OT (operational technology) and CPS (cyber-physical systems) environments, including industrial automation, energy, and critical infrastructure, demand high levels of security, scalability, and efficiency in their network communications. A major challenge is ensuring isolated, controlled, and structured traffic flow between different network segments while enabling seamless communication across multiple VLANs. Double VLAN tagging, also known as Q-in-Q, 802.1ad, or Q-in-Q tunneling, provides an effective solution by encapsulating customer VLANs within a service provider VLAN. This maintains segmentation and ensures reliable data transmission.
Understanding Double VLAN Tagging (Q-in-Q)
Double VLAN encapsulates one VLAN tag inside another, enabling organizations to extend VLANs across network boundaries without interfering with internal VLAN configurations. This technique is particularly useful in industrial setups where network segmentation is necessary to isolate control systems, PLCs, SCADA environments, and operational data.
Key Components of Double VLAN Tagging:
- Outer VLAN (Service VLAN): Managed by the service provider, this VLAN facilitates traffic transport across shared network infrastructure, ensuring customer data remains encapsulated and isolated.
- Inner VLAN (Customer VLAN): The original VLAN tag assigned by the enterprise. It remains intact and is restored at the destination.
By leveraging Q-in-Q, industrial enterprises can scale their networks efficiently while preserving VLAN integrity and reducing operational complexity.
How Double VLAN Tagging Works in Industrial Setups
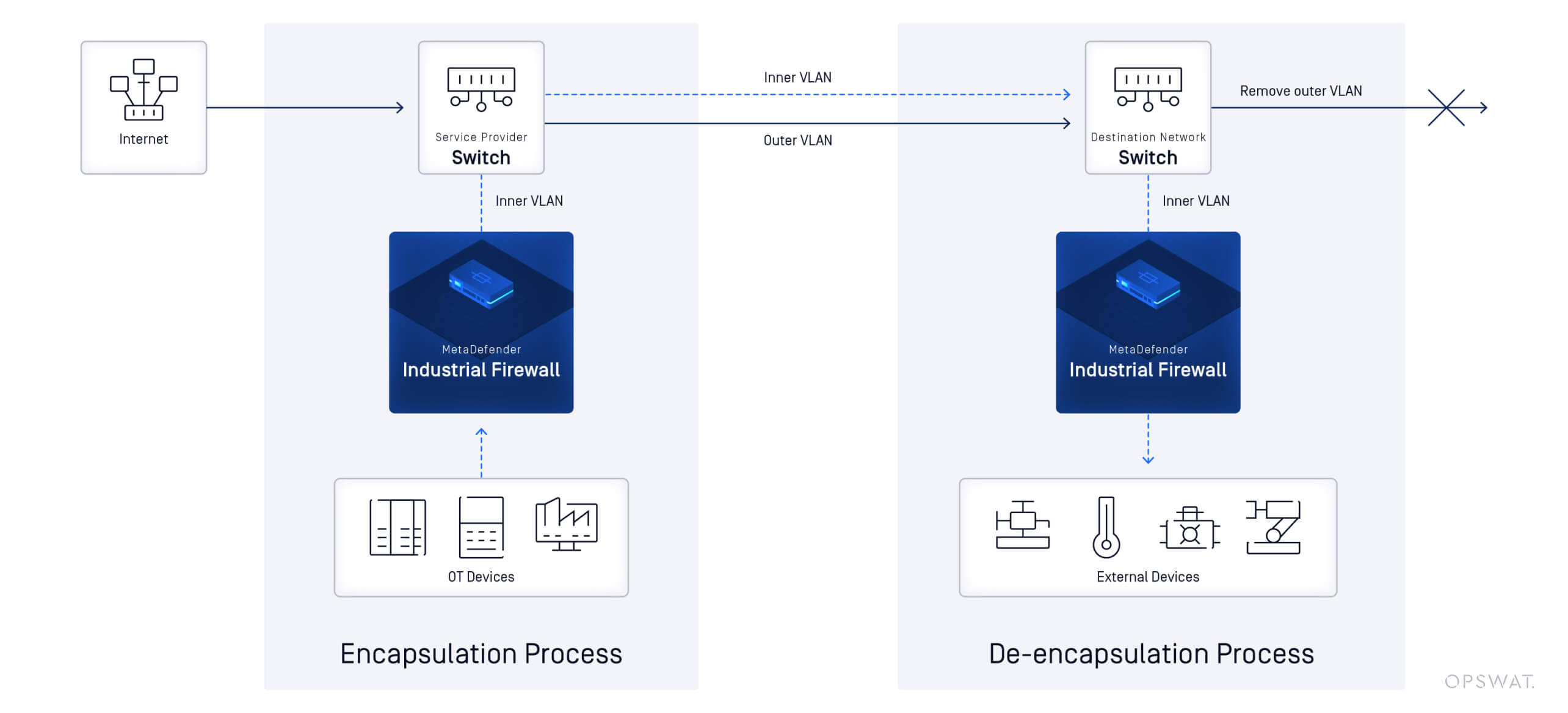
This structured traffic flow allows industrial networks to extend VLANs across multiple locations while keeping each segment manageable.
Benefits of Double VLAN (Q-in-Q) in OT Networks
Traffic Segregation
Double VLAN allows segregation of traffic between different parts of an OT network. This ensures that critical control traffic from PLCs remains isolated from other non-essential traffic, improving reliability and minimizing interference.
Scalability
As OT networks expand, Q-in-Q provides a solution to manage a growing number of VLANs efficiently. It prevents VLAN ID exhaustion, which is especially beneficial for large industrial plants with multiple PLCs and control systems.
Security
By isolating different VLANs within an industrial network, Q-in-Q can enhance and simplify certain network security controls. However, VLANs are not a complete security solution. They are relatively easy to circumvent using techniques such as VLAN hopping.
Simplified Network Management
Q-in-Q enables the creation of a structured VLAN hierarchy in industrial networks. This simplifies network configuration, reduces operational complexity, and makes troubleshooting more efficient.
Vendor Independence
As part of the widely adopted IEEE standard 802.1Q (2011), Q-in-Q is supported by multiple networking vendors. This allows industrial operators to integrate different hardware and still maintain uniform traffic segmentation and management.
Use Cases for Double VLAN Tagging (Q-n-Q) in OT Environments
- Service Provider Bridging: Q-in-Q enables communication between different industrial sites by extending Layer 2 VPNs across large-scale OT networks.
- Industrial Automation: Manufacturing plants and energy grids use Q-in-Q to segregate traffic between automation devices and control systems, ensuring seamless operation.
- Smart Grids: Q-in-Q helps manage traffic between substations and control centers, maintaining efficient communication in smart grid deployments.
- BMS (Building Management Systems): Industrial campuses use Q-in-Q to isolate traffic for HVAC, lighting, and security systems, ensuring proper functioning.
- Transportation Systems: Q-in-Q supports data transmission across various transportation networks, including railway control systems, ensuring uninterrupted operations.
Example Network Topology
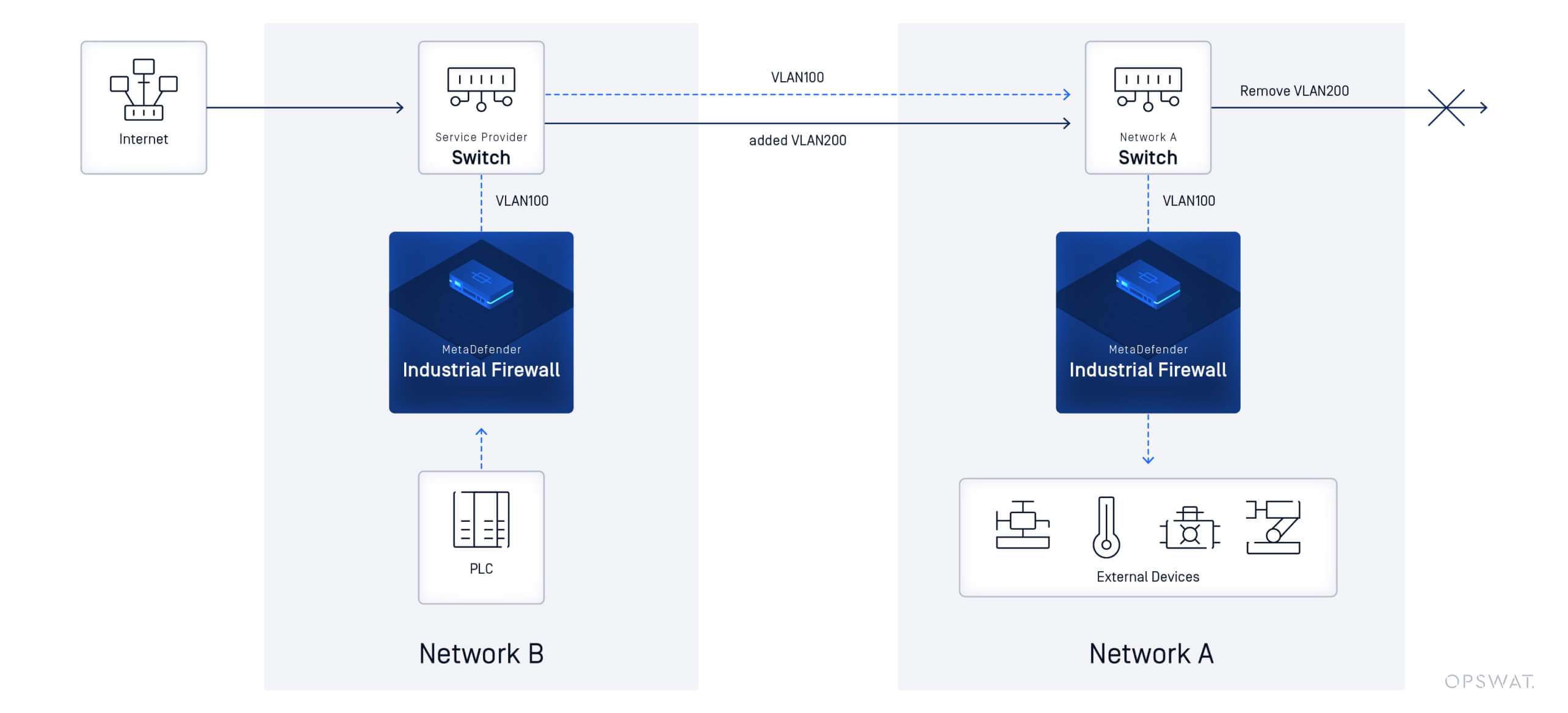
Consider a factory with the following setup:
1. Devices: PLC (server), Industrial Firewall, and clients on Network B.
2. Network Segmentation:
- Network A: VLAN 100 (PLC resides here) - 192.168.10.0/24
- Network B: VLAN 200.100 (HMI or external device) - 10.10.10.0/24
- Industrial Firewall: Interfaces in both networks, translating traffic between them.
3. Traffic Flow:
- Devices on Network B send traffic tagged with VLAN 100.
- The firewall or service provider switch adds an outer VLAN tag (VLAN 200).
- The packet travels across the network while keeping VLAN separation intact.
- On reaching Network A, the outer VLAN tag is removed, restoring VLAN 100.
- The PLC can now communicate with external devices without internal VLAN modifications.
Conclusion
Double VLAN tagging is a powerful technique for organizations that require VLAN scalability, isolation, and data transfer over shared infrastructures. In industrial and OT environments, Q-in-Q ensures seamless and efficient VLAN management, enabling flexible and cost-effective networking solutions.
Industrial Firewall™
Unlock secure and segmented OT/ICS communication with Q-in-Q – without sacrificing performance. Discover how MetaDefender Industrial Firewall can strengthen your industrial network.
Frequently Asked Questions (FAQs)
Q:What is double VLAN tagging (Q-n-Q)?
A: Double VLAN tagging, also known as Q-in-Q, encapsulates one VLAN tag inside another to extend VLANs across networks while preserving segmentation. It is particularly useful in industrial environments where network segmentation is critical for isolating control systems, PLCs, SCADA environments, and operational data.
Q:How Secure are VLANS?
A: VLANs can improve network security by logically segmenting traffic and limiting broadcast domains, which helps reduce the risk of unauthorized access between segments. However, VLANs are not inherently secure. They require careful configuration to effectively prevent attacks like VLAN hopping or unauthorized access.
Q:What is VLAN hopping?
A: VLAN hopping is a network security vulnerability where an attacker exploits weaknesses to gain unauthorized access to one VLAN and then pivot to others within the same network. VLANs are meant to improve security and performance by isolating traffic between different segments. VLAN hopping undermines this separation, allowing attackers to bypass controls and potentially access sensitive systems and data that should remain protected and isolated.

