As cyberthreats continue to evolve, attackers are finding new ways to evade detection through unconventional file types, embedded malicious content, and novel attack vectors. OPSWAT’s latest security enhancements take threat detection to the next level, providing organizations with powerful tools to analyze, classify, and neutralize threats with greater precision. From custom file type detection to deep inspection of PCAPs (network packet captures), these upgrades ensure security teams stay ahead of emerging risks.
File Type Detection
Define Custom Rules
Organizations often encounter files in unique or proprietary formats that standard tools can’t immediately recognize. Waiting for vendor-provided fixes can stall workflows, leaving teams unsure whether to block these files (risking disruption) or allow them (risking exposure).
The File Type Detection engine addresses this with custom rule-based file type detection, enabling organizations to define their own classification logic for unrecognized files.
- Define your own criteria (e.g., headers, extensions, or byte patterns) to classify unsupported formats.
- Act immediately—no need to wait for updates.
- Balance security and productivity by tailoring rules to your organization’s specific file-handling policies.
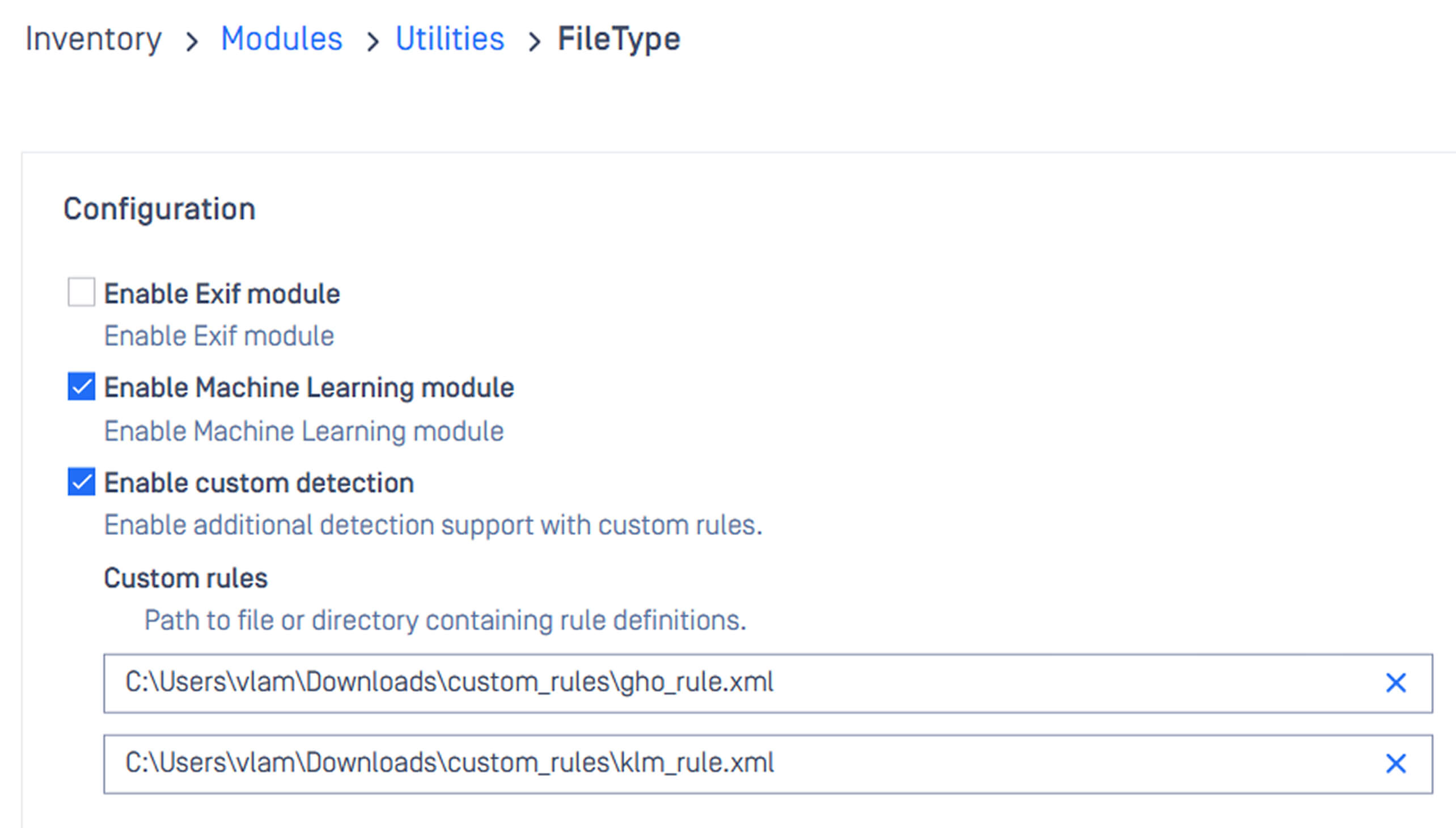
This puts control back in your hands, ensuring even niche or new file types align with your workflows.
Deep CDR™
Provide "Reason for Action"
Modern documents are more than just text and images—they contain metadata, embedded objects, and even hidden scripts that can serve as attack vectors. While macros are widely recognized as risky, subtler threats like document properties, template references, or QR codes embedded in legacy Office files often evade scrutiny.
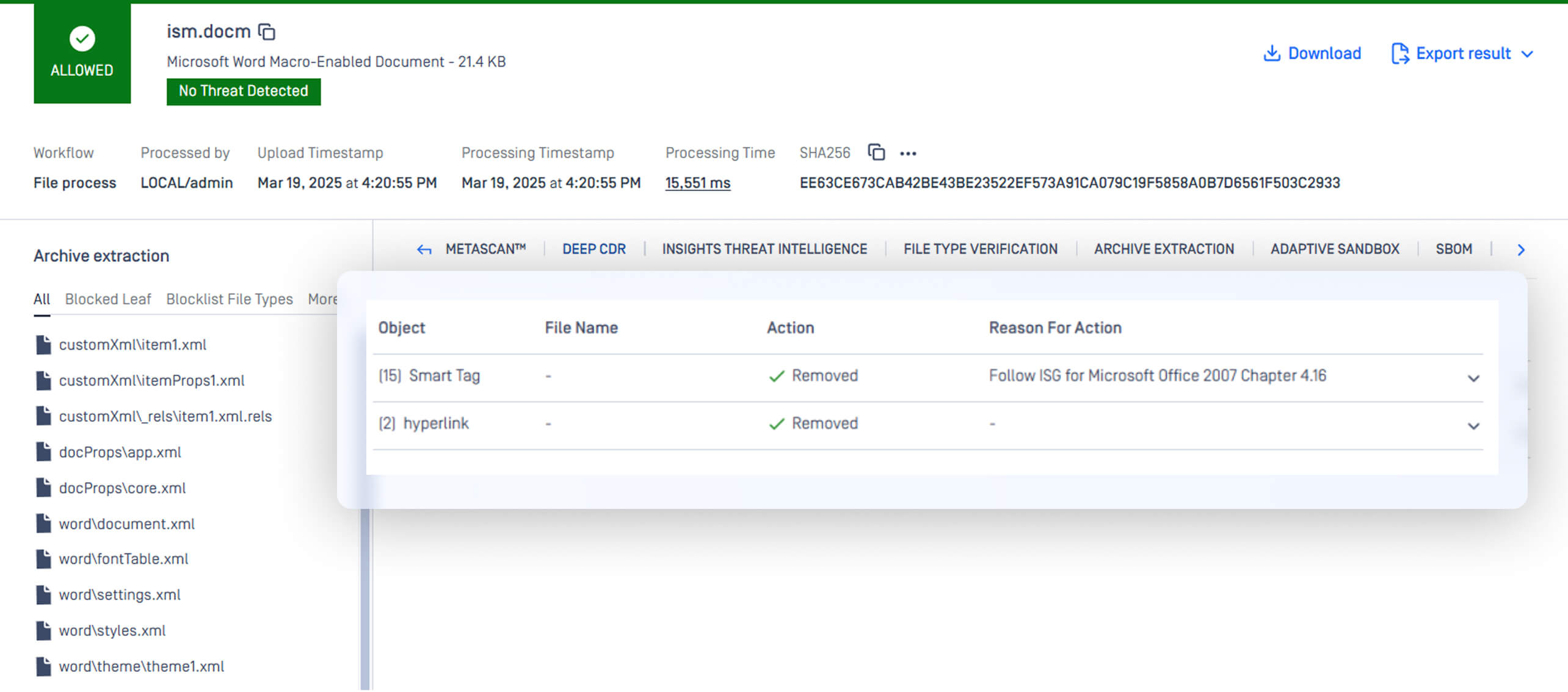
Deep CDR now provides detailed “Reason for Action” explanations, helping security teams understand why specific elements were sanitized. This transparency is crucial for compliance, forensic analysis, and user trust.
Detect ASCII-Based QR Codes
Threat actors continuously innovate to evade detection. One emerging tactic involves embedding malicious QR codes in ASCII format. These QR codes, when scanned, can lead to phishing websites or malicious downloads.

Deep CDR now detects and neutralizes ASCII-encoded QR codes, mitigating this novel attack vector before it can be exploited.
Recursively Sanitize Base64-Encoded JSON Data
Another critical enhancement is deep inspection of Base64-encoded JSON data. Attackers increasingly embed malicious payloads in encoded strings within API responses or configuration files.
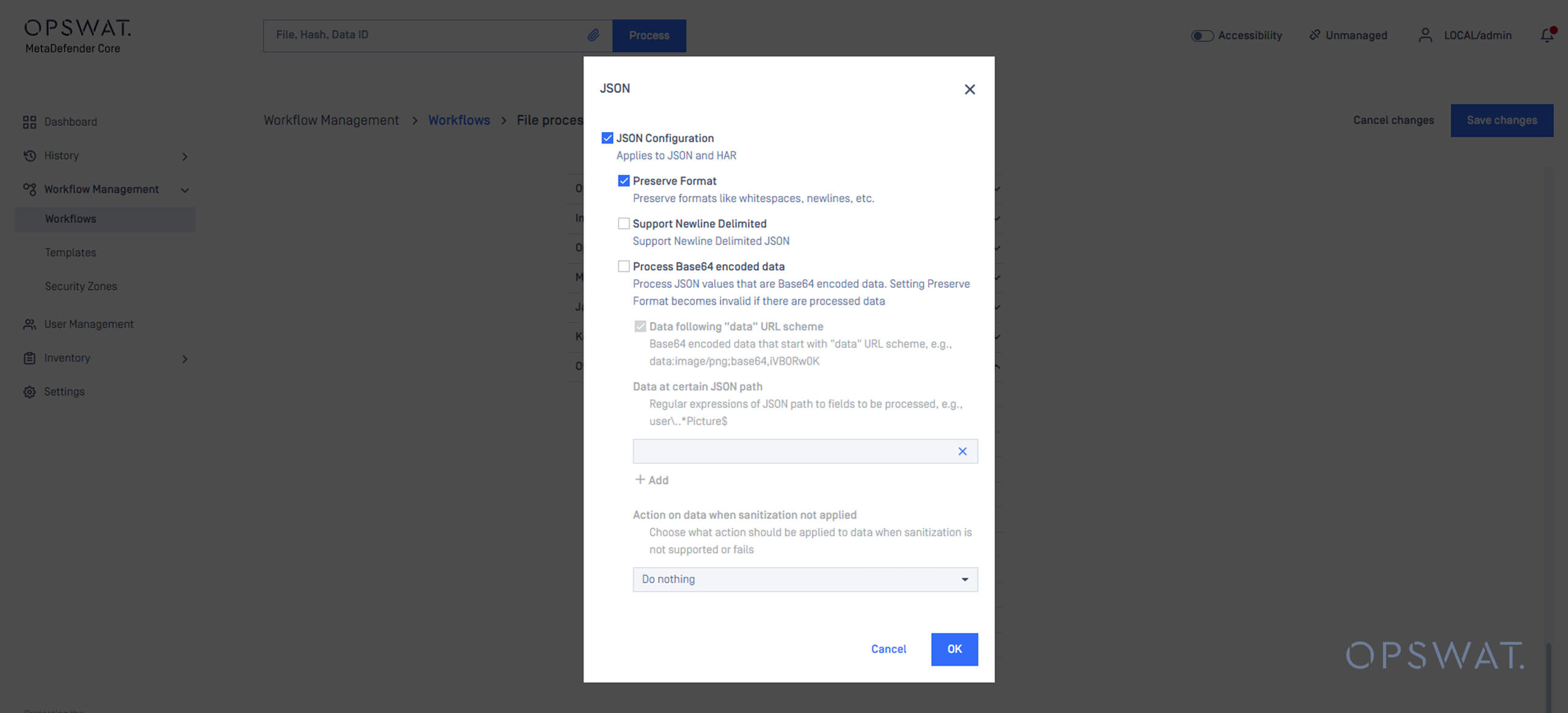
Deep CDR now includes recursive sanitization functionality for Base64-encoded JSON content, ensuring that:
- The Base64-encoded data is decoded.
- The extracted content is sanitized.
- The sanitized data is re-encoded in Base64 and reinserted into the JSON structure.
This process ensures that no threats remain embedded within structured data files.
Archive Extraction
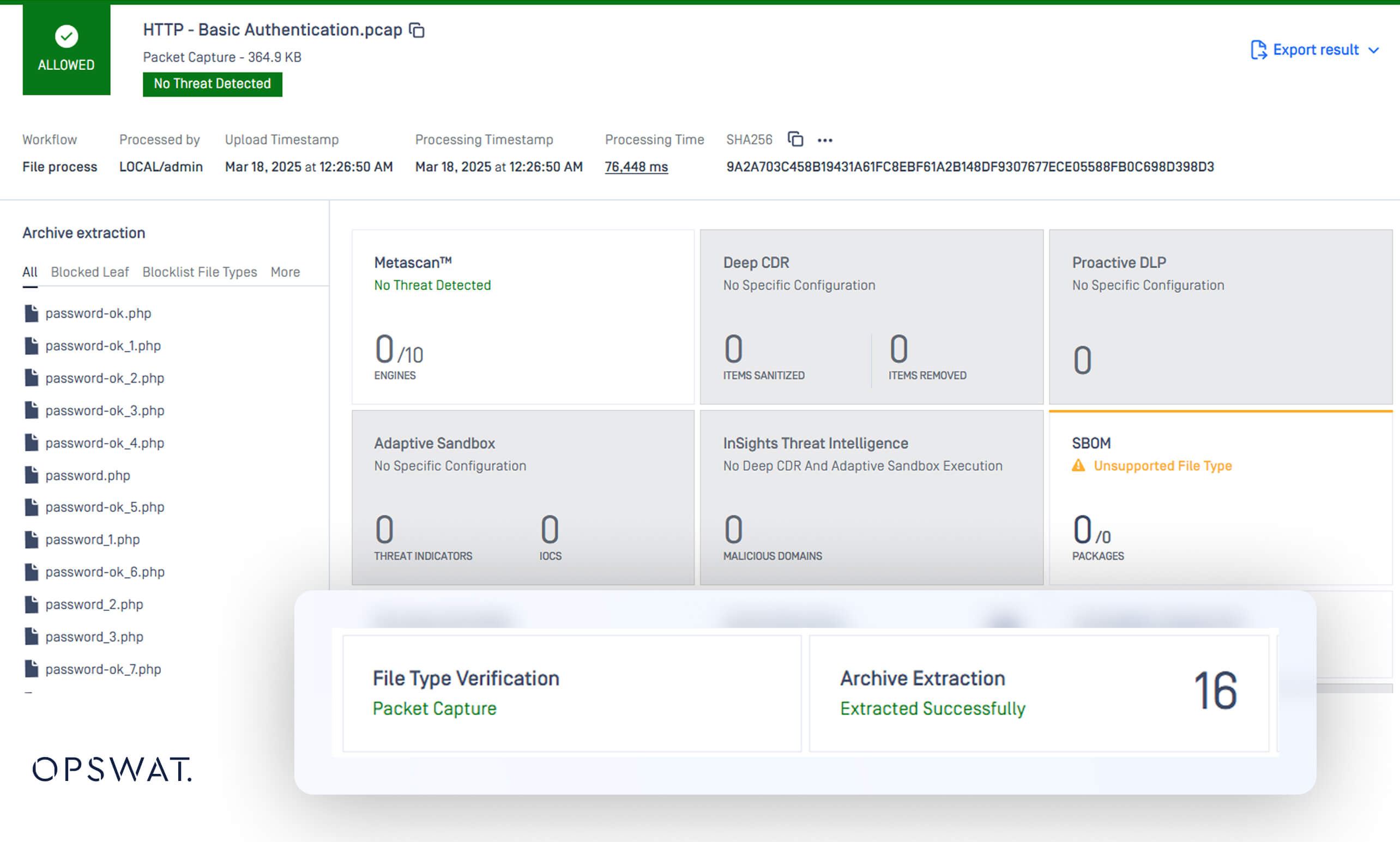
Extract and Inspect PCAP Files
Network packet captures (PCAP files) are a goldmine for forensic investigators, but they’re also a blind spot for many security solutions. Traditional tools often treat PCAPs as opaque containers, ignoring the HTTP, FTP, or IMAP traffic embedded within. This oversight allows attackers to exfiltrate data or deliver malware through seemingly benign network logs.
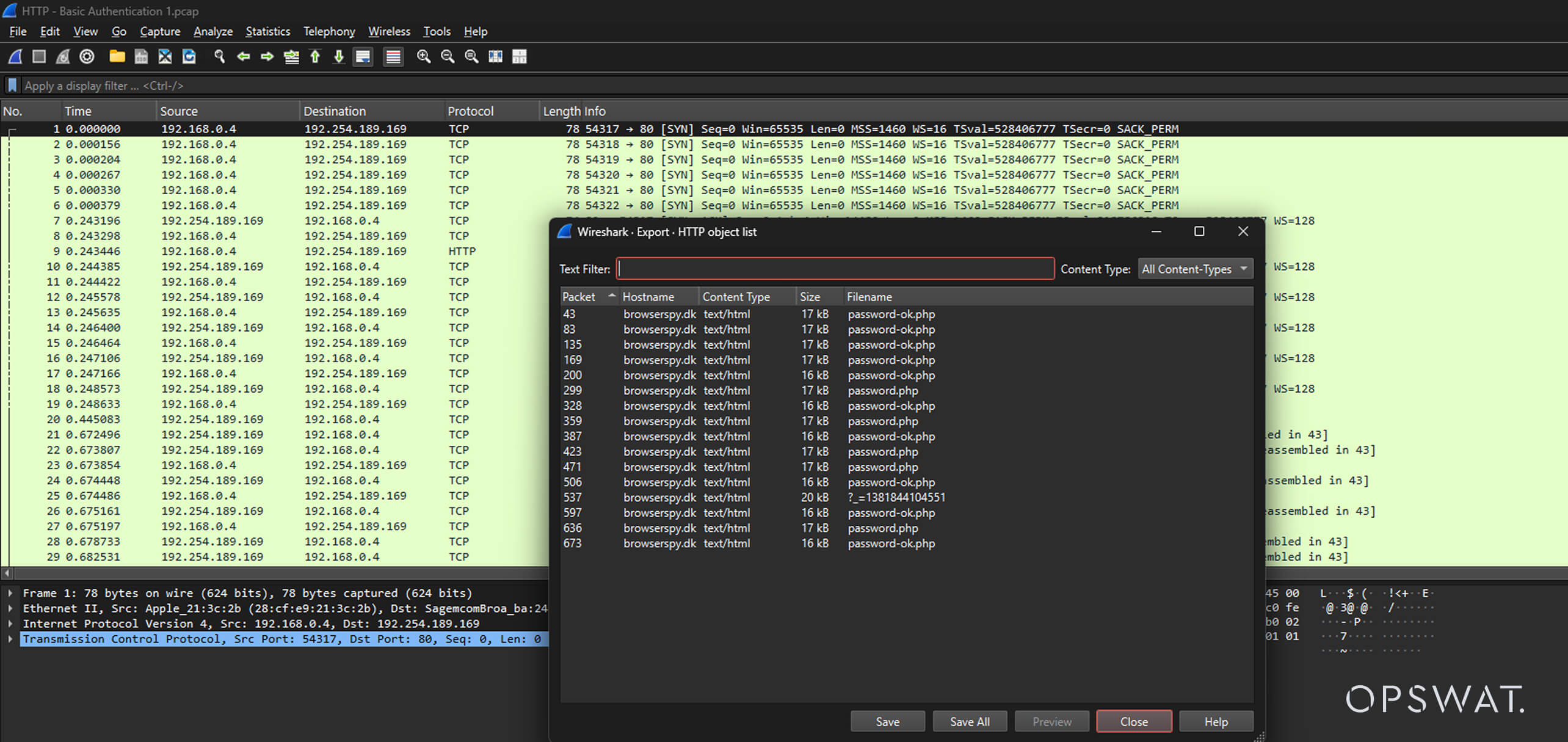
Archive Engine now extracts and inspects all packets within PCAP files, applying the same rigorous analysis as standalone files. By reconstructing network sessions and inspecting extracted payloads, security teams can detect:
- Malware downloads
- Data exfiltration attempts
- Command-and-control communications
Enable Flexible Configuration via Workflow Integration
Previously, several global configuration options were restricted at the module level. With this update, key configurations have been moved to workflows, enabling:
- Greater flexibility in defining security policies.
- Easier customization based on organizational needs.
- Improved efficiency in managing large-scale security deployments.
Upgrades to Meet Your Needs
The latest updates to Deep CDR, File Type Verification, and Archive Extraction engines give security teams direct control over how files, documents, and network data are analyzed, so decisions stay rooted in context, not guesswork. To learn more or see these features in action, contact OPSWAT today.

