At 6:58 a.m., a patient uploads a referral form to your hospital portal. It looks like another harmless PDF among thousands. By 7:15 a.m., that file has already replicated across three backup tiers. What no one realizes is that it carries a zero-day exploit no endpoint antivirus product has seen before. By noon, ransomware has encrypted your imaging systems, radiology is down, and care teams are scrambling.
This isn’t a dramatic hypothetical. It’s the ongoing reality of modern healthcare cybersecurity. And it illustrates a hard truth: endpoint protection alone is no longer enough to keep patient data or hospital operations safe.
Healthcare now faces the highest breach costs of any industry, averaging $7.42 million per incident, and nearly one third involve ransomware. Files move too quickly, too widely, and through too many systems for endpoints to be the sole line of defense.
Why Endpoint Protection Fails to Stop File-Borne Threats in Healthcare
Traditional endpoint tools were built for desktop environments, not sprawling hospital ecosystems where files pass through imaging systems, cloud storage, vendor networks, and AI pipelines without ever touching a protected endpoint. This creates massive blind spots that attackers exploit.
How File-Borne Malware Evades Endpoint Defenses
Modern malware is engineered to slip past signature-based and even behavioral endpoint tools. Zero-day exploits hide inside PDFs and DICOM files. Polymorphic malware mutates constantly. Backups and cloud repositories replicate malicious files before endpoint agents can intervene.
In many hospitals, the first sign of infection could be a locked-up radiology workstation or a corrupted imaging archive, rather than a blocked file.
Myths That Leave Hospitals Exposed
Despite this, several dangerous misconceptions persist across the industry. Hospitals often believe:
- “Endpoint protection is enough.”
- “Cloud vendors take responsibility for security.”
- “Store-then-scan catches everything.”
- “Encryption solves the problem.”
But threats frequently enter through storage or imaging networks, bypassing endpoints entirely, and cloud providers only secure infrastructure, not the content hospitals upload.
The “store-then-scan” approach is particularly harmful. If malware is detected only after a file has replicated to backups or downstream systems, containment becomes exponentially harder. Recovery efforts stretch into days or weeks, not hours.
How Ransomware and File-Borne Threats Spread Across Hospital Systems
Hospital operations depend on constant file movement: patient uploads, referrals, scans, lab results, insurance claims, vendor files, and now AI training data. Each movement represents a potential attack path.
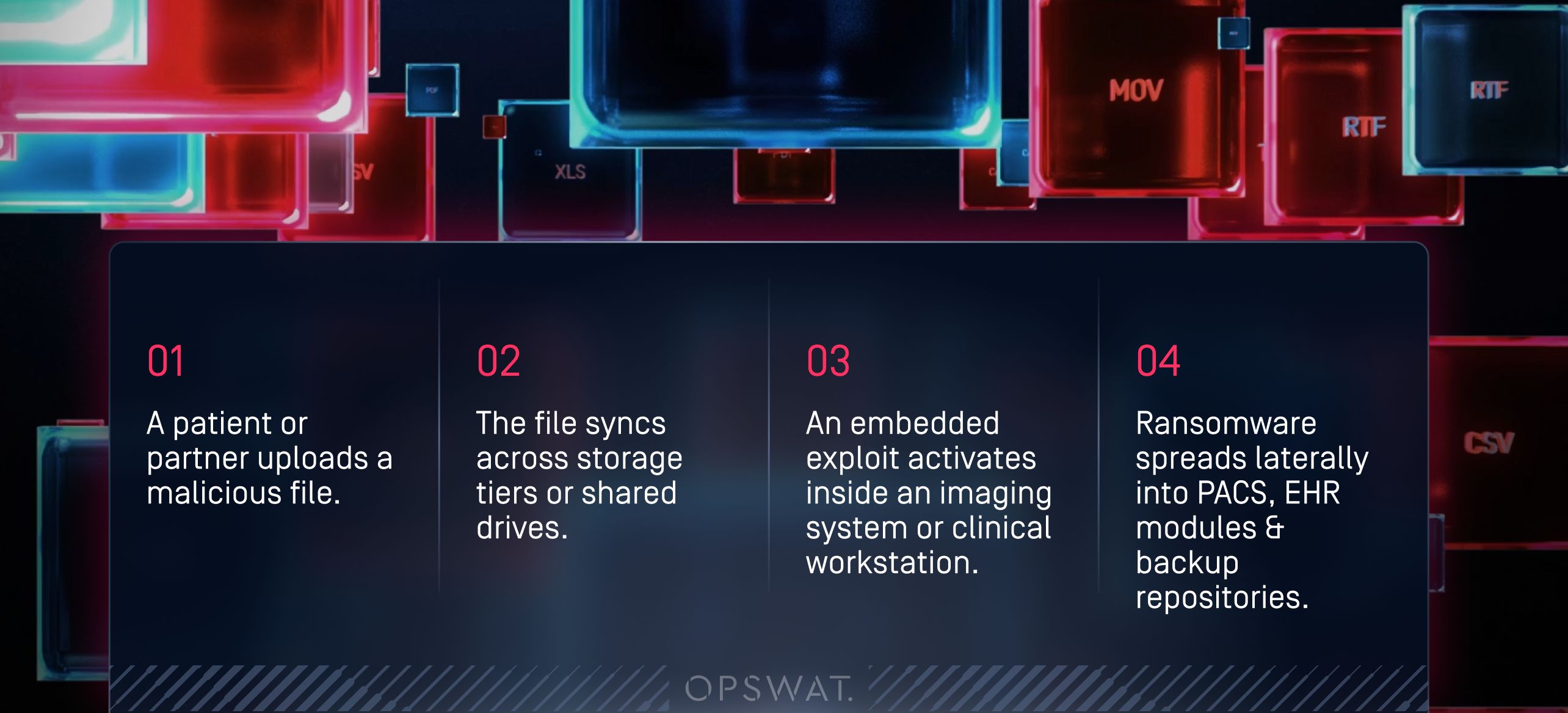
A Typical Attack Timeline
A single malicious file can travel from an external entry point to critical systems in minutes. The sequence often looks like this:
- A patient or partner uploads a malicious file.
- The file syncs across storage tiers or shared drives.
- An embedded exploit activates inside an imaging system or clinical workstation.
- Ransomware spreads laterally into PACS, EHR modules, and backup repositories.
Once backups are infected, incident recovery becomes a race against time.
Imaging, PACS, and Connected Devices: High-Value Targets
Healthcare imaging systems present some of the most unique and dangerous vulnerabilities. DICOM files can contain hidden scripts or malware. Legacy devices and outdated operating systems create soft entry points. Interconnected imaging workflows provide fertile ground for lateral movement.
If an attacker compromises a single imaging file, the ripple effect can shut down radiology for days.
AI Pipelines: The New Frontier for File-Borne Attacks
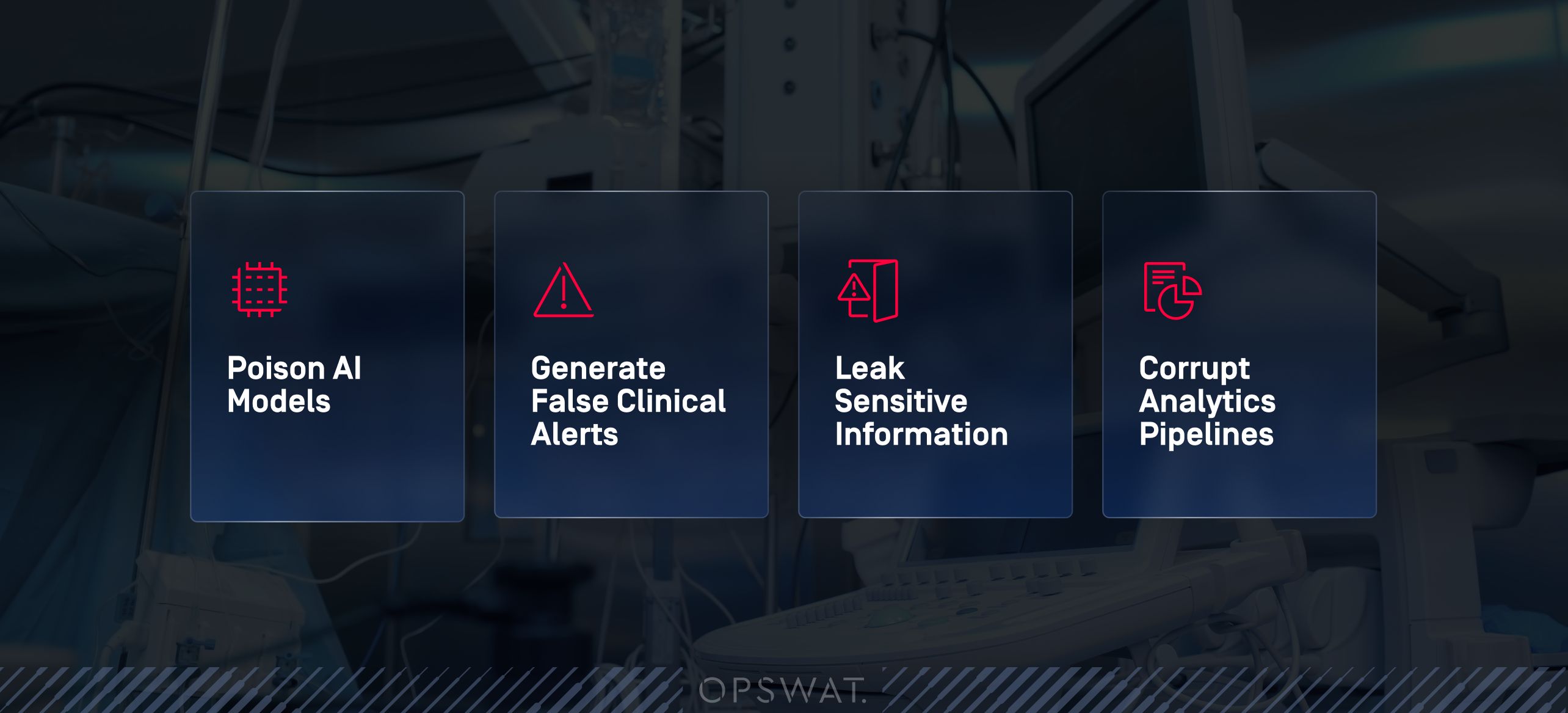
AI and machine learning models ingest massive volumes of documents, forms, and images. These workflows are powerful, but they also expand the attack surface dramatically. Malicious or manipulated files can:
- Poison AI models
- Generate false clinical alerts
- Leak sensitive information
- Corrupt analytics pipelines
Hospitals using OPSWAT solutions now sanitize and audit every file before it enters an AI workflow, ensuring clinical AI remains an asset, not a liability.
File Security: A Compliance Imperative, Not a Checkbox
Healthcare file security is often misunderstood as mere encryption or access control. But regulations like HIPAA, GDPR, and NIS2 require organizations to go much further, ensuring the integrity, not just the confidentiality, of patient data.
Understanding ePHI in the Context of File Security
Electronic protected health information lives everywhere: in imaging files, referral documents, task lists, AI datasets, lab reports, and even metadata. Any file containing identifiers or clinical context must be protected, monitored, and auditable.
Compliance Requirements Are Tightening
Regulators now expect hospitals to demonstrate:
- End-to-end visibility of file movement
- Rapid incident detection and reporting
- Integrity controls that prevent data tampering
- Auditable logs of scanning and sanitization events
Fragmented or reactive file security makes these requirements nearly impossible to meet.
File Security and Patient Safety: Directly Connected
When file-borne threats disrupt imaging, lab systems, or medication workflows, patient safety is immediately impacted. More than simply an IT problem, ransomware risks the operational integrity of the entire healthcare facility.
Advanced Strategies for Multi-Layered File Security in Healthcare
Forward-thinking healthcare organizations are moving beyond endpoints toward a multi-layered, proactive file security architecture.
Multiscanning: Strength in Numbers
Instead of relying on a single antivirus engine, OPSWAT’s Metascan™ Multiscanning leverages 30+ engines simultaneously, detecting over 99% of known and unknown threats.
This dramatically reduces exposure windows and catches the threats other tools miss.
Content Disarm and Reconstruction: Sanitizing Files from Embedded Threats
Deep CDR™ removes active content, exploit code, and embedded threats, then regenerates a safe, functional version of the file. It’s especially powerful for:
- PDFs and Office docs
- DICOM imaging
- Forms uploaded by patients or partners
- File formats with nested archives
Deep CDR, with a 100% Protection and Accuracy Score from SE Labs, prevents known and unknown threats while preserving full file functionality in milliseconds.
Adaptive Sandboxing and AI-Powered DLP
When files require deeper scrutiny, OPSWAT’s emulation-based Adaptive Sandbox analyzes their behavior in real time. AI-powered Proactive DLP™ detects and blocks or redacts ePHI and other sensitive content, aiding with HIPAA and GDPR obligations.
Inline File Sanitization: Protecting Every Entry Point
Inline inspection means files are scanned and sanitized before entering your environment—not hours later. It enables:
- Immediate threat removal
- Full chain-of-custody logging
- Rapid incident response
- Consistent protection across portals, email, MFT, imaging, and AI workflows
Real-World Case Studies: Proof That Multi-Layered File Security Works
Healthcare organizations worldwide are adopting this approach and seeing measurable results.
Clalit Health Services: Governing Millions of Files a Day
As one of the world’s largest health organizations, Clalit implemented Metascan Multiscanning and Deep CDR to inspect millions of files daily. The result: blocked zero-day threats, stronger compliance posture, and a new benchmark for file security at scale.
Recovering from Ransomware Without Shutting Down
A major healthcare provider used MetaDefender Managed File Transfer™ (MFT), a secure MFT solution that seamlessly integrates with OPSWAT’s file security technologies, to sanitize restored files during a ransomware recovery. They maintained business continuity and proved compliance, avoiding significant legal penalties.
Luzerner Psychiatrie AG: Stopping Email-Borne Malware
Facing frequent phishing attacks, Luzerner Psychiatrie AG deployed Adaptive Sandbox and MetaDefender Email Security™ to prevent malware-laden attachments from reaching clinical staff. Patient data remained protected, and breaches dropped to zero.
Actionable Steps to Move Beyond Endpoint AV
Healthcare security leaders ready to strengthen file security should begin with a structured roadmap.
1. Conduct a File Security Risk Assessment
Map every file workflow (patient portals, PACS, cloud storage, AI pipelines) and identify where files enter without scanning or sanitization.
2. Protect Imaging and Transfer Workflows
Enforce scanning and CDR for DICOM files, secure vendor exchanges, and ensure auditability of every file touchpoint.
3. Secure AI and Data Analytics Pipelines
Sanitize and validate all data before ingestion to prevent contamination and data leakage.
4. Build a Future-Ready Architecture
Combine multiscanning, CDR, sandboxing, AI-powered DLP, and inline sanitization for comprehensive, compliant protection.
Ready to Take the Next Step?
Check out the full whitepaper to see how leading hospitals are using multi-layered file security to neutralize threats before they ever reach a workstation or a patient.

