
Cyber criminals will use almost any type of file to conceal and deliver malware, often using social engineering to trick users into opening untrustworthy documents and enabling malicious content.
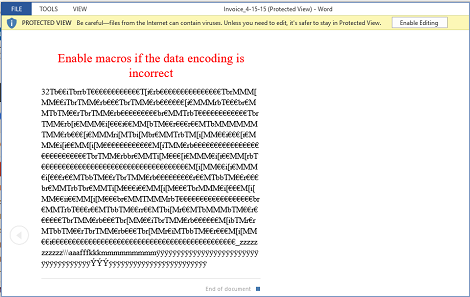
Although the majority of malicious documents in the wild fall within a few categories — Microsoft Office files and Adobe PDFs being the most common — attackers also use images, archives, and other file types to conceal malicious code.
In this paper, we take a look at the ways attackers embed malicious content within these files, and we survey recent incidents from all types of industries when malicious documents were used to breach security defenses. We also examine why users continue to open files from untrustworthy sources, and why traditional anti-malware defenses do not work against file-borne malware attacks.
Contact us to learn more about how data sanitization (CDR) provides the strongest protection against file-borne malware.
Be sure to check out our other white papers as well!

