Security professionals safeguard valuable digital assets by effectively detecting and hunting emerging threats. OPSWAT, a leader in advanced threat intelligence solutions, developed a cutting-edge MetaDefender Threat Intelligence within the MetaDefender Cloud platform to uncover hidden malicious activity. By utilizing machine-learning powered Similarity Search, we can analyze files with more than 300 features and match complex patterns in known malicious files to hunt threats.
OPSWAT’s MetaDefender Threat Intelligence utilizes pattern search to query our massive dataset, identifying files using patterns and expressions. Combined with our Similarity Search functionality similarity search, this powerful technology provides a comprehensive and intuitive system that detects, analyzes, and responds to all threats.
Access the intelligence data you need with the MetaDefender Cloud platform's fast, scalable threat intelligence and prevention. Dedicated security teams can also benefit from MetaDefender Sandbox's best-in-class sandboxing and detection of unknown threats.
Two Features of Threat Intelligence Search
Pattern Search
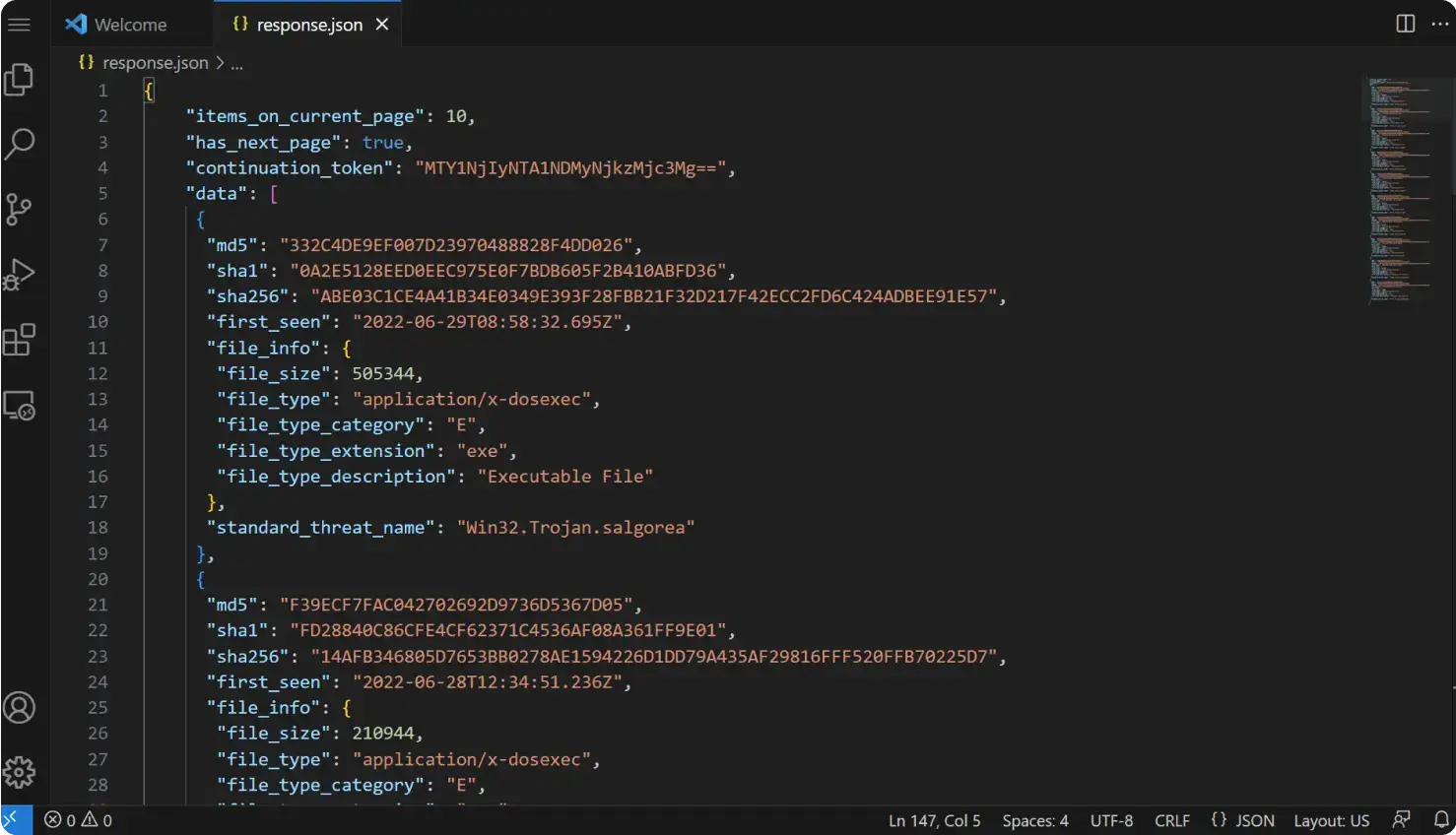
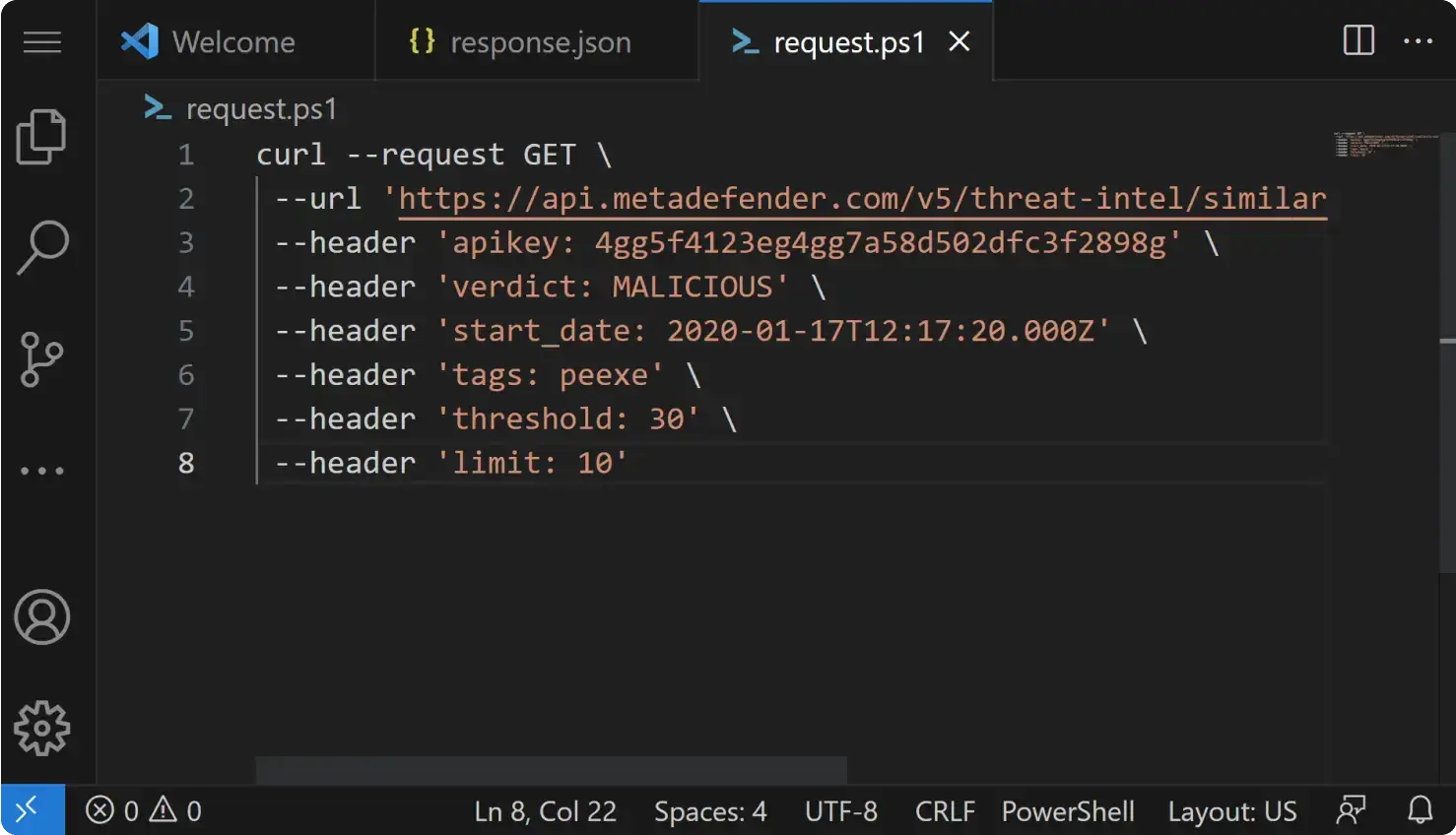
Search hashes of known malware by querying malware families, malware threat names, antivirus (AV) detection filtering, and first and last seen, among many others. By performing pattern searches, you can quickly identify known threats or indicators of compromise (IOCs) associated with specific malware, campaigns, or threat actors. It is a highly effective method for detecting previously identified threats and known attack patterns.
Similarity Search
Scan files to identify new and unknown malware. During the similarity search, files undergo a rigorous scanning procedure using the MetaDefender Sandbox static and file emulation technologies. This advanced technology extracts the most relevant and useful information from a given file.
Our expert malware analysts have determined the most effective features for calculating the similarities between two files. These features are carefully selected based on their ability to provide accurate and relevant results. They are also continuously updated to stay current with the latest malware trends and techniques.
Features Used to Calculate Similarity Scores:
- Binary metadata such as file size, entropy, architecture, and file characteristic, among others.
- Imports
- Resources
- Sections
- Threat Patterns and more.
Note: When searching for similarities between files, it is important to use signals generated by Filescan and not to rely solely on the final verdict of a file. This approach helps to avoid any potential biases that may arise during the similarity search process. Learn more about Similarity Search.
Contact us to request more information on our Threat Intelligence Search.

