In the cybersecurity industry, technical accuracy is critical. Inaccurate or misleading claims not only confuse customers, but can also create a false sense of security in environments where precision matters most.
At OPSWAT, we believe in transparency, and in letting our globally-trusted technology and solutions speak for themselves.
- File Type Support: Designed for Threat Relevance, Not Arbitrary Volume
- File Size Handling: Scalable Beyond 2 GB
- Threat Intelligence: Validated by Experts, Trusted by the Pentagon
- Global Support Infrastructure: Meeting You Where You Need Us
- Integration and Technology Access: Flexible, Transparent, and Comprehensive
- Technology-Driven Threat Mitigation: Automated Protection at Scale
- The Bottom Line: Technology-Driven, Mission-Focused Security
File Type Support: Designed for Threat Relevance, Not Arbitrary Volume
Our Deep CDR™ technology is engineered to sanitize 184 high-risk, commonly exploited file formats. This coverage includes Office documents, PDFs, archives, images, CAD files, and multimedia — precisely the types most frequently targeted in malware campaigns against IT and OT environments.
These numbers can be "inflated" by broadly counting a near limitless variation of file types, particularly those that are text-based. We believe in simplicity and transparency, and don’t want to cloud the value you are looking for in your security program.
Beyond Deep CDR, MetaDefender Core processes thousands of file types through our layered multi-scanning architecture. OPSWAT’s priority is not to enumerate every conceivable file extension, but to ensure that supported types align with the real-world threat landscape and critical infrastructure needs.
Key Takeaway
OPSWAT’s file type coverage is mapped to risk relevance and operational necessity, not inflated to meet arbitrary counts.
File Size Handling: Scalable Beyond 2 GB
OPSWAT has no inherent file size limitation. Our platform supports files well beyond 2 GB depending on customer configuration, engine capabilities, and system resources.
For example, MetaDefender Core’s default maximum size can be tuned to meet high-throughput and large-file environments such as industrial design systems, geospatial analytics, and healthcare imaging repositories.
Statements that OPSWAT imposes a 2 GB file size limit are inaccurate. We happily support many users with a program requiring well beyond a TB file size limit. Again, our solutions are built to fit your needs and ensure the best experience for the user.
Key Takeaway
OPSWAT file security can handle large datasets efficiently, configurable to industry-specific requirements.
Threat Intelligence: Validated by Experts, Trusted by the Pentagon
When it comes to threat intelligence, accuracy and operational reliability matter. OPSWAT’s file security solutions are powered by InQuest InSights Threat Intelligence — a platform recognized for its precision, real-world efficacy, and elite-level validation.
- InQuest, acquired by OPSWAT in 2024, is a proven leader in deep file inspection and malware detection technologies.
- MetaDefender InSights Threat Intelligence powers critical detection infrastructure across three-letter agencies, including the Pentagon.
- Intelligence is curated through continuous corpus testing, behavioral detection validation, and partnerships with cybersecurity research communities.
Rather than measuring success by the number of hashes collected, InQuest InSights focuses on high-fidelity indicators, ensuring that every signature, heuristic, and reputation indicator directly strengthens threat detection and risk mitigation.
This rigorous methodology results in faster, more reliable threat identification without the noise and redundancy associated with inflated data sets.
Key Takeaway
OPSWAT delivers threat intelligence proven in the highest-stakes environments, where detection fidelity defines success.
Global Support Infrastructure: Meeting You Where You Need Us
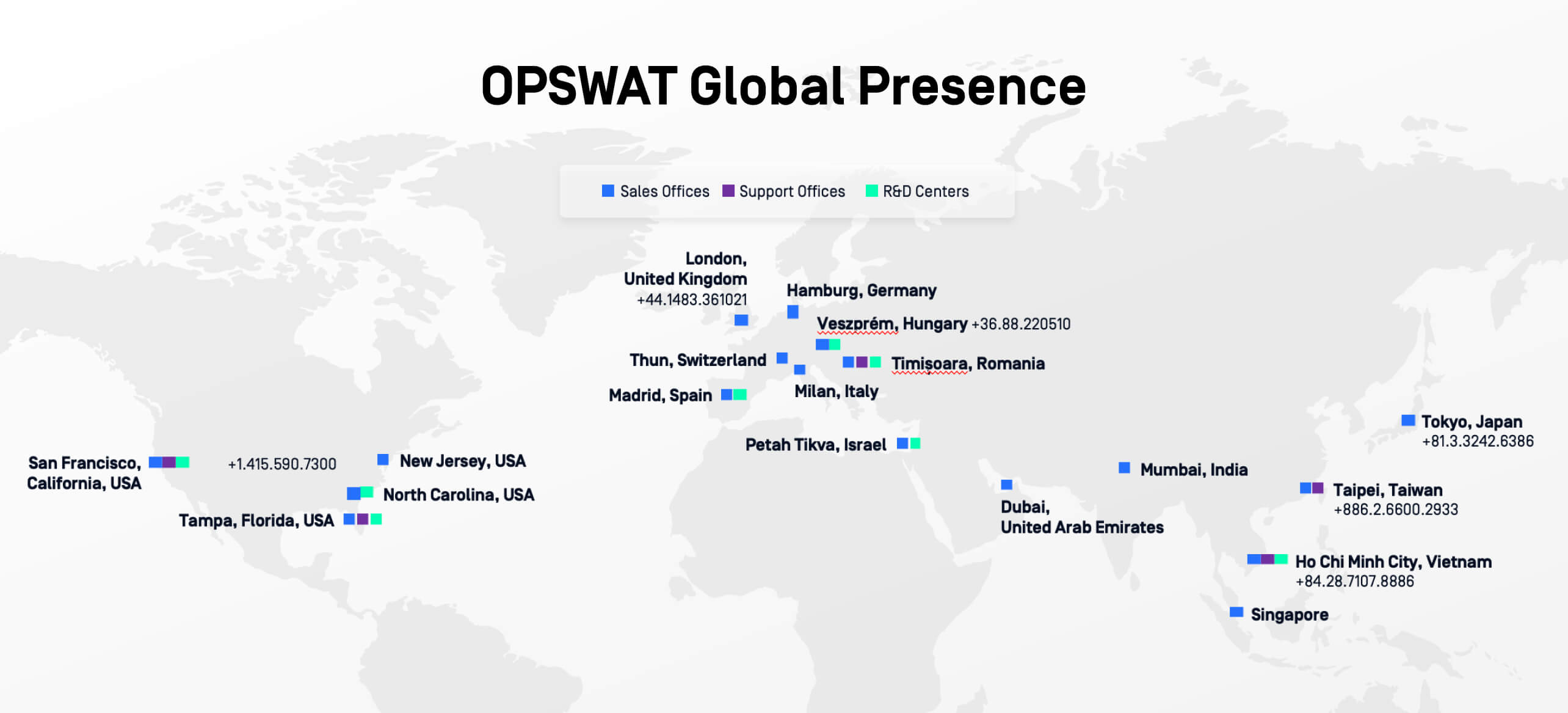
OPSWAT operates a 24x7 global support model with technical teams located in North America, EMEA, and APAC.
Customers receive 24x7 assistance, with region-specific escalation paths to ensure rapid response and in-depth technical engagement, including local language support where required. Additionally, for those who desire it, we do offer a 24x7 US only support model.
Key Takeaway
OPSWAT support is geographically distributed to align with customer operations worldwide.
Integration and Technology Access: Flexible, Transparent, and Comprehensive
Accurate information is critical when evaluating cybersecurity solutions. Here’s how OPSWAT’s technology approach is structured:
- Based on the product and use case, OPSWAT licenses vary to build the right solution for our customers.
- Our offerings are built for on-prem, hybrid, or cloud environments, with flexible models to ensure our services align with customers' needs.
- MetaDefender Core offers 34 anti-malware engines with OEM agreements, allowing for enhanced licensing handling, customer support and greater data privacy.
- Our modular architecture allows customers to select engine configurations and performance profiles based on specific security and operational requirements.
Key Takeaway
OPSWAT’s integration strategy prioritizes scalability, cost-efficiency, and tailored protection across IT and OT environments.
Technology-Driven Threat Mitigation: Automated Protection at Scale
Recent suggestions that OPSWAT’s approach increases “time to mitigation” due to manual file investigation are inaccurate.
In reality, OPSWAT’s unified File Security platform is engineered to eliminate manual triage, accelerating threat detection and remediation at enterprise scale.
Here’s how:
- Comprehensive File Type Support: OPSWAT can scan and process over 4,500 file types, including the ability to parse and inspect files at the binary level when necessary, ensuring that virtually any file encountered can be analyzed without requiring manual categorization or sorting.
- Zero-Day Prevention: Our solutions can detect and prevent unknown threats without relying on detection signatures or manual review. Our Deep CDR technology sanitizes files at the point of entry, regenerating clean, safe-to-use versions and removing embedded threats.
- Immediate Threat Correlation: Metascan™ Multiscanning aggregates intelligence from 30+ anti-malware engines simultaneously, identifying known and unknown threats in near real time.
- Seamless Behavioral Analysis: Suspicious or unknown files are automatically escalated to MetaDefender Sandbox for dynamic, behavior-based inspection, without disrupting trusted data flows.
OPSWAT’s pipeline is designed for automated, high-confidence mitigation, dramatically reducing time to remediation even in the most demanding IT and OT environments.
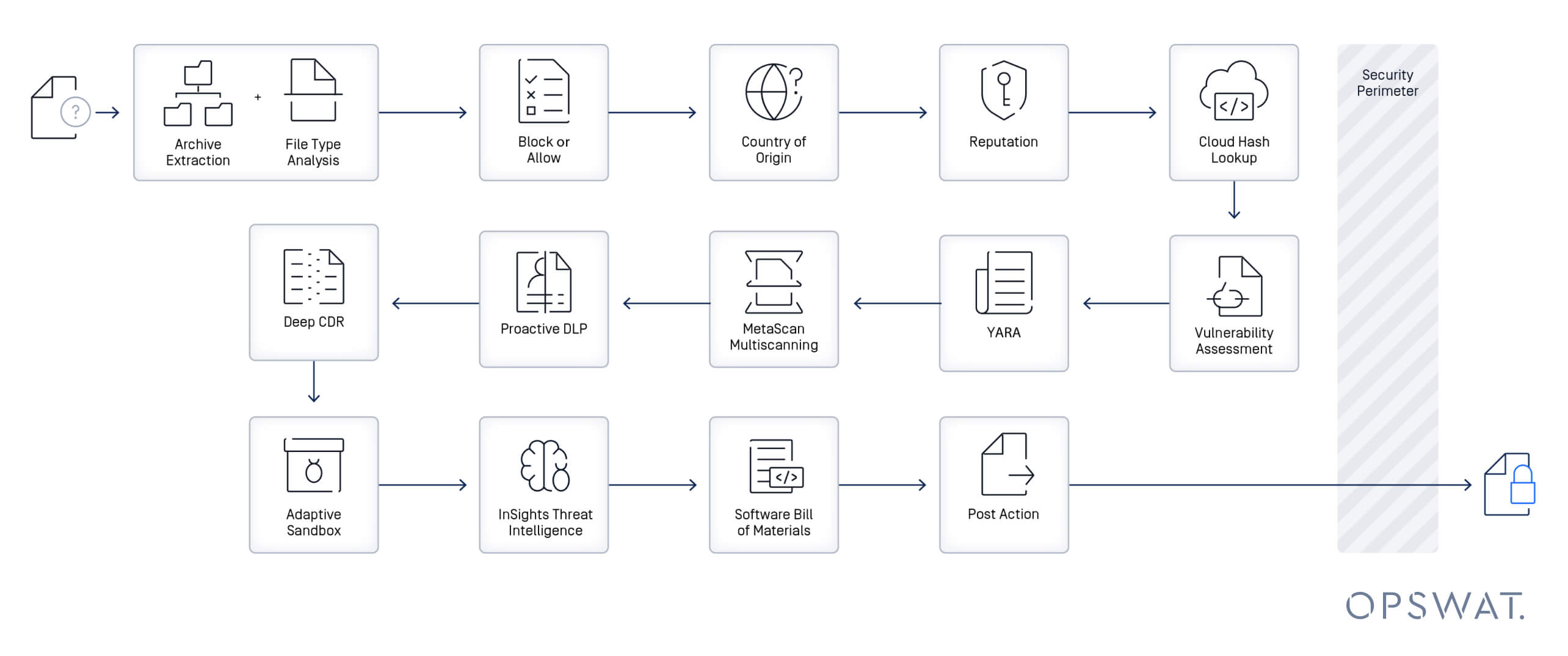
Key Takeaway
OPSWAT’s robust, automated threat mitigation platform minimizes manual investigation and accelerates secure file usage, protecting operations without operational drag.
The Bottom Line: Technology-Driven, Mission-Focused Security
At OPSWAT, our commitment is clear: protect critical infrastructure and enterprise environments through precision-engineered solutions and a unified approach to file security.
We focus on delivering tangible security outcomes validated every day across sectors like energy, manufacturing, transportation, and defense.
If you would like to understand the technical depth behind OPSWAT’s File Security solutions — or validate these capabilities in your own environment — our experts are ready to show you why OPSWAT is trusted globally to defend some of the world’s most critical environments.

