The MetaDefender Access Zero-Trust Access Platform is continuously expanding its capabilities. In the most recent release, several important features were added to the already powerful Zero-Trust platform, including reporting of Known Exploited Vulnerabilities (KEV) as cataloged by CISA, the addition of a NERC-compliance dashboard, and automated patch management for third-party applications.
These new features fit neatly into the new MetaDefender Access modules that were rolled out at the start of 2023: The baseline Deep Compliance module and others such as Vulnerability Management, Patch Management, Advanced Endpoint Security, and Secure Access.
MetaDefender Access Features in Sync with Emerging Regulatory Environments
The new MetaDefender Access features are not coming in a vacuum. Regulations for compliance are becoming stronger and more prevalent across the board. Early last year, the White House issued a Memorandum for the Heads of Executive Departments and Agencies in the Federal Government, setting forth a Federal Zero Trust architecture strategy. In October of 2022, CISA – the American Cybersecurity and Infrastructure Security Agency – issued a Binding Operational Directive (BOD 23-01) for improving asset visibility and vulnerability detection on Federal networks.
The short of it is that, by April 3, 2023, all Federal agencies must comply with the need to perform automated asset discovery every 7 days and to initiate vulnerability enumeration across all discovered assets (including endpoints such as laptops) every 14 days. Specifically for critical infrastructure organizations, the Biden Administration is getting ready to unveil a national strategy that for the first time puts in place a set of comprehensive cybersecurity regulations for critical infrastructure.
Blog: Understanding Cybersecurity Compliance (Protect Your Business and Gain a Competitive Edge)
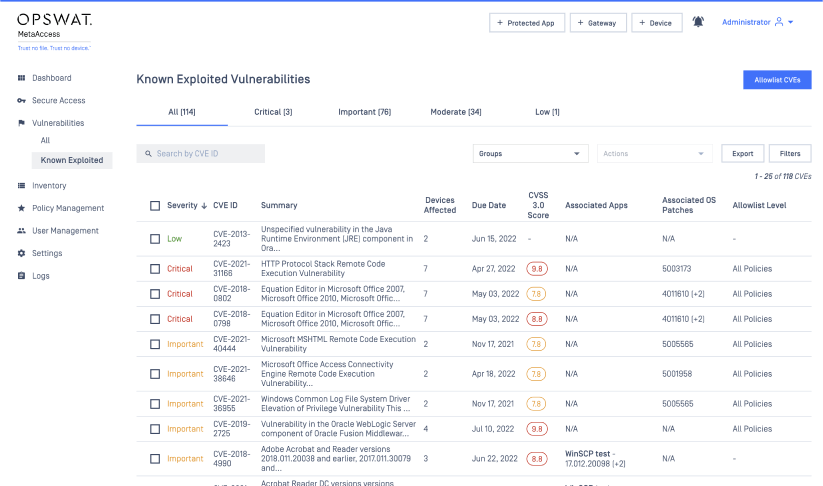
Detection and Remediation of CISA Known Exploited Vulnerabilities
The remediation of Known Exploited Vulnerabilities (KEV) as cataloged by CISA lets users easily view devices which have KEVs. From a compliance point of view, the system will detect if the endpoint has a KEV, and, in accordance with Admin policy, it will either be automatically remediated or flagged as critical. A warning will then be sent to the user, and their access to the network will be blocked if needed.
The platform will now show KEVs alongside CVEs (Common Vulnerabilities and Exposures) in the report, as shown below.
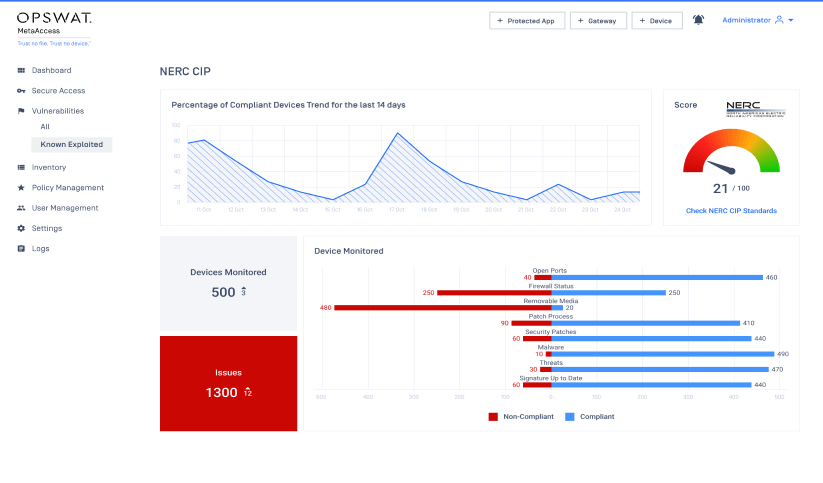
Ensuring You are Ready for the NERC CIP Compliance
With OPSWAT’s long-standing experience in providing cybersecurity solutions to critical infrastructure organizations, many of OPSWAT’s customers will find a NERC compliance dashboard to be a very helpful feature. The MetaDefender Access Platform will now clearly show devices that are either compliant or non-compliant with NERC-regulated compliance categories such as firewall status, port control, security patch gaps, prevention of malicious code, signature updates, and enforcement of authentication of interactive users.
Automatic Patching of 3rd-Party Vulnerabilities
Moving to the Patch Management component of the platform, MetaDefender Access now provides automated patch management for third-party applications. The admin can either let users perform updates manually with a single click or enable automatic update on the endpoint.
The Big Picture
With the US government taking the lead, regulations requiring compliance in a variety of areas, including vulnerability, patch management, and zero-trust security, are rapidly becoming the industry standard. OPSWAT’s MetaDefender Access Zero-Trust Access Platform is well-placed to address the cyber challenges in the market working with critical infrastructure organizations and others, in this new reality.
To learn more about MetaDefender Access, check out our recently released MetaDefender Access datasheet.