Understanding the Complexities of Email Security
The ever-evolving landscape of email security has encountered new challenges beyond the traditional realms of encryption and spam filters. Advanced email threats are increasingly becoming successful at bypassing conventional email security defenses including those of Microsoft 365.
From sophisticated phishing tactics to evasive malware, email threats often disguise themselves as legitimate communications or use advanced techniques to slip through the security gaps. As a result, protecting email systems now demands a multi-layered proactive approach that deals with threats before they enter an email system.
Attachment-based Security: A Critical Concern
In terms of email-based threats, attachments top the list. We often come across Word documents, PDFs, and spreadsheets as attachments in our daily communication. But did you know these are also the most common vectors used in cyberattacks?
Given their ubiquity in business communication, it’s impractical, if not impossible, for organizations to block such file types. While malware scanning and content filtering can weed out threats, they are not as strong against zero-day attacks - threats that have been recently discovered or are unknown.
The most robust defense strategy an organization can adopt is to assume every attachment is malicious. This means dynamically analyzing them, neutralizing threats and sanitizing the files by stripping them of potentially malicious content. After these steps are taken, the harmless attachment is allowed to reach the end user.
Navigating the Tricky Terrain of URL-based Security
Hyperlinks or URLs in emails present a security challenge similar to attachments. They can easily mask malicious sites, but outright blocking of URLs would cripple modern communication. This is where advanced email security solutions come into play. These solutions analyze URLs, checking if they lead to malicious or suspicious sites.
Machine learning has emerged as a powerful ally in this fight, helping model what “good” URLs look like and spotting anomalies. Not only is this technique effective against malware, but it’s also a formidable tool against spam, ensuring minimal false positives.
Email Security Best Practices: A Technology Checklist

Phishing Attack Defense
Multi-layered detection with advanced heuristics and machine learning algorithms can be employed to detect malicious emails. Furthermore, replacing harmful links in emails with ones that undergo real-time reputation checks can neutralize threats.

Zero-Day Attack Mitigation
Deep Content Disarm and Reconstruction (CDR) technologies are pivotal in defending against unknown threats. They sanitize email attachments by eliminating embedded threats. The cleaned-up, usable file is then delivered to the end-user.

Multiscanning
Using multiple anti-virus engines can significantly improve malware detection rates from an average of 45.4%, with a single AV engine, to 99.39%. This multi-engine approach, combined with signatures, heuristics, and machine learning, ensures that threats are promptly detected and addressed.

Real-time Sandbox
With a 10x faster performance than a traditional sandbox, a real-time sandbox can uncover unknown and zero-day threats in Microsoft Office documents, PDFs, and other file types before the user clicks on them.

Data Loss Prevention (DLP)
With regulations like PCI, HIPAA, and GDPR, organizations have a responsibility to protect data like Personally Identifiable Information (PII) and Patient Health Information (PHI). Controls should be in place to redact sensitive information in emails, ensuring compliance and preventing breaches.
To learn more on how to prevent malicious email attacks, download this whitepaper that focuses on threats challenging conventional email security systems.
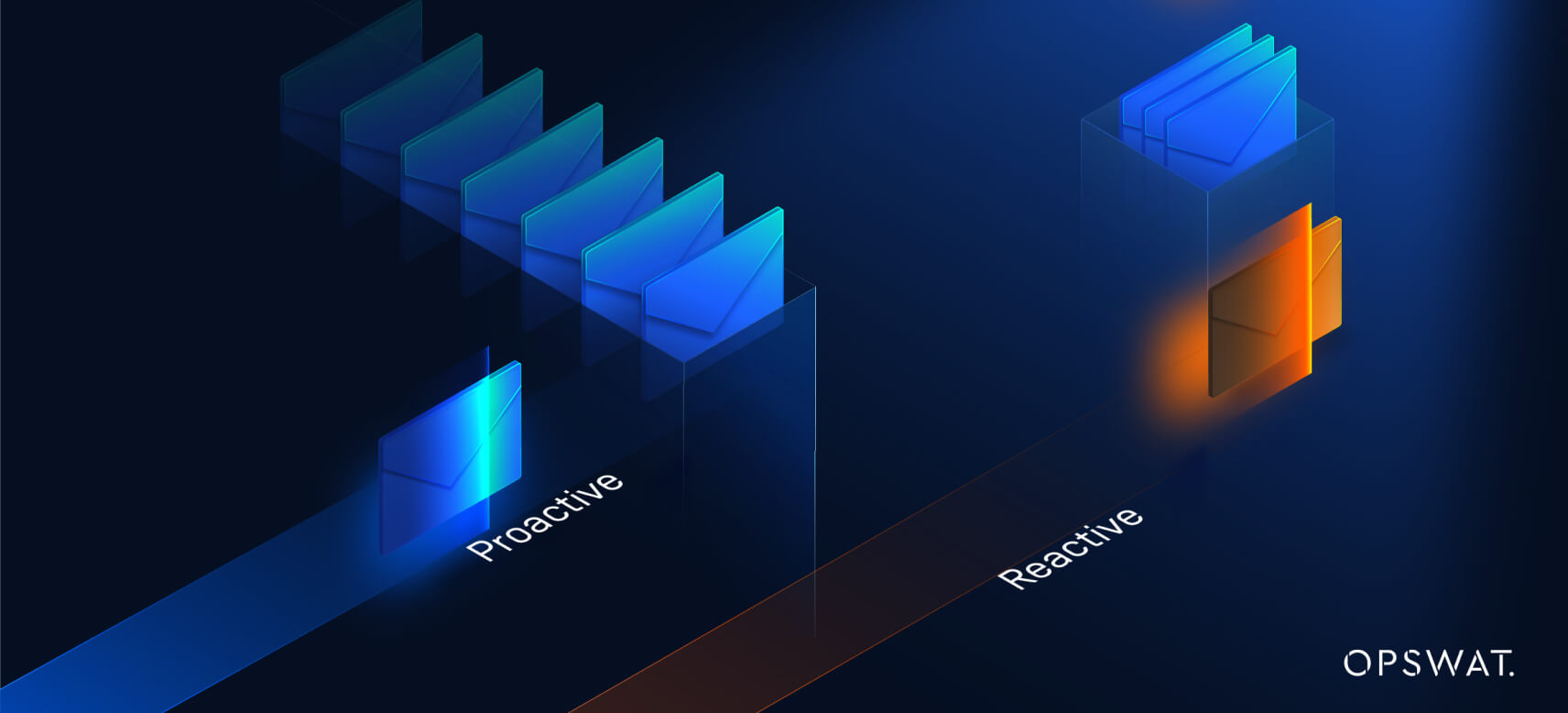
OPSWAT’s Proactive vs. Reactive Email Security Approach
In the crowded landscape of email security vendors, OPSWAT stands out with its proactive approach, setting it apart from competitors that largely rely on detection-based methods. While many vendors focus on identifying and responding to threats after they’ve entered an email system, OPSWAT neutralizes threats before they can enter and cause harm.
This zero-trust approach is akin to stopping a potential intruder at the gates rather than dealing with the aftermath of a breach.
OPSWAT’s Multi-layered Defense Strategy
Another distinguishing aspect of OPSWAT’s approach is its multi-layered defense strategy. Recognizing that no single solution is a silver bullet for the multi-faceted challenges of email security, OPSWAT employs a combination of advanced market-leading technologies.
From Deep Content Disarm and Reconstruction (Deep CDR™ Technology) that sanitizes potential threats in email attachments to real-time URL reputation checks and machine learning anomaly detection, OPSWAT offers a comprehensive suite of solutions that work in tandem to provide robust email protection.
In contrast to vendors that play a reactive game of catch-up with cyber threats, OPSWAT’s proactive and holistic methodology positions it as a leader in the email security domain, ensuring businesses can communicate with confidence and security.

