Water and wastewater operators manage cyber risk while keeping plants running without interruption. Adversaries target both business and operational systems, often through routine file exchange and third-party services. Dispersed sites and contractor activity increase variability in how media is handled. Consistent, auditable controls for removable media are a practical requirement.
Industry Landscape
According to the World Economic Forum’s Global Cybersecurity Outlook 2025, 72% of organizations surveyed say cyber risks rose in the past year. 54% of large organizations cite third-party and supply-chain challenges as the biggest obstacle to resilience, which complicates controls across vendors and field partners. Regional preparedness varies for major incidents targeting critical infrastructure, underscoring systemic risk if water utilities are hit.
Geopolitics affects strategy in nearly 60% of organizations, increasing the likelihood of spillover attacks on critical infrastructure. Public-sector entities, which include regional utilities, report different resilience confidence levels than private peers.
File-Borne & OT-Relevant Threats
The 2025 OPSWAT Threat Landscape Report notes increasing pressure on OT cybersecurity and critical infrastructure, including utilities. Adversaries blend financial motives with espionage, raising the risk of operational disruption. Below are key file-borne threat types affecting OT and critical infrastructure today.
File-based vectors
PDFs, archives, and HTML remain common malware carriers, and HTML smuggling is rising.
Example: A vendor arrives with a USB holding a project ZIP and a PDF submittal. A hidden script triggers when the ZIP is unpacked on an engineering workstation, aiming to pivot into plant systems unless the media is scanned at intake and validated again at use via endpoint checks.
Phishing and social engineering
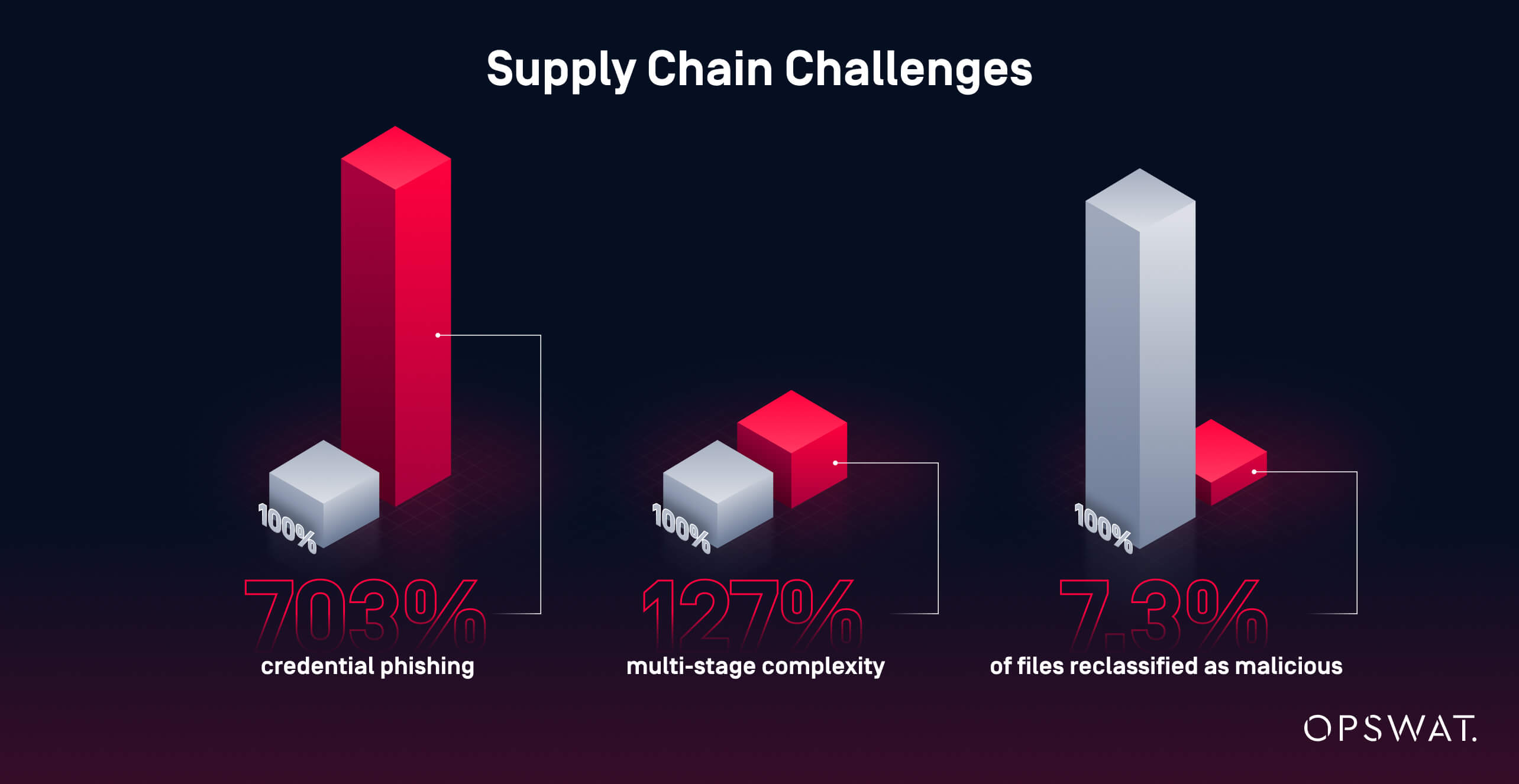
Email-driven compromises often begin with credential theft or fileless scripts that stage payloads. One study mentioned in the OPSWAT report measured a 703% spike in credential-phishing campaigns.
Example: A contractor’s laptop is phished offsite then used to copy “clean” reports to a USB for a site visit. The staged payload rides along and would execute first open inside the plant without scanning and endpoint validation.
Attack chains
Multistage malware is increasingly complex, and single-engine or signature-only screening can miss threats later caught by deeper analysis. OPSWAT telemetry shows a 127% jump in multi-stage complexity, and that 7.3% of files missed by public feeds were reclassified as malicious.
Example: An archive with a benign-looking config file passes a single AV engine scan, then pulls a second-stage component after it is opened on a jump host. Without multiple antivirus scanning at entry and validation at use, the delayed activation can slip into the control environment.
Why This Mattered to Our Customer
The organization operates dispersed facilities that historically accept data from removable media and contractor devices. Without enforced, auditable scanning and user authorization at entry points, one infected file could interrupt treatment processes, trigger costly downtime, or erode public confidence. The risk profile matches sector trends, where file-based malware, phishing-led intrusions, and supply-chain exposures intersect with always-on operations serving millions.
Reinforced Perimeter for Every Site
A standardized OPSWAT stack now controls every piece of removable media before it touches the utility provider’s plant or office systems. In practice, every site has a predictable intake point, consistent logs of who scans what and when, and a repeatable way to keep unvetted media out of control networks. Verify-at-use is enforced by MetaDefender Endpoint Validation™ on endpoints.

MetaDefender Kiosk Desktop & App
Fixed MetaDefender Kiosk™ Desktop units are now the first stop for any removable media devices such as USB drives, SD cards, or discs headed toward operational systems. Visitor management restricts kiosk use to authenticated personnel, so staff and contractors must authenticate with company credentials to scan media and receive clear pass or block result.
Kiosk policy now layers three advanced controls on top of Multiscanning. Deep CDR™ Technology deconstructs and regenerates files to remove active content, delivering threat-safe copies for allowed types. Proactive DLP™ inspects files for sensitive data and, per policy, blocks or redacts before release. File-based Vulnerability Assessment checks installers, firmware, and software packages for known vulnerabilities and blocks items that fail policy.
The MetaDefender Kiosk Application extends the same workflow to authorized workstations in offices and engineering spaces. Sites with limited connectivity follow identical workflows, including offline enforcement, so air-gapped locations receive the same scanning, sanitization, DLP, and vulnerability checks before any transfer.

MetaDefender Endpoint Validation
After files are scanned by MetaDefender Kiosk, MetaDefender Endpoint Validation verifies at the moment of use that media was scanned under enforced policies and that files remain unaltered.
If anything changes, access is blocked until the item is rescanned and revalidated. This closes the common loophole where clean media becomes risky after content edits or file additions. It also adds a security layer at entry points that do not always sit near a kiosk, including air-gapped networks or low-connectivity sites.

Metascan Multiscanning
Metascan™ Multiscanning is the first inspection stage at the kiosk. For this deployment, it is configured with 12 antivirus engines to increase detection coverage and reduce single-engine blind spots. Policy applies engine sets by file type and inspects archives and nested content before any release decision. Multiscanning operates the same way at connected and air-gapped sites, and it feeds clean or flagged outputs into Deep CDR™ Technology, Proactive DLP, and File-based Vulnerability Assessment according to the site’s workflow.
How it Works, End to End
- User authenticates at a MetaDefender Kiosk or approved workstation and inserts media. Files are scanned with Metascan Multiscanning and other policy controls.
- Policy actions apply as needed, including Deep CDR™ Technology, Proactive DLP, and file-based vulnerability checks, before release.
- Kiosk issues a validation signature and records file hashes for files that are allowed.
- MetaDefender Endpoint Validation checks the kiosk signature and file hashes.
- Audit logs and reports document who scans what and when, supporting compliance.

What Changed on the Ground
- Control: Media enters through controlled checkpoints, not ad hoc USBs and discs
- Authentication: Only authenticated personnel can use kiosks to scan and transfer files
- Scanning enforcement: Endpoints running MetaDefender Endpoint Validation allow access only to media and files verified by enforced policies
- Revalidation: Modified content is flagged and routed back for rescanning until validated
- Consistency: Air-gapped and connected sites follow the same workflow, improving consistency across locations
- Sanitized, policy-compliant files are released, while vulnerable or sensitive items are blocked or redacted before use
Building a Predictive Defense
With the media control program in place, the focus shifts to scale, visibility, and continuous improvement. My OPSWAT Central Management aggregates MetaDefender Kiosk scanning reports and logs and centralizes scan events, user access logs, policy actions, and endpoint validation results across sites.
Operations and security teams review trends, refine policies, and plan capacity using one source of truth. The same dataset supports compliance reporting and incident readiness across water and wastewater facilities.
Suggested next steps include:
- Central analytics to surface patterns in media usage and blocked threats
- Policy tuning based on trend data, including engine configuration and workflows
- Phased expansion to additional sites and contractors for consistent controls
Stronger Plants, Safer Region
The organization replaced unsecured, ad hoc media handling with a consistent, enforced process across plants and offices. MetaDefender Kiosk, MetaDefender Endpoint Validation, and Metascan Multiscanning provide scan-before-entry controls (kiosk scanning prior to transfer) and verify-at-use controls (endpoint checks that allow only kiosk-approved, unaltered files). The result is lower operational risk, clearer accountability, and a repeatable path to continuous improvement.
Want a direct walkthrough? Contact us to see how MetaDefender Kiosk can work in your environment.





