In spite of advances in cybersecurity, malicious attacks are still becoming more prevalent than ever. Vulnerabilities have been leveraged as leading weapons in recent years, and we can find them being used in many of the recent attack incidents, including the Microsoft Follina vulnerability attack and in the Russia-Ukraine cyber war. It is, therefore, critical to effectively secure data safety in an unsafe state. Secure Access Service Edge (SASE) and Cloud Access Security Broke (CSAB) hold the key to this issue.
The topic of SASE has been discussed continuously over the years. This type of network architecture embodies the vision of a safe network model for enterprises and lies in the definition of network boundaries, such as network security gateways, cloud access, firewalls, and zero-trust networks. In early 2022, Gartner proposed a new concept of Secure Service Edge (SSE), which replaced the original Cloud Access Security Broke (CSAB) concept, mainly because of the outbreak of the epidemic that has changed the way we work today. The previous office environment transformed into a hybrid office or a completely remote office environment. OPSWAT MetaDefender Access and MetaDefender Core, along with the proprietary Deep CDR Technology, are the foundational building blocks of such hybrid offices.
Strict Security Boundaries with OPSWAT MetaDefender Access
OPSWAT MetaDefender Access addresses both secure access and device compliance in a single platform whether end users are at home, at the office, or at remote locations, and whether data and applications are on premises or in the cloud. When users connect to the network, MetaDefender Access checks the compliance on endpoints and examines devices with standard security checks, such as OS and Anti-virus, and then goes much deeper with a risk and vulnerability evaluation and the ability to detect and fingerprint over 5,000 third-party applications. At the same time, it can also be integrated with MetaDefender Core to provide higher security for enterprises.
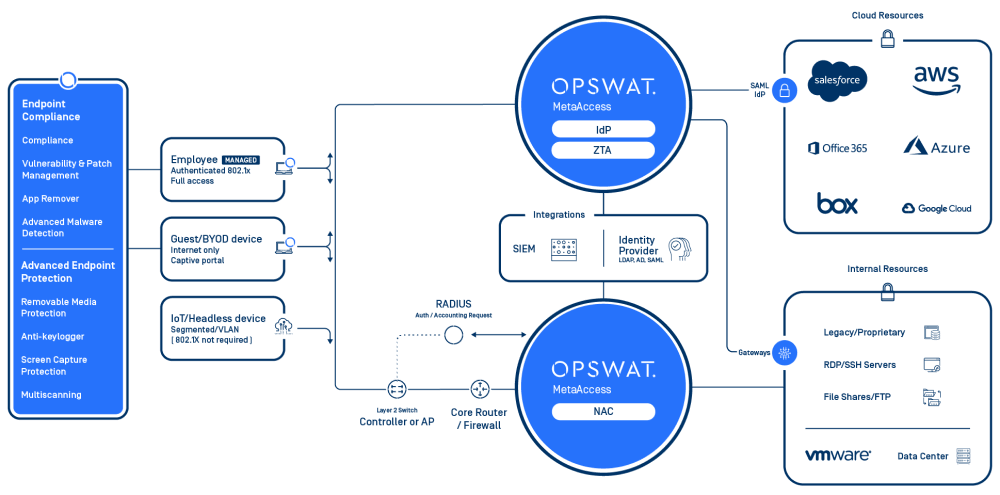
Zero-Trust Security: How Multiscanning and Deep CDR Detect Unknown Threats
Based on the zero-trust security model, OPSWAT MetaDefender Core is an advanced threat prevention solution that detects, analyzes, and eliminates malware and zero-day attacks. Some key features and benefits of MetaDefender Core include Multiscanning and Deep CDR (Deep Content Disarm and Reconstruction) technologies.
OPSWAT Multiscanning allows you to scan files with over 30 anti-malware engines on premises and in the cloud to achieve detection rates greater than 99% by using signatures, heuristics, and machine learning. With Multiscanning, you can avoid exposures caused by the potential limitations of a single vendor, which could be due to a vendor not being allowed to operate in certain geographic regions or government agencies.

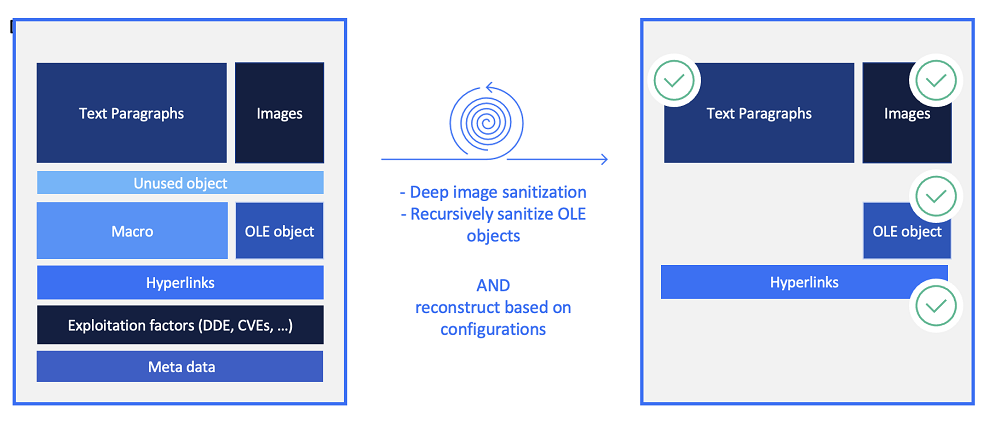
Breaking Down Deep CDR: How It Works
Deep CDR, also known as file sanitization, is the primary driving force behind MetaDefender Core. Just as you should always sanitize your hands to prevent viruses from getting into your household, you should also be sanitizing the files trying to get into your corporate network. If all the files were disarmed before getting into the corporate network, then those files won’t pose a threat once they are inside.

Hence OPSWAT’s philosophy: Trust no File. Trust no Device.

“As malware sandbox evasion techniques improve, the use of CDR at the email gateway as a supplement or alternative to sandboxing will increase”
Fighting Phishing: Optimize your Defense, Gartner.
Known vulnerabilities can be exploited, but there are many unknown attack surfaces as well. Zero-day attacks tend to take advantage of the vulnerability management life cycle (discover, assess, and remediate), so many security defenses won’t be able to detect the attacks. Deep CDR disarms all the media that may be used so that users are in a safe state when they access the files, ensuring strong border security protection.
The following is an example: when there are objects in the file that should not exist in nature, after disarming, the same file can still be used normally, and the armed objects are cleaned and removed.
In March 2022, the Ministry of Internal Affairs and Communications of Japan issued the local government information security policy guidelines. The key point of these guidelines was to pay attention to Local Government Wide Area Networks (LGWAN). They also mentioned the importance of removing risk factors in the exchanges of files and the strengthening the security during file use, further cementing the need for implementing Deep CDR into critical networks.
- ファイルからテキストのみを抽出(Extract only text from files)
- サービス等を活用してサニタイズ処理(ファイルを一旦分解した上で危険因子を除去した後、ファイルを再構築し、分解前と同様なファイル形式に復元する)Sanitize files using security services. (After disarming the file and removing risk factors, reconstruct the file and restore it to the same file format as before)

OPSWAT uses Deep CDR technology to strengthen the security boundary of the enterprise. Now you can apply MetaDefender Core Technology to Email Security, Network Security, File Secure Storage, Kiosk, Vault and other application scenarios. In addition, MetaDefender Core API make it easier to integrate Deep CDR Technology in various environments, such as cloud, on-premises, closed networks, and docker deployment architecture.

If you are interested in setting up a robust security system to protect critical assets, don’t hesitate to contact our cybersecurity experts for more information!

