
SentinelOne researchers recently identified a new variant of Zusy malware that spreads via PowerPoint presentations — without using macros. Zusy, also known as "Tinba" and "Tiny Banker," is a banking Trojan. This new threat vector is an example of malicious documents that don't use macros, and of the need for data sanitization, also known as Content Disarm and Reconstruction (CDR).
Per Eduard Kovacs of Security Week, the malicious PowerPoint files come attached to spam emails with subject lines like "Confirmation" and "Purchase Order #130527," and the files have legitimate-seeming titles like "order.ppsx" and "invoice.ppsx."
Once users download and open the PowerPoint file, they see a hyperlink that says "Loading...Please wait." Passing the cursor over this hyperlink triggers PowerPoint to open an external application that eventually results in the download and execution of the malicious payload (more details of the process at Dodge This Security).
However, before the external application is opened, a popup window from PowerPoint appears asking users if they want to enable PowerPoint to access the application, much like with macros.
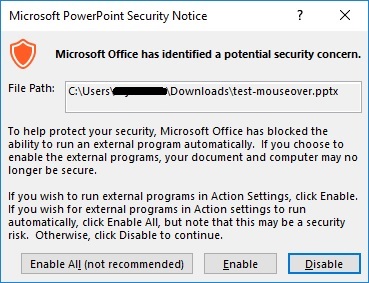
This attack exploits a legitimate feature of PowerPoint. Hovering the cursor over a hyperlink in a presentation can trigger macros, take the user to the next slide, play a sound, open a web page, or open an external application. Most document-based malware attacks via PowerPoint would use macros to download the malicious payload — but now that Office blocks macros by default and more users know not to enable them, attackers are looking for other ways to deceive users.
How to set up a link to an external program on PowerPoint
The malicious PowerPoint presentations are in PPSX format instead of PPTX. PPSX files are read-only and begin playing immediately when opened, instead of opening in the editing view.
In order for the attack to work, users have to:
- Download the file
- Open the file using PowerPoint (PowerPoint Viewer does not open external programs)
- Mouse over the hyperlink
- Enable external programs
It's probable that only a small percentage of users will take all four steps, but it only takes one instance of user error for an entire organization to become infected. What makes this particular attack so dangerous is that even security-conscious users who know not to enable macros or click strange hyperlinks could be susceptible since the attack is not macro-based and users don't even have to click on the hyperlink for the attack to occur.
Even with the best user training, attackers will always find a way to trick somebody.
When Zusy was first detected, it carried out a variety of malicious actions once present on a system, including browser code injections and the theft of banking credentials. Researchers at SentinelOne have not yet determined for sure what exactly this new variant does, but it's likely that it performs similar malicious actions.
How to Protect Users
Malicious content in Microsoft Office documents is not limited to just macros; this much is illustrated by the discovery of this new attack method.
To ensure that users do not unwittingly enable or download malware, organizations should remove the possibility altogether by using data sanitization (CDR).
OPSWAT's data sanitization technology removes potentially exploitable elements from common file types, including PowerPoint presentations. We performed a quick test in which we created a hyperlink within a presentation with the same mouse-over trigger found in the malicious Zusy-downloading PPSX files. After data sanitization, the presentation still attempted to open an external program, but the name of the program had been removed altogether, rendering the action harmless.
Macros, links to external programs, and potentially insecure hyperlinks are all removed by using OPSWAT's data sanitization (CDR).
Data sanitization (CDR) is available for a variety of use cases. Particularly relevant to this attack method is MetaDefender Email Security. MetaDefender Email Security sanitizes all email content, including attachments, rendering malicious attachments like these PowerPoint presentations harmless while preserving file usability.
Contact OPSWAT today to learn more about data sanitization and be protected from this strain of Zusy malware.


