
In 2012, the infamous Shamoon virus targeted Saudi Arabia's oil industry and wiped the data of over 35,000 PCs. Now a variant of this malware, called "Shamoon 2" by some, is attacking Saudi organizations again, and this time, it's targeting more than the energy and oil sector. These attacks, first reported on Saudi state television on January 23rd, are yet another example of the need for stronger security measures that take user error into account.
According to the Associated Press (h/t Security Ledger), these new Shamoon-related attacks have already struck as many as 15 organizations in the private and public sectors, including one Saudi organization in Australia. Among the victims are the Saudi Labor ministry, Sadara Chemical Co., and the largest state-run Saudi oil company, Saudi Aramco.
During the original Shamoon attack 5 years ago, the cybercrime group known as Shamoon used "Disttrack" malware to wipe data from the victims' PC hard disks. Disttrack can corrupt files and overwrite the master boot record in an operating system. Once compromised, the device is unusable unless its system is reinstalled. These attacks can cause severe data loss for an organization.
According to Symantec, the latest attack targeted a wide range of verticals, including aviation, government, and energy. In addition to destructing data from hard disks, this campaign uses a Trojan called Ismdoor to steal data from its victims too. Symantec suggests that another cybercrime group, Greenbug, may have provided stolen user credentials to Shamoon, who then were able to access users' systems in order to introduce Disttrack.
Security Ledger and CyberScoop posit that Greenbug most likely started stealing user credentials with a spear-phishing email campaign. The Symantec Security Response team explained:
It is believed that the attacks start with an email that asks the recipient to download a RAR archive containing what is purported to be information about a business proposal. These lure documents were hosted on a legitimate website, which may have been previously compromised by Greenbug. The Ismdoor malware is hidden inside the RAR archive using an alternate data stream.
The RAR included a PDF file and a CHM (Compiled HTML Help) file, which contained the hidden Ismdoor Trojan.
Most major organizations educate their users on security to some extent. However, targeted spear-phishing attacks are often well-crafted and personalized, making it possible for even the savviest users to be fooled. Attackers only have to trick one user for the whole corporate network to be compromised. Organizations need a technology solution that altogether prevents these kinds of attacks from being carried out.
That's why Content Disarm and Reconstruction (CDR) is so essential.
CDR is a technology that strips all exploitable content — macros, scripts, hyperlinks — from a document or file (such as an email attachment or a website download), and then reconstructs the file with all its original functionality. OPSWAT MetaDefender offers next-generation CDR technology called data sanitization, which supports 15 file types and over 90 types of file conversions.
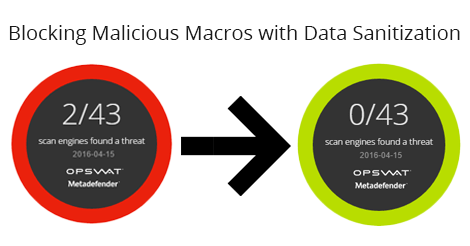
With data sanitization, organizations can eliminate document-based threats and file-borne malware even before they reach an end user. Working together with other prevalent anti-malware technologies such as sandboxes and threat intelligence platforms, data sanitization is a "gate-keeper" helping prevent document-based attacks.
Contact OPSWAT today to learn more about this technology.

