We will explore the types of threats attackers can hide in media or video files, such as WMV files, to launch attacks and download malware. Additionally, we look at how to reduce the risk of these attacks with OPSWAT technologies by detecting, preventing, and analyzing file-based threats.
Table of Contents:
- Video File Attack Techniques
- How Opening a Video File Can Trigger Malware Download
- How to Remove Malicious Objects with Deep Content Disarm and Reconstruction Technology
- How to Detect and Uncover Evasive Malware with Adaptive Threat Analysis
- OPSWAT Advanced Threat Detection and Prevention

Video File Attack Techniques
A few years ago, we published a blog post highlighting the risks of video files and how attackers use them to deliver malware. We discussed two tactics: vulnerability exploitation and abuse of legitimate features.
Exploit a vulnerability
File type verification validates the file type. We can’t trust the Content-Type header or extension name that defines the file type, as they can be spoofed. Unfortunately, many media players don’t strictly verify the structure of video files, leading to several exploitable vulnerabilities.
For example, VLC Media Player 3.0.11 had the CVE-2021-25801 that allowed attackers to cause an out-of-bounds read via a crafted AVI file, which reads data from a buffer outside of its intended boundaries, causing crashes, incorrect program behavior, or disclosure of sensitive information. The CVE-2019-14553 in VideoLAN VLC media player 3.0.7.1 can cause a use-after-free vulnerability—a type of memory corruption flaw in which an application attempts to use freed memory, resulting in crashes, unexpected results, or executing malicious payloads.
Abuse a legitimate feature
Another attack technique abuses a legitimate media player feature to deliver malware through videos. For example, attackers can exploit the Script Command feature in Windows Media Player by embedding malware within a hyperlink in the video.
How Opening a Video File Can Trigger Malware Download
The demo below shows how a victim can unintentionally download malware on their device by opening a video file.
This technique demonstrates how attackers abuse a legitimate feature as an attack vector. Script Command is an essential feature of Windows Media Player—it allows the media player to interact with a browser while playing a file to download video codec or tracking. Despite its potential for exploitation, Script Command is an essential feature of Window Media Player. A WMV video file is based on the Microsoft Advanced Systems Format (ASF) container format and compressed with Windows Media compression. ASF can contain a Script Command Object used to stream text and provide commands that can control elements within the client environment.
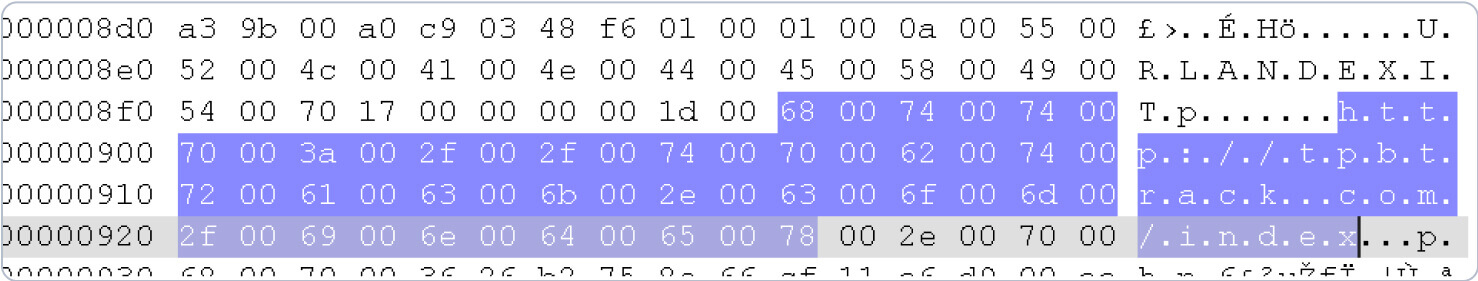
ASF allows simple script commands such as URLANDEXIT, which automatically launches a URL embedded within the video file in a default browser when executed. Threat actors exploit this feature to prompt the victim to download a malicious file masquerading as a plugin, update, or codec required to play the media and compromise the user’s system.
In this example, the attacker had inserted a malicious URL into a legitimate media file.

We can view the URL with a hex reader application:
How to Remove Malicious Objects with Deep Content Disarm and Reconstruction Technology
Deep CDR (Content Disarm and Reconstruction) treats every file as a potential threat. It processes and analyzes files to remove unapproved objects to ensure all files coming into your organization are safe to consume. At the same time, Deep CDR reconstructs the file content for full functionality so that users can view the video without downloading malware.
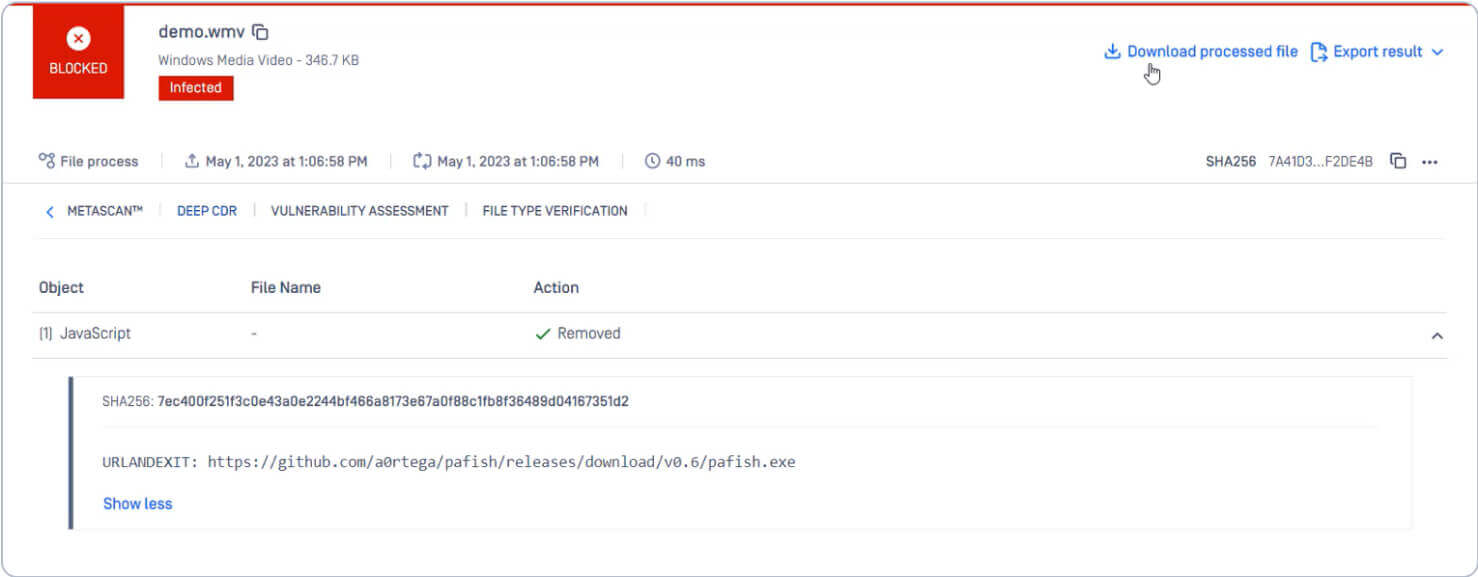
Processing the infected file with MetaDefender Core detects the URLANDEXIT command in the file.
Deep CDR removes the URLANDEXIT object and the Script Command Object. The new, reconstructed file remains fully usable. The attackers are unable to download malware.
How to Detect and Uncover Evasive Malware with Adaptive Threat Analysis
We can scan the file with MetaDefender Sandbox sandbox adaptive threat analysis engine to dive deeper into the malware's behaviors and capabilities.
MetaDefender Sandbox is a next-generation sandbox that utilizes adaptive threat analysis, enabling zero-day malware detection, more Indicator of Compromise (IOC) extraction, and actionable threat intelligence.
We get deeper insights into the threat by processing the WMV file with Deep CDR and Filescan. Filescan downloads the file from URLANDEXIT and performs static analysis to provide more details on the malware's behavior, tactic, technique, and IOCs.

OPSWAT Advanced Threat Detection and Prevention
OPSWAT advanced technologies protect applications, networks, and devices from zero-day attacks, evasive malware, and advanced targeted attacks. Besides media files, Deep CDR also recursively scans and sanitizes more than 130 file types, including complex ones such as nested archives, email attachments, embedded documents, and hyperlinks. The reconstructed file remains fully usable and functioning.
Contact one of our technical experts to learn more about Deep CDR, Filescan, and other threat-prevention technologies.

