Remote access has become a critical requirement across industrial environments, whether to enable third-party support, remote maintenance, or real-time troubleshooting. However, implementing remote access into an ICS (Industrial Control System) or OT (Operational Technology) environment introduces new cybersecurity challenges. If not properly managed, it can significantly increase the attack surface and expose critical systems to cyberthreats.
In industrial settings, it's common for organizations to engage third-party vendors or contractors under strict SLAs (service-level agreements), requiring timely support. These support models often necessitate remote access to industrial assets — sometimes urgently. While traditional solutions like VPNs and jump servers are widespread, they are not always sufficient to meet the unique security requirements of OT networks.
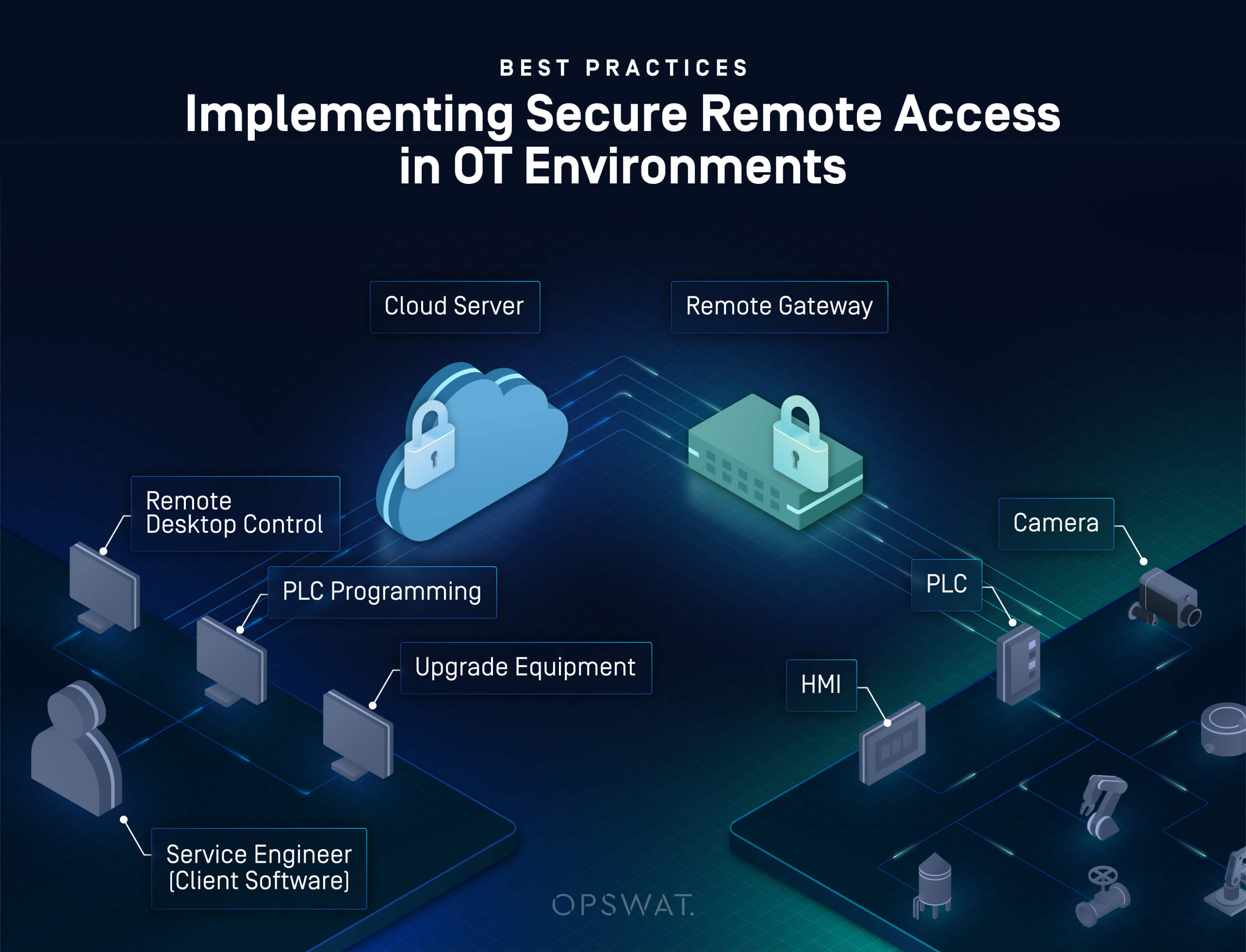
To mitigate the additional risks that remote access introduces, organizations must follow these essential recommendations and best practices:
1. Minimize and Centralize Remote Access Paths
Establish a single, controlled access path for all remote connectivity inyour network. Multiple or ad hoc access routes increase the risk of misconfigurations or oversight, making it easier for attackers to exploit vulnerabilities in your system. A single, centralized path, routed through an access control solution, allows for better visibility, monitoring, and overall control.
2. Enforce “Least Privilege” Access
Apply and follow the principle of “Least Privilege” rigorously. Remote users should have access only to select systems and functions required for their tasks – nothing more. For example, if a third-party vendor needs to only READ data from a PLC, avoid giving WRITE permissions. For contractors, restrict access to their own systems or assets only, and define granular controls around time-based access windows, permitted operations, and device scope.
3. Use DMZs or Proxies to Isolate Critical Systems
Prevent remote users from having direct access to critical OT assets. All remote access should be brokered through a DMZ (Demilitarized Zone), secure access proxy, or unidirectional gateway, ensuring that no inbound connections reach sensitive devices directly. These intermediaries allow additional inspection, logging, and policy enforcement.
4. Verify Remote Endpoints Before Granting Access
Before allowing any device to connect to your OT network, enforce endpoint posture validation to ensure it meets minimum security requirements:
- Is antivirus or anti-malware installed and active?
- Has a recent malware scan been conducted?
- Are there known vulnerabilities on the endpoint?
- Is the device encrypted?
- Is the OS and software fully patched?
This validation prevents compromised or non-compliant endpoints from becoming a gateway into the industrial environment.
5. Enable Real-Time Session Control
Operators in the industrial site should retain the control to monitor, pause, or terminate remote sessions at any time they deem necessary. This control is crucial to respond to unauthorized activity, system malfunction, or potential security incidents.
6. Log All Activity and Integrate with A SIEM
All remote access attempts, authentication events, and in-session activities should be fully logged and auditable. These logs should be forwarded to a SIEM (Security Information and Event Management) system for real-time monitoring, threat investigation and analysis. Proper log retention and forensic capabilities reduce incident response time and support compliance requirements as well.
As remote access becomes indispensable for industrial operations, securing it must be a top priority. Traditional IT access models cannot be blindly applied to OT environments without proper adaptation. A layered approach that includes endpoint validation, access segmentation, session control, and centralized logging is essential for defending critical infrastructure from modern threats.
Secure Path to OT Remote Access
Discover how MetaDefender OT Access provides enterprise-grade security specifically designed for industrial environments.

