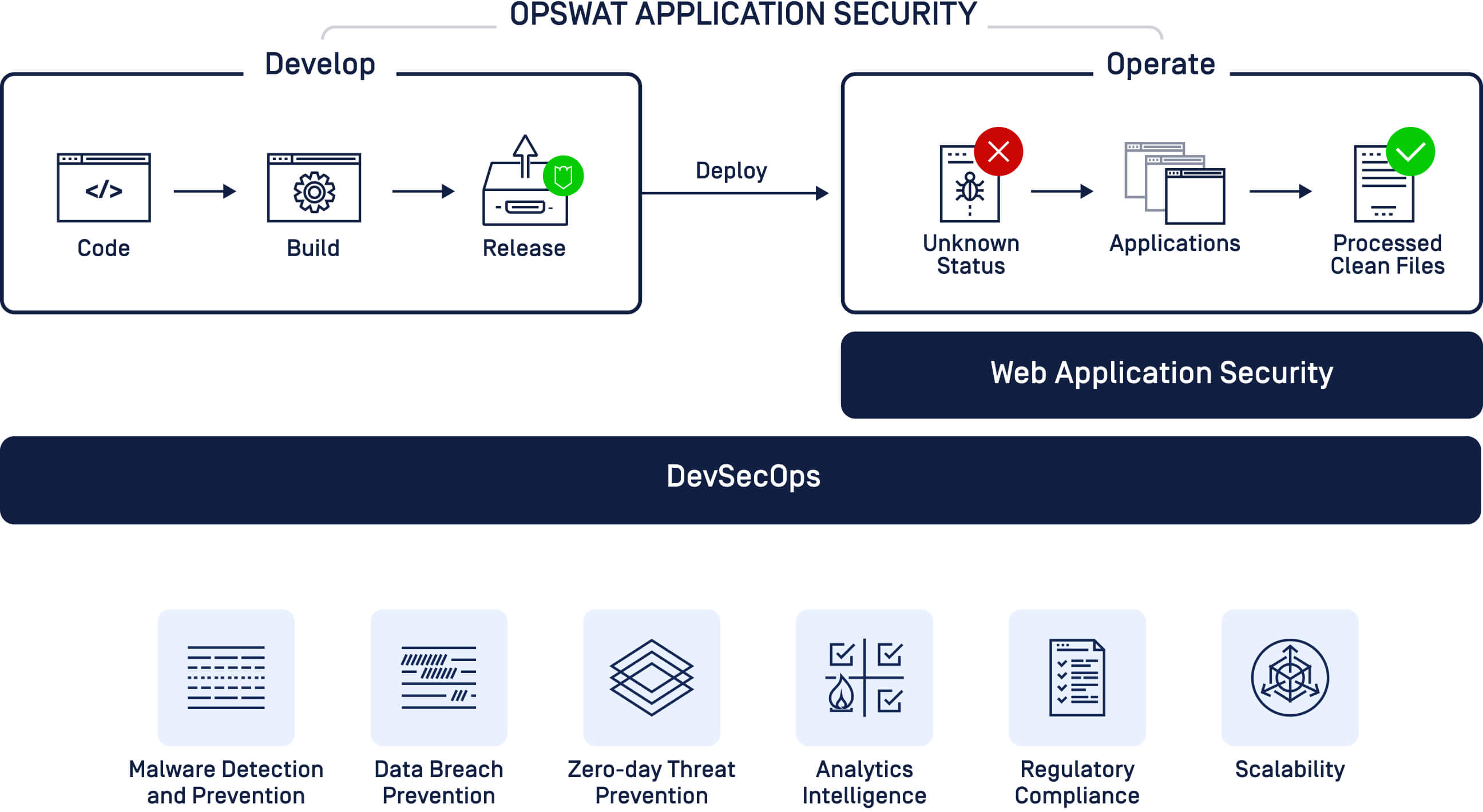
How OPSWAT Can Help with Application Security

Web Application Security
You could be susceptible to threats hidden in file content: malware, sensitive information, ransomware, exploitable vulnerabilities, or malicious users. Secure Your Web Applications and Services from Malicious File Uploads with the OPSWAT Web Application Security solution. More about Web Application Security
DevOps Security
Minimize security and compliance risks pre deployment by integrating shift left testing to enable secure and timely software development and delivery that meets the highest security standards.

Code
Build
Release
Deploy
Operate
Benefits
Protect Customers and Organizations
Prevent data theft, secret leakage, regulatory fines and interruptions in business continuity by building automated security safeguards both pre and post deployment in business applications.
Mitigate 3rd Party Risk
Secure the software supply chain. Scan and manage open-source code, libraries and their dependencies, external artifacts and distributed repositories that are the building blocks of modern applications.
Faster and Safer
Automated scanning and detection builds in application security, from the earliest stage of the SDLC (enabling quick iterative development and deployment), to the monitoring of millions of daily file uploads and transfers in heavy use applications (without impacting productivity).
Actionable Intelligence
Highest detection rates give you the confidence to focus on what matters most; lower false positives help reduce distractions that waste time and resources - for greater productivity all round.

Why OPSWAT?
OPSWAT streamlines your application security processes and enables collaboration among various stakeholders to protect your enterprise from potential breaches and data loss.

Visibility
Monitor and evaluate your security status and potential risks at a glance.
Real-time dashboard immediately alerts you to potential threats and vulnerabilities in your assets. Drill deeper to investigate any areas of concern and take corrective actions.
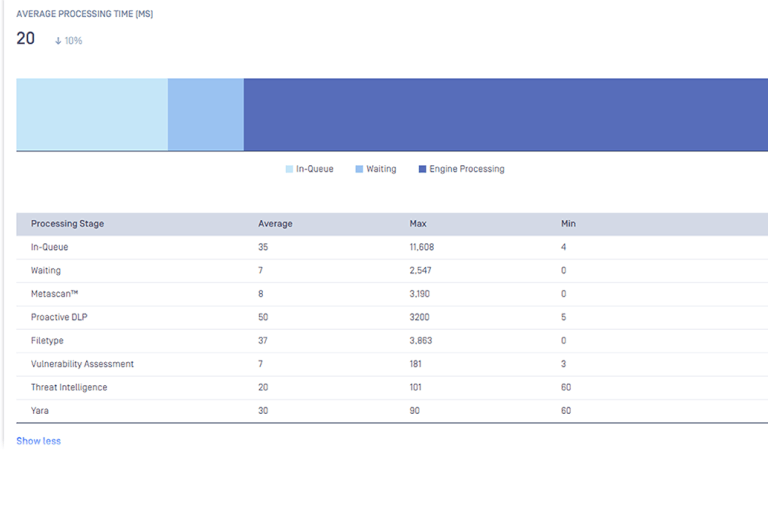
High Performance and Scalability
Fast scanning and reconstruction of files in milliseconds without affecting performance. Scalability to any volume with our built-in high-performance architecture and load balancing features.
Simple and Flexible Deployment
Fast and scalable implementation on-premises and in the cloud using REST API or any Internet Content Adaptation Protocol (ICAP) enabled product.
Multi-platform (Windows, Linux) and multiple deployment mode (Docker, Cloud, Datacenter) support. We provide easily integrated tools for you to check and secure your TeamCity and Jenkins build.
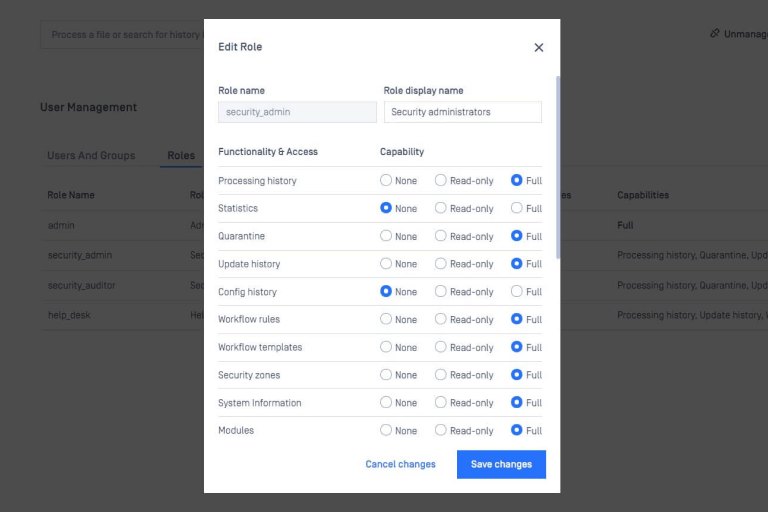
Customizations
You have the flexibility and control to customize and create multiple workflows and rules to meet different security policies.
Administrators can create processes and restrict access based on users, file sources and file types to best fit the use case for your organization.
Low Overhead Implementation
Powerful control over cybersecurity through a single platform. This results in a higher ROI, higher adoption, lower overhead, and fewer trained professionals needed to oversee complex systems.

