Delta Electronics is a global provider of industrial automation and control technologies deployed across a broad range of Operational Technology (OT) environments. Among its automation offerings, the Delta DVP series programmable logic controllers (PLCs) are commonly used to support industrial control functions and process automation. Because PLCs directly influence industrial processes, their security is a key factor in overall OT resilience - helping reduce the likelihood that weaknesses in a single device become broader operational or safety risks.
Unit 515’s research on the Delta DVP series
OPSWAT Unit 515 is OPSWAT’s elite red team, responsible for safeguarding OPSWAT products and contributing to the broader security community through rigorous technical research and responsible vulnerability disclosure. In addition to research, Unit 515 delivers professional penetration testing engagements to help customers assess real-world risk, validate security controls, and strengthen their overall security posture.
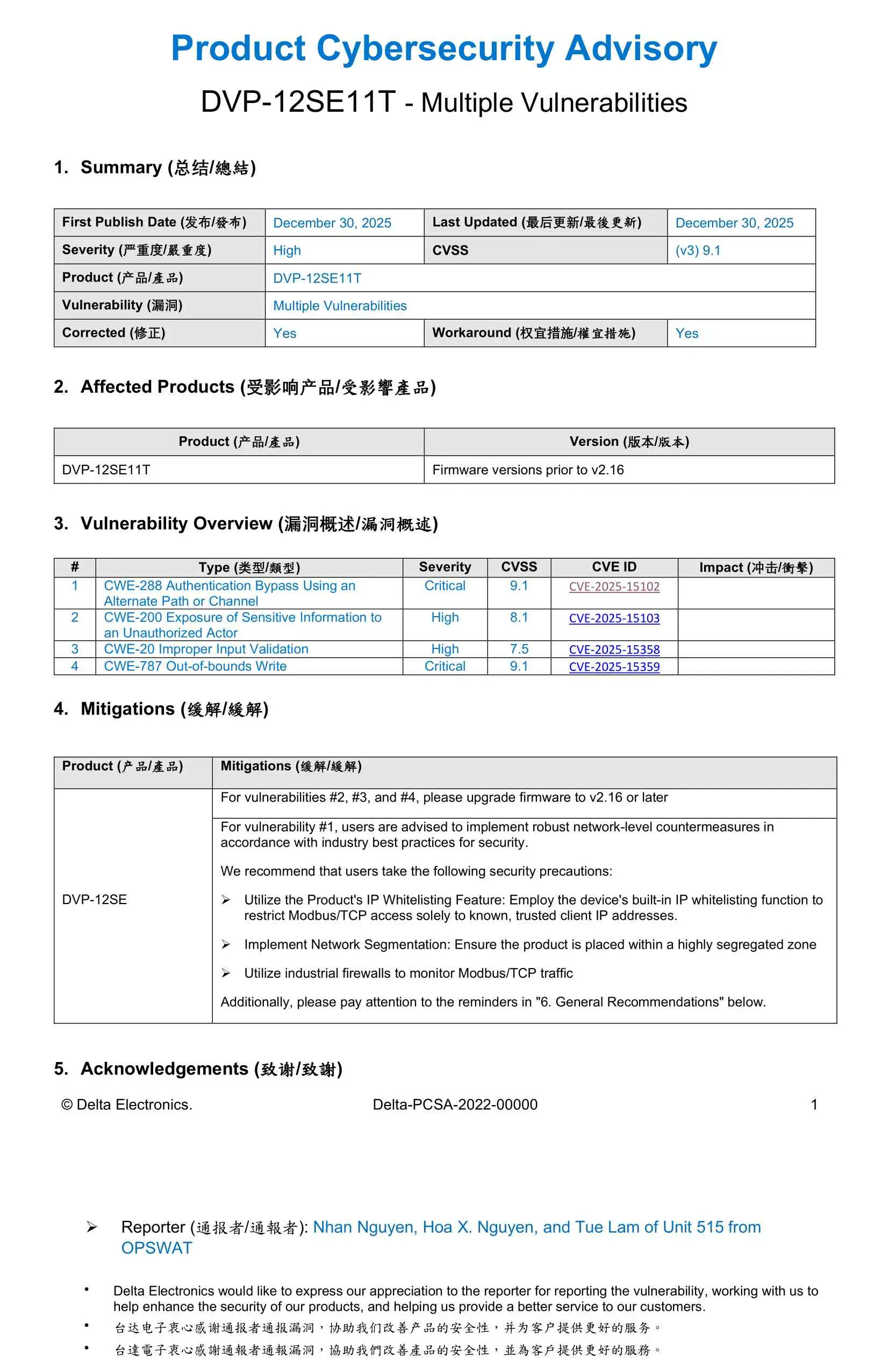
In August 2025, Unit 515 performed a targeted security assessment of the Delta DVP-12SE11T PLC to evaluate weaknesses that could be leveraged in Operational Technology (OT) deployments. The assessment identified multiple critical-impact vulnerabilities affecting security-critical functionality, including conditions related to authentication bypass, information exposure, and denial-of-service (DoS) - issues that, depending on deployment architecture and segmentation, may increase the likelihood of unauthorized access or operational disruption.
In accordance with responsible disclosure best practices, Unit 515 promptly reported the findings to Delta Electronics and worked closely with the Delta security team throughout triage and validation. Delta engaged proactively to confirm the issues, develop mitigations, and move remediation through to release. Delta subsequently published an official security advisory and issued firmware updates in late December 2025 to address the affected systems. The vulnerabilities were assigned the following CVEs:
- CVE-2025-15102
- CVE-2025-15103
- CVE-2025-15358
- CVE-2025-15359
Technical overview of security vulnerabilities on Delta DVP series
In collaboration with Delta Electronics, we recognize the unique safety and operational risks associated with Operational Technology (OT) environment. Protecting critical infrastructure remains our highest priority, and we uphold our responsibility to ensure these findings are not leveraged for malicious activity. Accordingly, we are providing only a high-level summary and are not releasing exploit code or in-depth technical details.
Below is a high-level overview of the vulnerabilities identified by OPSWAT Unit 515:
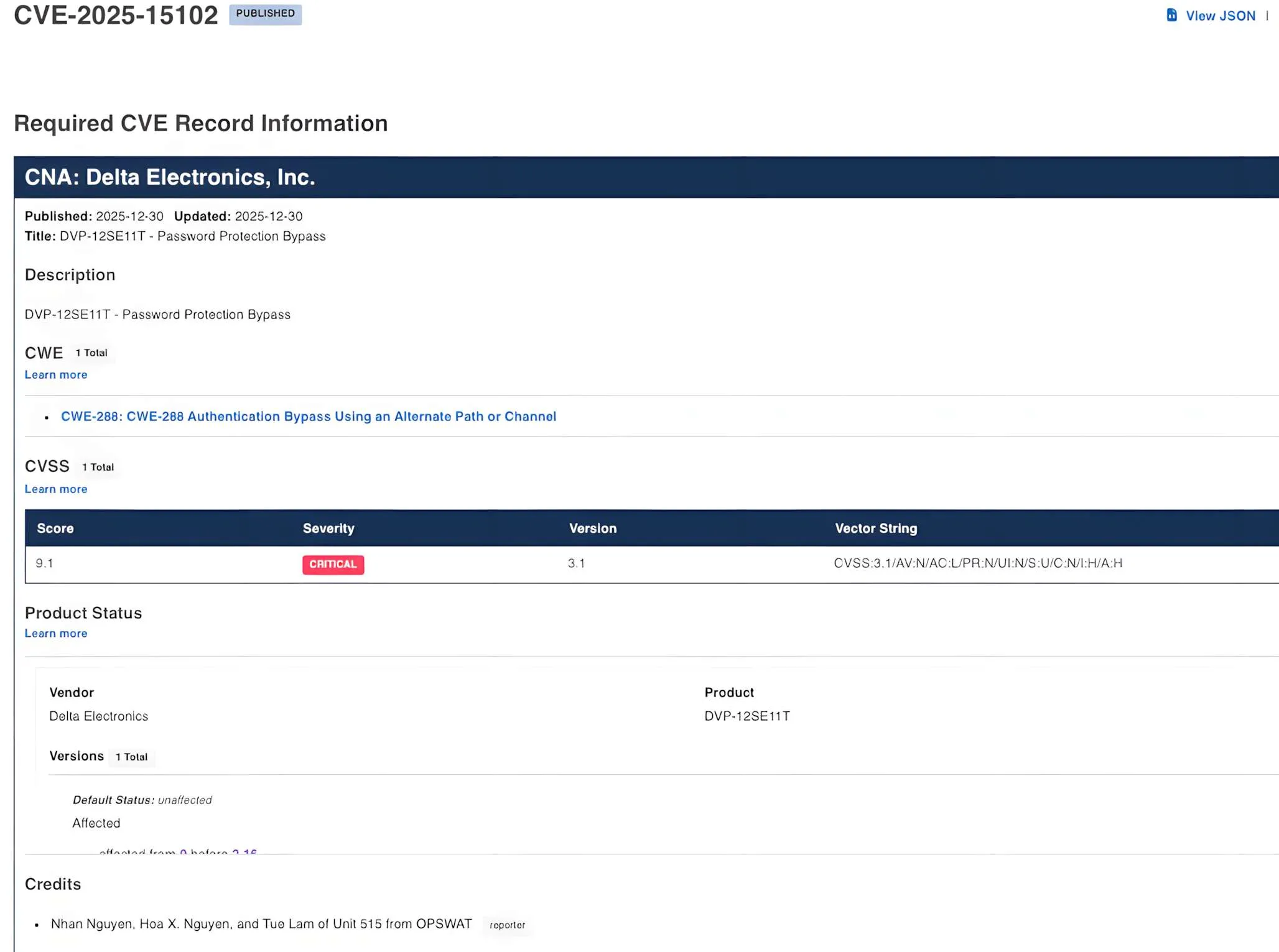
CVE-2025-15102: Password authentication bypass (Critical, CVSS v3.1: 9.1)
This vulnerability is associated with insufficient authentication enforcement in a security-critical code path. Under certain conditions, an unauthenticated attacker may be able to bypass required authentication by sending specially crafted network traffic to the device.
Affected device(s): DVP-12SE11T (firmware prior to 2.16)
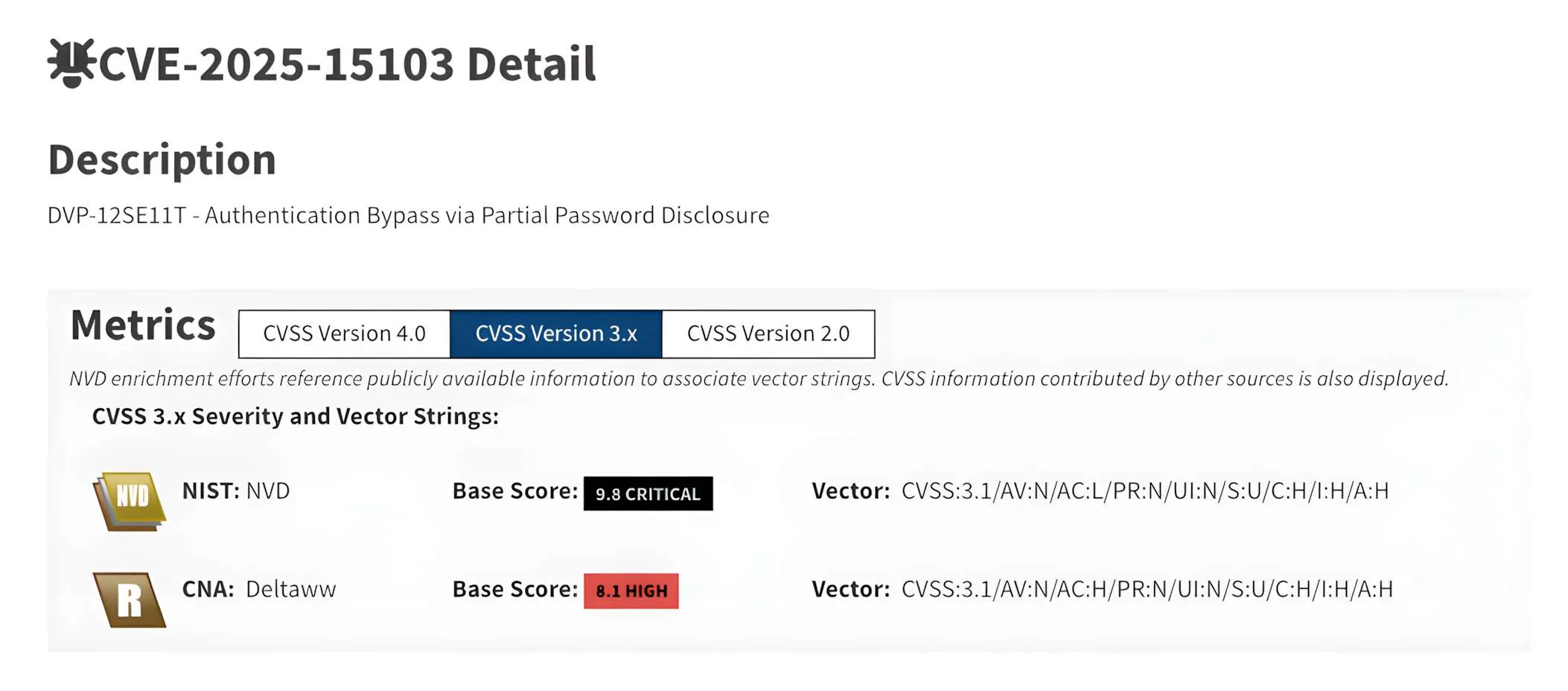
CVE-2025-15103: Authentication bypass via partial password disclosure (Critical, CVSS v3.1: 9.8)
This vulnerability stems from weaknesses in the authentication handling logic that may allow limited disclosure of password-related information. An unauthenticated attacker could use crafted network traffic to obtain partial authentication data, potentially reducing the strength of the authentication mechanism.
Affected device(s): DVP-12SE11T (firmware prior to 2.16)
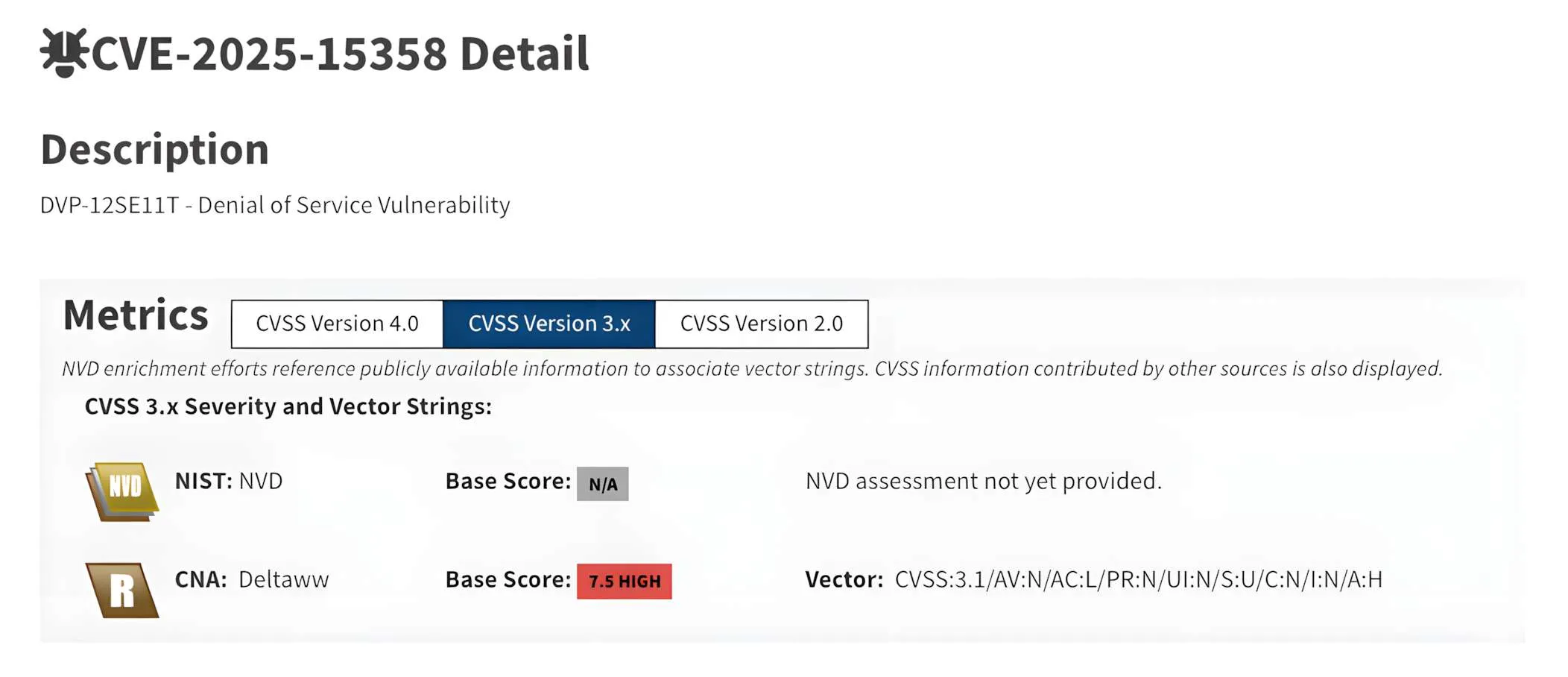
CVE-2025-15358: Denial of service (High, CVSS v3.1: 7.1)
This vulnerability is related to insufficient validation in memory-handling functionality. An unauthenticated attacker may be able to trigger a condition that disrupts normal PLC operation and causes the device to become unresponsive until recovery actions are taken.
Affected device(s): DVP-12SE11T (firmware prior to 2.16)
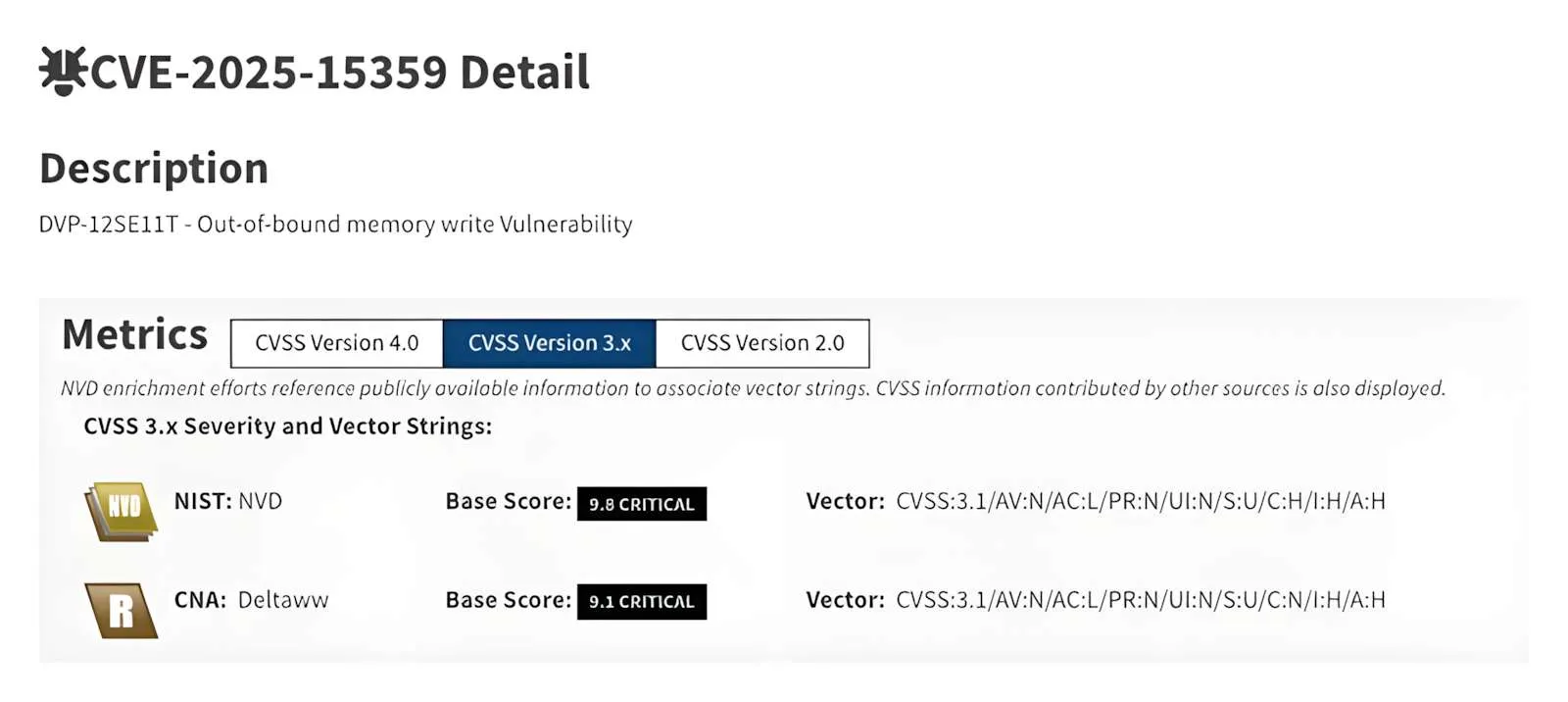
CVE-2025-15359: Out-of-bounds memory write (Critical, CVSS v3.1: 9.1)
This vulnerability is caused by improper bounds checking in a memory manipulation routine and may enable out-of-bounds writes. Successful exploitation could impact integrity and lead to unpredictable device behavior.
Affected device(s): DVP-12SE11T (firmware prior to 2.16)
Remediation
Organizations using Delta DVP-12SE11T PLCs should follow Delta Electronics’ official advisory and apply the recommended firmware updates as soon as operationally feasible: https://filecenter.deltaww.com/news/download/doc/Delta-PCSA-2025-00022_DVP-12SE11T%20Multiple%20Vulnerabilities.pdf
Beyond patching, we recommend a defense-in-depth approach aligned to OT operational constraints:
- Vulnerability detection via continuous CVE scanning and remediation: Regularly scanning networks for vulnerabilities, and apply remediation (best with firmware patching if possible)
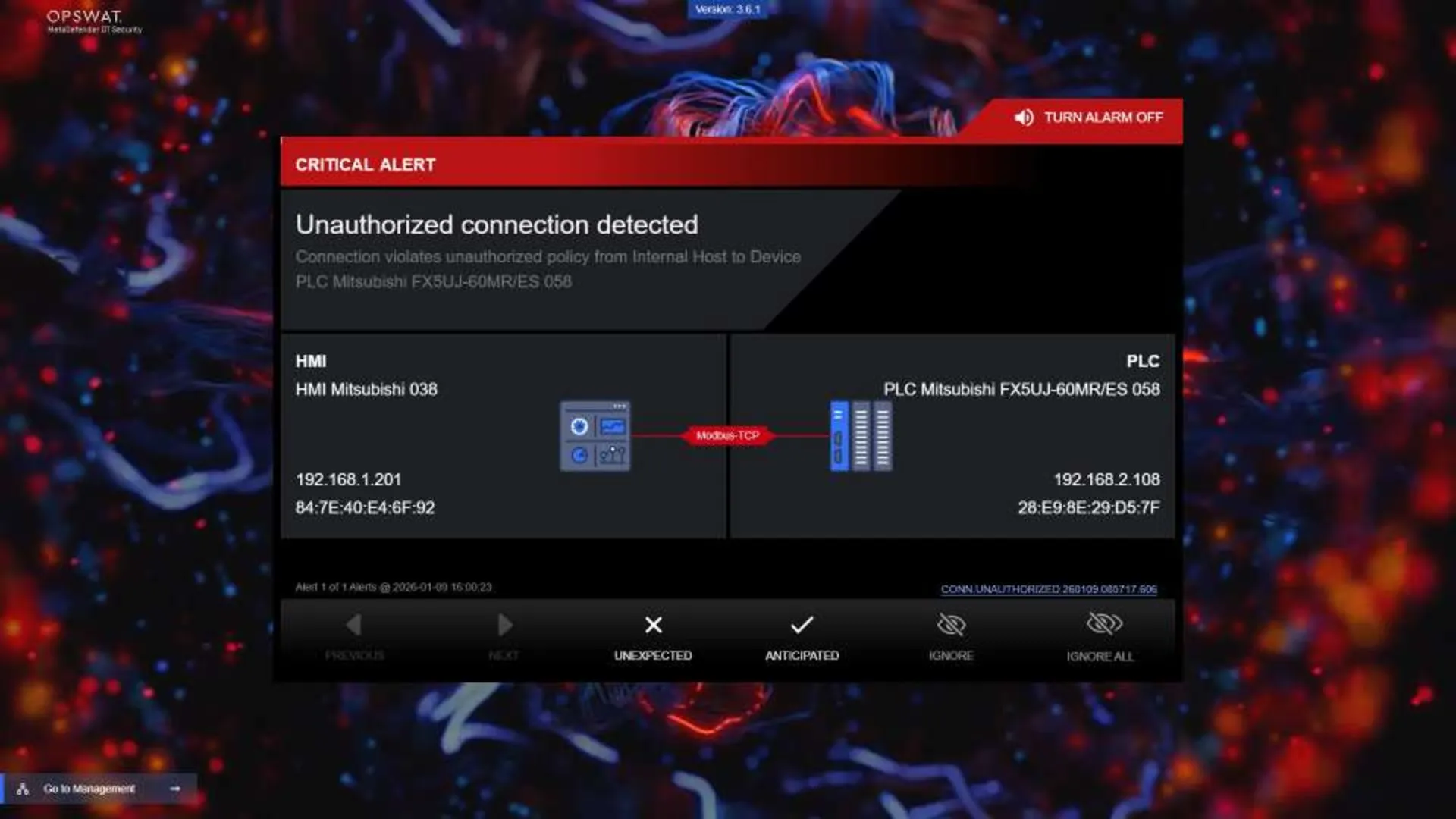
- Monitoring for anomalous behaviors: Flagging unusual increases in frequency in communication to the Delta DVP-12SE11T PLC, which could suggest an ongoing unauthorized data exfiltration attempt.
- Identifying unauthorized device connections: the system should detect when a rogue/ unauthorized device connects to the PLC.
- Network segmentation: Isolating affected devices can help prevent the lateral spread of attacks, thus minimizing impact.
- Intrusion Prevention: immediately identifying and blocking malicious/ unapproved commands to the PLC, then effectively protect normal operations of the PLC
OPSWAT MetaDefender OT Security supports these requirements by helping organizations identify vulnerable assets, continuously monitor OT networks for anomalous behavior, and detect unauthorized connections. Using behavioral baselining and policy controls, it enables faster detection and response while minimizing operational disruption. MetaDefender OT Security also supports remediation workflows, including centralized firmware management capabilities for supported controllers.
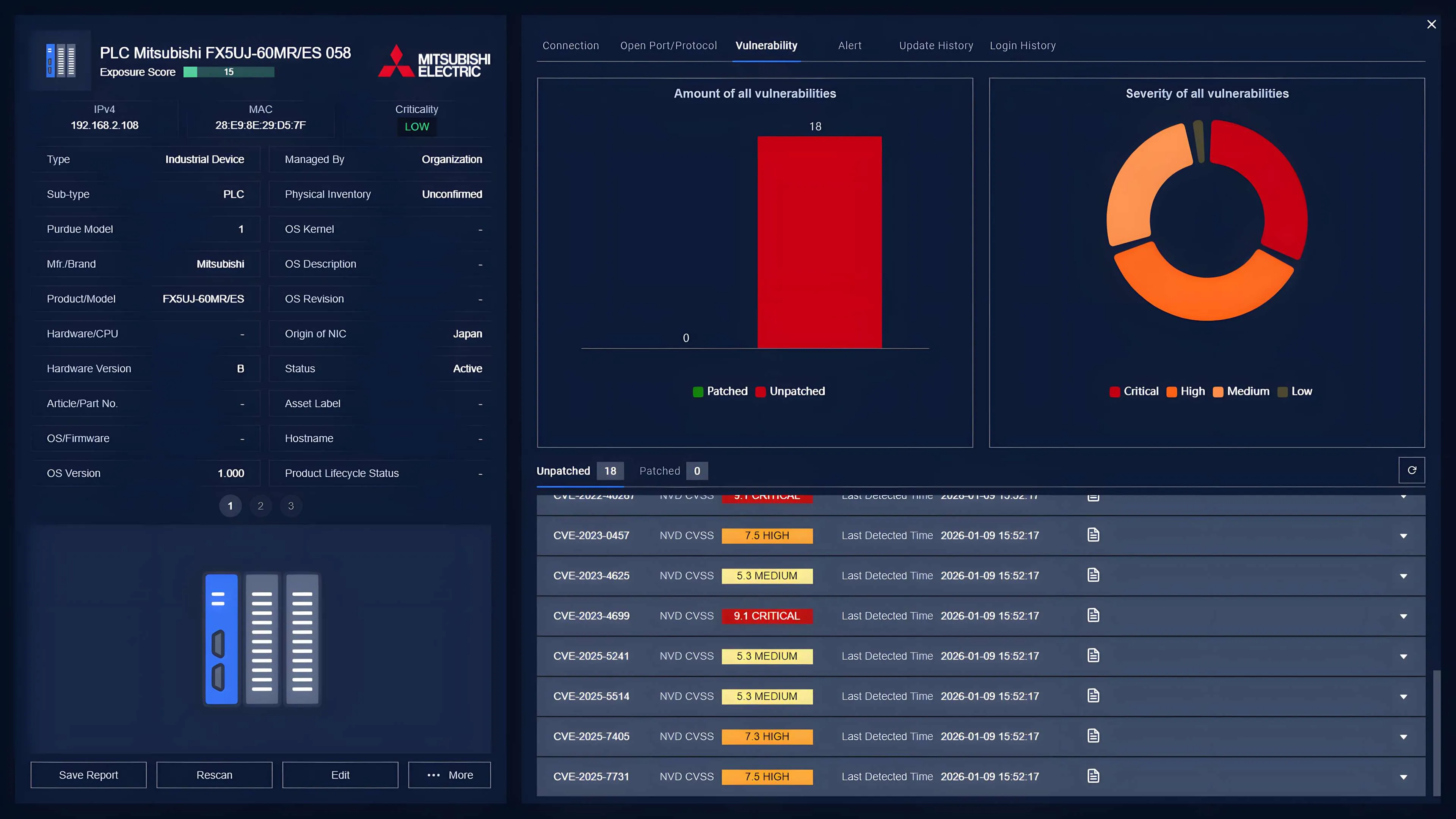
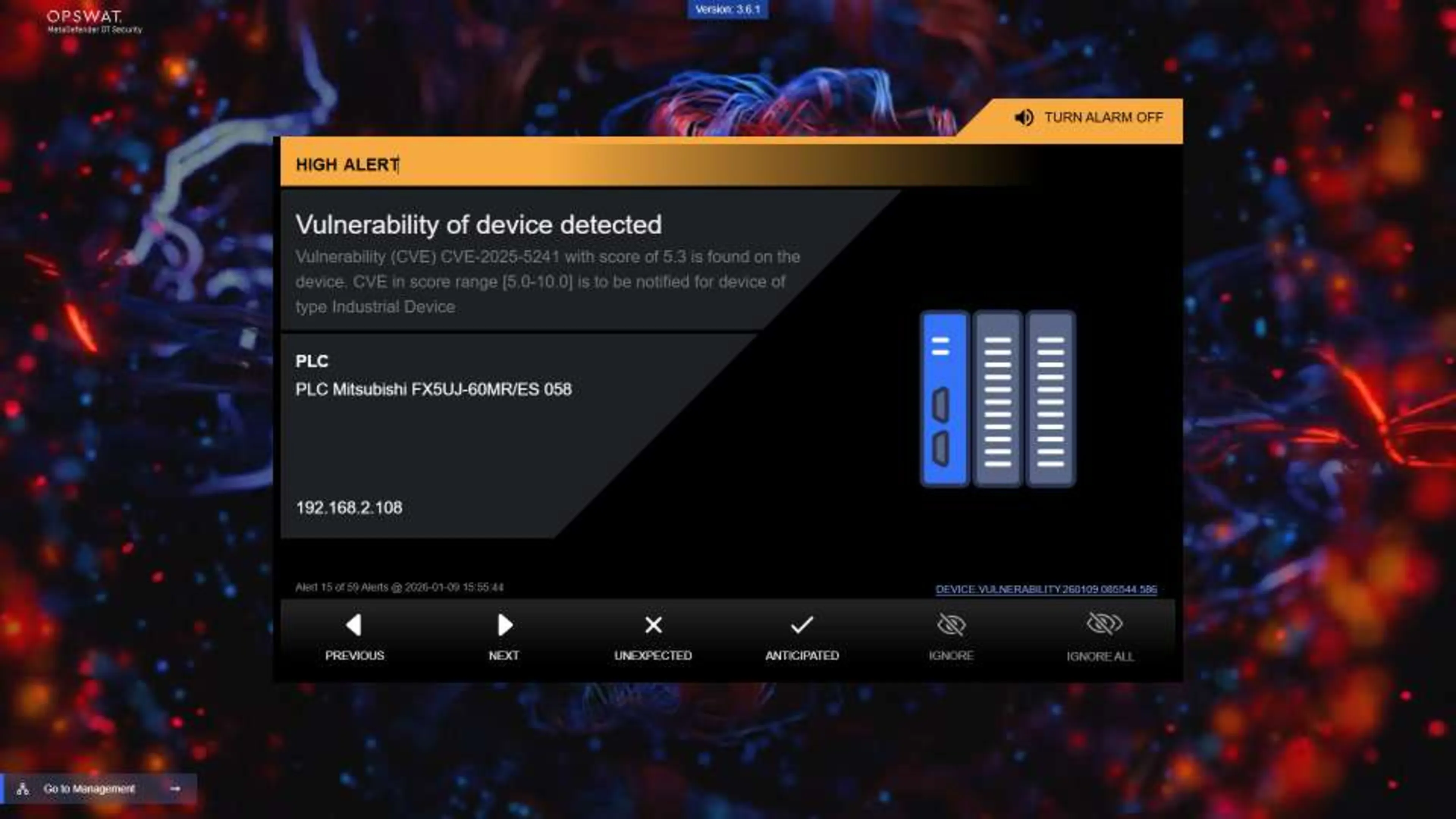
For enforcement and containment, MetaDefender OT Security can integrate with OPSWAT MetaDefender Industrial Firewall to detect, alert on, and block suspicious communications based on defined OT-aware rules and expected traffic patterns - helping prevent unauthorized access paths and reduce the likelihood of operational impact.