OPSWAT’s elite red team, Unit 515, is dedicated to proactive cybersecurity through advanced testing, adversarial simulation, and in-depth vulnerability discovery. With a mission to strengthen the security of critical infrastructure, Unit 515 initiated a comprehensive security assessment of the Schneider Electric Modicon M241 PLC in early 2025.

Uncovering Multiple Vulnerabilities in the Modicon M241
In February, Unit 515 performed a thorough evaluation of the Modicon M241 to identify potential weaknesses that could pose cybersecurity risks to operational technology (OT) environments. This effort led to the discovery of several vulnerabilities, including data exposure risks, denial-of-service (DoS) conditions, and client-side security flaws.
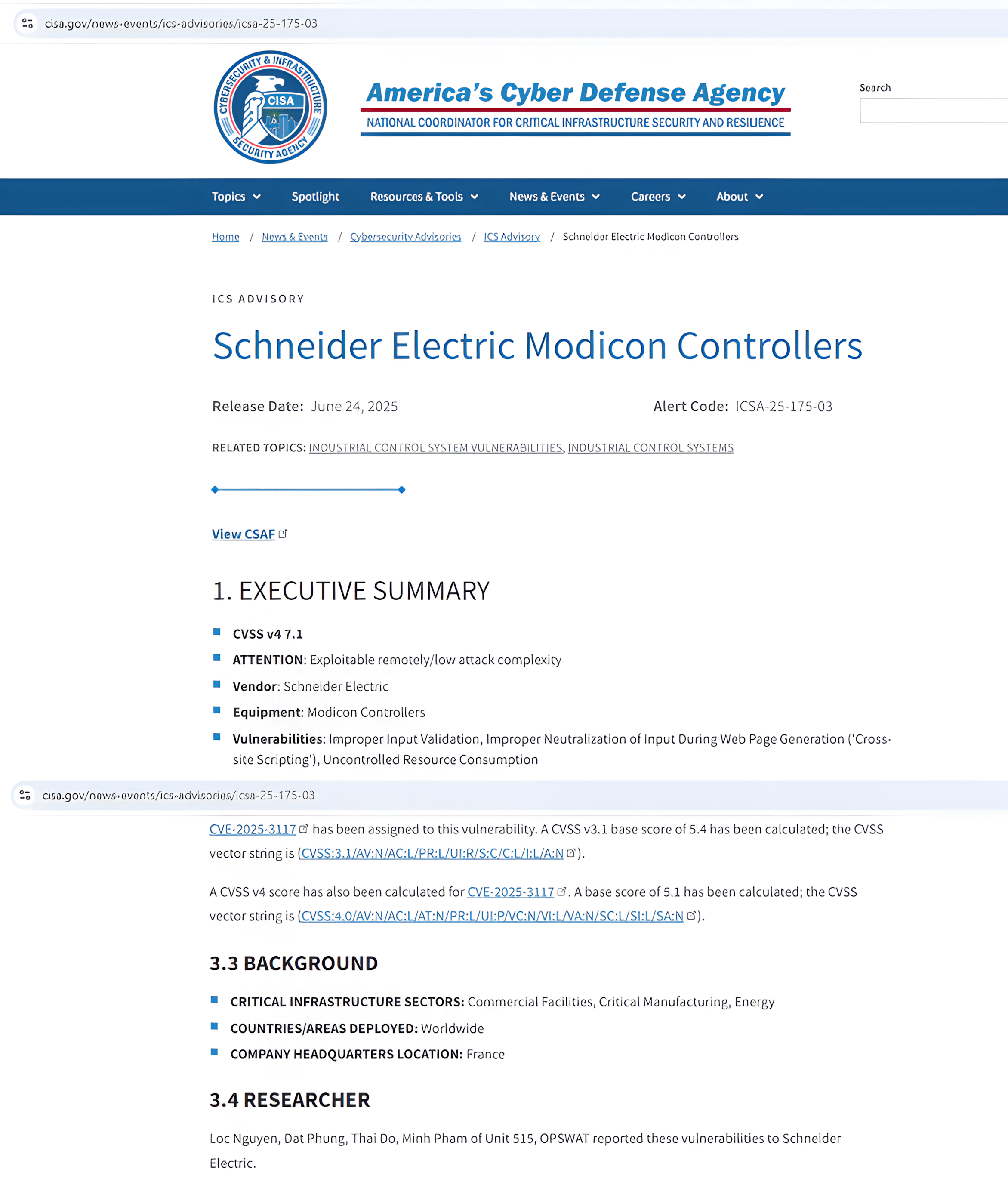
In alignment with responsible disclosure practices and OPSWAT’s commitment to securing industrial systems, Unit 515 promptly reported all findings to Schneider Electric. Following our disclosure, Schneider Electric conducted further investigation and responded with security advisories and firmware patches released in May and June 2025, aimed at remediating these risks and safeguarding their product line.
The first published vulnerability, CVE-2025-2875, was disclosed in May 2025 along with Schneider Electric’s official advisory and remediation guidance.
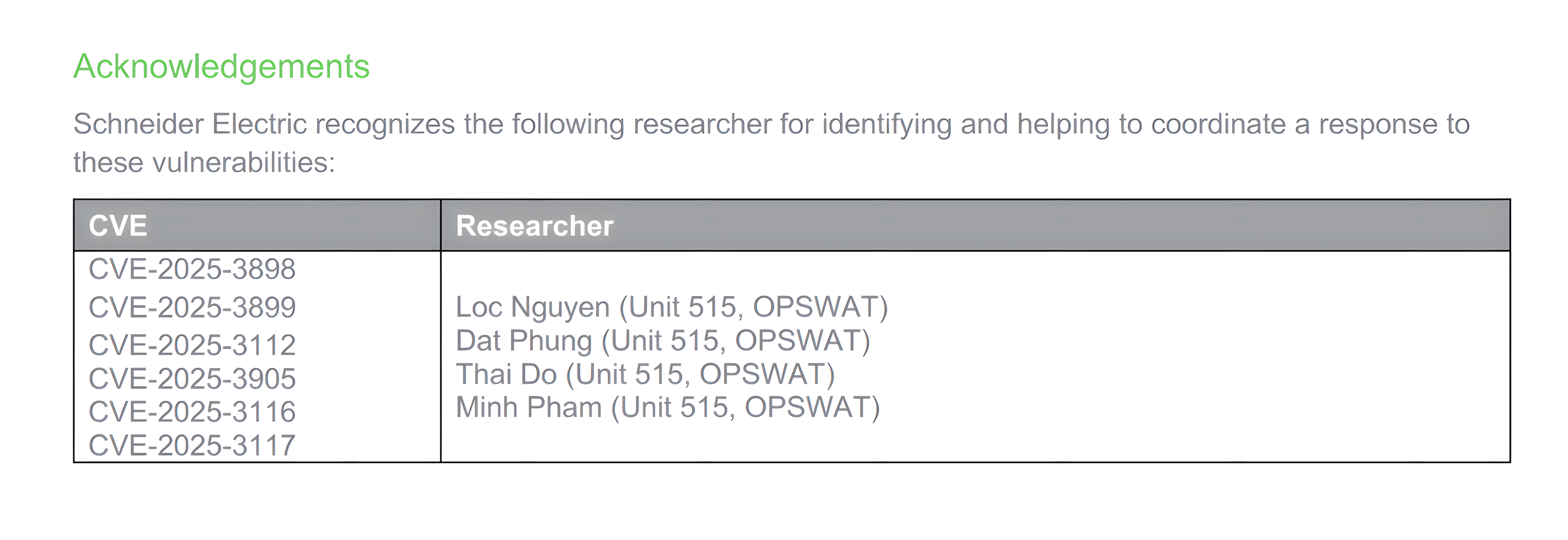
Subsequently, in June 2025, Schneider Electric published additional advisories addressing the remaining vulnerabilities discovered by Unit 515. These CVEs include:
- CVE-2025-3898
- CVE-2025-3899
- CVE-2025-3112
- CVE-2025-3905
- CVE-2025-3116
- CVE-2025-3117
These findings underscore the critical role of proactive security assessments and secure-by-design principles in protecting industrial control systems. OPSWAT remains dedicated to collaborating with vendors and asset owners to uncover and remediate vulnerabilities early - before they pose a threat in operational environments.
Technical Overview of CVEs Identified in Schneider Electric Devices
In close coordination with Schneider Electric, OPSWAT recognizes the sensitive nature of cybersecurity risks in operational technology (OT) environments. To avoid aiding malicious exploitation and to safeguard Schneider Electric customers, OPSWAT has opted not to publicly disclose exploit code or deep technical details of the vulnerabilities.
Below is a high-level summary of the vulnerabilities discovered by Unit 515:
CVE-2025-3898 and CVE-2025-3116 - Improper Input Validation (High Severity)
These vulnerabilities arise from insufficient validation of input data, potentially allowing a Denial of Service (DoS) condition on the affected devices. An authenticated attacker could send a specially crafted HTTPS request with malformed body content to the controller, triggering a crash or unexpected behavior.
- CVE-2025-3898 affected:
- Modicon M241/M251 (firmware versions prior to 5.3.12.51)
- Modicon M262 (versions prior to 5.3.9.18)
- CVE-2025-3116 affected:
- Modicon M241/M251 (versions prior to 5.3.12.51)
- All versions of Modicon M258 and LMC058
CVE-2025-3112 - Uncontrolled Resource Consumption (High Severity)
This vulnerability, with a CVSS v4.0 score of 7.1, could allow an authenticated attacker to exhaust system resources by manipulating the Content-Length header in HTTPS requests, resulting in a denial-of-service condition.
- Affected devices:
- Modicon M241/M251 (versions prior to 5.3.12.51)
CVE-2025-3899, CVE-2025-3905, and CVE-2025-3117 - Improper Neutralization of Input During Web Page Generation (Medium Severity)
These client-side vulnerabilities involve improper neutralization of user input in the web interface, allowing Cross-Site Scripting (XSS) attacks. An authenticated attacker could inject malicious scripts, potentially compromising the confidentiality and integrity of data in the victim’s browser.
- CVE-2025-3899, CVE-2025-3905, and CVE-2025-3117 affect:
- Modicon M241/M251 (versions prior to 5.3.12.51)
- CVE-2025-3905 and CVE-2025-3117 additionally affect:
- All versions of Modicon M258 and LMC058
- CVE-2025-3117 further affects:
- Modicon M262 (versions prior to 5.3.9.18)
Remediation
We strongly recommend that organizations utilizing Schneider Electric Modicon M241/M251/M262/M258/LMC058 PLC devices follow the official guidance provided by Schneider Electric to remediate this vulnerability, available here: Schneider Security Advisory Document
To effectively mitigate these vulnerabilities, organizations should adopt a comprehensive defense-in-depth strategy, which includes:
- Vulnerability detection via continuous CVE scanning and remediation: Regularly scanning networks for vulnerabilities, and apply remediation (best with firmware patching if possible)
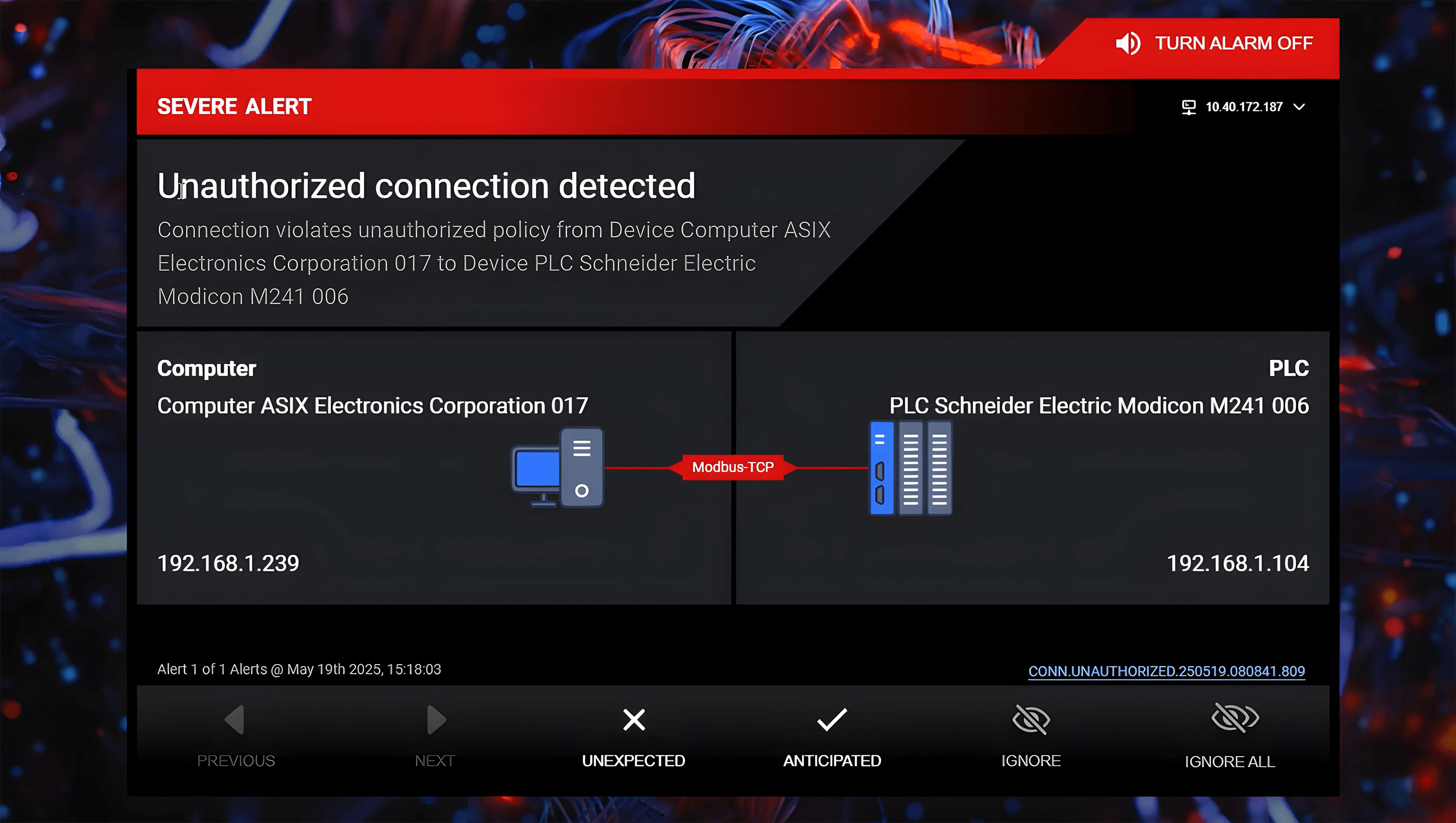
- Monitoring for anomalous behaviors: Flagging unusual increases in frequency in communication to the Schneider Modion M241 PLC, which could suggest an ongoing unauthorized data exfiltration attempt.
- Identifying unauthorized device connections: the system should detect when a rogue/ unauthorized device connects to the PLC.
- Network segmentation: Isolating affected devices can help prevent the lateral spread of attacks, thus minimizing impact.
- Intrusion Prevention: immediately identifying and blocking malicious/ unapproved commands to the PLC, then effectively protect normal operations of the PLC
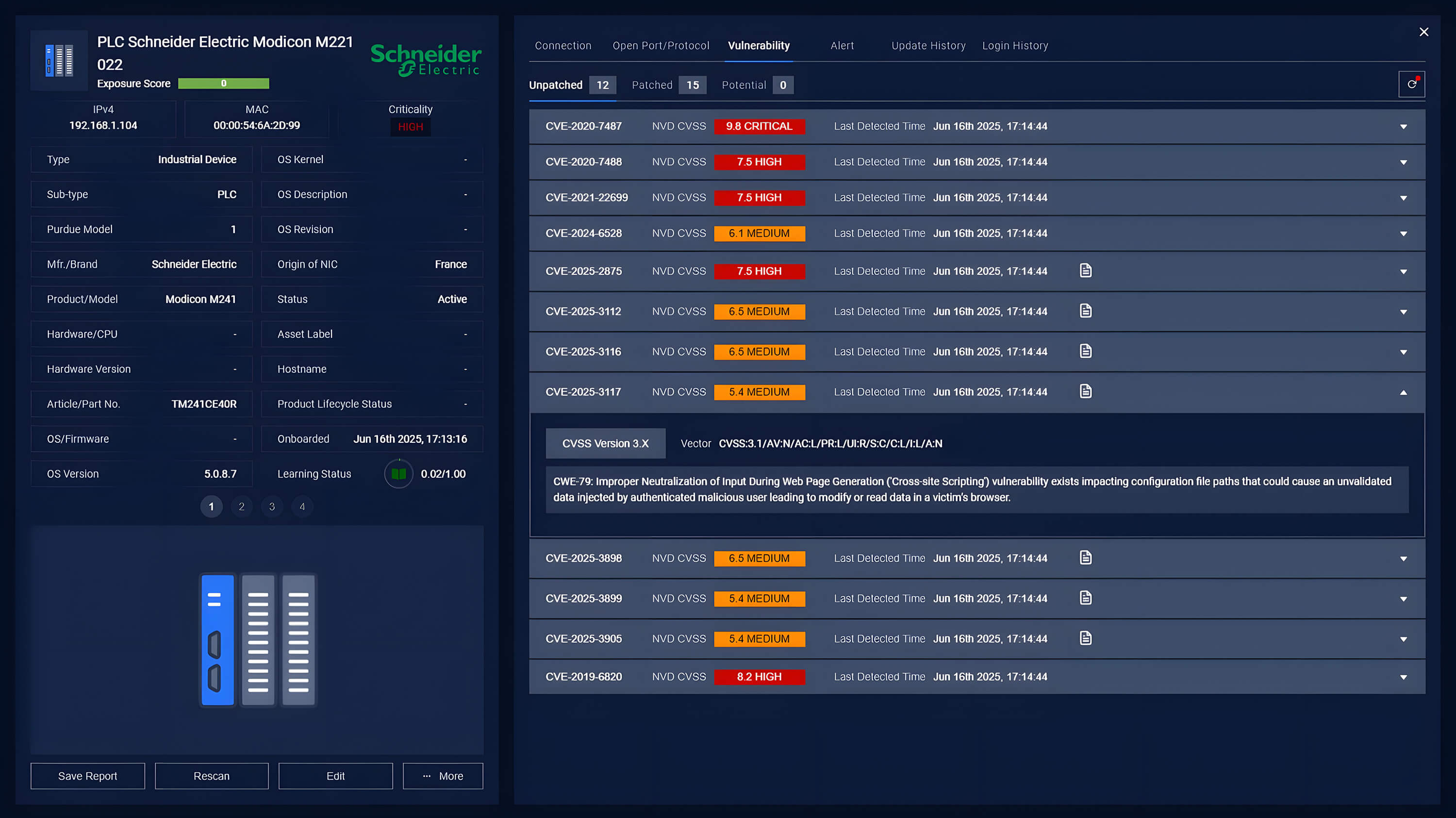
OPSWAT’s MetaDefender OT Security addresses these needs by detecting CVEs, continuously monitoring the network for unusual behaviors and identifying unauthorized connections. Using AI, it learns normal traffic patterns, establishes baseline behavior, and implements policies to alert anomalies. This allows instant, informed responses to potential threats. In addition, MetaDefender OT Security allows remediation of vulnerability with its unique capability of centralized and integrated firmware upgrade for the controllers.
In the case of an attack exploiting these CVEs, MetaDefender OT Security integrates with the MetaDefender Industrial Firewall to detect, alert and block suspicious communications based on set rules. MetaDefender Industrial Firewall uses AI to learn regular traffic patterns and enforce policies to prevent unauthorized connections.
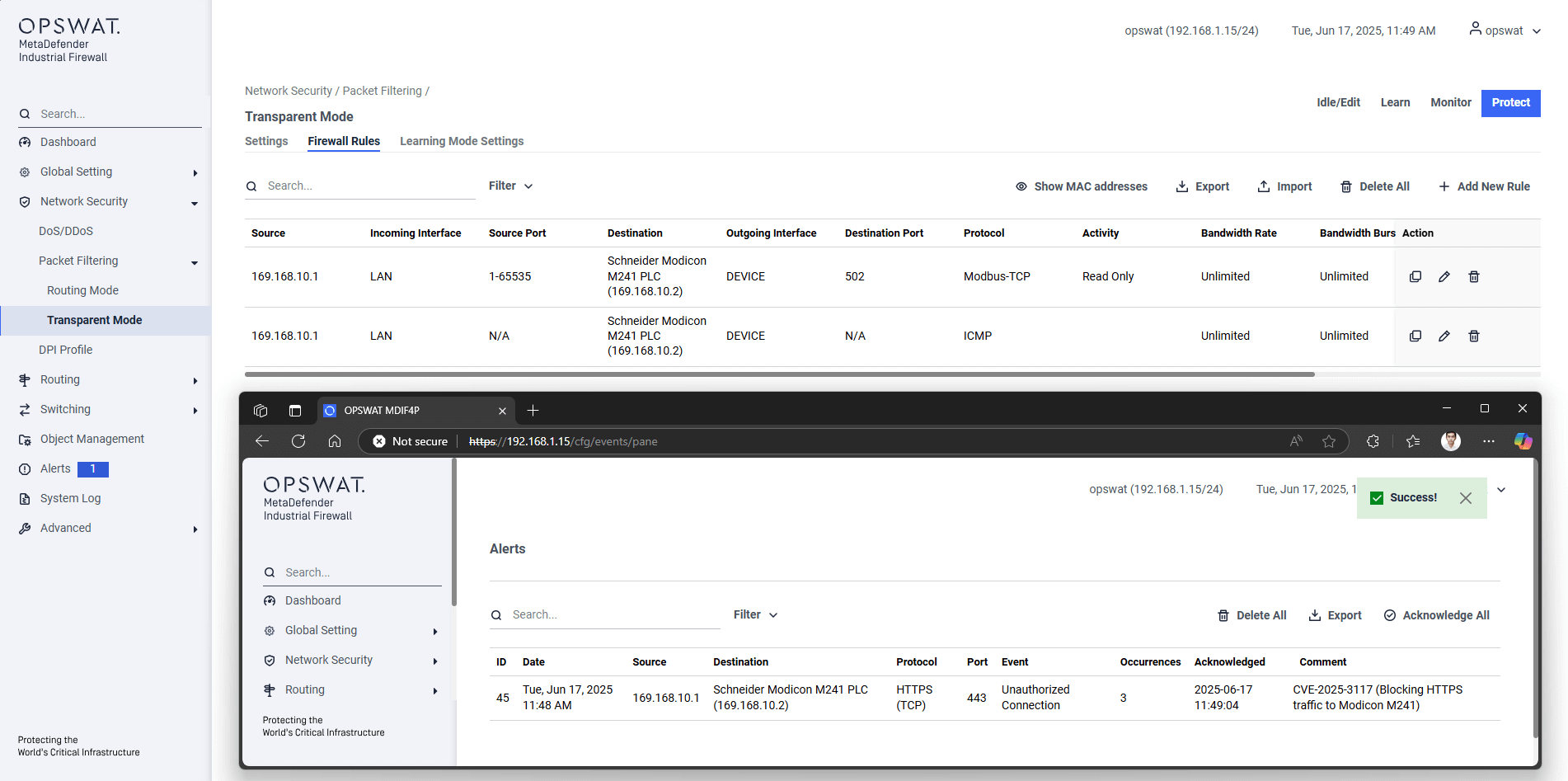
Beyond prevention, OPSWAT’s MetaDefender OT Security also empowers organizations to monitor signs of exploitation in real time through continuous asset visibility and vulnerability assessment. By leveraging advanced asset inventory discovery and tracking, vulnerability assessment and patching capabilities, our platform provides proactive threat detection and facilitates rapid, effective remediation actions.