A few weeks ago, we published a blog post that posed an important question: How Much Can We Trust PUA Installers? To follow up on this theme and explore the topic a little further, we will now take a closer look at the relationship between vulnerabilities and PUAs (Potentially Unwanted Applications).
End user systems have been increasingly targeted by PUAs in recent years. These are usually offered to users when downloading applications from websites or during the installation of certain software. This can trick end users into thinking that the additional PUA is a component of the application they intend to use. Once these PUAs are allowed access to the user's system, they are likely to flood the user with endless advertisements, collect unnecessary and perhaps sensitive personal information, and slow down the system by occupying a substantial amount of CPU and memory. Furthermore, they provide an additional threat as they can introduce application vulnerabilities (which are considered security holes) to the user's system.
As mentioned in the previous blog post, around 50% of a group of randomly picked PUA installers were reported to contain threats. Does this mean that the other 50% are safe? The answer is definitely not. While some PUAs may not contain any immediate threat themselves, they can still be used as a catalyst for malware and viruses. Since the majority of these types of applications lack thorough maintenance and hit the market without any security protection, allowing them onto an end user's system is more likely to leave this system open and susceptible to attack. Consequently, PUAs increase the possibility of infection to, or the theft of user data from, the system.
There are many different vendors who currently provide huge databases which allow users to verify known vulnerabilities. NVD (National Vulnerability Database) and OSVDB (Open Sourced Vulnerability Database) are two of the most popular ones. For experimental purposes, we used both of these databases to search the 60 PUAs that we tested in the previous blog post for known vulnerabilities. The results of the study can be seen below (click the blue numbers for additional details):
| Product name (Vendor name) | Number of engines reported infection | Number of vulnerabilities reported by NVD | Number of vulnerabilities reported by OSVDB |
| aMule (aMule Team) | 0 | 3 | 2 |
| aMSN (aMSN Team) | 0 | 5 | 10 |
| Anomos (Anomos Liberty Enhancements) | 0 | 0 | 0 |
| Artemis (CyberArtemis LLC) | 1 | 2 | 2 |
| BearShare (MusicLab, LLC) | 1 | 2 | 2 |
| BitHit (P2PHood LLC.) | 1 | 0 | 0 |
| BitLord (BitLord) | 1 | 0 | 0 |
| BitRope Sharing (BitRope) | 1 | 0 | 0 |
| BitSpirit (ByteLinker Inc.) | 0 | 0 | 0 |
| BitTornado (John Hoffman) | 0 | 0 | 0 |
| BitTorrent (BitTorrent Inc.) | 0 | 11 | 55 |
| Bopup Messenger (B Labs) | 0 | 1 | 1 |
| CitrixWire (CitrixWire) | 1 | 0 | 0 |
| Crux P2P (Cruxp2p) | 3 or more | 0 | 0 |
| DBGO (DBGO) | 0 | 0 | 0 |
| Deepnet Explorer (Deepnet Security) | 0 | 0 | 0 |
| Deluge (Deluge Team) | 0 | 2 | 4 |
| Easy File Sharing Web Server (EFS Software, Inc.) | 3 or more | 11 | 22 |
| eDonkey (MetaMachine) | 3 or more | 1 | 3 |
| FeyAccelerator (FeyTools LLC.) | 3 or more | 0 | 0 |
| FeyTorrents (FeyTools LLC.) | 2 | 0 | 0 |
| FlashGet (Trend Media Corporation Limited) | 0 | 1 | 2 |
| Free Download Manager (FreeDownloadManager.ORG) | 0 | 5 | 11 |
| FrostWire (FrostWire) | 1 | 0 | 1 |
| GetRight (Headlight Software, Inc.) | 0 | 1 | 2 |
| Glace Space (CaffeeSoft) | 0 | 0 | 0 |
| Global Downloader (Actysoft Inc) | 3 or more | 0 | 0 |
| Hermes (HermesP2P LLC) | 3 or more | 0 | 0 |
| Lightning Download (Headlight Software, Inc.) | 0 | 0 | 0 |
| LimeRunner (P2PHood LLC.) | 1 | 0 | 0 |
| LimeZilla (ShareZillas) | 1 | 0 | 0 |
| Lphant (Bandoo Media Inc.) | 0 | 0 | 0 |
| Metacafe (Metacafe) | 0 | 2 | 2 |
| Miranda IM (Miranda IM) | 0 | 4 | 8 |
| Miro (Participatory Culture Foundation) | 3 or more | 6 | 0 |
| Movie Torrent (GoodKatShare LLC) | 1 | 0 | 0 |
| ooVoo (ooVoo LLC) | 1 | 1 | 1 |
| P2P Rocket (P2P Rocket LLC) | 1 | 0 | 0 |
| qBittorrent (The qBittorrent project) | 0 | 1 | 1 |
| QIP (QIP.ru) | 1 | 4 | 3 |
| Shareaza (Bandoo Media Inc.) | 0 | 2 | 4 |
| ShareGhost (ShareGhost) | 1 | 0 | 0 |
| Sharin'Hood (P2PHood LLC.) | 1 | 0 | 0 |
| ShareIT (ESIB) | 0 | 0 | 0 |
| StrongDC++ (BigMuscle) | 0 | 0 | 0 |
| SoMud (SoMud) | 0 | 0 | 1 |
| Soul Seek (SoulSeek) | 0 | 1 | 1 |
| Speedy P2P Movie Finder (SPEEDYP2P) | 3 or more | 0 | 0 |
| SuperNZB (TechSono Engineering, Inc.) | 0 | 0 | 0 |
| Tixati (Tixati Software Inc.) | 0 | 0 | 0 |
| Torrent Captor (Torrent Raptors LLC) | 1 | 0 | 0 |
| Torrent Swapper (Tim Tucker) | 0 | 0 | 0 |
| Trilix (Trilixp2p) | 3 or more | 0 | 0 |
| TudZu (Tipi Software) | 0 | 0 | 0 |
| TurboWire (GoForSharing LLC) | 3 or more | 0 | 0 |
| Uranium Backup (Nanosystems S.r.l.) | 1 | 0 | 0 |
| VIP Torrent (VipRumor LLC) | 1 | 0 | 0 |
| Vuze (Azureus Software, Inc) | 2 | 1 | 1 |
| Yet ABC (Choopan Rattanapoka) | 0 | 0 | 0 |
| µTorrent (BitTorrent Inc.) | 0 | 8 | 9 |
According to the results listed above, 26 of the 60 PUAs contain known vulnerabilities. Additionally, 15 of the 30 "clean" PUAs from the multi-scan experiment (documented in the previous blog post) are reported to contain known vulnerabilities. If we combine these results, we notice that 75% (45 out of 60) of the randomly picked PUAs have been flagged as programs which can introduce either malware or known vulnerabilities to user systems.
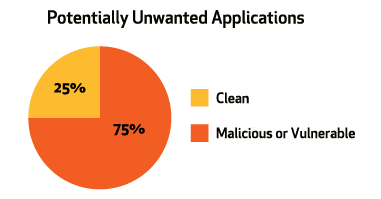
Does this research mean that users have only a 25% chance of downloading a "safe" PUA? Is it possible that the applications that were only detected by one engine and did not contain any of the known vulnerabilities are false positives? The answer to both of these questions may very well be yes. However, it must be noted that all the research data is based on known vulnerabilities and that the vulnerability database is growing every day, every hour, and even every minute. No one can guarantee that any software is positively and undeniably not vulnerable. For example, one has only to recall the recent OpenSSL "Heartbleed" vulnerability case, where the issue was completely unknown until reported, whereupon it became a massive threat.
The PUA industry is changing, and so is the vulnerability world. If end users do not take action or move quickly enough to protect their system, it will likely become an extremely challenging task for IT administrators to maintain and manage their networks. Therefore, user education must play a significant role in the solution. Educating end users to regionalize PUAs and keep them off their systems would go a long way towards helping the network's malware and vulnerability protection levels.
Similar to the previous post, the ultimate suggestion is still to avoid installing and using any PUA on an end user's system. However, if it is absolutely necessary that you avail of some PUA-provided functionalities, then I would suggest that you confirm the following three points before trying to launch any of these PUAs:
- Does the download source come from the application's official website or a reputable software-hosting website?
- Does the application contain any known malware? A multi-scanning website would answer this for you.
- Does the application contain any known vulnerability? Any reputable vulnerability database website would help identify the known vulnerability for a given application.
If the above questions produce any suspect answers, I would highly suggest not using this PUA and reporting it to your IT administrator. Helping to identifying PUAs and protecting the overall network are responsibilities that every end user should undertake.

