Digital Imaging and Communication in Medicine (DICOM) files have been a standard for storing, viewing, and transmitting medical imaging information over the last few years. However, these files contain not only viewable images, but also a header with sensitive data elements. These metadata elements include identifiable information about patients, studies, and institutions, which are considered sensitive and personal. To maintain patient privacy and protect sensitive data, it is essential to implement proper security measures when handling DICOM files.
To address these security concerns, OPSWAT announces a new feature called DICOM Anonymization in the OPSWAT Proactive Data Loss Prevention (DLP) technology. This feature can fully anonymize the metadata in DICOM files, ensuring data privacy and compliance with regulations.
How DICOM Anonymization Works
A medical image acquired for clinical purposes can have a range of secondary uses, such as being used as part of research projects. For privacy concerns, you might need to remove or modify certain sensitive data elements—such as personally identifiable information (PII) or protected health information (PHI) before you analyze or share the DICOM images with authorized collaborators.
1. Remove the metadata
To help meet the requirements of the HIPAA Safe Harbor provision, OPSWAT Proactive DLP DICOM Anonymization provides a default configuration. The DICOM standard includes attributes that may potentially reveal PII or PHI, which can violate HIPAA Safe Harbor and other compliance standards. By incorporating the DICOM Anonymization feature into your file upload security measures, all sensitive information will be anonymized.
Below is a table that defines specific actions for each tag in the DICOM header, such as replacing values with dummy data or removing certain tags altogether.
| Groups | Actions |
|---|---|
| D_TAGS | Replace with a non-zero-length value that may be a dummy value |
| Z_TAGS | Replace with a zero-length value, or a non-zero-length value that may be a dummy value |
| X_TAGS | Completely remove the tag |
| U_TAGS | Replace all UID's* random ones. The same UID will have the same replaced value |
| Z_D_TAGS | Replace with a non-zero-length value that may be a dummy value |
| X_Z_TAGS | Replace with a zero-length value, or a non-zero-length value that may be a dummy value |
| X_D_TAGS | Replace with a non-zero-length value that may be a dummy value |
| X_Z_D_TAGS | Replace with a non-zero-length value that may be a dummy value |
| X_Z_U_STAR_TAGS | If it's a UID, then all numbers are randomly replaced. Else, replace with a zero-length value, or a non-zero-length value that may be a dummy value |
*UID: Unique Identifier
Reference: dicom.nema.org
2. Anonymize the image
In addition to anonymizing DICOM files headers, OPSWAT Proactive DLP DICOM Anonymization can also redact and remove sensitive content from DICOM images. With the integration of a powerful AI-based identification engine, we have been able to identify and redact the PII and PHI that is burned on the medical images.
To make this task possible, OPSWAT Proactive DLP leverages a powerful Natural Language Processing (NLP) method called Named Entity Recognition.
NER identifies and categorizes key information, or “entities” within a given context. The term “entity” can refer to any word or set of words that is consistently used to refer to the same thing. Detected entities are classified into predetermined categories based on their characteristics. By using NER, we were able to categorize and detect the PII and PHI that could otherwise be lost in the texts and images as traditional approaches are not as effective.
OPSWAT Proactive DLP currently supports these entities: PERSON, LOCATION, NRP (nationalities/religious/political groups), and DATE_TIME. In the future, we will add more entities to the product.
DICOM Anonymization in Action
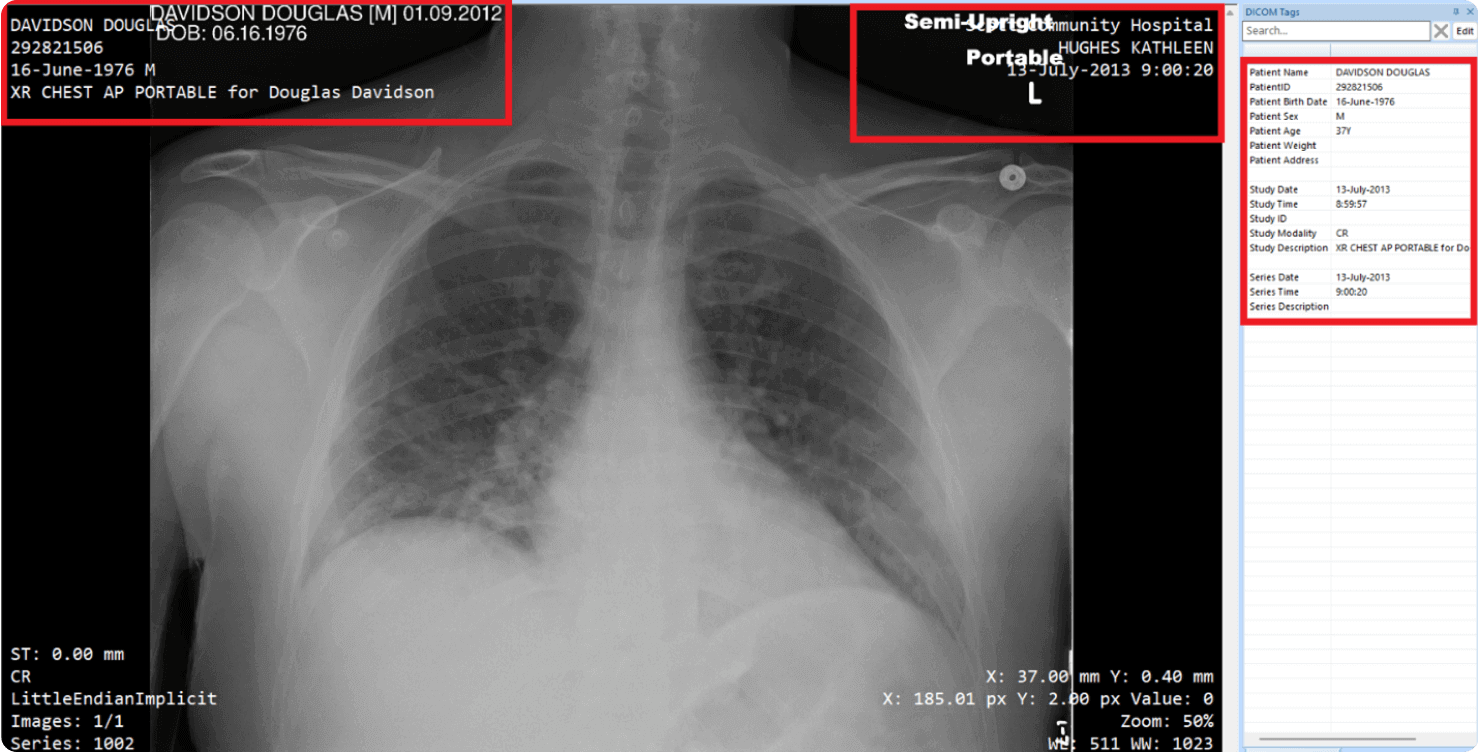
To illustrate the effectiveness of DICOM Anonymization, let’s take a look at some examples. We have two sample X-Ray images to compare: one before anonymization and one after, where the goal was to remove all sensitive information burned into the image.
The first image shows an X-Ray image with sample PII data and PHI data visible in both the headers and burned into the image. This piece of information is a privacy concern and needs to be removed before analysis or sharing.
The second image displays the same X-Ray image after being processed by DICOM Anonymization. All sample PII and PHI have been successfully removed, ensuring the image is privacy-compliant and safe to use and share.

Double the Power with Deep CDR and Proactive DLP
OPSWAT Deep Content Disarm and Reconstruction (CDR) removes unapproved content and reconstructs the DICOM file with only its legitimate data. Deep CDR ensures every file entering into your organization is harmless, helping you prevent zero-day attacks and evasive malware. Our solution supports sanitization for over 100 common file types, including PDFs, Microsoft Office files, HTML and many image file types. Learn how Deep CDR secures DICOM files
Deep CDR and Proactive DLP are available in OPSWAT’s file upload security products for various use cases: MetaDefender Core, MetaDefender ICAP Server for integration with network devices, MetaDefender Storage Security and MetaDefender Cloud.
If you have any questions or would like more information about DICOM anonymization or OPSWAT File Upload Security solutions, talk to our security experts.

