PDF files are widely used for sharing documents across multiple collaboration platforms, providing a reliable format for everything from business reports to end-user productivity. However, their ubiquity also makes them a favorable target for cybercriminals. Malicious PDFs can exploit unsuspecting users by embedding harmful content or leveraging PDF features in dangerous ways.
The Growing Threat of PDF-Borne Malware
PDF files are among the most commonly exploited file types for cyberattacks, with malicious actors utilizing them to distribute dangerous malware such as WikiLoader, Ursnif, and DarkGate. Recent statistics and reports indicate a significant rise in PDF-borne malware attacks, making it critical to understand the security risks associated with PDF files.
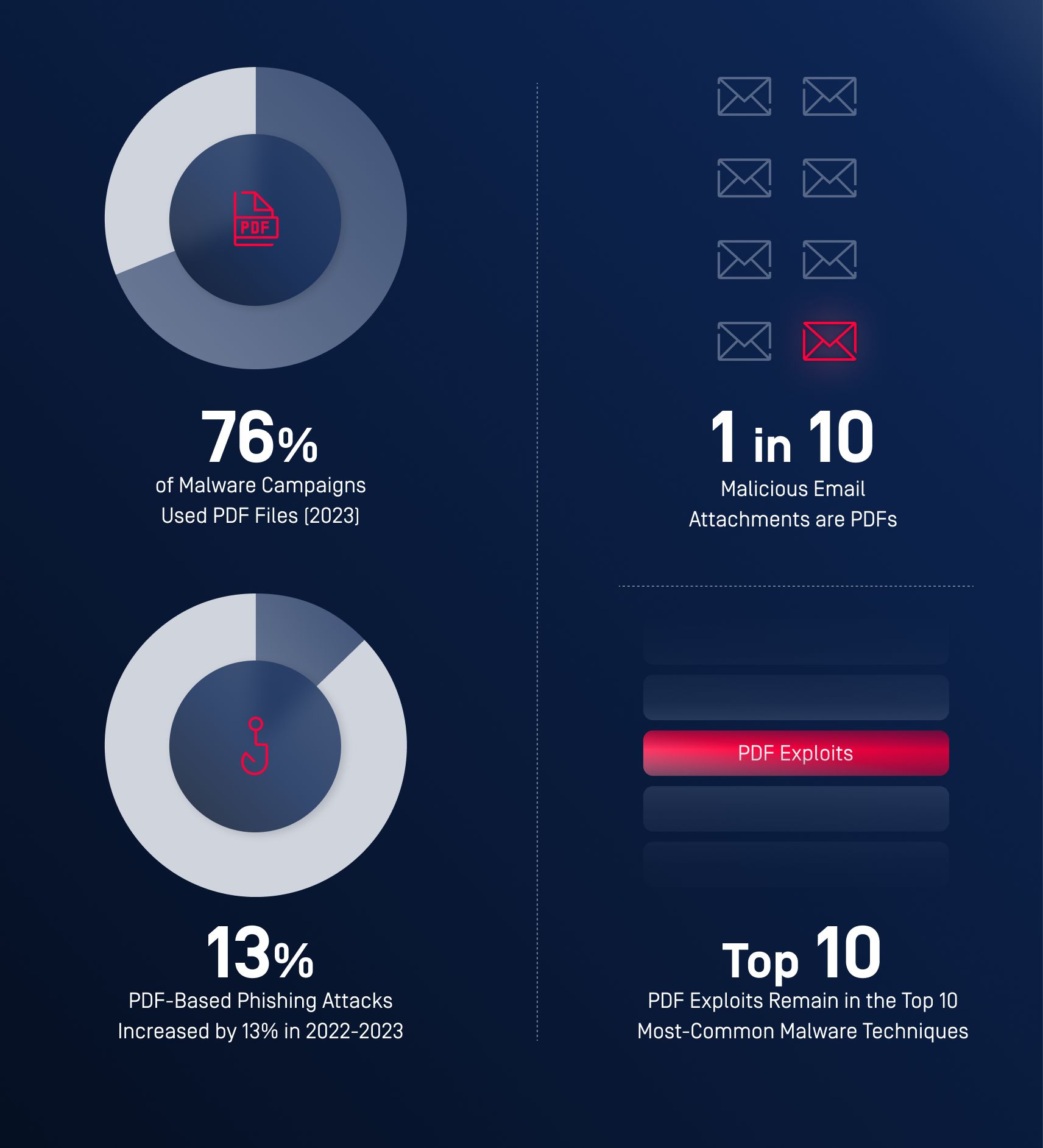
According to a report by Palo Alto Networks, 76% of email-based malware campaigns leveraged PDF attachments as the initial infection vector. Attackers favored PDFs due to their widespread use and the ability to embed malicious code that bypasses traditional antivirus software.
Phishing attacks using malicious PDFs grew by 13% between 2022 and 2023, according to security firm Proofpoint. These attacks often involved embedding harmful links or forms inside the PDF to steal login credentials or sensitive financial information.
Five Signs of a Malicious PDF
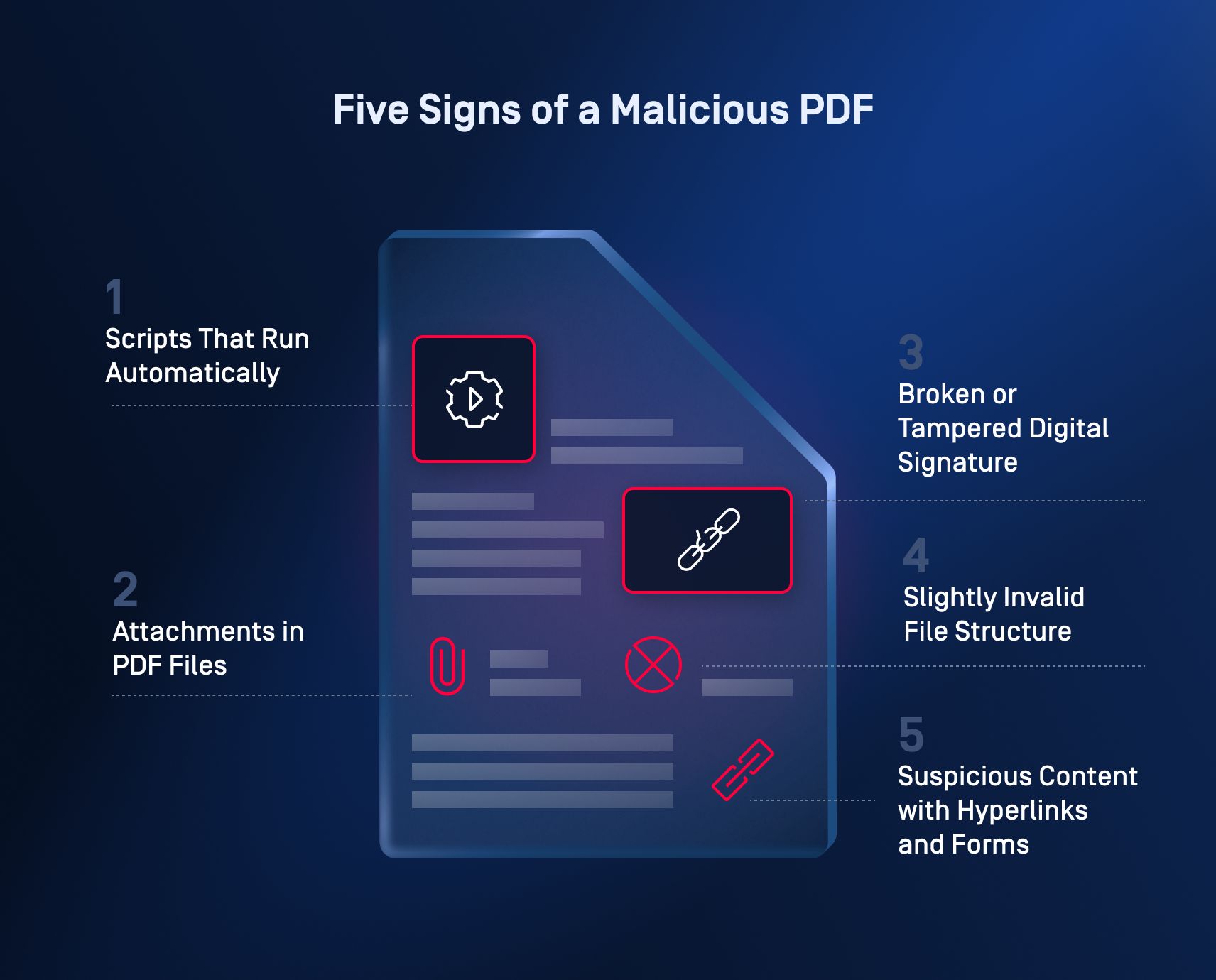
1. Scripts that run automatically
JavaScript embedded in PDFs allows attackers to inject malicious code that executes when the document is opened.
Warning signs:
- Unexpected pop-ups
- System interactions, and
- Unauthorized script execution
2. Attachments in PDF Files
PDF attachments could be disguised as legitimate content, but upon opening, they could infect user’s device.
Warning signs:
- Unexpected attachments
- Executable files (.exe, .bat, or .scr)
- PDFs that prompt downloads without context
3. Broken or Tampered Digital Signature
The digital signature is no longer valid or has been compromised, indicating that the signed content has been altered or tampered with.
Warning signs:
- Broken digital signature
- Tampering alerts from PDF reader
- Mismatched or unclear signatory information
4. Slightly Invalid File Structure
Manipulate the XREF table to reference malicious objects, conceal harmful components, cause buffer overflows, allowing malicious code execution.
Warning signs:
- Corrupt or invalid file structures detected by PDF tools
- Unusual behavior when interacting with the PDF, such as: slow loading times, unexplained crashes
- Multiple trailers or fake entries designed to confuse parsers
5. Suspicious Content with Hyperlinks and Forms
PDFs contain phishing hyperlinks that lead to malicious websites, hide dangerous links behind legitimate-looking text or buttons, gather sensitive personal information through embedded forms.
Warning signs:
- Hyperlinks pointing to suspicious or unfamiliar URLs
- Forms requesting sensitive information without a legitimate purpose
- Unexpected redirects to external websites after clicking on links or buttons within the PDF
Prevent PDF-Borne Malware with Deep CDR™
One of the most effective ways to prevent PDF-borne malware is by using Deep CDR technology. Unlike detection-based antivirus software, Deep CDR takes a proactive approach by stripping potentially harmful elements from files, ensuring only safe-to-use content is delivered.
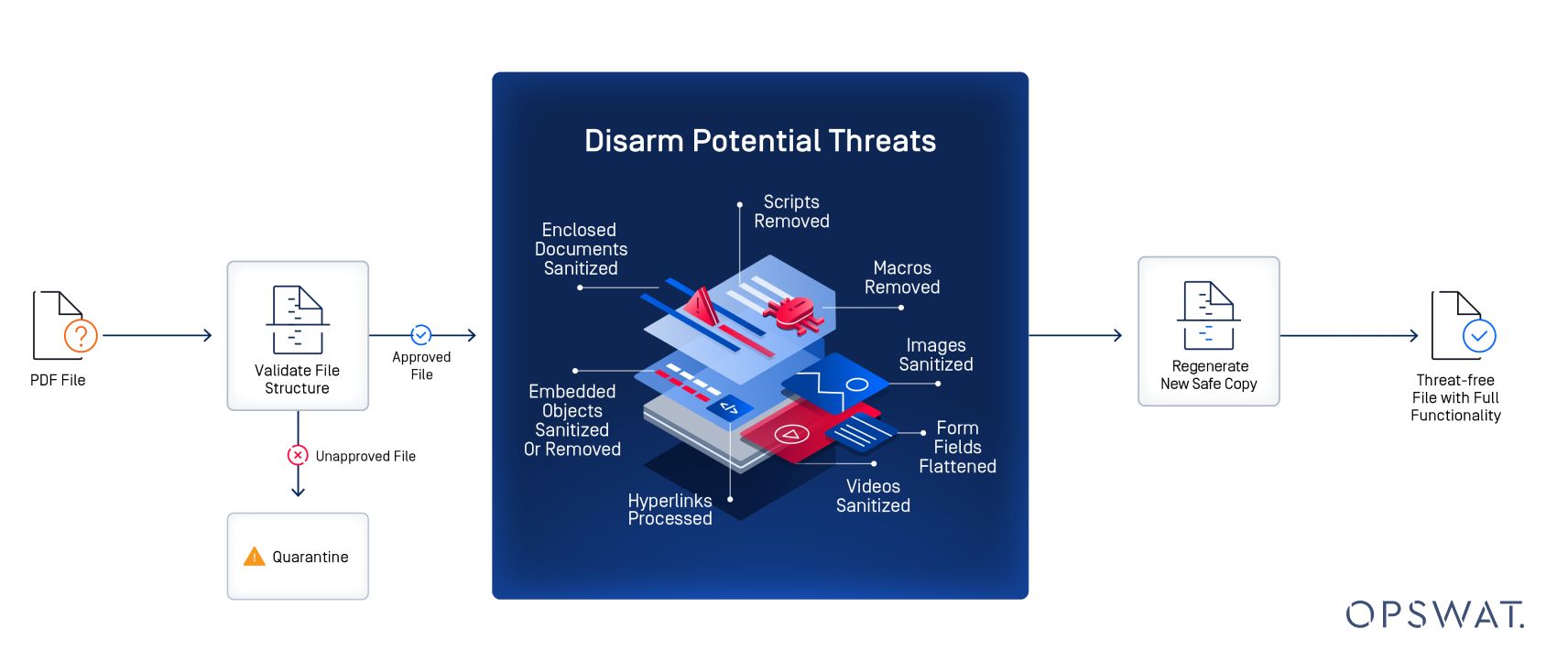
1. File Type and Consistency Check
Deep CDR begins by verifying that the file type and extension match the actual content. This prevents malicious files from being disguised as PDFs.
2. Creation of a Safe Placeholder File
A placeholder file is generated to hold the safe elements. This file keeps the same layout, metadata, and structure as the original, minus any risky components.
3. Removal of Harmful Content
Potentially dangerous elements, such as JavaScript, macros, or embedded executables, are removed. Only safe content—like text and images—is transferred to the placeholder file, preserving the document’s structure, including tables and frames.
4. Integrity Check
The newly reconstructed file undergoes integrity tests to confirm that it works properly and is free from harmful code, ensuring users can safely interact with it.
5. Quarantine of the Original File
The original file, which may still contain harmful elements, is quarantined for further analysis or secure disposal, preventing any potential risks.
Prevent Zero-Day Attacks
Deep CDR doesn’t rely on detecting known malware signatures, which makes it effective against zero-day threats—new or unknown malware types that haven’t been identified by traditional security tools yet.
Protect Against Embedded Hyperlinks and Forms
Deep CDR also scans and sanitizes hyperlinks or embedded forms within PDFs, ensuring that any potentially malicious links are disabled or replaced. This helps in preventing phishing attempts and unauthorized redirection to harmful websites.
Proactive Protection
Unlike reactive, detection-based methods, Deep CDR stops threats before they can even reach the user’s system.
Maintain Document Usability
Essential content like text, images, and static forms are preserved, allowing users to interact with the document without risk.
Protect Your Organization from PDF-Borne Threats
The rise in PDF-borne malware, as indicated by recent statistics, makes it critical to recognize the signs of malicious activity within PDF documents. From JavaScript exploits to tampered signatures and suspicious hyperlinks, understanding these red flags can help you avoid falling victim to cyberattacks. Always use up-to-date PDF readers, stay vigilant about the content you interact with, and avoid opening files from untrusted sources.
Are you ready to improve your organization’s security posture with Deep CDR technology?

