In This Release
- Improvements for C/C++ libraries
- Utilize PE information to detect DLL/EXE libraries
- Add more signatures for C/C++ libraries
- Support processing CycloneDX file format
In our latest enhancements for SBOM (Software Bill of Materials) technology version 4.0.0, we extend our database coverage for binary components such as DLL and EXE files, improve binary identification through PE (Portable Executable) metadata, and enable validation and enrichment for CycloneDX SBOM reports.
The Binary Blind Spot
Traditional SBOM solutions primarily rely on package managers and manifest files (e.g., requirements.txt, package.json) to identify third-party components. While effective for many modern applications, this approach leaves significant blind spots, particularly in scenarios such as:
- Projects without consistent package manager usage: C/C++ projects that incorporate DLL libraries that are not tracked by package managers can remain invisible to SBOM generation tools.
- Software installers containing embedded third-party binaries: Installers often contain third-party binary dependencies without explicit metadata, making them difficult to track.
- Binary format libraries in artifact repositories: Artifact repositories like JFrog Artifactory, Nexus Repository, or Apache Archiva store libraries in binary formats (whl, egg, zip) rather than source code. These binary packages also lack declarations, which also limits traditional SBOM visibility.
These gaps create security risks – binary dependencies remain invisible, installer packages go unexamined, and vulnerabilities in undeclared dependencies cannot be tracked.
Closing the SBOM Binary Security Gap
To address these critical blind spots, OPSWAT SBOM 4.0.0 delivers enhanced capabilities through multiple complementary approaches:
Expanded Database Coverage for Binary Components
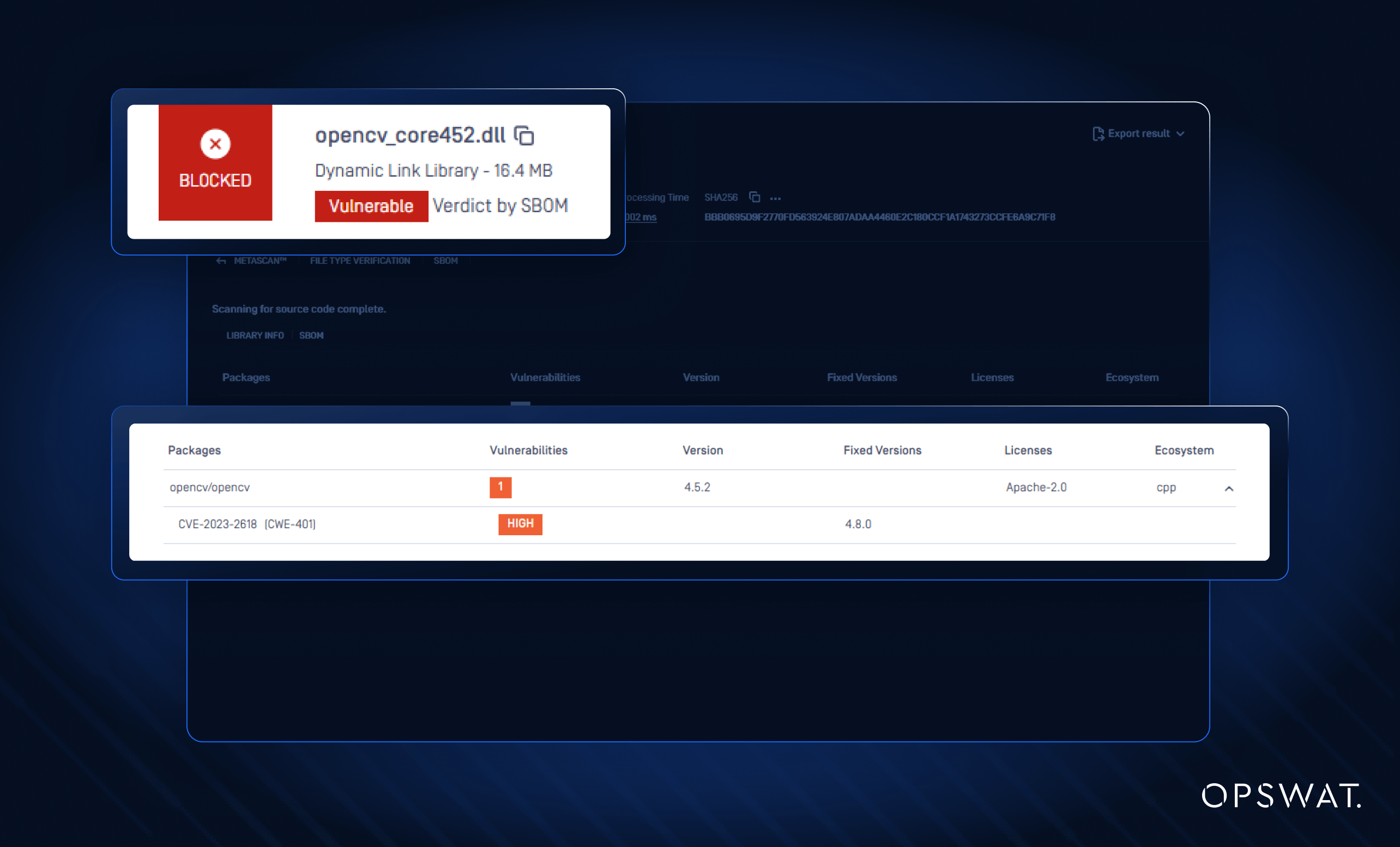
We've significantly expanded our signature database for C, C++, and C# binaries (DLLs, EXEs). Software development teams can identify embedded third-party libraries even when package manager metadata is unavailable.
With this update, OPSWAT SBOM ensures comprehensive component tracking across source code, compiled binaries, and software installers.
Precise Library Identification with Metadata Analysis
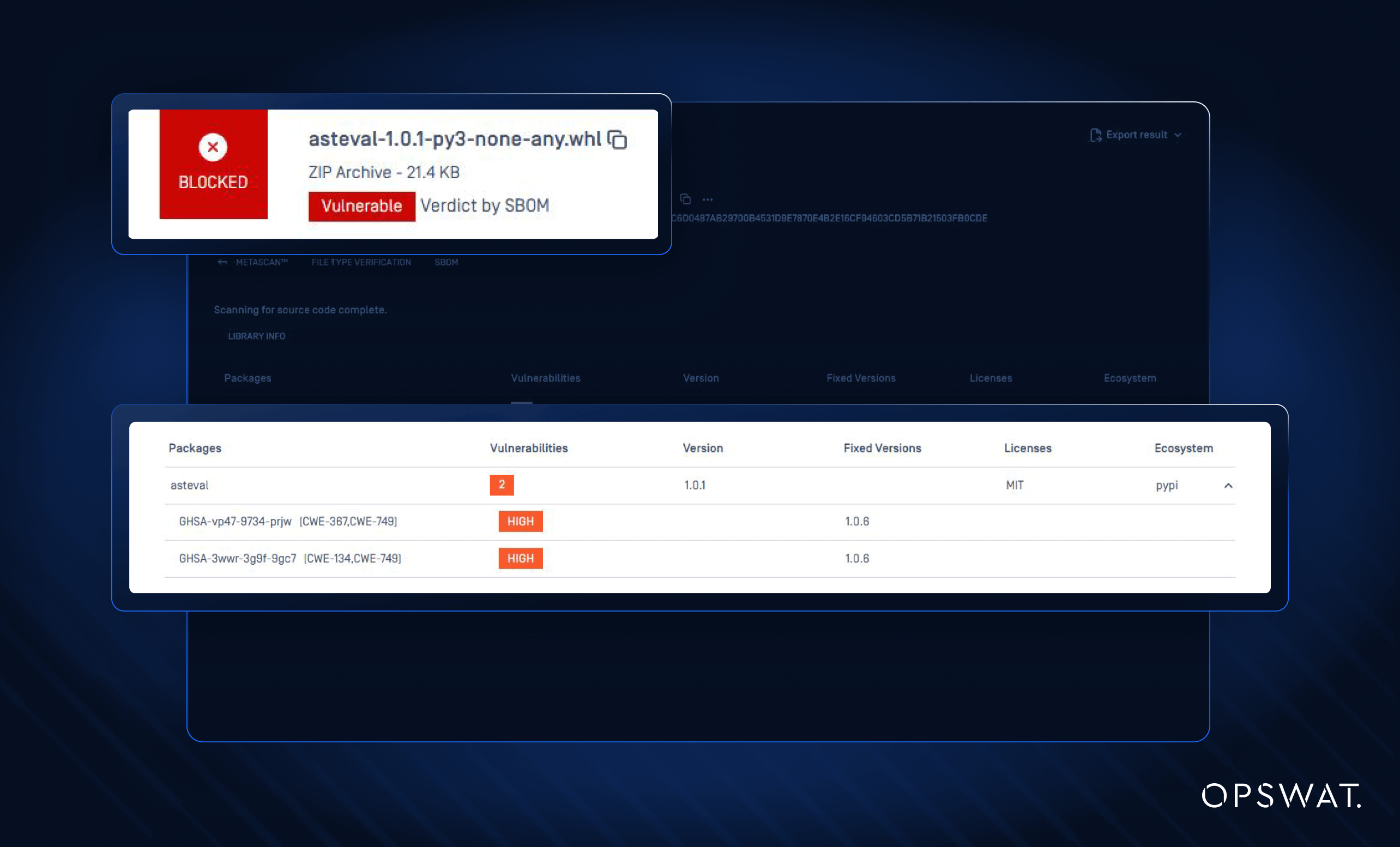
Our new release leverages PE (Portable Executable) metadata analysis to identify binary files and match them to known vulnerabilities and licensing databases. This automated approach replaces what was previously a manual, time-consuming, and error-prone process.
How it Works:
- OPSWAT SBOM detects third-party libraries in binary form (DLLs, EXEs) by utilizing their signatures and PE (portable executable) metadata.
- Extracted binary information is mapped to known libraries and versions
- These findings are then cross-referenced against our vulnerability and license databases.
Benefits:
- Identify third-party components, including manually managed C/C++ libraries and installer packages
- Improve accuracy in identifying binary components using metadata analysis
- Mitigate security risks by detecting dependencies even without package manager declarations
- Enable comprehensive vulnerability management and security assessments
Precise Library Identification with Metadata Analysis
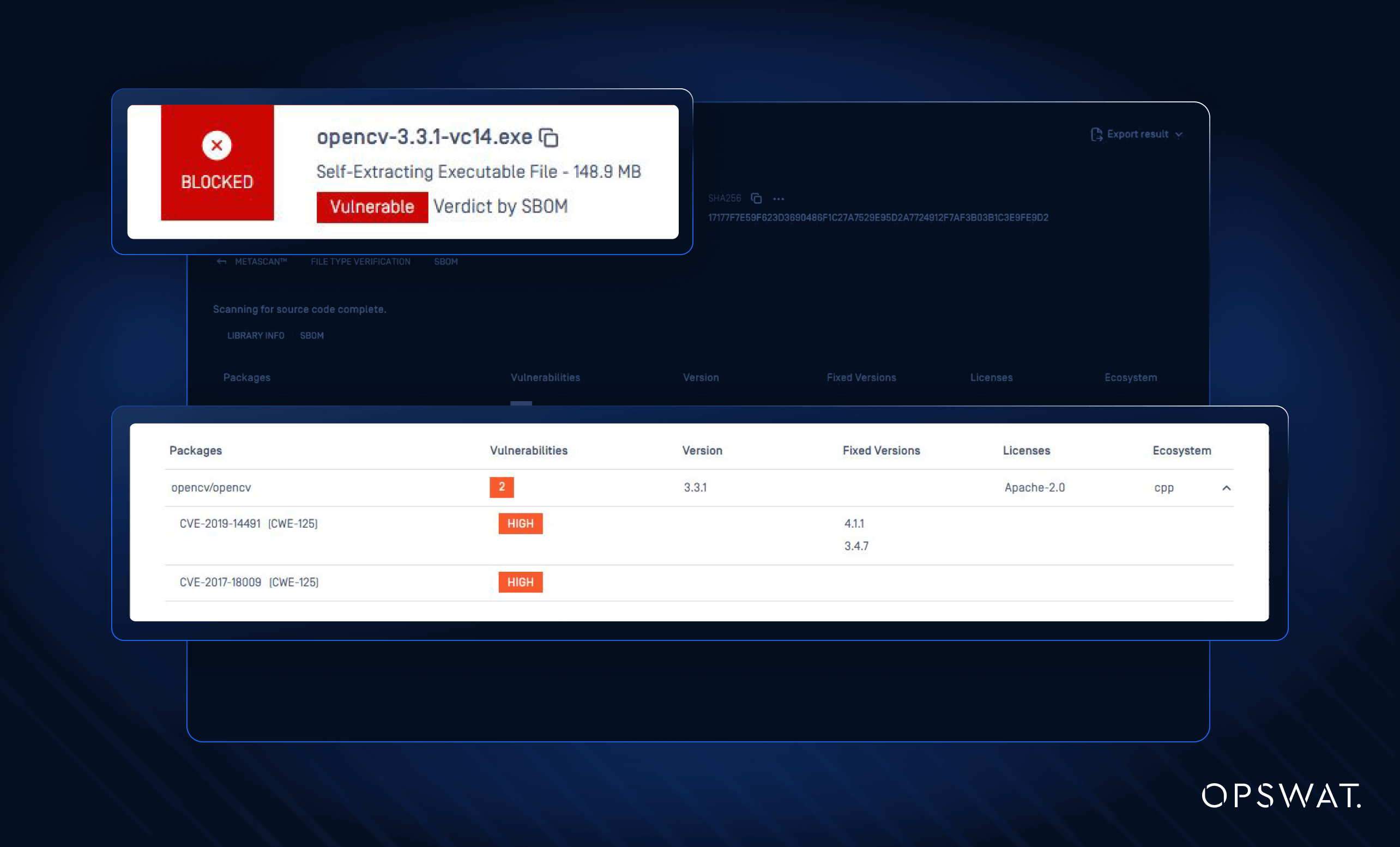
Integrating SBOM with Artifact Repositories
Beyond scanning binary libraries directly, OPSWAT SBOM and MetaDefender Software Supply Chain supports native integration with artifact repositories such as JFrog Artifactory to scan the original packages and retrieve their metadata. Learn more about JFrog Artifactory integration.
This cross-referencing enables accurate identification of embedded third-party libraries, and ensures teams will not miss critical security information in the binary components of their projects.
CycloneDX SBOM Report Validation and Enrichment
Another update in this release focuses on the accuracy and completeness of SBOM reports – particularly those in the CycloneDX format.
CycloneDX is a widely used SBOM format for security and vulnerability tracking. However, some of these reports often lack insights such as licensing data or undeclared dependencies.
At OPSWAT, we believe in the philosophy of multi-layered defense. Just as layered security strategies improve malware detection, multi-layered SBOM validation enhances software supply chain security. This enhancement validates and enriches CycloneDX SBOM reports to create more complete component inventories.
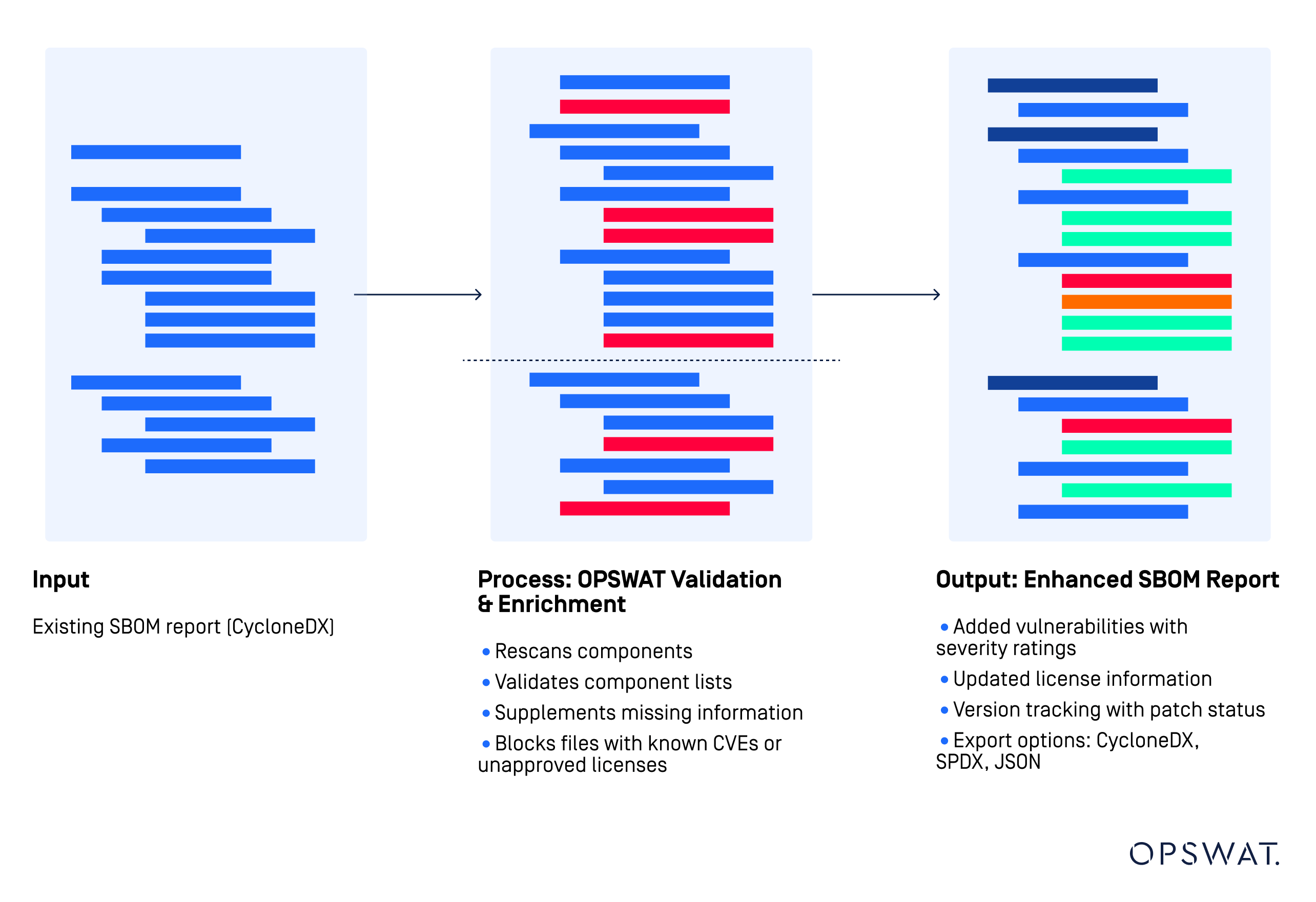
How it Works:
Import Existing SBOM
Users provide an SBOM report in CycloneDX format as a baseline for analysis and validation.
Validation and Enrichment
OPSWAT rescans the SBOM, validating the listed components against our database, and supplement missing details, including:
- Vulnerability insights (CVE detection and severity ratings)
- Licensing data
- Version tracking (outdated versions and fixed patches)
Additionally, files with known CVEs or unapproved licenses will be flagged or blocked based on pre-configured policies.
Generate and Export Enhanced SBOM
The updated SBOM includes additional security insights. Export enriched findings in JSON, CycloneDX, or SPDX SBOM format.
Why Binary Detection Matters
Comprehensive Vulnerability Management
When new CVEs are announced, security teams can immediately assess whether they are affected, even for components in binary form. This eliminates security blind spots in vulnerability response workflows.
Compliance and Regulatory Readiness
Organizations facing increasing regulatory requirements or customer demands for SBOMs can ensure all components are accounted for—not just those managed through package managers.
Security Assessments for Installer Packages
Software distribution packages often contain numerous third-party components. Binary detection extends visibility into installers and ensures that all dependencies reaching customers are inventoried and security-checked.
Legacy Codebase Support
Older applications lacking modern dependency management can now be included in software supply chain security programs, without requiring manual tracking or extensive rework.
About OPSWAT SBOM
OPSWAT SBOM enables software transparency by providing an accurate inventory of software components in their software application stacks. With OPSWAT SBOM, developers can identify known vulnerabilities, validate licenses, and generate component inventory for OSS (open-source software), third-party dependencies, and container images. Software development teams can stay compliant and keep ahead of attackers without impacting development velocity.
Learn more about how SBOM helps secure your applications at https://www.opswat.com/technologies/sbom.

