When Cybersecurity Protects Our Way of Life
Millions of people rely on essential resources such as water, electricity, or natural gas to live a normal day-to-day life. The scale at which these resources are used is only matched by how fragile and susceptible the systems really are.
The energy and utilities industries play a critical role in a modern society. At the same time, the industry is also highly dependent on technology and it's heavily regulated.
The interconnected nature of its systems leaves it vulnerable to cyberthreats.
A successful cyberattack on an organization operating in this industry would not only cause financial loss for the organization or a breach in data privacy; the consequences could reach far beyond.
This was showcased in 2021 with the Colonial Pipeline attack. The attack, carried out by the DarkSide hacker group, forced the organization to shut down thousands of miles in their pipeline, leading to fuel shortages.
The immediate consequences for private citizens were visible: panic buying, a spike in fuel prices, air travel disruptions. The hack was eventually deemed a national security threat.
In the end, a successful attack in the Energy & Utilities industry will place the people that rely on these services in the line of fire.
Our client, operating in the Middle Eastern Energy & Utilities sector, understood what's at stake, and approached their cybersecurity challenges with great care and consideration.
Dealing with a Fragmented Security Landscape and Incompatibility Issues
Our client managed multiple cloud environments, each with unique security policies, so they needed a solution that could:
Scan file uploads from both external resources and internal repositories to prevent any malware from infiltrating the network.
Simultaneously adapt to different policies so the organization stays compliant across different environments.
To make matters even more complex, their initial solution, relying solely on ICAP, proved incompatible with their existing Palo Alto firewalls, disrupting the seamless integration they were hoping to achieve.
Meeting the Needs for Strength and Flexibility
OPSWAT’s solutions came with a tailored, specific, and strong approach for the client’s ultra specific needs.
To overcome the limitations of real-time upload scanning in all environments, we implemented a post-upload scanning strategy.
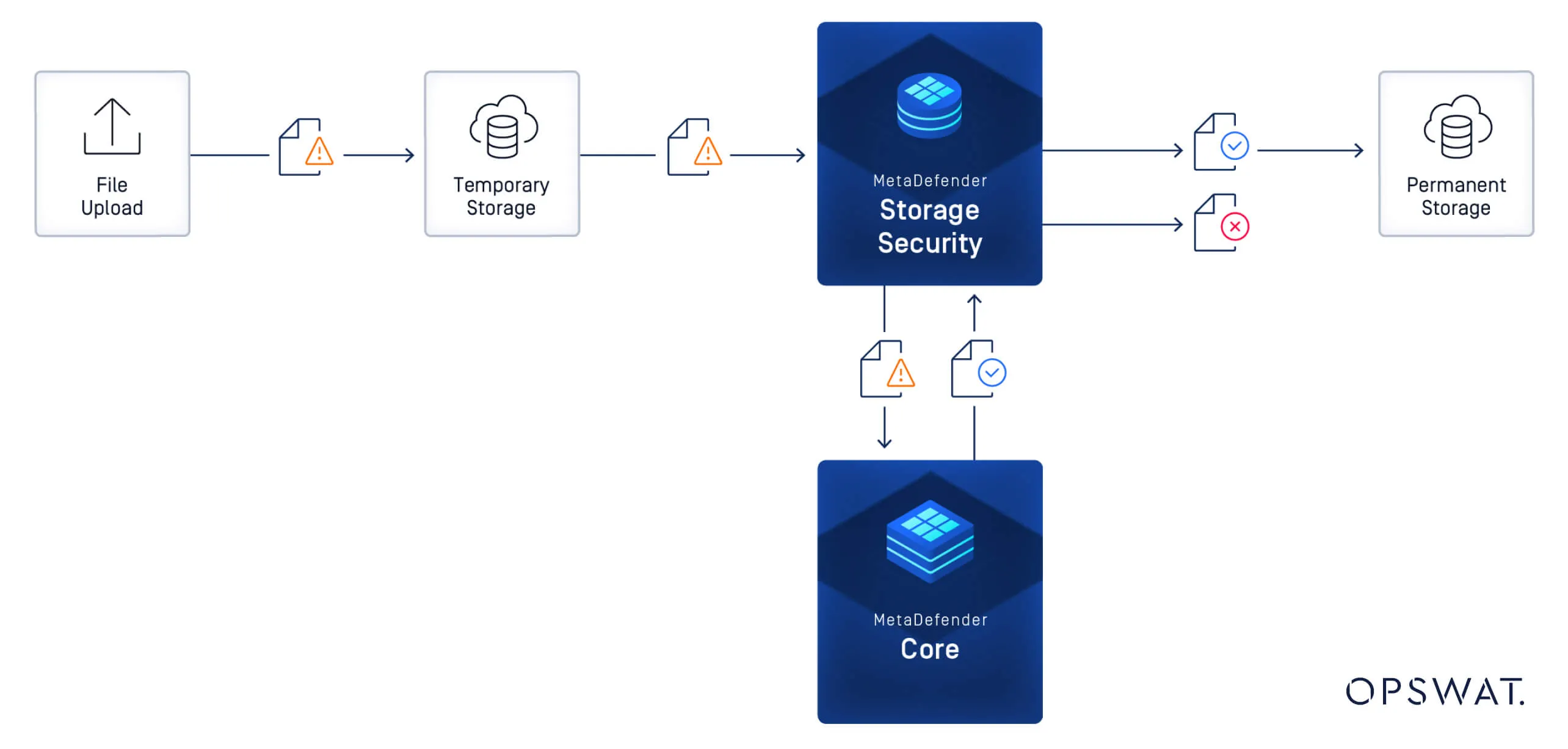
The first step is storing the files in temporary storage.
Next, MetaDefender Storage Security initiates the scanning processes using MetaDefender Core.
Only after the scanning process is complete, are the files moved to permanent storage.
This approach not only ensured the integrity of the scanning process but also provided a smooth upload process.
We addressed the ICAP incompatibility by strategically implementing ICAP-enabled devices in compatible environments.
For environments utilizing Palo Alto firewalls, we adjusted the storage workflow, ensuring secure file scanning without relying on direct ICAP integration with the firewalls.
Transforming a Complex Security Challenge into a Streamlined and Effective Solution
With OPSWAT’s solutions, the client did not have to compromise or choose between agility and security.
After understanding their unique needs, OPSWAT delivered a solution which adapted to the client’s environment, with comprehensive file scanning across their diverse cloud infrastructure:
Post-upload scanning ensured that all files, regardless of their source or destination, were thoroughly scanned for file-borne threats.
The integration with their Palo Alto firewalls showcased OPSWAT’s flexibility and commitment to customer success.
Achieving secure file scanning across the customer’s diverse cloud environments, met their security requirements and ensured customer satisfaction.
To see how OPSWAT can secure your critical operations, contact an OPSWAT expert today.





