
In early December 2017, OPSWAT announced that OpenDocument Text files are supported in MetaDefender for data sanitization (CDR). Data sanitization, or Content Disarm and Reconstruction (CDR), removes potentially malicious embedded objects from files and rebuilds the files with their original content intact. This process eliminates many concealed cyber attacks “ document-borne malware is extremely common.
We are always improving the quality and coverage of our data sanitization, and today we will demonstrate how MetaDefender data sanitization helps prevent a vulnerability exploit in OpenOffice/LibreOffice. We chose CVE-2017-3157 for this demo, as it is one of the most recent vulnerabilities affecting the ODT file type at the time of publication.
Deep Dive into CVE-2017-3157: Arbitrary File Disclosure Vulnerability
By exploiting the way OpenOffice and LibreOffice render embedded objects, an attacker can craft a document that allows them to read from a file on the user's file system. Information can be retrieved by the attacker by using hidden sections to store the information, tricking the user into saving the document, and convincing the user to send the document back to the attacker.
Users of OpenOffice 4.1.3 and older or LibreOffice before 5.1.6 are affected by this vulnerability.
Below is an ODT file crafted to exploit CVE-2017-3157. When extracting this file, which contains an ObjectReplacement\Object1 file, the content is something like this:
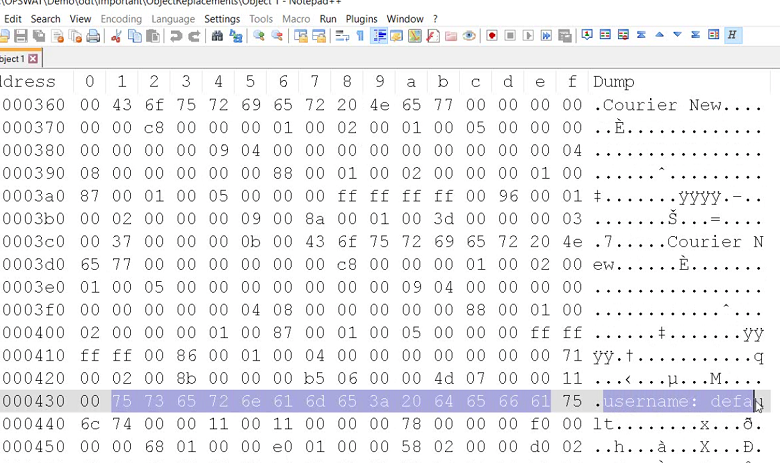

Click images to expand
We can see some information, such as "username: default, password: default."
Also, the content.xml file in the extracted file has a relative link to a specific file.
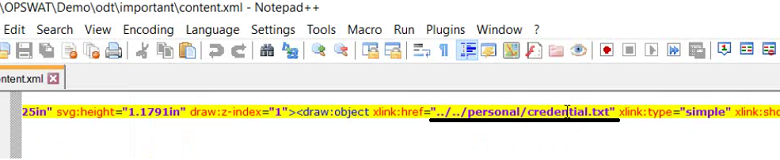
Click image to expand
In this scenario, the attacker knows the file's location on the victim's machine and sets the file path accordingly. This makes the attack tricky, but there are several real-world scenarios in which this is possible. For example, if you download a file, it usually goes to "C:\Users\<username>\download," so the attacker can set the relative path as "../../../Windows/..." to get system file content.
Now, they send a phishing email to the victim, prompting the victim to update the document and send it back to them.
Suppose that this is the credential.txt file content on the victim's machine:
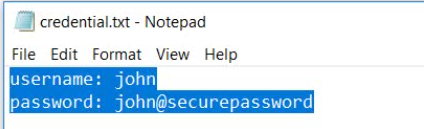
After the user opens the ODT file, updates it, and sends it back to the attacker (as prompted in the phishing email), the attacker extracts the ODT file and checks Object1 again.
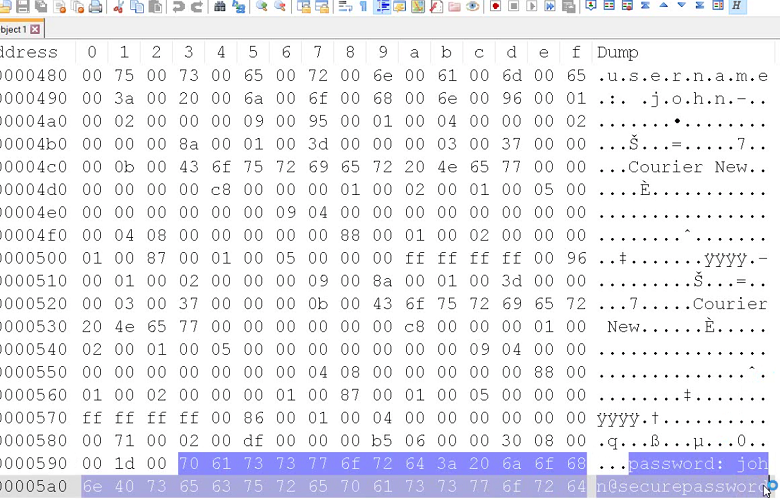
Click image to expand
The attacker can now see the content of the credential.txt file on the victim's machine.
Does CDR work for this CVE?
After sanitizing the file, we extract the sanitized file to see what changed.
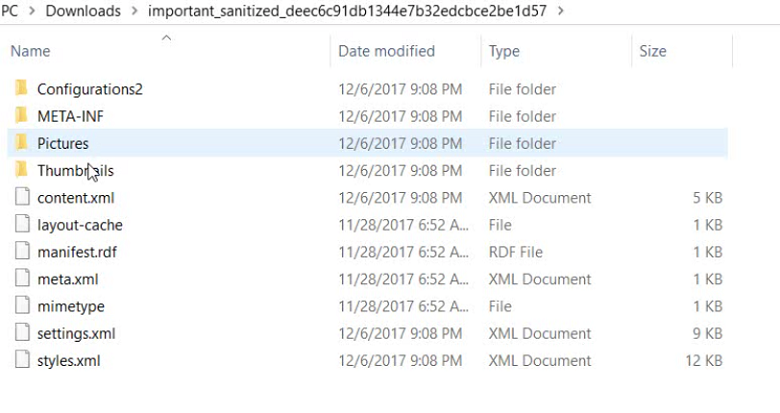
First, we see (above) that ObjectReplacement was removed.
Click image to expand
Second, we see that the relative link in context.xml was removed as well.
So it is safe to open!
The video below demonstrates the entire process.
Conclusion
The first line of defense against malicious files is to always be careful whenever opening a file. Read, think, and if necessary confirm with the sender before clicking on anything such as popups or links, and before enabling advanced features like macros. This level of caution is always necessary.
Besides that, an effective Content Disarm and Reconstruction (CDR) solution that removes malicious content from files is also essential.
We are always adding support for more file types to MetaDefender data sanitization (CDR). We will publish updates to our blog as we add support for more file types. If you have any questions about this technology, contact OPSWAT today.
References
- https://nvd.nist.gov/vuln/detail/CVE-2017-3157
- https://www.openoffice.org/security/cves/CVE-2017-3157.html
- https://www.libreoffice.org/about-us/security/advisories/cve-2017-3157/

