Why Legacy Tools Fell Short
The utility's internal defenses were no longer enough. Their homegrown scanning system was inefficient and failed to keep up with modern threats. The detection rates were poor. Scans required manual oversight, often delaying work or introducing inconsistencies across plants.
More importantly, the system couldn’t address the rising risks associated with transient cyber assets, such as contractor laptops and removable media brought onsite for maintenance and diagnostics, which posed new risks. Without a proper scanning process, there was no reliable way to identify malware hiding at the firmware, boot sector, or kernel level.
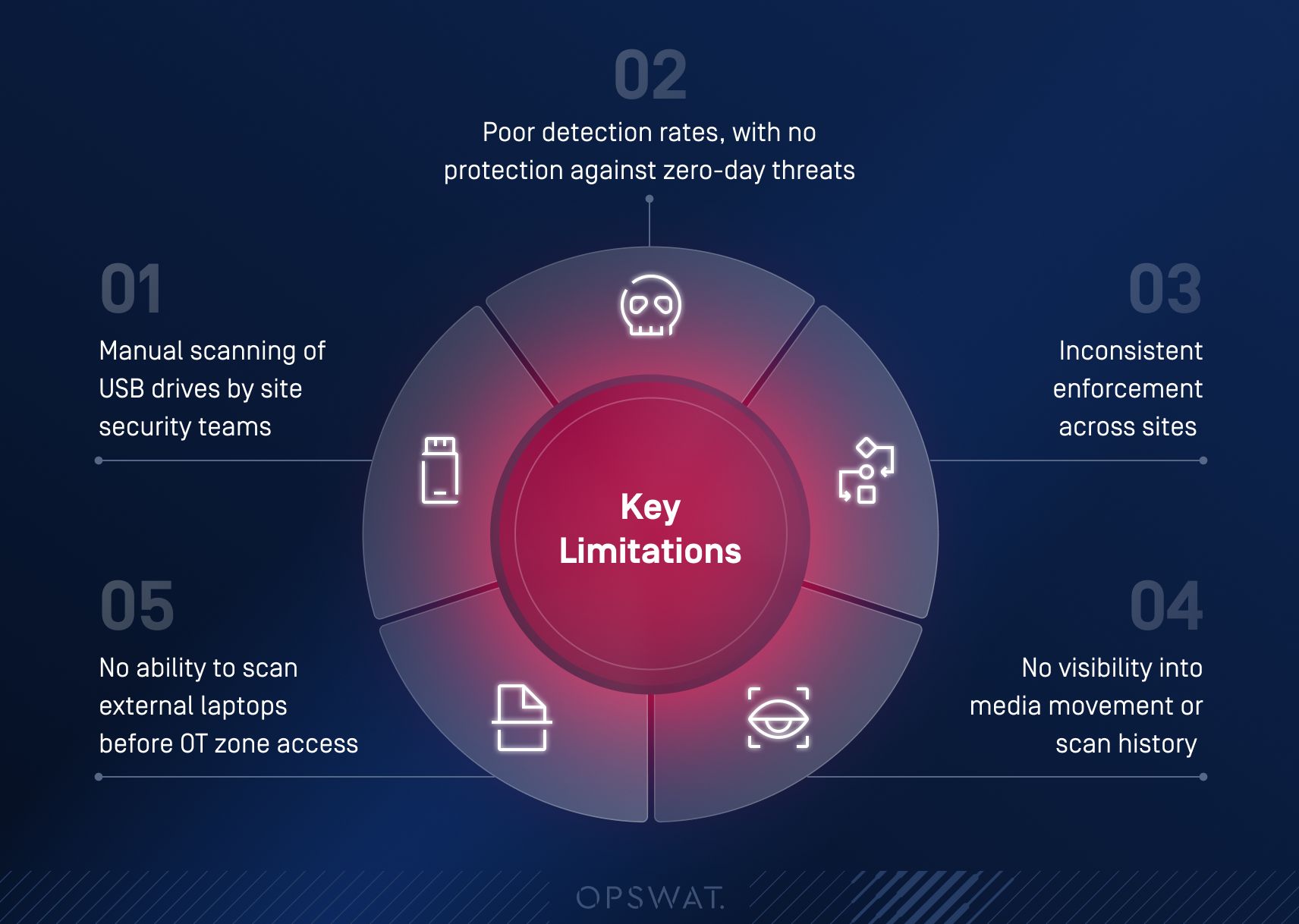
This weakness was not just operational. It risked deep regulatory penalties. Under NERC CIP 003-7, violations can result in fines of up to $1.5 million per day, per violation. The largest fine issued to date reached $10 million. To avoid such consequences, the company needed a compliant approach to managing transient devices and removable media as their existing tools lacked centralized control, consistent enforcement, or reporting capabilities.
Meanwhile, threat actors were evolving. According to the IBM X-Force Threat Intelligence report, in 2024, nearly one in three intrusions exploited valid credentials or public-facing vulnerabilities, many of them undetected for weeks. Credential harvesting surged, infostealer malware grew by 84% year-over-year, and critical infrastructure operators faced a growing wave of campaign-level attacks targeting supply chains and air-gapped networks.
For a utility that manages physical assets, complex supply partners, and operational zones not designed for modern cybersecurity, the risks were real and growing by the day.
A Purpose-Built Approach to Removable Media & Third-Party Laptop Security
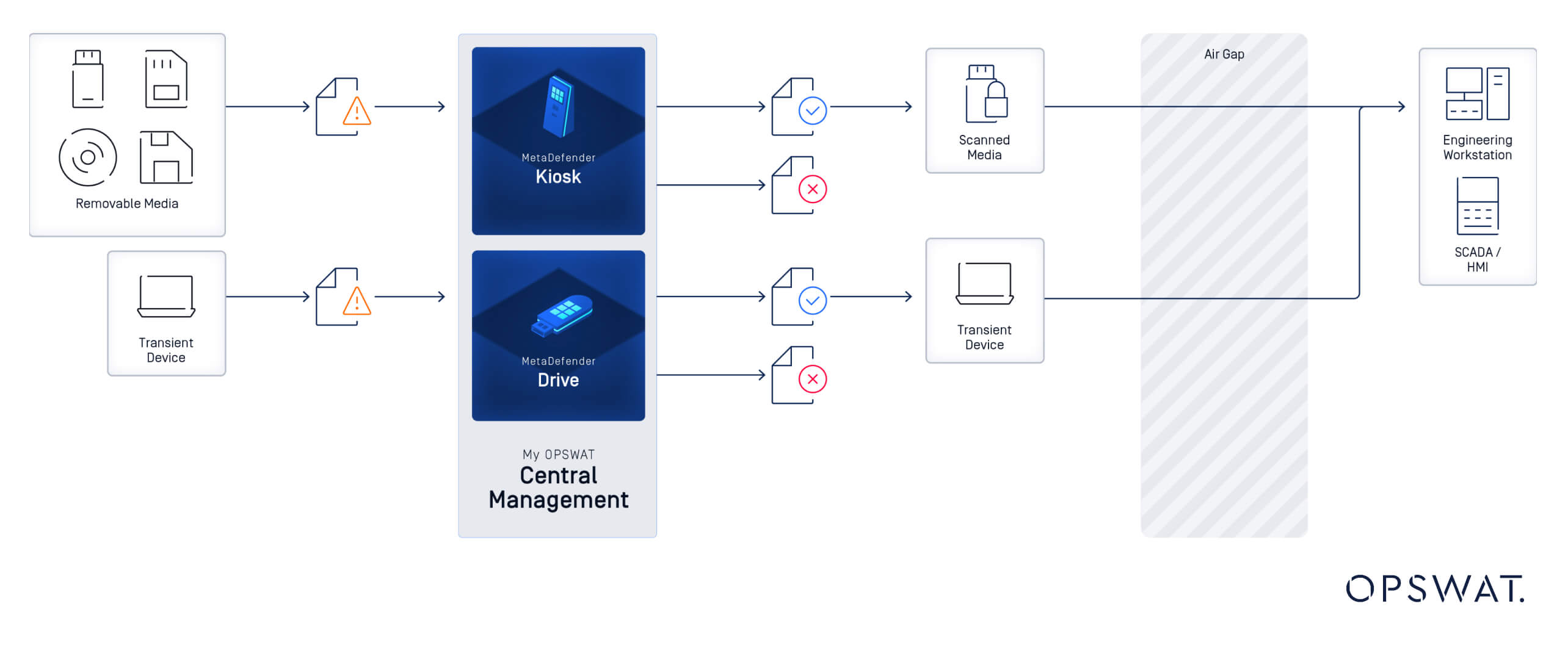
The company started with a pilot program at one site, testing MetaDefender Kiosk and MetaDefender Drive in live operational environments. Field teams found the tools immediately valuable and easy to use. That early success led to a broader rollout across major plants, eventually scaling to dozens of Kiosks and hundreds of Drives. Together, these tools formed a robust, OT-ready solution that brought confidence back to device and media handling inside sensitive environments.
3 Key Solutions for Integrated Defense
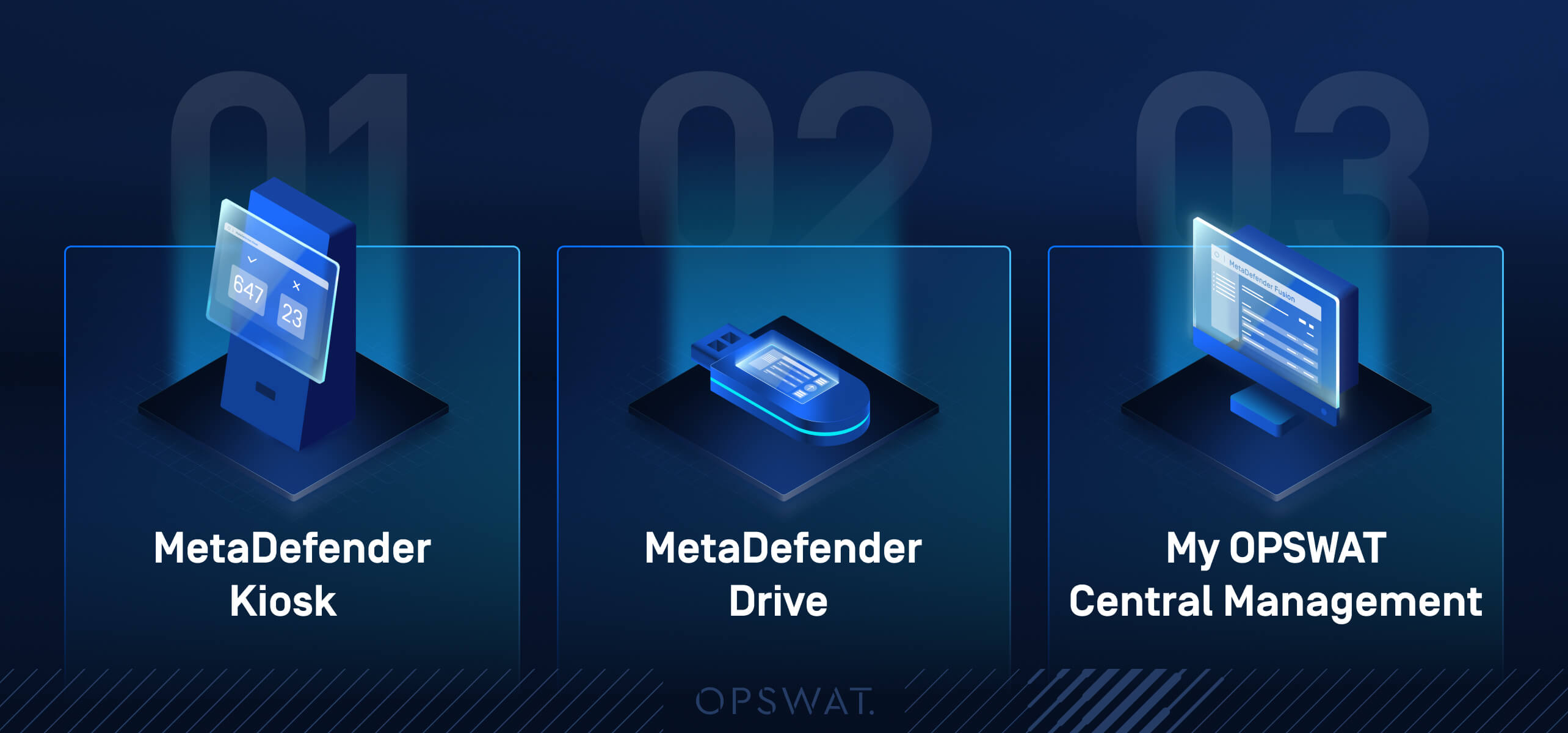
1. MetaDefender Kiosk
MetaDefender Kiosk serves as a critical security checkpoint for all removable media devices, acting as the first line of defense at your network's entry point. USBs, External Hard Drives, MicroSD, SD Cards, and CD/DVDs are rigorously scanned for malware, vulnerabilities, sensitive data, blocking threats before they reach critical networks. Additionally, Kiosk leverages these core technologies:
Metascan Multiscanning
Scans with 30+ anti-malware engines for broad threat detection.
Deep CDR
Sanitizes files by rebuilding them into safe, usable versions.
Proactive DLP
Prevents sensitive data from entering or leaving the network.
File-Based Vulnerability Assessment
Identifies known weaknesses in files and applications.
Adaptive Sandbox
Safely execute suspicious files in an isolated environment for analysis.
Country of Origin
Identifies the geographic source of uploaded files.
These technologies work in conjunction to provide a robust and multi-layered defense against threats carried by removable media. With its robust functionalities, MetaDefender Kiosk ensures OT compliance by enforcing security controls that meet NERC CIP 003-7, NIST 800-53, and ISA/IEC 62443, NEI 08-09 standards.
2. MetaDefender Drive
MetaDefender Drive plays a different but complementary role. Before any third-party laptop is powered on inside a secure zone, it's scanned offline using MetaDefender Drive’s contained, secure operating system. The tool inspects everything — from user files to firmware and boot sectors — with no need to install software. That means contractors can be cleared quickly and safely without touching the internal network.
By scanning vendor and contractor laptops offline before they connect to operational systems, the company now enforces a consistent supply chain protection policy, without disrupting workflows or requiring software installs. This process directly supports compliance with NERC CIP-003-7 for transient cyber assets, as well as NIST SP 800-53 and 800-82 guidelines for securing OT environments against external devices.
3. My OPSWAT Central Management
To manage the deployment at scale, the company brought all devices under My OPSWAT Central Management. This gave security teams unified control, automated reporting, and consistent policy enforcement across the fleet, which marked a critical improvement over manual oversight.
The platform provides a single pane of glass to manage policy enforcement, monitor system health, and coordinate updates across all MetaDefender devices. It also enables real-time visibility into global threat activity and deployment status, reducing manual effort while improving incident readiness.
A Safer, Faster & More Compliant Operation
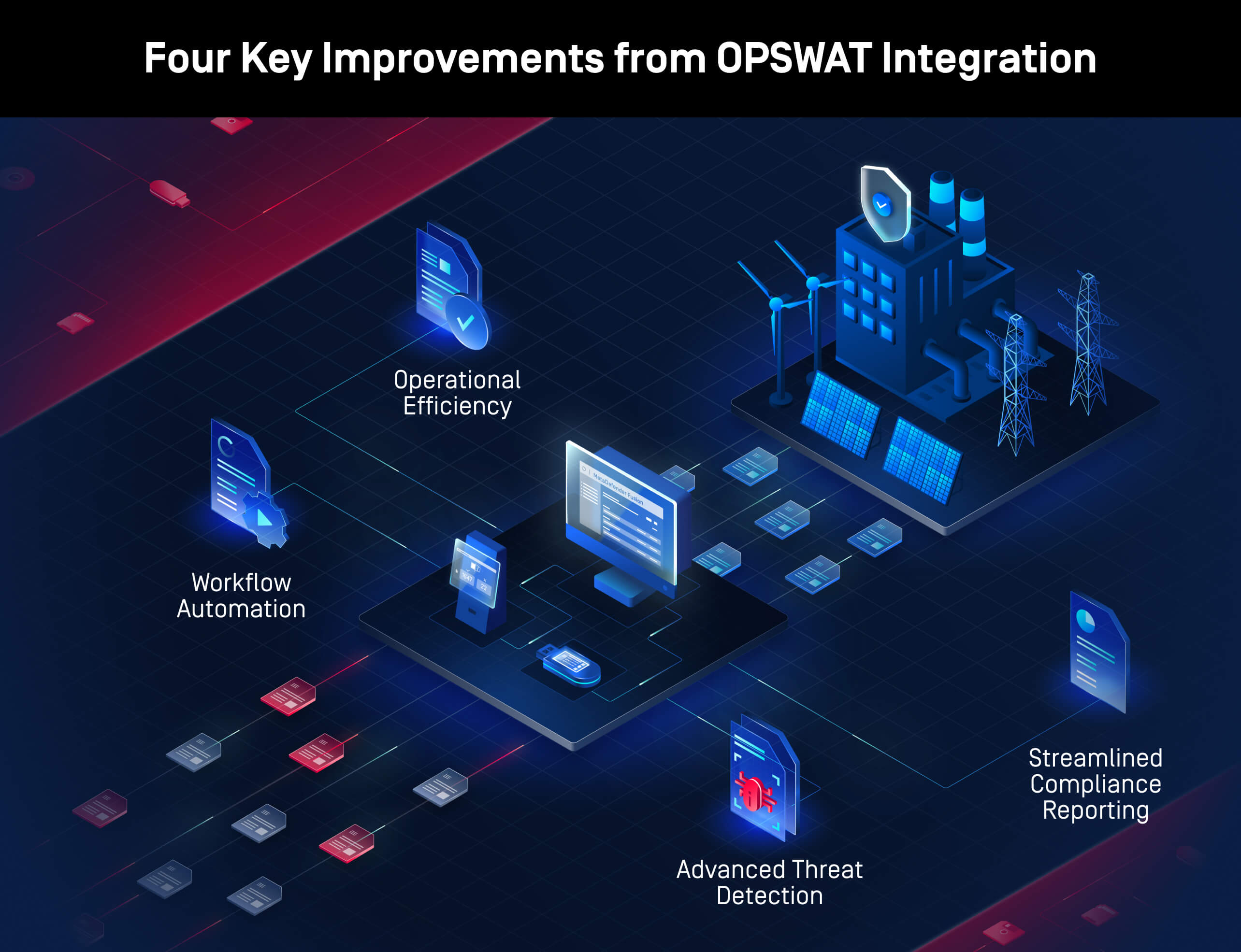
The integrated deployment of MetaDefender Kiosk, MetaDefender Drive, and My OPSWAT Central Management helped the company proactively remediate detected issues, preventing potential threats from spreading across the network. As a result, the company saw four primary areas of improvement:
Workflow Automation
Today, every file is scanned upon arrival with no exceptions or manual steps. MetaDefender Kiosk enforces this automatically, removing the burden from site security managers and ensuring a consistent, auditable process. MetaDefender Drive is now used to scan third-party laptops offline before they enter sensitive OT zones, eliminating the need for temporary installations or trust-based approvals.
Advanced Threat Detection
Threat detection has significantly improved. With OPSWAT’s Multiscanning technology, which can achieve up to 99.2% malware detection when combining 30+ engines, the company can close the gaps that single-engine tools left behind. This multilayered scanning approach also includes protection against zero-day threats and deeply hidden malware, which traditional methods often miss.
Streamlined Compliance Reporting
Compliance efforts have become more streamlined. My OPSWAT Central Management provides centralized oversight and automated reporting, allowing compliance teams to generate reports with minimal effort.
Operational Efficiency
What used to take days now takes hours. The organization can now operate faster, with more confidence, knowing that every device and file entering the environment has been thoroughly vetted. The utility’s security team continues to adapt its strategy, prioritizing safety, continuity, and compliance across all operations.
In OT environments, you can't afford assumptions. Every file, every device must be verified before it gets anywhere near our systems. With MetaDefender Drive and MetaDefender Kiosk, we not only block threats before they reach critical assets, but we also have the proof for compliance with confidence.
Site Security Manager
Proven Defense at Every Entry Point
These improvements have strengthened the company’s ability to detect and contain sophisticated threats before they reach critical systems. By securing every file and device at the point of entry, the organization is better equipped to defend against targeted attacks on its infrastructure.
As cyberattacks grow more advanced and regulations more specific, organizations can no longer rely on ad hoc tools or manual checks. OPSWAT’s platform offers purpose-built protection that fits the reality of critical infrastructure environments: air gaps, compliance audits, and zero tolerance for downtime.
To see how OPSWAT solutions can help secure your critical infrastructure, talk to an expert today.





