The banking and financial services sector operates in an increasingly hostile cyber environment. While institutions have spent years enhancing their perimeter defenses with the implementation of network security protocols, sophisticated threat actors continue to exploit a critical vulnerability: file-based attack vectors.
Financial institutions process millions of documents daily—from loan applications to regulatory filings—understanding and mitigating file-based threats is essential for maintaining operational integrity and regulatory compliance.
The 10 Cybersecurity Challenges Keeping CISOs Awake at Night
1. File-Borne Malware
Cybercriminals embed malicious code in seemingly legitimate documents - PDFs, spreadsheets, and presentations - that bypass traditional signature-based detection systems.
2. Data Privacy and Compliance Requirements
Compliance frameworks including GDPR, PCI-DSS, SOX, FFIEC, KYC, and AML mandate strict data protection standards while maintaining operational efficiency.
3. Advanced Persistent Threat
APTs (Advanced Persistent Threats) leverage file-based entry points to establish long-term network presence, moving laterally through systems to access high-value financial data.
4. Phishing & Social Engineering Attacks
Malicious actors embed threats within legitimate documents to trick users into opening compromised files, leading to credential theft and network infiltration.
5. Insider Threats
Privileged users handling sensitive financial documents may inadvertently introduce compromised files or fall victim to targeted social engineering campaigns.
6. High Volume and Variety of Files
Financial institutions process diverse file types across multiple channels, from customer-facing portals to internal trading systems. This creates numerous entry points for malicious content.
7. Third-Party & Supply Chain Risks
Third-party vendors and partners introduce files that may contain embedded threats, extending your attack surface beyond organizational boundaries.
8. Complex Security Infrastructure
Disparate security tools and legacy infrastructure create gaps in file inspection coverage, particularly at system integration points.
9. Threat Detection and Response Delays
Outdated tools and limited SOC resources can hinder timely detection. Attackers exploit this gap to stay hidden while exfiltrating sensitive data or executing fraudulent transactions.
10. Recovery Time Objectives
Legacy systems and inadequate disaster recovery plans often prolong downtime after cyber incidents, resulting in financial losses and regulatory penalties.
Debunking Common File Security Misconceptions
Before we dive into solutions, let's address some common misconceptions that could be putting your institution at risk.
"We already have a single antivirus engine with 100% protection"
Even the best antivirus solutions have limitations. New threats emerge constantly and relying solely on one antivirus engine leaves you vulnerable to threats that it hasn't been updated to detect. Conversely, layering multiple AV engines improves threat coverage and resilience.
"We already use network security solutions like WAF, IPS, and proxies to protect our systems"
While these tools are essential for blocking malicious traffic and application-layer attacks like DDoS or CSRF, they aren't designed to inspect the contents of files. Threats hidden inside documents, images, or archives can easily slip through. To stop file-based attacks, you need deep content inspection beyond what traditional network security devices provide.
"Third-party security is the vendor's concern, not ours"
Third-party security is an extension of your organization's own security perimeter. A vulnerability in a partner's system can serve as a direct entry point for attackers to make their path to your infrastructure. Continuously monitor third-party access, enforce strict access controls, and apply zero-trust principles to minimize exposure.
"Traditional sandboxing is enough"
While useful, traditional sandboxes can be slow, expensive, and easily bypassed by advanced threats. Relying on them alone leaves gaps. A layered approach that combines Adaptive Sandbox, DLP (data loss prevention), and CDR (Content Disarm and Reconstruction), offers stronger, more reliable protection against both known and unknown threats.
Building Effective File Security Architecture
So, what's the answer? It's not about finding one perfect security tool—it's about building a comprehensive defense system.
Effective file security in financial services requires a defense-in-depth approach that covers a wide range of attack surfaces. Your security solution must also protect sensitive data throughout its entire lifecycle:

- Ingestion: Screen all incoming files at entry points
- Processing: Analyze content during workflow operations
- Storage: Maintain security controls for archived documents
- Distribution: Ensure safe file sharing and transmission
The organizations getting this right implement zero-trust models and a comprehensive security architecture that combines advanced threat prevention, adaptive threat analysis, data loss prevention, and vulnerability detection capabilities. This creates resilient file security frameworks that scale with your business while maintaining the performance and reliability that financial operations demand.
How Leading Financial Organizations Are Winning the File Security Battle
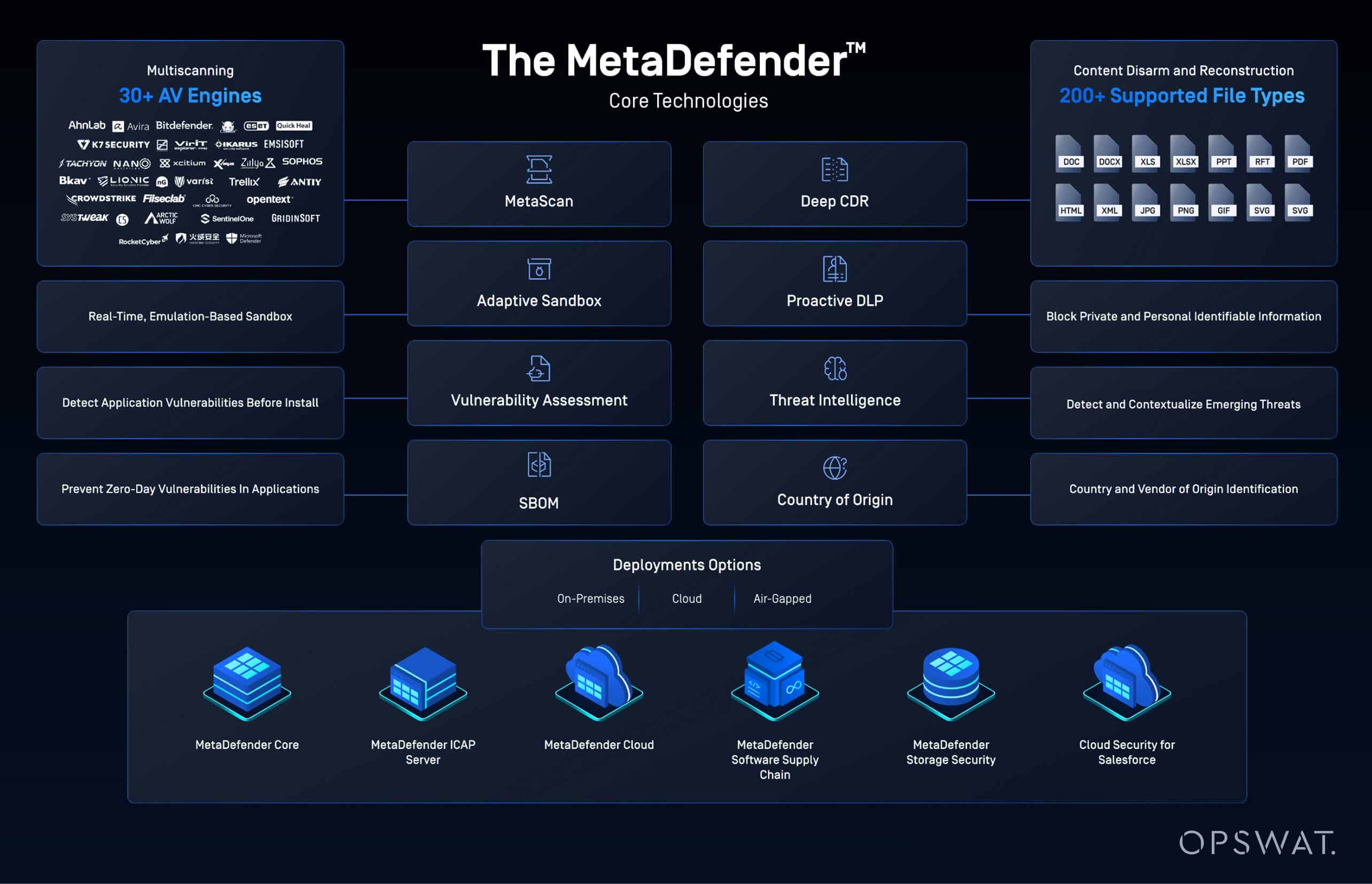
From powerhouses to major banking and financial services players across EMEA, APAC, and North America, OPSWAT solutions are trusted globally to solve file security challenges.
The File Security Proven Deployments in Banking and Financial Services e-book reveals:
- The gap between perception and reality in file security can be the difference between in-depth defense and a catastrophic breach
- Strategy and tailored products/solutions to comprehensively protect your critical data
- Proven real-world deployment stories, with challenges, solutions, and outcomes from different sizes of organizations
Your Next Step
File security isn't just an IT problem - it's a business imperative. The financial institutions that recognize this reality and act on it will be the ones still standing when the next major cyber-attack makes headlines.
The question isn't whether your institution will face a file-based attack. The question is: Will you be ready when it happens?
Talk to an expert today and discover how with OPSWAT in your corner, you can ensure your critical data and networks stay secure.

