New capabilities empower security teams, enabling a better understanding of adversaries and more effective responses to threats.
The latest release of MetaDefender Aether adds enhanced features to address complex threats. We have streamlined our reporting with ChatGPT, improved threat indicators, and added SOAR integrations to help stay one step ahead of adversaries.
New Features:
- Quickly generates executive summaries with ChatGPT
- Integrates with Detect It Easy to identify characteristics of executable files related to compilation and packing
- Supports unpacking of 64-bit executables
- Detects and extracts embedded RTF files in Office documents, as described in CVE-2023-36884
- Enhances threat indicator for Mavinject
Faster Reporting
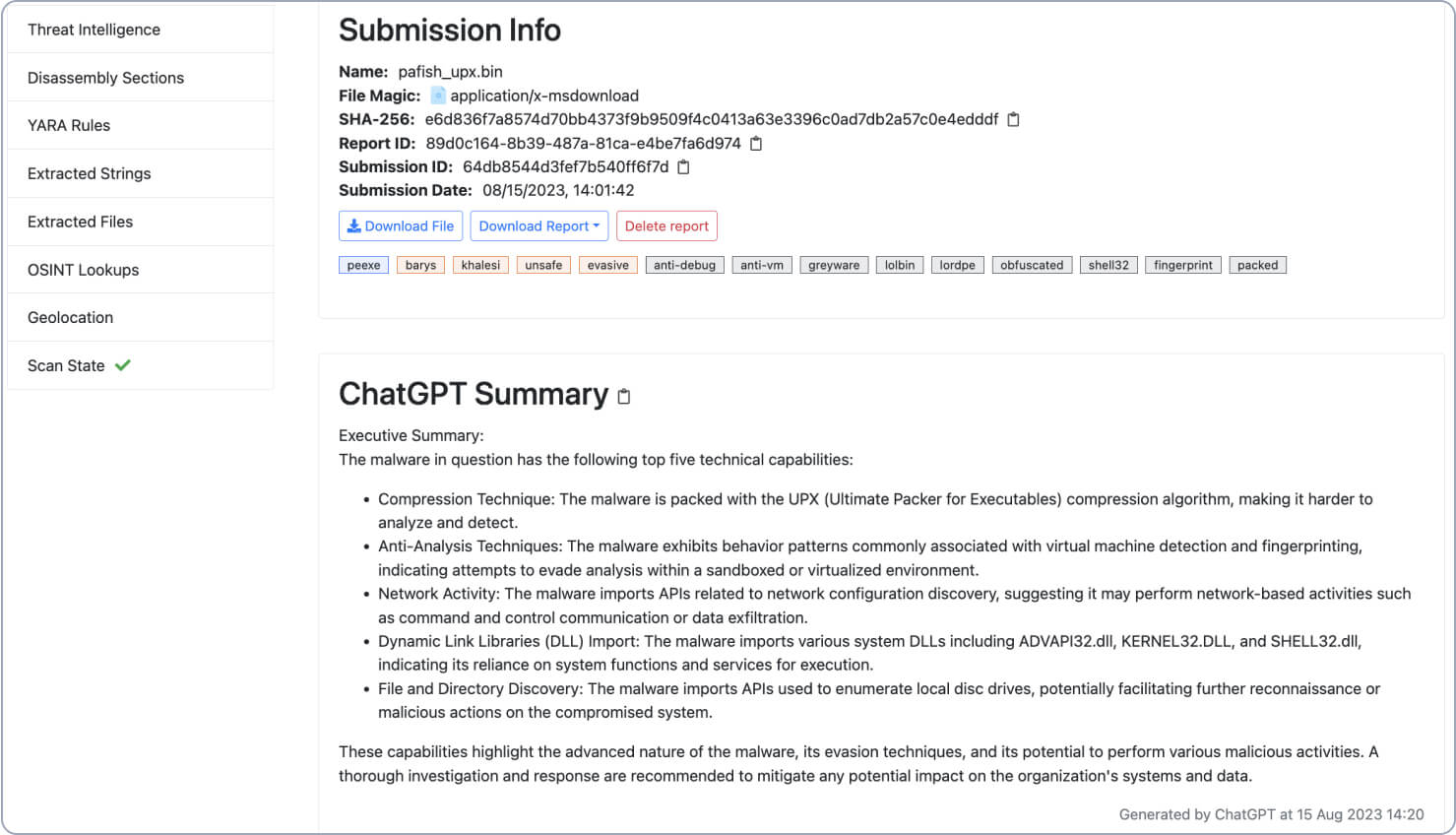
Share detailed, high-quality information across the organization to better respond and address threats with ChatGPT. MetaDefender Aether summarizes complex intelligence into easy-to-consume summaries without leaving the dashboard.
More Threat Indicators
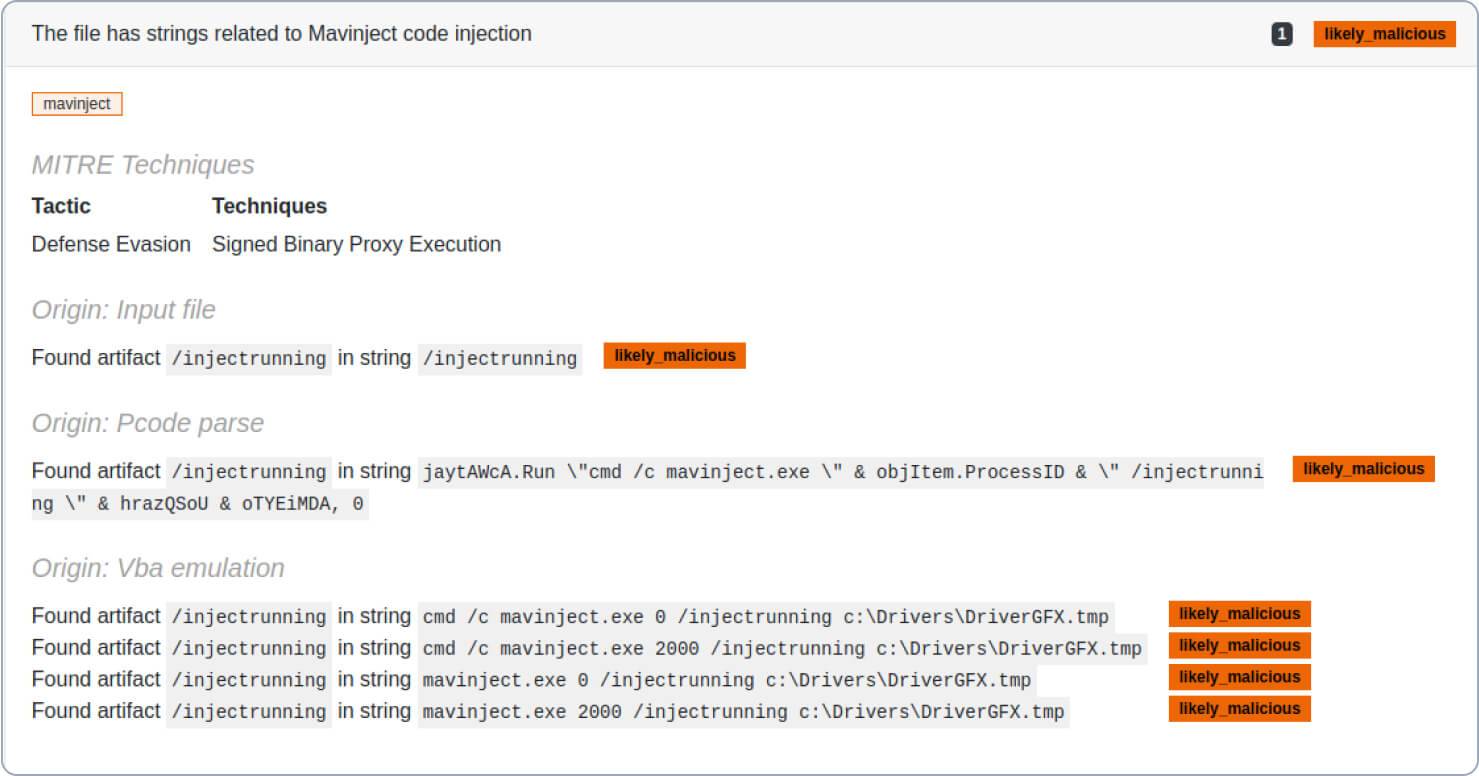
Adversaries may abuse mavinject.exe to proxy the execution of malicious code. Mavinject.exe is the Microsoft Application Virtualization Injector, a Windows utility that can inject code into external processes as part of Microsoft Application Virtualization (App-V). See an example and new threat indicator.
Additional improvements:
- Accelerated scan processing reduces the time it takes to analyze files, enabling quicker results and more efficient workflows.
- Enhanced threat indicators and verdict calculation improve the accuracy of threat detection and the overall assessment process, ensuring more precise identification of potential risks.
- Improved MITRE mapping for user clarity aligns threat information with MITRE framework standards, making it easier for users to understand and respond to threats.
- Advanced VBA emulation features expand VBA emulation to support additional functionalities, enhancing the depth of analysis for macro-based threats.
See the full list of 1.9 updates and additional features.
MetaDefender Aether Key Features
MetaDefender Aether's adaptive threat analysis detonates and extracts indicators of compromise (IOCs) from evasive and zero-day malware.
Threat-agnostic analysis
Processes a high volume of files and URLs to find a wide variety of threats.

Actionable IOCs
Focuses on quality and quantity of actionable indicators of compromise (IOC) for incident response.

Adaptive threat analysis
Enables targeted attack detection bypassing anti-analysis tricks (e.g., geofencing).

Single source of truth reputation endpoint
Analyzes threats efficiently with a massive Reputation API.

Threat intelligence similarity search
Leverages cutting-edge machine learning to identify unknown threats in similar files.
For more information on MetaDefender Aether, contact our experts right away.

