Waiting for public threat feeds to flag a new malware family can leave you exposed for hours. In that gap, campaigns spread, credentials are stolen, and breaches can start to move laterally. This post shows how OPSWAT’s MetaDefender Sandbox (the engine behind Filescan.io) collapses that window with instruction-level behavioral analysis, automated unpacking, and ML-driven similarity search. This gives SOC teams, malware researchers, and CISOs a practical path to earlier, higher-confidence detections.
The Problem: An “OSINT lag” That Attackers Exploit
In today’s threat landscape, the difference between “minor event” and “major incident” is measured in hours. New binaries often circulate well before open-source intelligence (OSINT) catches up, giving adversaries a crucial lead. Our recent research shows:
- 1 in 14 files that public TI feeds initially ignore are actually malicious, exactly the kind of early samples that seed later campaigns.
- Filescan.io surfaces these threats on average ~24 hours earlier than conventional sources, shrinking the window for attackers to entrench.
- All of this is playing out as credential-phishing volumes have surged ~700% and vulnerability disclosures are trending toward 50,000+ in a single year, which expands the attack surface and the number of “first-seen” binaries SOCs must triage.

The takeaway: Waiting for community indicators is no longer a strategy. You need a way to assess risk before a YARA rule lands on a public feed—and to do it at enterprise scale without drowning analysts in noise.
What Changed: Malware is Denser, Stealthier, and More Multi-Stage
Static checks alone struggle against modern evasion. Across samples we see:
- Behavioral gating (e.g., TLS callbacks, geo-fenced payloads, delayed execution) that hide on sandboxes and evade naive detonation.
- Encoding tricks (e.g., UTF-16 BOM markers) that break simplistic parsers.
- Packer inflation (VMProtect, NetReactor, ConfuserEx) wrapping multi-stage loaders that only reveal purpose in memory.
- Fileless tradecraft (PowerShell, WMI) moving the decisive logic into RAM where disk-centric scanners have least visibility.
- Complexity spikes: the average malicious file now drives 18.34 execution nodes (vs. 8.06 last year), reflecting chained scripts, LOLBINs, and staged payloads.
Implication: To win back those 24 hours, defenders need instruction-level behavioral truth with consistent unpacking, memory introspection, and automated correlation that turns early signals into reliable verdicts.
The MetaDefender Sandbox Advantage: Behavior First, Everything Else Second
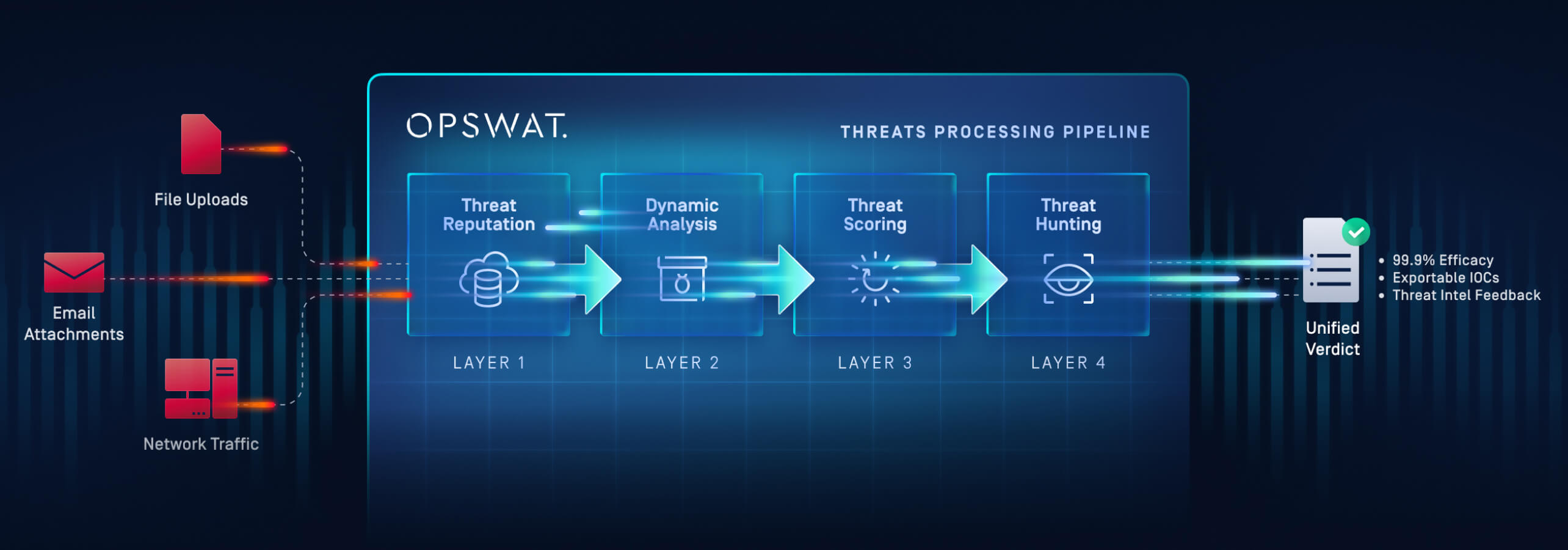
OPSWAT’s MetaDefender Sandbox, the engine that powers Filescan.io, is purpose-built to collapse the OSINT lag by focusing on how a sample behaves, not which signature matches it.
Core capabilities include:
1. Instruction-level emulation to defeat modern evasion - Handles TLS callbacks, timing tricks, and region-locked logic so payloads fully expose themselves. Neutralizes UTF-16 BOM and similar parser traps to keep the full execution path observable.
2. Memory-centric visibility for fileless and staged attacks - Captures in-memory payloads that never touch disk (e.g., PowerShell, WMI), providing artifacts, configuration, and C2s otherwise missed.
3. Automated unpacking of advanced packers - Drills through VMProtect, ConfuserEx, NetReactor, and custom packers to reveal the real code so analysts can triage intent, not wrappers.
4. Rich, explainable outcomes - MITRE ATT&CK mapping, decoded payloads, network traces, and a visual execution graph that documents the entire chain (e.g., .LNK → PowerShell → VBS → DLL inject).
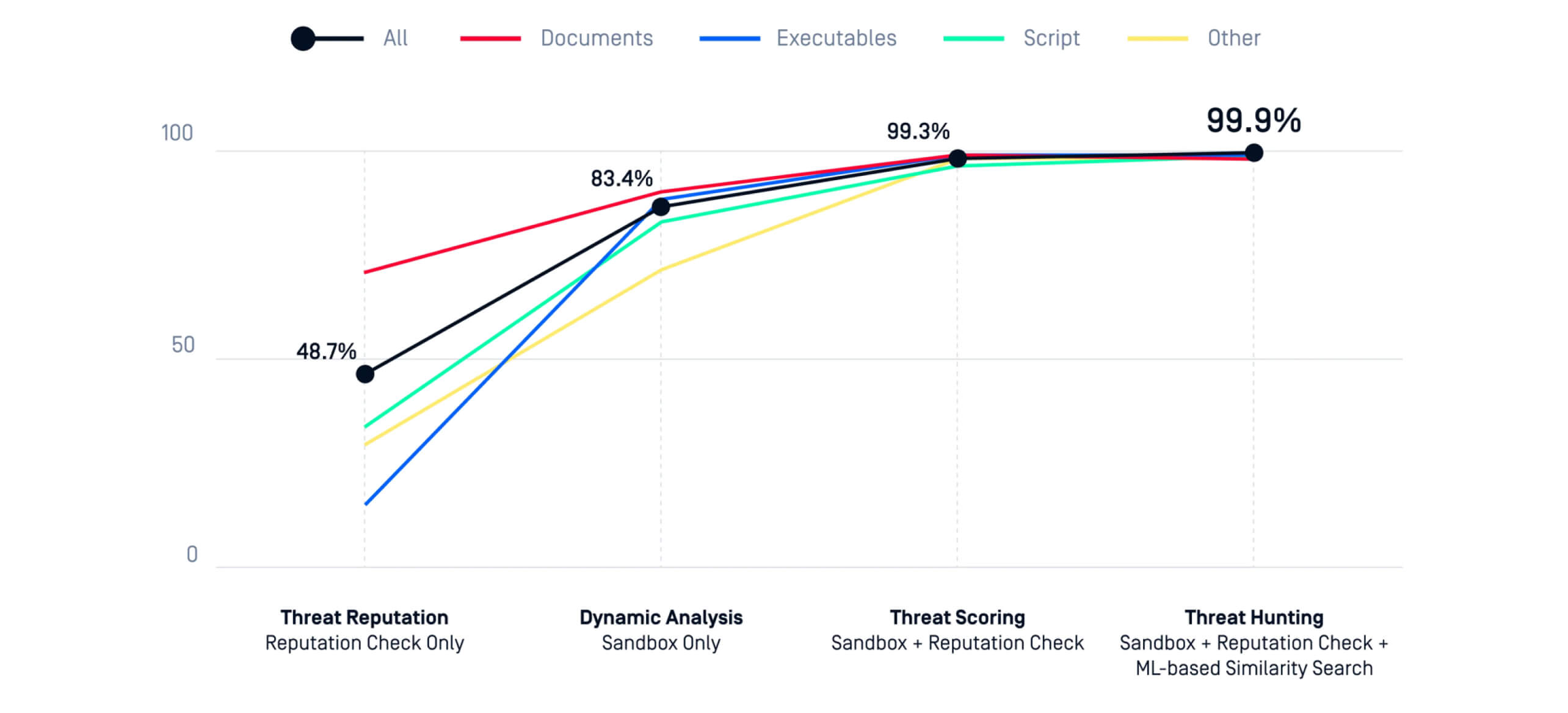
When reputation, behavioral sandboxing, and ML similarity search operate together, organizations achieve 99.9% detection accuracy, combining precision with the timeliness required to beat OSINT by hours.
Filescan.io: Community-Powered Early Warning for Everyone
Filescan.io exposes the same enterprise-grade sandbox to the public—so defenders everywhere can submit suspicious files and see deep behavioral truth in seconds. With a free account, you can:
- Upload and detonate files for full behavioral analysis.
- Inspect decoded payloads and complete network activity; review MITRE ATT&CK mappings for rapid triage.
- Contribute to and benefit from a growing graph of 74M+ IOCs—feeding higher confidence back into OPSWAT’s global Threat Intelligence.
Every public or private scan strengthens the collective signal—and gives you earlier visibility into what’s spreading right now, not what was published yesterday.
From Free Scan to Full Coverage: Integrate Once, Catch Threats Everywhere
Enterprises can embed MetaDefender Sandbox into the live traffic paths where risky files enter:
- ICAP on web proxies and DLP gateways
- MetaDefender Core for orchestrated antivirus and sandbox pipelines
- Managed File Transfer (MFT) workflows to quarantine and analyze at ingress
- Email gateways to detonate attachments and linked downloads before delivery
- Air-gapped deployments for classified or regulated environments that can’t rely on cloud connectivity
What changes on day one:
- Unknowns are auto-detonated and enriched with ATT&CK, C2s, registry/file system changes, and decoded configs.
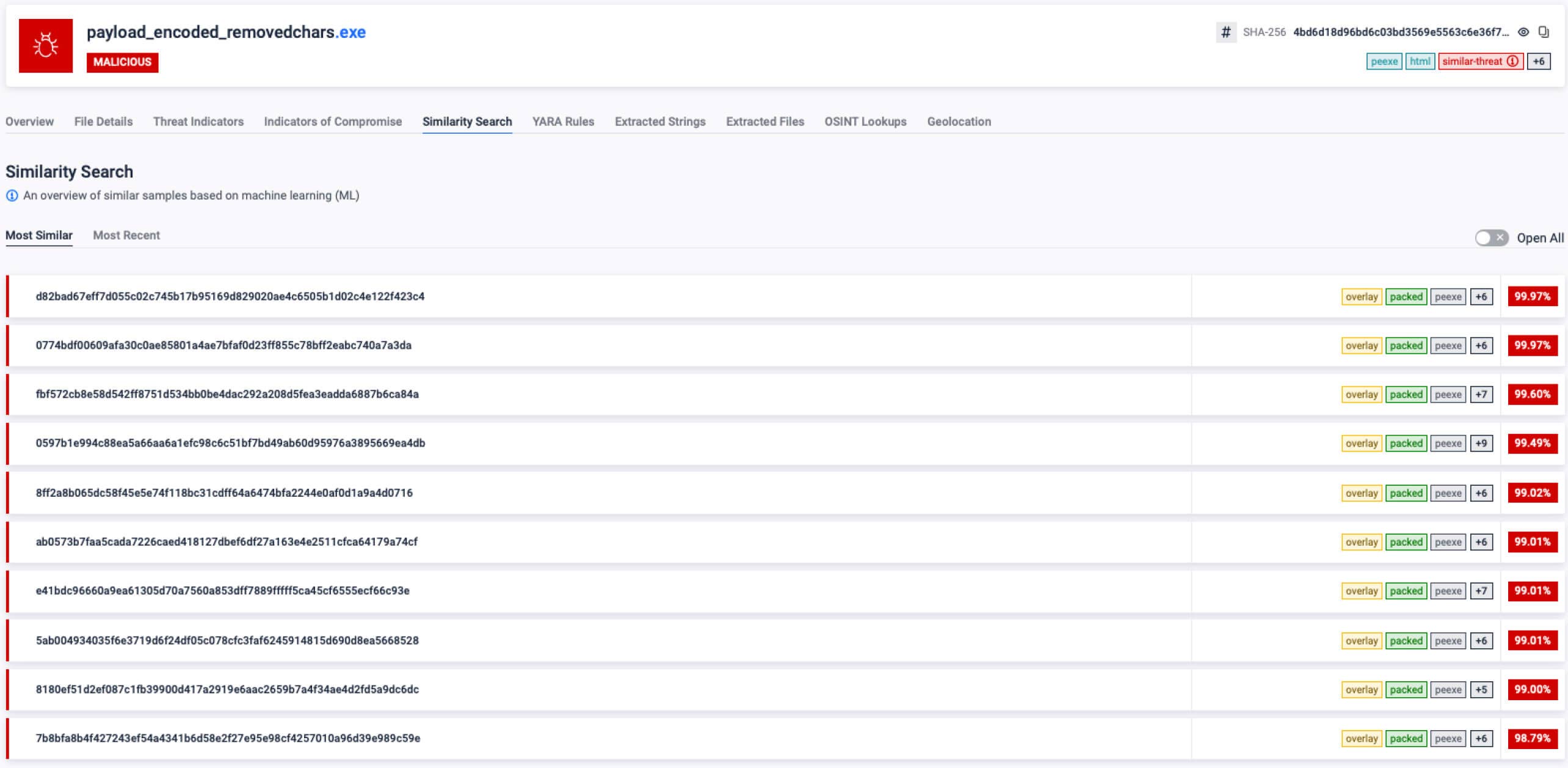
- Similarity search clusters fresh samples with known families/campaigns even when hashes and strings are novel.
- SOC triage shifts from “Is this bad?” to “How bad, how related, and who else is hit?”
Field result: An energy-sector customer integrated MetaDefender Sandbox into file transfer processes and realized a 62% reduction in manual SOC investigations, while blocking targeted attacks that OSINT had not yet labeled.
Role-Based Value: What Each Team Gets on Day One
For SOC analysts & incident responders
- Faster triage: Enriched, behavioral verdicts with ATT&CK tactics reduce guesswork.
- IOC extraction: Automatic pull of domains, IPs, certificates, mutexes, and dropped files.
- Clear visualizations: Execution graphs show what happened and when, ideal for handoffs.
For malware researchers & TI engineers
- Unpacking & decompilation: Get to true code (not just wrappers) for confident family attribution.
- Similarity search: Cluster new samples with historical campaigns by code and behavior, not just hashes.
- Infrastructure reuse hunting: Pivot from one sample to the actor’s broader toolset.
For CISOs & enterprise security managers
- Validated efficacy: Behavior + reputation + ML yields 99.97% accuracy and earlier findings than OSINT.
- Audit-ready: Evidence-rich reports back every decision with artifacts and mappings.
- Scale & flexibility: Cloud or air-gapped, API-first, integrates with existing controls.
For IT & infrastructure teams
- Simple deployment across ICAP, MFT, email, and storage flows.
- Policy automation: Quarantine on risk score; release on clean verdict.
- Operational safeguards: Comprehensive logging and admin tooling for change control.
Real-World Evidence: Early, Explainable Wins That Matter
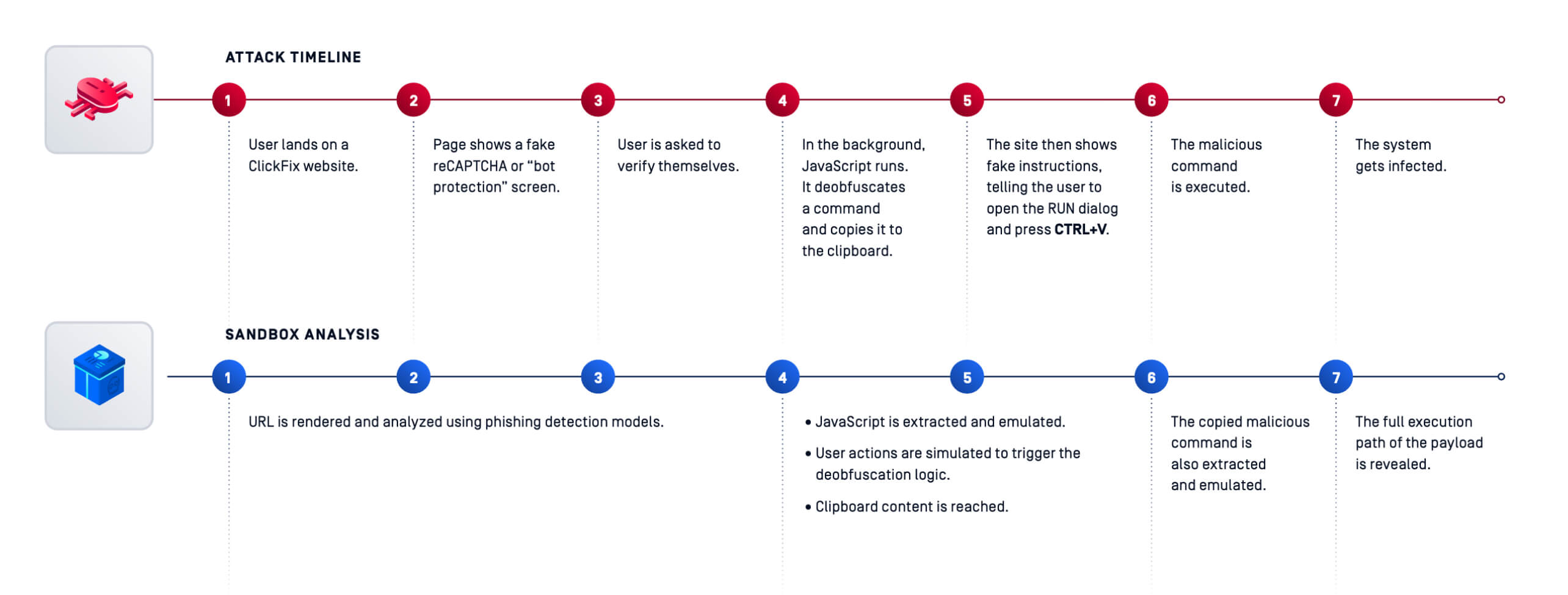
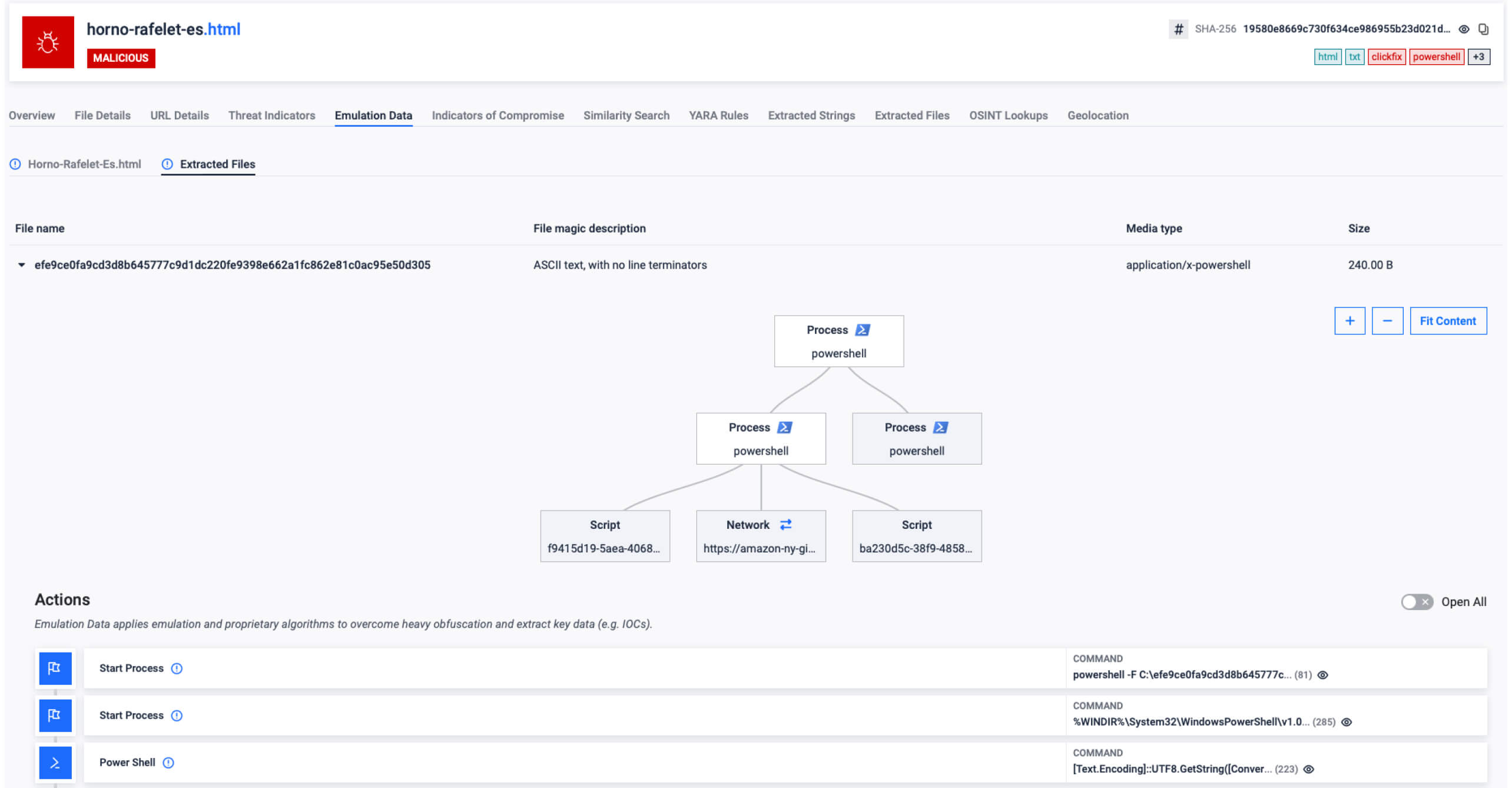
- ClickFix, first to public detonation: Filescan.io quickly detonated and classified the ClickFix clipboard hijacking technique—documenting the end-to-end behavior attackers used to trick users into executing malicious clipboard content. This visibility helped defenders tune detections and uplift user education.
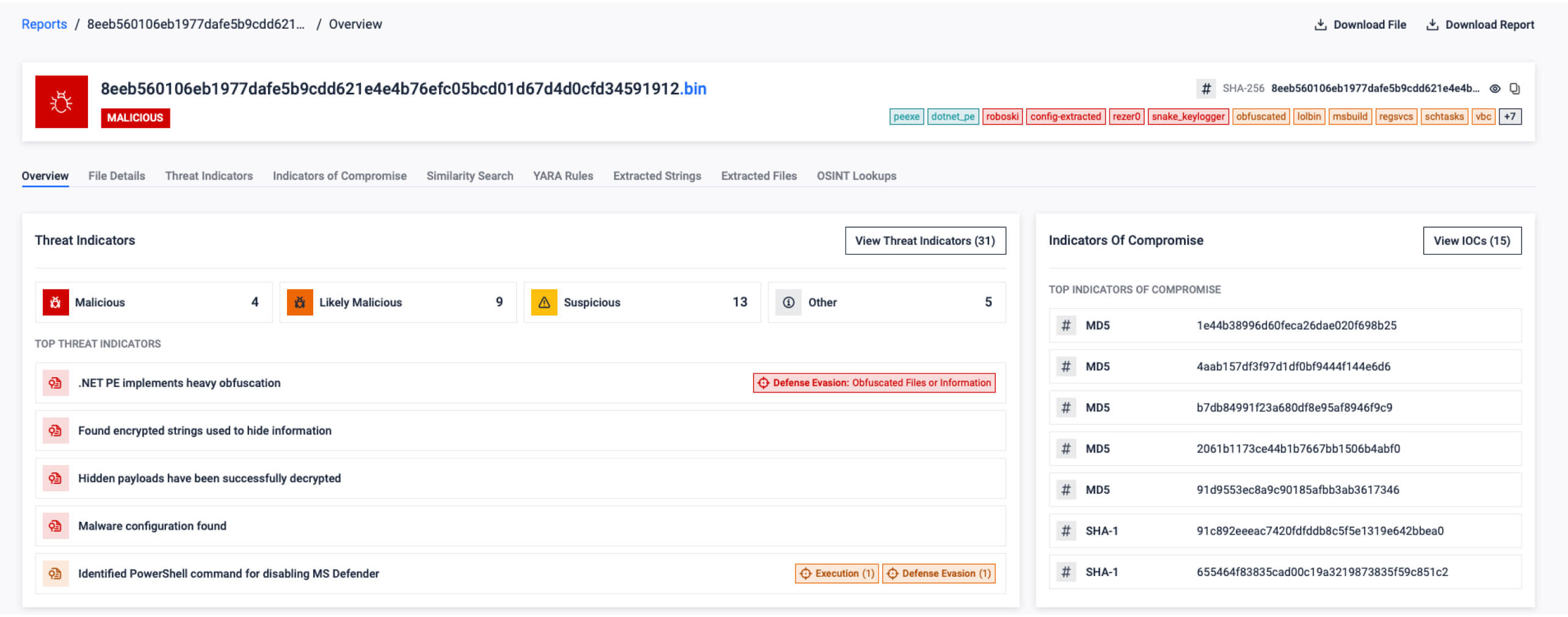
- Snake Keylogger fully unpacked in <40s: A multi-layer Snake Keylogger variant concealed a .NET payload inside a Bitmap. The sandbox peeled back encryption layers, extracted full configuration (including C2s), and generated actionable IOCs without manual RE.
- Reclassifying the unknowns: The sandbox re-labeled ~7.3% of OSINT-“unknown” samples as malicious, with high-confidence behavioral evidence ~24 hours before public YARA hits appeared—time you can spend blocking, not waiting.
Operational Blueprint: How to Collapse the OSINT Lag in Your Environment
You don’t need a rip-and-replace to gain early warning. Start with this phased plan:
1. Detonate by default
Route all inbound file types (especially archives, scripts, and Office formats) through MetaDefender Sandbox at web, email, and MFT chokepoints. Tag results with risk scores and ATT&CK tactics.
2. Automate disposition
Use sandbox verdicts and similarity scores to automate quarantine/release decisions. Forward high-risk behaviors (e.g., credential theft, injection, LOLBIN abuse) to SOAR for containment playbooks.
3. Cluster the novel
When hashes are new, similarity search anchors them to families/campaigns by behavior. This enables faster enrichment and reduces “orphan” alerts.
4. Hunt from behaviors
Build hunts around behaviors (e.g., clipboard command injection akin to ClickFix; suspicious child processes from Office; odd certificate API usage) and enrich with sandbox IOCs across EDR and DNS logs.
5. Measure the delta that matters
Track Mean Time to Detect (MTTD) for unknown threats, measure ‘first-seen to block’ time, quantify manual triage hours saved, and monitor containment Service Level Agreements (SLAs) on sandbox-confirmed threats. Expect a step-function reduction in analyst workload, as demonstrated in the energy-sector example.
Why This Works (and Keeps Working)
Attackers evolve, but behavioral fundamentals don’t. Even as strings, packers, and crypters mutate, payloads still need to:
- Touch credentials, secrets, or tokens
- Persist across reboots
- Talk to infrastructure
- Manipulate the OS in telltale ways
By capturing what the malware must do rather than which signature it matches, you maintain durable visibility—amplified by similarity search that generalizes across “same-actor, new-tooling” evolutions. Add community telemetry from Filescan.io, and your organization benefits from shared early warning without sacrificing local control or privacy.
What You’ll See in Practice
- Cleaner queues: Fewer “unknowns”; more high-fidelity, evidence-backed alerts.
- Faster incident reports: Visual chains, ATT&CK mappings, and decoded configs cut write-ups from hours to minutes.
- Better tabletop outcomes: Executable playbooks tied to specific behaviors (e.g., blocklist based on sandbox C2s, EDR containment on LOLBIN patterns).
- Executive clarity: Audit-ready artifacts and accuracy metrics translate directly to risk posture KPIs.
Call to Action: Find earlier. Act faster.
- Try a free scan on Filescan.io and watch how fast deep behavior, decoded payloads, and IOCs appear.
- Request an enterprise trial of MetaDefender Sandbox to integrate analysis at your web/email/MFT chokepoints and quantify the impact on your MTTD and triage load.
If this is the level of insight we provide for free, imagine the uplift when it’s fully integrated into your pipeline.
Frequently Asked Questions (FAQs)
Where does the research in this blog come from?
From OPSWAT’s internal threat telemetry and sandbox analyses surfaced through Filescan.io, along with findings synthesized for the Threat Landscape work used to inform this post. Specific statistics (e.g., OSINT lag, 7.3% reclassification, 74M+ IOCs, and 99.97% accuracy) come from our program data and engineering validation.
How is “similarity search” different from signatures?
Signatures match known traits exactly; similarity search correlates code and behaviors across related samples, revealing family links even when hashes, packers, or encryption layers have changed.
Can I run this in an air-gapped network?
Yes. MetaDefender Sandbox supports fully disconnected deployments for sensitive or regulated environments while preserving robust analysis and reporting.
What’s the best first integration point?
Email attachments and MFT ingress deliver immediate value: high volume, high risk, and straightforward policy automation based on sandbox verdicts and risk scores.

