Proactive DLP™ is one of several core technologies ( including Deep CDR™ and Metascan™ Multiscannning ) powering the OPSWAT MetaDefender Platform to prevent sensitive and confidential information in files from leaving or entering organizations’ systems by content-checking files before they are transferred. This aids compliance with regulatory requirements like HIPAA, PCI-DSS, and GDPR. Proactive DLP also uses AI and machine learning to detect adult content in images and offensive language in text.
Better Document Identification with Enhanced AI
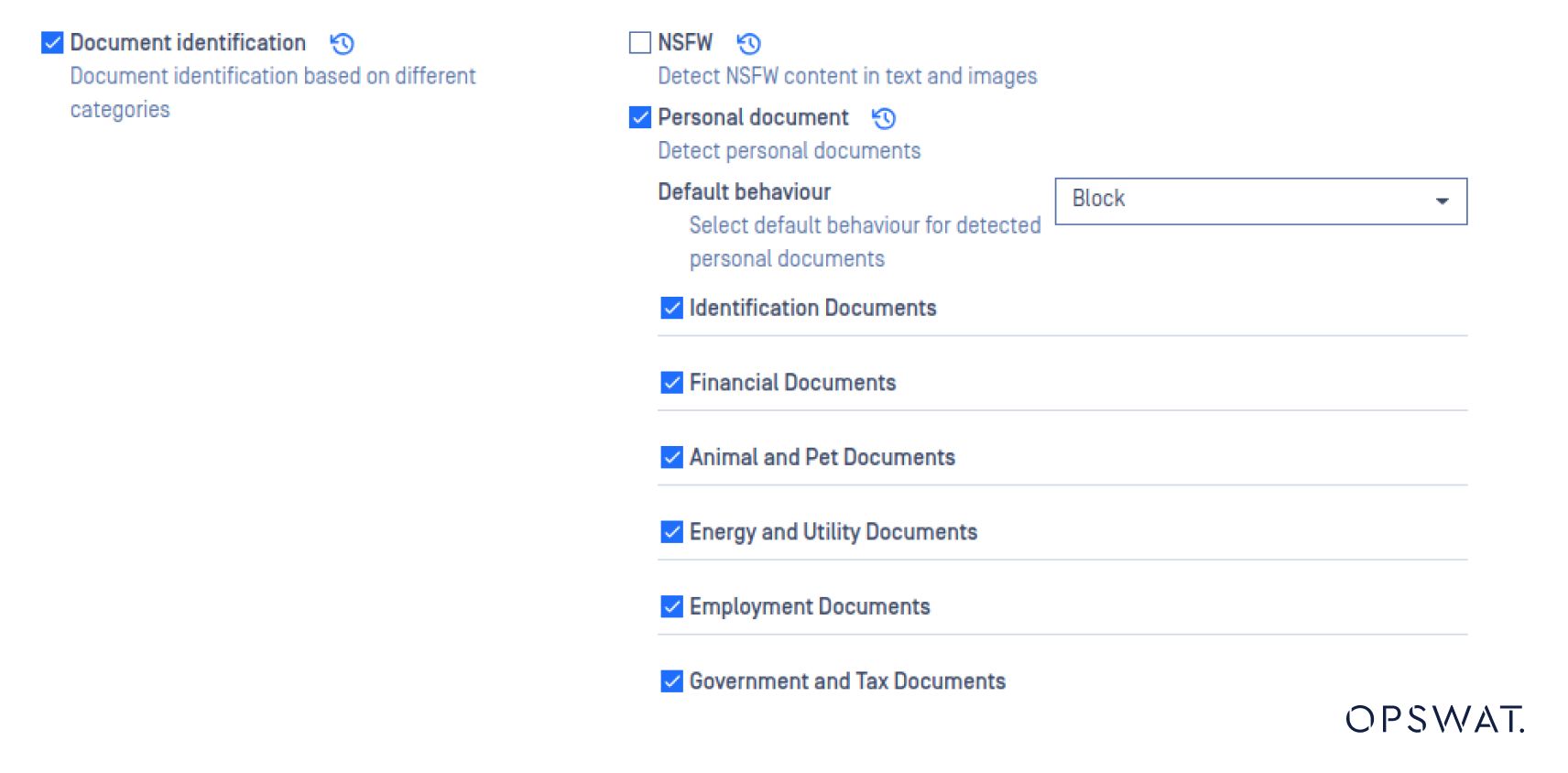
Building on its already robust capability, Proactive DLP has further refined its AI-Powered Document Identification feature, delivering even more accurate and efficient document classification. These enhancements enable organizations to better recognize and protect sensitive information across a wider range of document types.
The latest enhancements to AI-Powered Document Identification include:
Enhanced Machine Learning Models
Advanced machine learning algorithms improve detection accuracy, allowing for more precise identification of sensitive documents and reduced false positives.
Expanded Document Type Support
Proactive DLP now supports an even broader array of document types, including:
- Financial documents
- OCR-processed documents
- Specialized file formats
This feature can be activated in MetaDefender Core:
Prevent Data Leaks from Malicious Insiders
When it comes to security threats and fraud risks, we often focus on hackers and external attacks attempting to breach companies' networks to steal information and data. However, insider threats are another common source of data leaks.
Threats from employees and other trusted insiders are on the rise. In 2023, the average annual cost of insider security breaches surged to $16.2 million per organization, while the average time to contain such incidents extended to 86 days. More than ever, it’s important for businesses to adopt robust security protocols to safeguard sensitive information and data.
Insider Threats vs External Attacks
Over the past five years, the perception of the challenges in detecting and preventing insider attacks, as opposed to external cyberthreats, has undergone a significant shift. Concern about malicious insiders has increased significantly, rising from 60% in 2019 to 74% in 2024. This rise indicates a greater awareness or experience of intentional insider attacks.

Insider threats are malicious acts carried out by authorized employees within an organization. These threats represent a major cybersecurity challenge for both private and public organizations, as insider attacks can cause extensive damage to organizational assets, often more than external attacks. Most existing approaches in the field of insider threat detection focus on general attack scenarios. However, insider attacks can be executed in various ways, with the most dangerous being data leakage attacks, which can be carried out by a malicious insider before they leave the organization. This highlights the need for advanced, nuanced methods to identify these emerging risks.
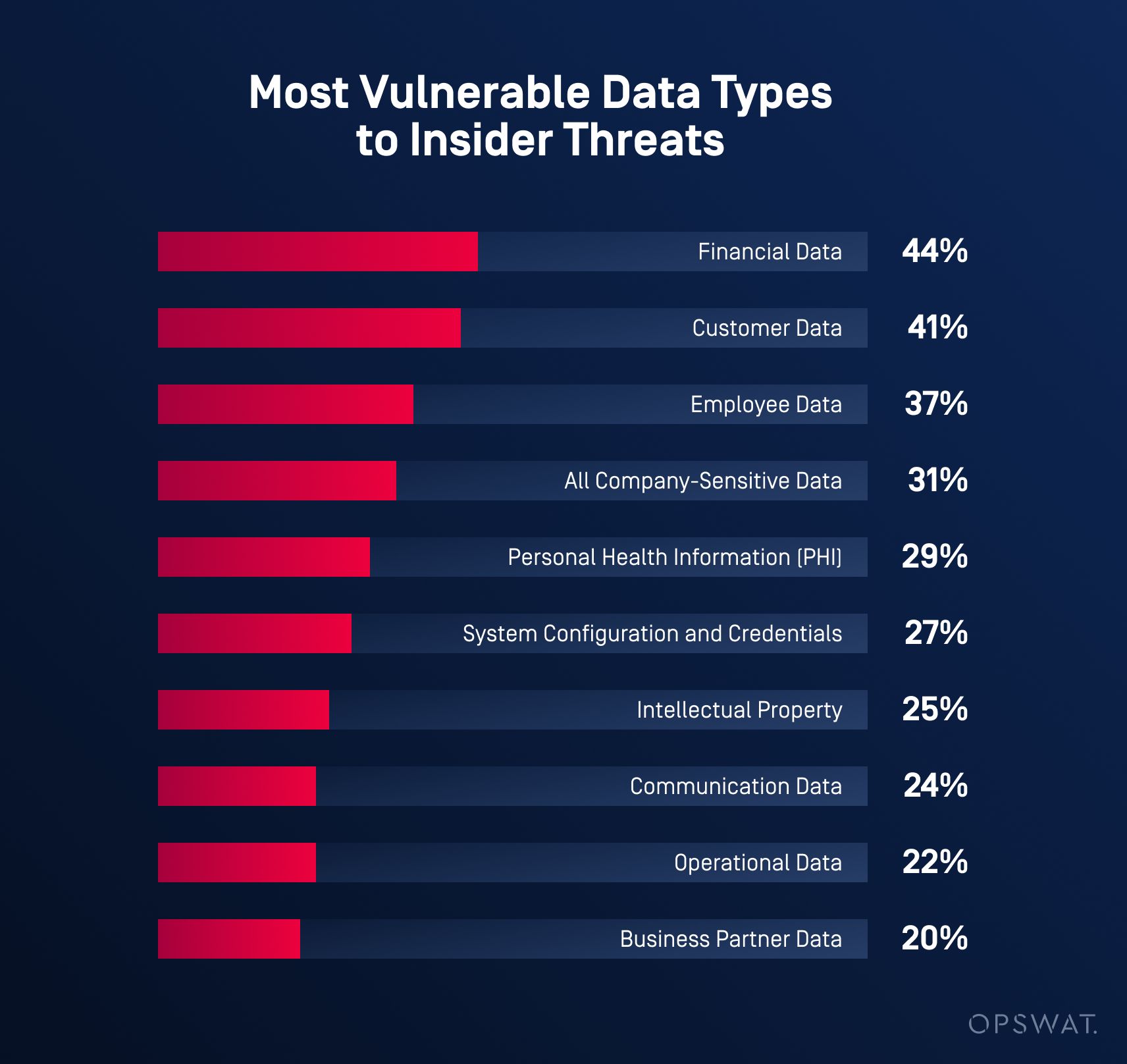
Types of Data at Risk
According to the 2024 Insider Threat Report, financial data, customer data, and employee data are highly vulnerable to malicious insiders. Financial data is particularly at risk due to its direct monetization potential. Customer data follows closely, raising concerns over the loss of PII (personally identifiable information). Employee data is also a significant concern, highlighting risks from mishandling sensitive personnel information. The report emphasizes that all company-sensitive data is susceptible, highlighting the need for comprehensive data security measures.
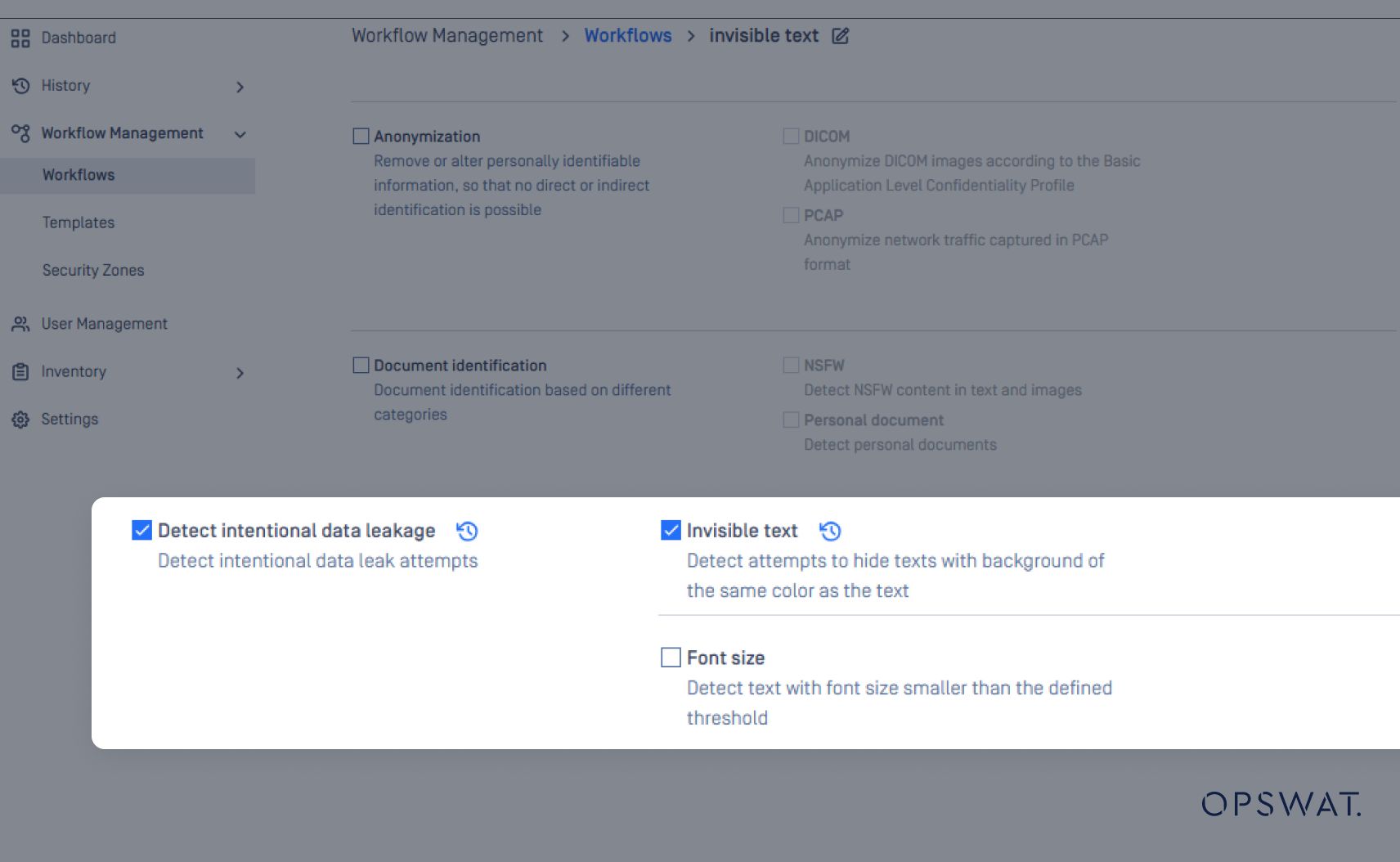
Detect Malicious Insider Threat Attack Techniques
Malicious insiders often use clever techniques to bypass security measures.


Sample of invisible texts inside a sensitive document

Sample of actual text disguised as invisible text
With Proactive DLP, organizations can proactively detect and prevent these techniques.
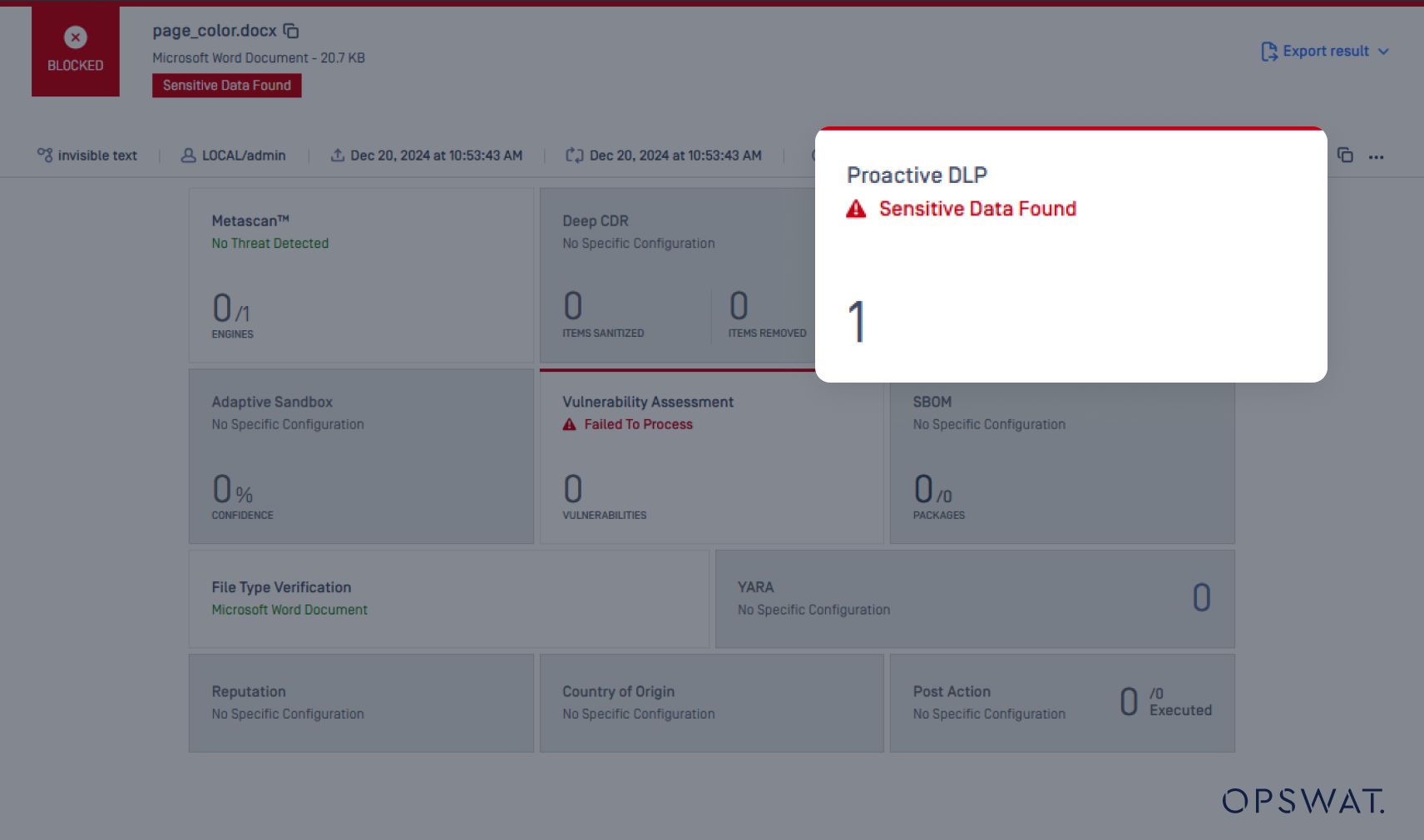
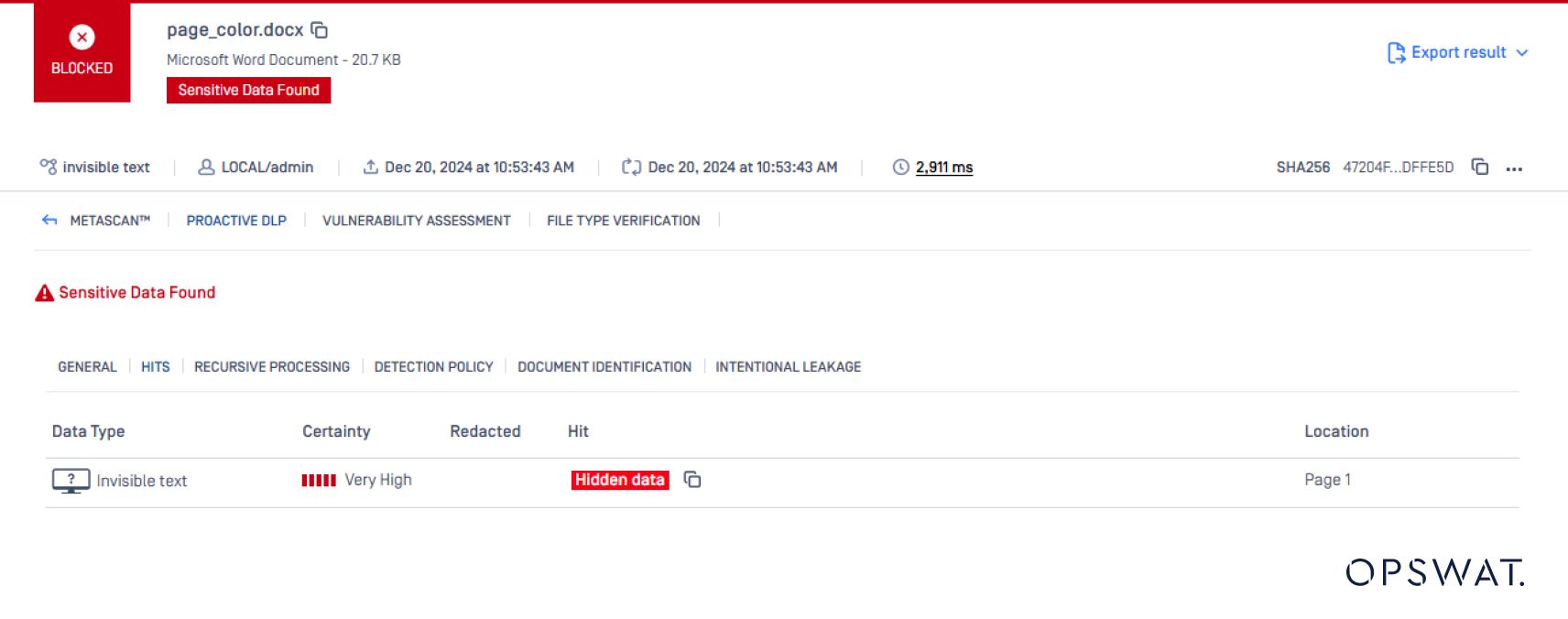
This new feature ensures that no malicious insider techniques escape scrutiny, empowering organizations to maintain tighter control over sensitive data and prevent regulatory violations.
Protect Sensitive Data with Proactive DLP
The threat of malicious insiders is a reality that no organization can afford to ignore. By leveraging advanced technologies like Proactive DLP, companies can gain a competitive edge in protecting sensitive information and preventing regulatory violations. As the use of AI-powered document classification and malicious insider threat detection continues to evolve, it's essential for organizations to stay informed and adapt their security strategies accordingly.
Additional Resources
Ready to get started with Proactive DLP v2.22.0? Check out these helpful resources:
- Visit opswat.com/technologies/proactive-data-loss-prevention
- Upgrade to Proactive DLP™ v2.22.0
- Learn more about other advanced Proactive DLP features:
Have other questions? Reach us at support@opswat.com.

