The Cleo Exploit: A Wake-Up Call for File Transfer Security
In December 2024, cybersecurity researchers uncovered an alarming zero-day remote code execution (RCE) vulnerability in Cleo’s managed file transfer products, as first reported by CSO Online.
Attackers actively exploited this flaw in the wild, bypassing even recently issued patches. Despite Cleo's initial security updates, threat actors were able to continue compromising up-to-date systems, revealing deep-rooted weaknesses in basic file handling, input validation, and platform resilience.
This latest incident is part of a troubling trend: managed file transfer solutions have become prime targets for sophisticated cyberattacks. These platforms, responsible for the secure file transfer of highly sensitive data across trusted channels, represent an attractive entry point for attackers.
A breach within an MFT (managed file transfer) environment can trigger catastrophic outcomes, from systemic data leakage and regulatory violations to operational disruption across critical infrastructure sectors, all of which can cause severe reputational damage.
Secure MFT is no longer optional in critical infrastructure environments. Organizations must move beyond reactive patching and single antivirus solutions. Instead, organizations must adopt proactive, multi-layered, advanced security architectures designed specifically to defend MFT operations against modern threat landscapes.
Today, the following are no longer best practices but instead, operational necessities:
Building resilience
Organizations must implement security measures to recover quickly from breaches or disruptions, minimizing impact and downtime.
Maintaining centralized governance
Central control over file transfers, user access, and audit trails is essential for visibility and compliance.
Enforcing policy-based transfers and security rules
File transfers must follow automated, pre-defined rules to prevent human error and ensure consistency.
Applying multilayer threat prevention measures
Single antivirus engines are no longer a secure option; multiple AV engines have a much better chance of detecting and neutralizing cyberthreats.
Inside the Cleo Breach: How Attackers Exploited MFT Weaknesses
In late 2024, security researchers identified active exploitation of a critical zero-day remote code execution vulnerability in Cleo’s managed file transfer products. The affected solutions included Cleo LexiCom, Cleo VLTrader, and Cleo Harmony, widely used across enterprise environments.
Cleo LexiCom is a desktop-based MFT client for connecting with major trading networks. Cleo VLTrader provides server-level MFT capabilities for mid-sized enterprises, while Cleo Harmony is aimed at meeting the integration and secure file transfer needs of large enterprises.
Even after an initial security patch was issued in October 2024, attackers continued to successfully target Cleo systems, exploiting weaknesses that were not fully addressed, as reported by Darktrace in December 2024.
Security teams urged organizations to immediately disconnect affected servers from the internet and implement temporary mitigation measures while awaiting a more complete fix.

Three key technical elements of the attack included:
- Exploiting a file upload vulnerability to achieve unauthorized file writes
- Dropping malicious files into the "Autorun" folder, triggering automatic execution
- Leveraging the autorun feature to deploy a payload chain involving ZIP archives, XML configuration files, and malicious PowerShell commands
The follow-up investigations revealed signs of advanced attacker tactics, such as Active Directory reconnaissance, stealth file deletion, and the deployment of a custom Java backdoor known as Cleopatra.
Immediate impacts observed:
- Remote code execution on vulnerable servers
- Unauthorized access to sensitive business and customer data
- Full system compromise enabling lateral movement across network environments
This breach illustrated how a failure to fully eliminate file-based vulnerabilities despite continuous patching can result in persistent exploitation of critical enterprise systems.
Why MFT Platforms are Now Prime Cyberattack Targets
The Cleo breach is not an isolated incident. Over the past several years, managed file transfer systems have become prime targets for sophisticated threat actors. Sensitive files exchanged through these platforms are often deeply tied to business operations, customer data, or regulated information, making the reward for successful compromise extremely high.
Previous high-profile cases such as the MOVEit Transfer, Accellion File Transfer Appliance, and Fortra GoAnywhere breaches show a consistent pattern: threat actors are focusing on file transfer technologies as a strategic entry point into enterprise networks.
The Cleo incident reinforces that even organizations with patched, updated systems are at risk if MFT solutions are not designed with built-in, multi-layered security principles.

Why MFT platforms are such high-value targets:
- Sensitive data in motion often includes credentials, PII, financial records, and intellectual property
- Trusted relationships with internal and external stakeholders amplify the potential impact of breaches
- Breaching a trusted file transfer node can provide entry points for broader network exploitation
To defend against cyberthreats, MFT security must move from a reactive model to a resilient, proactive architecture. Prevention, detection, and response should not be treated as separate stages. Instead, they must be integrated into the core design of the managed file transfer solution itself.
Recent breaches, including those involving Cleo software, reflect a broader pattern of attackers targeting trusted tools. The Hertz incident exposed customer identities and demonstrated the risks of third-party file transfer vulnerabilities. It shows what can happen when organizations rely on external solutions without continuous, layered security. Such negligence can leave organizations exposed to serious data breaches and reputational risks.
Building Resilient File Transfer Defenses with MetaDefender Managed File Transfer (MFT)
The Cleo exploit highlights the need for MFT solutions that do not simply rely on patching but are built from the ground up with multi-layered security controls. MetaDefender Managed File Transfer (MFT) is designed for security-first environments where policy-based transfer control, multi-layered threat prevention, centralized governance, and strict zone isolation are essential.
Several capabilities of MetaDefender Managed File Transfer (MFT) directly address the weaknesses exposed in the Cleo breach:
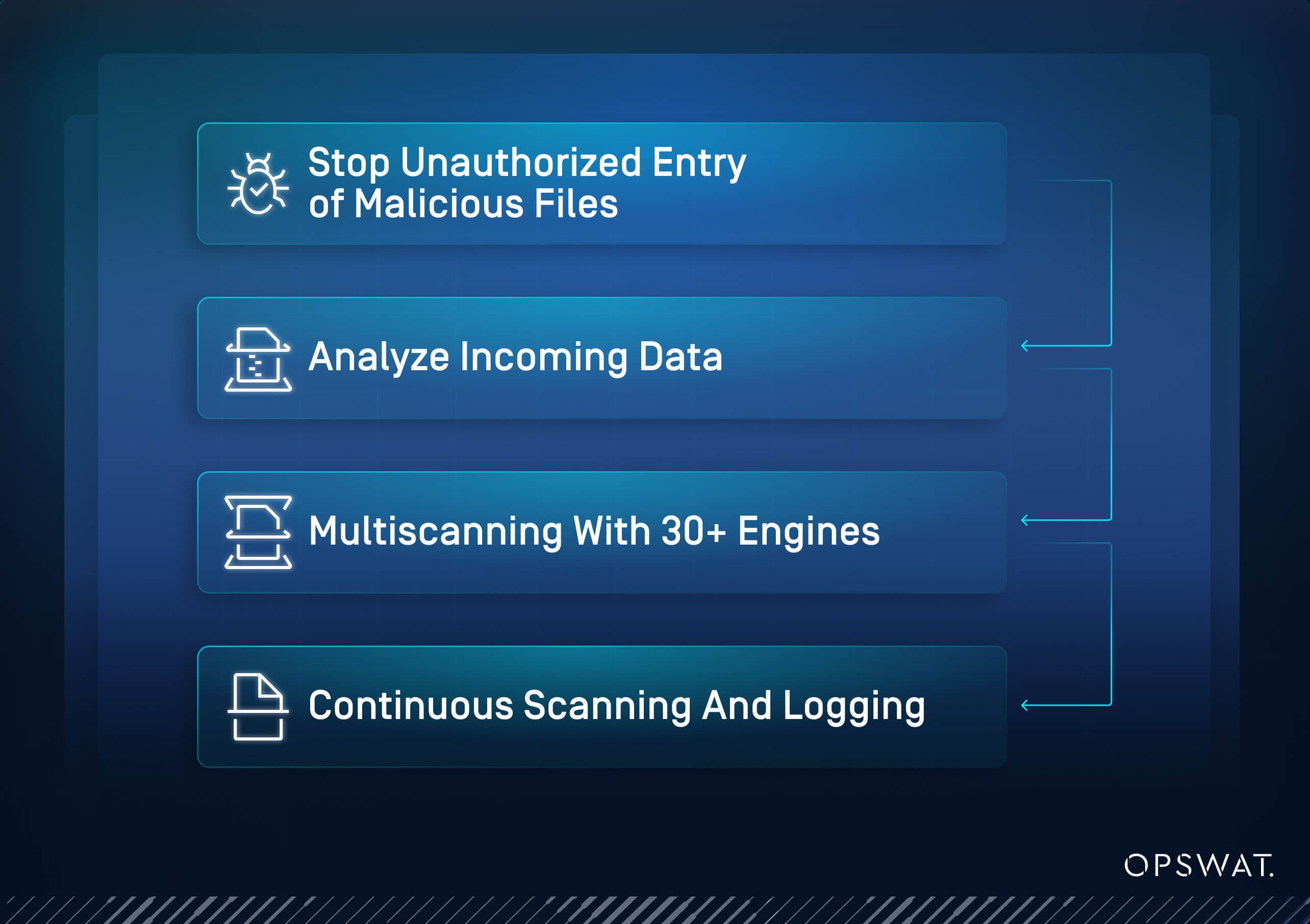
1. Preventing Initial Exploitation
Securing the first points of contact is critical. MetaDefender Managed File Transfer (MFT) strengthens access controls to block unauthorized entry before attackers can upload malicious files or gain a foothold in the network.
- Secure Access Control: Restricts MetaDefender Managed File Transfer (MFT) access to trusted internal or VPN-secured networks. This prevents direct exposure to external attackers attempting to upload malicious payloads.
- Multifactor Authentication (MFA): Enforces an additional layer of user verification. Even if credentials are stolen, attackers cannot easily gain unauthorized access.
- Role-Based Access Controls with Supervisor Approvals: Applies granular permissions to users and workflows. Even authenticated users must receive supervisory approval for critical upload and download actions.
2. Detecting File Spoofing & Hidden Elements
Stopping malicious files at the gateway prevents attacks from advancing inside the system. MetaDefender Managed File Transfer (MFT) thoroughly analyzes incoming data before any malicious content can be activated.
- Deep File Inspection Pipeline: Identifies and blocks files disguised under false extensions. Malicious ZIP archives or XML files are detected at the point of upload.
- Country of Origin Detection: Screens incoming files by geolocation. Files originating from restricted or high-risk regions can be automatically blocked.
- Archive Extraction and Content Scanning: Unpacks compressed files fully before transfer. This exposes hidden malware inside nested archives, such as PowerShell exploits. Learn more about archived files and the threat they pose here.
3. Advanced Threat Prevention
Going beyond static scanning is necessary to defend against advanced and unknown threats. MetaDefender Managed File Transfer (MFT) applies multi-engine scanning and neutralizes risks at the content level.
- Metascan™ Multiscanning with 30+ Engines: Simultaneously scans every file with multiple antivirus and threat detection engines. Malware and webshell-like files are blocked before execution. Learn more about Multiscanning here.
- Deep CDR™ (Content Disarm & Reconstruction): Rebuilds files by removing active or executable elements. Clean, safe versions of files are delivered while hidden threats are neutralized. Learn how Deep CDR regenerates files here.
- File-Based Vulnerability Assessment: Analyzes files for known vulnerabilities that could later be exploited. This catches weaponized document types before runtime.
4. Resilience and Early Detection
Persistent monitoring and rapid detection ensure that any breach attempts are caught early, minimizing impact. MetaDefender Managed File Transfer (MFT) continuously validates system integrity and logs every critical event.
- Adaptive Threat Analysis and Sandboxing: Executes and analyzes file behavior in a controlled environment. Suspicious actions like autorun execution or unauthorized outbound connections are flagged early. More on this AI-driven analysis here.
- Checksum Validation: Continuously monitors the integrity of system files and application directories. Alerts are triggered if unauthorized modifications occur.
Outbreak Prevention: Metascan™ Multiscanning continuously analyzes stored files using the latest threat intelligence database to detect zero-day malware and prevent emerging outbreaks. - Audit Logging and SIEM Integration: Records all file activity comprehensively. Enables fast breach tracing, forensic investigation, and regulatory reporting.
By embedding prevention, detection, and resilience at every layer, MetaDefender Managed File Transfer (MFT) could have stopped the Cleo exploitation at multiple stages, before malicious payloads ever reached execution.
Secure MFT is No Longer Optional
The Cleo incident provides a stark reminder that managed file transfer platforms sit at the heart of enterprise data flow and must be treated as part of the security perimeter. A breach at this layer can expose vast volumes of sensitive data, disrupt critical operations, and damage trust across entire supply chains.
Organizations cannot afford to view MFT security as an afterthought. The days of relying on patching alone are over. Threat actors are now demonstrating the ability to exploit minor weaknesses in file handling, upload permissions, and content processing with devastating effect.
MetaDefender Managed File Transfer (MFT) delivers zero-trust architecture, deep content inspection, and multi-layered threat prevention that could have disrupted the Cleo exploitation at multiple stages.
In summary, MetaDefender Managed File Transfer (MFT) would have:
- Blocked the initial unauthorized upload attempts
- Prevented the automatic execution of malicious payloads via autorun triggers
- Alerted administrators early through proactive monitoring and logging
By combining policy-based file transfer control, multi-layered threat prevention, centralized governance, and strict zone isolation, MetaDefender Managed File Transfer (MFT) establishes a hardened environment for secure file exchange. This level of resilience is no longer optional for enterprises and critical infrastructure providers. It is foundational to protect organizational data against the evolving threat landscape.



