Cybersecurity Solutions for National
Defense, Critical Infrastructure,
and Cross-Domain Security
OPSWAT is Trusted by
Trust No File, Trust No Device™
OPSWAT is dedicated to protecting the integrity of our nation’s most sensitive environments through high-assurance cybersecurity solutions purpose-built for U.S. federal missions.
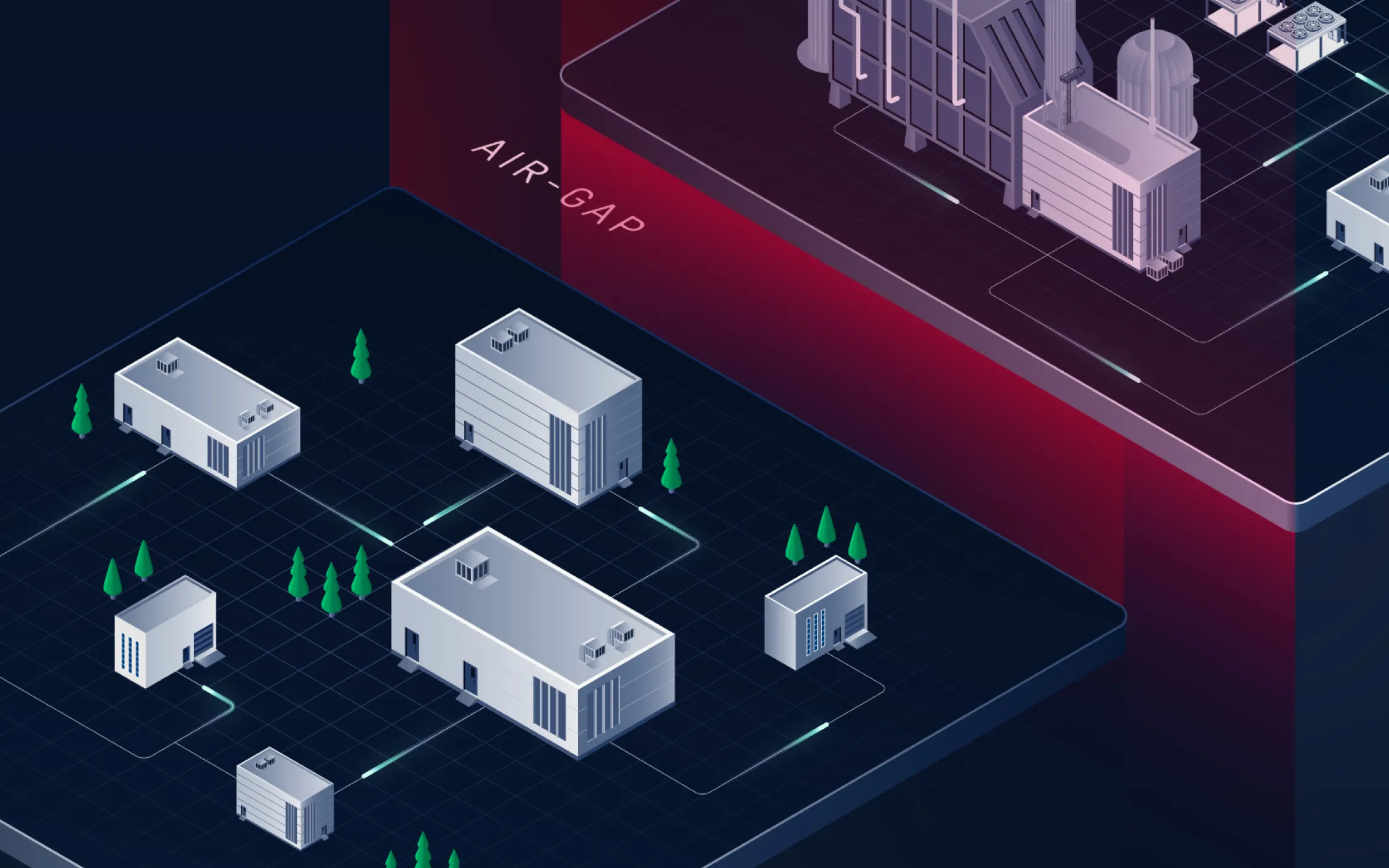
From securing classified information exchanges to protecting critical infrastructure, our technologies enforce Zero Trust principles across the DoW (Department of War), IC (Intelligence Community), DHS (Department of Homeland Security), and civilian agencies. Purpose-built for the unique demands of federal operations, our solutions provide resilient, compliant, and scalable protection for classified, air-gapped, and OT networks.

Our unified cybersecurity approach is built on five core pillars: Zero Trust, Compliance, Visibility, Artificial Intelligence, and Cross Domain.
We deliver trusted solutions that safeguard data, devices, and infrastructure across classified, air-gapped, and operational environments. With decades of innovation and the trust of national security leaders, OPSWAT ensures the security and continuity of our nation’s most mission-critical systems.

OPSWAT Federal AI-Powered Network Detection & Response for U.S. Government Missions
OPSWAT Federal equips agencies with AI-driven NDR that continuously monitors, analyzes, and responds to suspicious activity across essential federal networks. Strengthened by OPSWAT’s threat intelligence and zero-trust content security, this capability enhances visibility, accelerates incident response, and safeguards mission-critical data across all operational environments.

Why Federal Agencies and Integrators Trust OPSWAT
Federal agencies trust OPSWAT to secure their most critical operations, delivering purpose-built solutions for Zero Trust, CMMC, CDM, and national critical infrastructure, with proven deployments across classified, unclassified, and air-gapped environments.
From Zero Trust enforcement to high-assurance cross-domain data transfer, OPSWAT utilizes the
technologies that federal agencies rely on to protect national security.
Protect Your Mission
- Zero Trust
Every file, device, and data flow must be authenticated, inspected, and continuously verified. OPSWAT enables Zero Trust architectures for federal missions through:
- Device compliance enforcement
- Secure file and data transfer
- Network segmentation & hardware-enforced unidirectional flow
- Advanced threat detection & continuous monitoring
- Federal Use Cases
- Department of War: Stopping insider threats and lateral movement with content-level inspection.
- Intelligence Community: Securing mission data transfers between critical environments.
- Civilian: Achieving Zero Trust mandates for DHS, DOE, and other agencies
- Compliance
Federal operations demand strict adherence to CMMC, NIST 800-53, FedRAMP, and agency-specific security frameworks. OPSWAT streamlines compliance by:
- Enhancing audit readiness
- Mapping controls to NIST 800-207, CMMC, Zero Trust, etc.
- Enforcing policy at the content and device level
- Federal Use Cases
- Department of War: CMMC readiness and RMF support for contractors and program offices.
- Intelligence Community: Compliance with compartmentalized network controls.
- Civilian: Regulatory compliance for agencies such as HHS and DOT in hybrid/cloud environments.
- Visibility
Trust no network; situational awareness across endpoints, networks, and applications is critical for detecting and responding to threats. OPSWAT delivers:
- Endpoint telemetry and network behavior analytics
- Sandboxing insights, curate threat intelligence, and alert correlation
- Continuous monitoring for mission assurance
- Federal Use Cases
- Department of War: Monitoring mission-critical OT and IT networks.
- Intelligence Community: Visibility across segmented enclaves.
- Civilian: Oversight of distributed agency endpoints and remote workforces.
- AI (Artificial Intelligence)
AI-driven threat intelligence accelerates detection and reduces analyst burden. OPSWAT integrates AI for:
- Automated malware detection
- Behavioral analysis & threat scoring
- Predictive risk identification
- Federal Use Cases
- Department of War: Automated detection in contested environments with limited analyst capacity.
- Intelligence Community: Real-time threat correlation across massive datasets.
- Civilian: IT modernization with reduced false positives.
- Cross Domain
- Secure one-way data transfer with deep content inspection and data loss prevention.
- Mission-ready cross domain tech without NSA LBSA certification requirements.
- Trusted protection for secure, hardware-based communication between networks.
- Federal Use Cases
- Department of War: Transfers between networks that do not require Raise-the-Bar (RTB) baseline solutions.
- Intelligence Community: Secure interagency collaboration.
- Civilian: Sensitive data sharing for regulatory and research bodies.
Key Solutions Purpose-Built for
Federal Government
Network Detection & Response
Network Hunting Redefined
File Security
Prevent Known, Unknown, and AI-Generated Threats from Disrupting Your Business Processes.
Peripheral & Removable Media Protection
Proven Cyber-Physical Threat Prevention
Managed File Transfer
Security-First File Transfer with Policy Enforcement Across Users & Systems
Data Diodes & Security Gateways
Next-Level Data Diode and Security Gateway Solutions