In the digital collaboration rush, organizations are managing an ever-growing volume of data across multiple cloud environments, often reaching petabytes in size.
While speed and flexibility are critical, one thing is often overlooked—how secure are those files, really?
Without the right defenses in place, even the best cloud workflows can leave data exposed to threats.
This article dives into the often-underestimated risks of cloud file security and uncovers practical solutions to mitigate them.
Discover how to protect your data without compromising the pace or efficiency your business demands.
Common Challenges in Securing Cloud-Based Files
Managing File Distribution Across Cloud Environments
Organizations, especially those at the enterprise level, struggle to manage files across different cloud platforms.
Storage isn't limited to a single location—it's spread across multiple tools, stages, and systems, which makes it difficult to get a complete view of all associated risks.
In fact, a single file might trigger different alerts or be flagged with varying levels of risk depending on the tool being used, making it hard to keep a consistent security approach.
To add another layer of difficulty, global compliance laws require businesses to update their approach to file management based on the region or country.
This can create confusion and inconsistencies when it comes to meeting local data protection standards.
Without a clear approach to file distribution that ensures visibility, businesses risk compromising both security and compliance.
Handling Risks of Unstructured Data

Normally, every organization hosts two data types: structured, and unstructured.
Structured data is predictable as it comes in clean, organized formats such as online forms, network logs, or transaction systems.
It's easy to categorize, analyze, and assess for potential risks.
With this data, SOC teams can efficiently evaluate file-borne threats and apply standardized protection measures.
Unstructured data is a different story.
It comes from a variety of sources—messaging platforms, documents, social media, emails, and even multimedia files like images and audio.
It’s often scattered across different formats (PDFs, JPEGs, MP3s, etc.), making it harder to process and manage.
Many of these files never even make it to workstations or endpoints, creating blind spots in your security strategy.
Securing unstructured data requires an approach that can handle its complexity, diversity, and the fact that it often exists outside of traditional security boundaries.
Dealing with the Variety of File Formats in the Cloud
Every file format (PDF, image, video, audio file etc.) adds its own layer of risk and the more file types you manage, the more potential vulnerabilities you face.
Let’s start with (AV) antivirus software.
It’s a common, trusted tool for scanning files, but it doesn’t cover all potential risks.
AV software is good at flagging known threats, but it won’t look at certain elements like embedded URLs or scripts within files. If those lead to a malicious action, your AV might miss them altogether.
Then there’s sandboxing, where files are run in an isolated environment to see if they behave maliciously.
This method works, but the trade-off is time.
Sandboxing can take a couple of minutes per file.
When you’re processing thousands of files every day, those minutes add up, creating a bottleneck that can slow down operations.
Productivity takes a hit, and threats can lurk around longer than they should.
The situation is aggravated by content risks.
A file might look perfectly safe, but certain file types—like PDFs or images—can be modified to hide malicious content.
Take invisible text in PDFs (text in white on a white background), for example.
This tactic can fool systems that rely on content scans, like AI-driven resume reviewers or fraud detection systems, and it can fly under the radar of AV software and sandboxes.
Securing Collaboration in SaaS Platforms
Migrating to SaaS platforms is a standard move for businesses—and for good reason.
These tools are easier to manage, faster to implement, and eliminate the need for in-house maintenance.
However, as data gets moved from on-prem to cloud environments, the challenge becomes managing the vast dispersion of that data.
With companies using tools like Zoom, Teams, and Salesforce, data is spread across multiple platforms, often beyond the organization’s full oversight.
Each of these platforms takes a unique approach to threat prevention, focusing on different areas like web traffic, email, or internal communications.
This makes it difficult to ensure that all SaaS platforms are providing consistent and comprehensive security for the files they store and share.
Protecting Files in the (SDLC) Software Development Lifecycle
Organizations are eager to implement new AI technologies as quickly as possible.
In this rush to stay competitive, speed often becomes the priority, and crucial steps can get overlooked. People are frustrated by slow adoption processes, leading them to skip necessary approval checks and turn to faster solutions.
This rush can introduce significant risks.
Malicious libraries from third-party repositories, for example, can inadvertently make their way into development environments, opening the door to vulnerabilities.
The larger the organization, the more complex the ecosystem—and the harder it becomes to maintain control over your sources and ensure that all components are secure.
Key Strategies for Securing Cloud Files
Look at the Entire File Analysis Pipeline
As we’ve established, for cloud-based files, a singular security approach is rarely enough.
To effectively protect them, organizations need to consider every step of the file analysis process, making sure the right actions are taken depending on the file type.
Start by applying a file-by-file analysis method—one that considers the specific risks of each file.
For example, a software update, like Zoom, might require several checks, such as malware scans, multiple antivirus scans, file vulnerability assessments, and sandboxing to test the file in an isolated environment.
At the same time, file types like PDFs require a different set of security measures: (CDR) Content Disarm and Reconstruction to remove any harmful content without changing the file itself, or Proactive (DLP) Data Loss Protection measures to ensure that no sensitive data is leaked through these files.
The main idea is to identify the right action for each file, based on its characteristics and risks so potential threats are treated in a way that aligns with the specific file’s behavior.
Securing All Data Entry Points
Securing every data entry point into your cloud environment is just as important.
Files can enter your system in many ways—through email attachments, APIs, file uploads, downloads, or cloud storage—and each of these channels can open the door to threats.
Make sure every entry point is secure and monitored.
For example, email filters should scan attachments before they're opened or downloaded and APIs used for file transfers should have strong security protocols in place, including encryption and proper authentication.
Use Multiscanning for Complex Protection
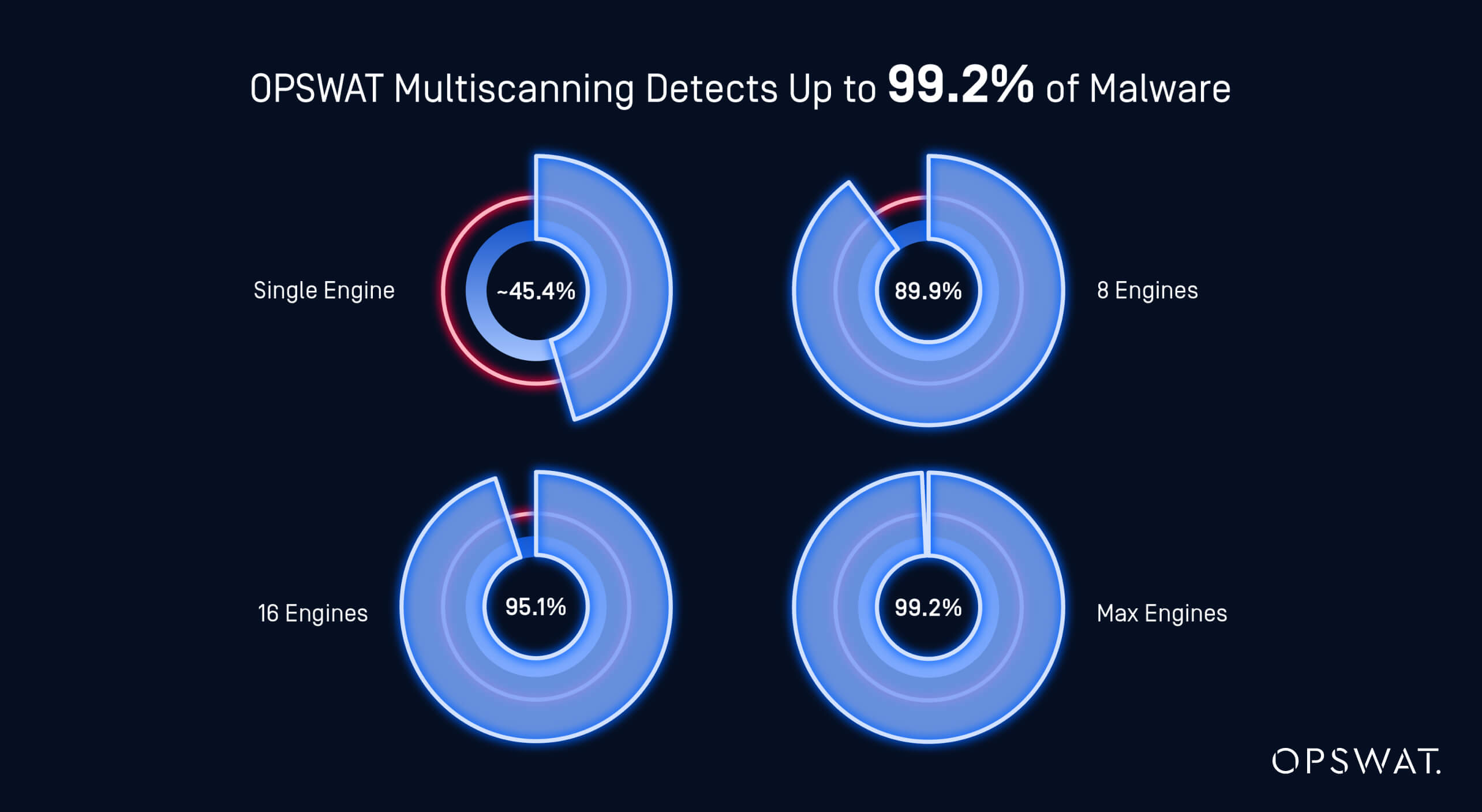
To improve the chances of detecting threats, organizations should use multiscanning, which involves scanning files with multiple (AV) antivirus engines.
The more AVs in use, the better the detection rate.
This approach helps cover a wider range of threats and reduces the risk of missing malware or other harmful content.
AVs should run scans either within your own environment or in a secure cloud environment, ensuring that no sensitive data leaves your system.
When the scans are done in the cloud, the data is processed and then deleted, so there is no transfer of private information to external AV databases.
OPSWAT’s MetaDefender Cloud Platform uses 20+ industry-leading anti-malware engines such as McAfee, or Bitdefender, using signature, heuristics and machine learning and the AVs are updated daily.
This mix of scanning methods improves the chances of detecting even new, sophisticated threats.
Implement CDR
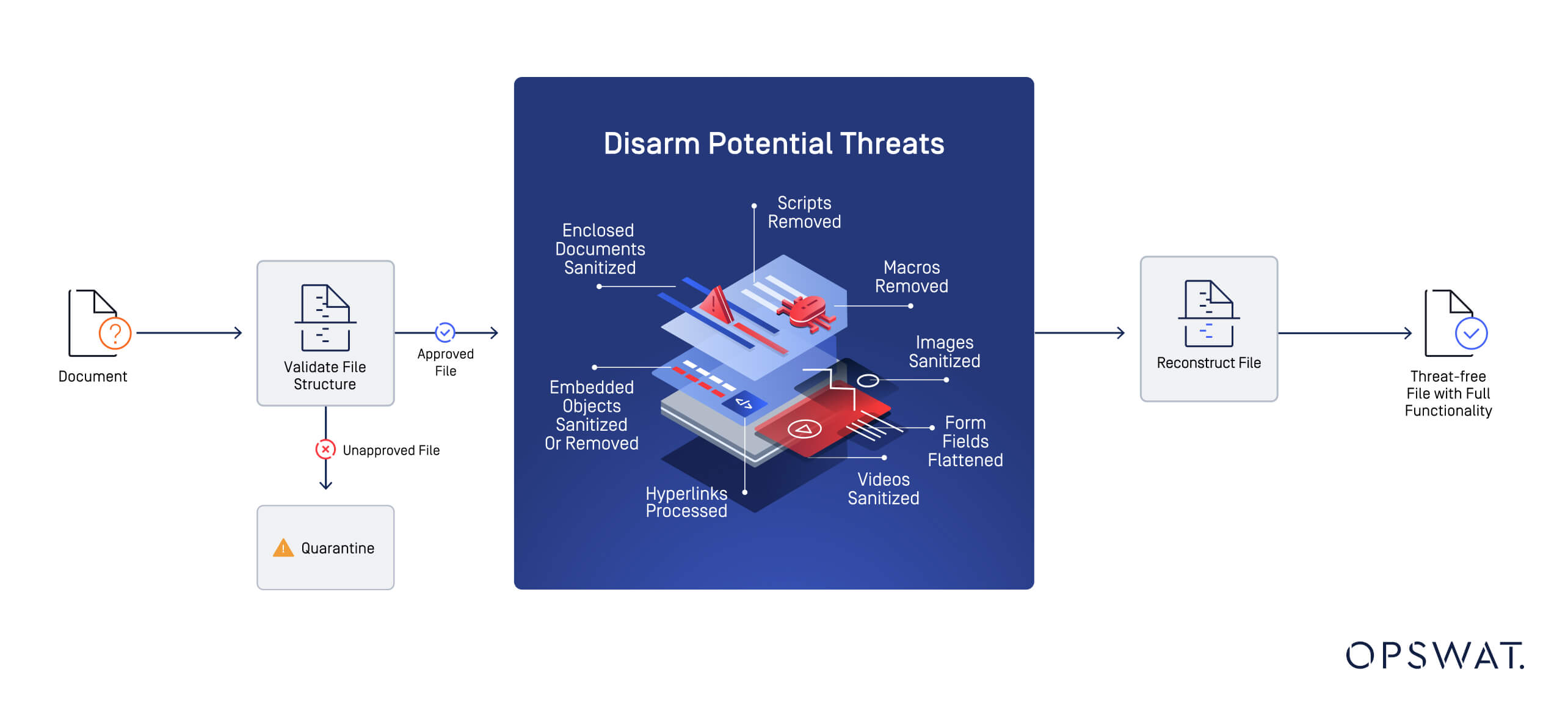
CDR is a necessary technology for protecting against hidden threats (scripts, links, and malicious code) in files.
CDR works by breaking down files into their basic components and removing any harmful content, such as hidden links, URLs, or QR codes.
After disarming the file, CDR reconstructs it, ensuring the file remains functional without carrying over any of the malicious elements.
For example, in the context of job applications, candidates may submit PDF resumes which can be rigged with harmful code designed to exploit your systems. CDR removes the threat and provides a clean, safe file that retains its original purpose.
This makes files safe for use and preserves data integrity while preventing harmful code from executing.
Enable Adaptive Sandboxing for Threat Analysis
Adaptive sandboxing adds an important layer to file security by safely testing potentially harmful files in a controlled environment.
This technology runs files in a simulated system, allowing SOC teams to observe behavior without risking damage to the actual system. Once the file is analyzed, the system provides a verdict based on its behavior in the sandbox.
For files containing scripts or suspicious content, adaptive sandboxing can isolate them in an air-gapped environment, ensuring that any malicious activity is contained.
An adaptive sandbox gives full control over how files are detonated and analyzed, allowing organizations to adjust the environment and monitoring tools based on the file's characteristics.
This flexibility enables a more thorough and precise assessment of threats that might bypass traditional detection methods.
While sandboxing provides an effective security measure, it can take a few minutes to analyze each file.
Given this time frame, it’s important to use sandboxing cautiously to avoid disrupting workflows, especially in environments where file throughput is high.
Take Preventive Measures with DLP
Proactive DLP goes beyond identifying sensitive content; focusing on preventing data leaks before they occur.
DLP detects sensitive information like (PII) Personally Identifiable Information, credit card numbers, NSFW content, and any other type of confidential business data, ensuring it's protected from unauthorized access or exposure.
It does so by redacting sensitive data automatically, removing or replacing it before it’s shared externally.
If necessary, it can apply watermarks to files to track how data is used or who is accessing it.
The latest DLP application includes the use of AI-driven tools allowing organizations to adopt and train AI models while maintaining strong privacy controls.
Track Software Components with a (SBOM) Software Bill of Materials

Organizations must have complete visibility into the components within their applications to manage software supply chain risks effectively—and an SBOM delivers this.
An SBOM provides a comprehensive list of all software components, including third-party libraries, open-source tools, and dependencies, ensuring no part of the application is overlooked.
This inventory becomes critical when developers submit new applications, Docker containers, or code, as it reveals every component involved.
An SBOM use case isn’t limited to vulnerability detection, as it also delivers essential data on component lifecycles, such as end-of-life details and licensing information.
With this visibility, organizations can stay ahead of risks throughout the development process and prevent issues before they arise.
Analyze Archives for Hidden Threats
Compressed or archived files can bypass traditional security measures.
For example, if a file is password-protected, antivirus software cannot scan its contents, which leaves it open to potential risks.
To prevent this, security solutions must be able to open and scan all files inside archived containers, including common formats like ZIP, RAR, and TAR, as well as encrypted archives.
Implementing the Zero-Trust Security Philosophy
No organization is immune to cyberthreats, whether they threat come from internal or external sources, so every file should be treated as a potential risk.
Hackers target organizations of all sizes, and the larger you are, the more attractive you become for lucrative ransomware attacks.
The Zero Trust model is essential in this environment.
It assumes every file, regardless of its origin or trust level, is compromised.
This philosophy ensures that threats cannot bypass your security measures, protecting every aspect of your infrastructure, both internal and external.
Implementing Zero Trust means applying this mindset across all workflows, locations, and systems—APIs, cloud storage, web gateways, etc.
Everything must be segmented with clear ownership at each level.
This model ensures uniformity in security measures, no matter where your organization operates.
Take global organizations, for example.
In some regions, DLP may be mandatory, but under Zero Trust, why limit it to one location?
The same security practices should apply globally, maintaining consistent protection everywhere.
A cloud-based security platform is ideal for this.
It allows easy scaling, ensuring that security measures can be uniformly applied across all locations and workflows.
With such a platform, organizations can effectively keep all systems secure regardless of where they operate.
See How MetaDefender Cloud™ Protects Your Cloud Workloads
You’ve taken the first step in understanding the best practices needed to secure cloud files across all workflows and are now aware that traditional approaches may no longer be enough to keep your organization protected.
MetaDefender Cloud is designed to address cybersecurity challenges directly, offering a clear solution that integrates seamlessly into your cloud infrastructure.
With multi-scanning, dynamic sandboxing, and proactive DLP, you can ensure the highest level of security across all your workflows—without compromising on speed or efficiency.

