An SBOM (Software Bill of Materials) serves as a foundational element in ensuring the integrity of software components—with origins dating back to the earliest software development efforts for documenting open-source dependencies in the 1990s. SBOMs help organizations track the components in their software application stack and maintain compliance with industry regulations. As software ecosystems grow increasingly complex, adopting standardized SBOM formats becomes essential for improving security and interoperability.
Defining SBOM
A Software Bill of Materials (SBOM) is a comprehensive inventory of all components within a software application, including proprietary, open-source, and third-party software elements. It provides detailed metadata such as software name, version, supplier, license information, and cryptographic hashes for verification.
By offering full visibility into software dependencies, SBOMs enhance supply chain transparency, enable vulnerability detection, and support regulatory compliance. They help organizations mitigate security risks, streamline audits, and improve incident response by identifying and addressing potential threats within their software ecosystem.
What is an SBOM Standard?
SBOM (software bill of materials) standards ensure consistency and interoperability across different industries and organizations by providing a unified framework for documenting software components. These standards help businesses streamline vulnerability management, comply with evolving regulatory requirements, and facilitate seamless collaboration between software producers, vendors, and end-users.
By adopting standardized SBOM formats, organizations can improve software supply chain security, reduce the risk of software tampering, and enhance overall software transparency.
What is an SBOM Format?
SBOM formats are standardized, machine-readable schemas used to structure and share the data contained in an SBOM. These formats define how software component details are represented and exchanged between systems.
The most widely used SBOM formats include SPDX and CycloneDX, both of which support automation, interoperability, and traceability across the software lifecycle. These formats enable improved vulnerability detection, regulatory compliance, and supply chain risk management by ensuring consistent documentation of software components.
Key Components of an SBOM
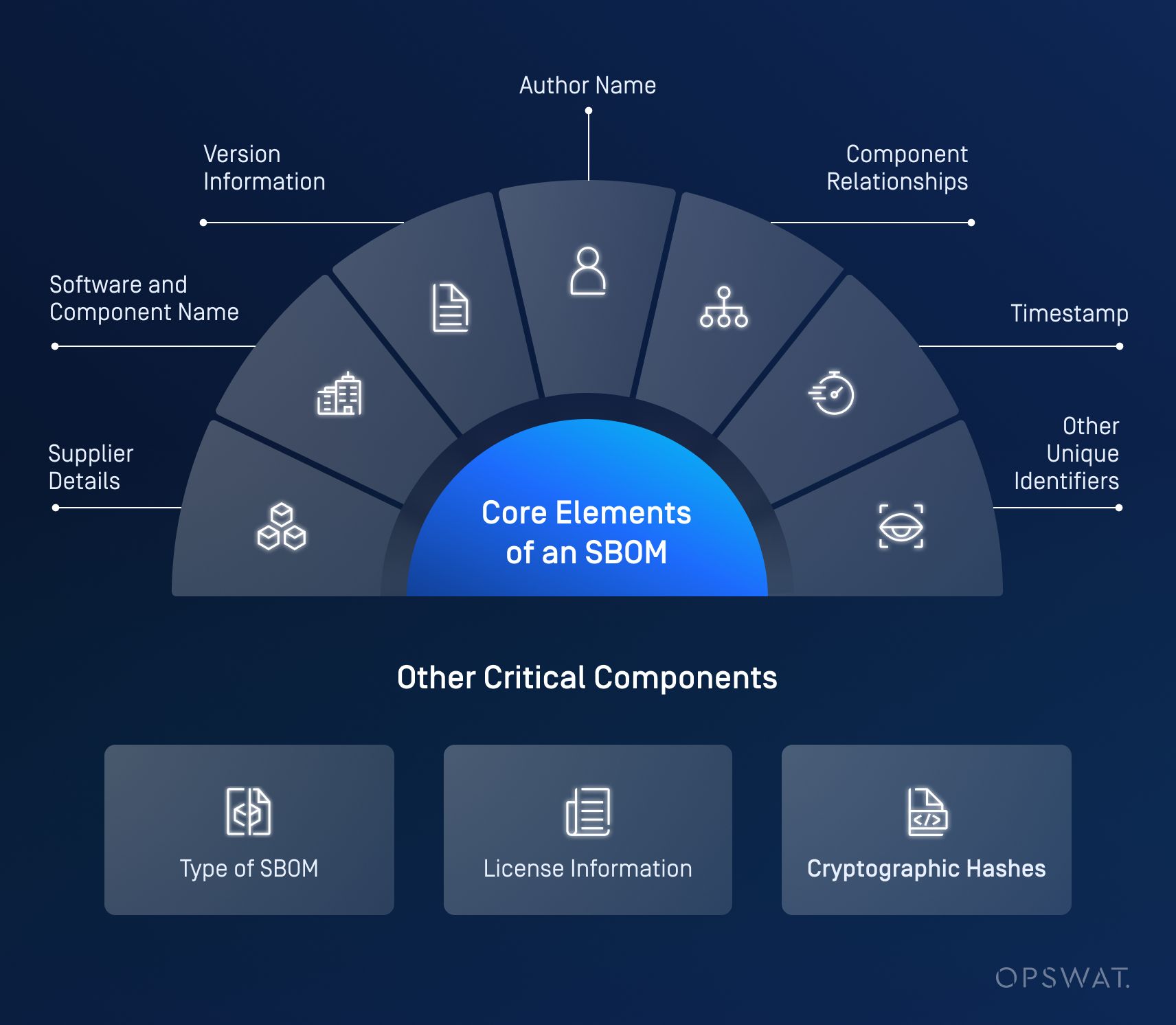
To be effective, an SBOM must contain key elements that provide complete transparency into a software package. The US NTIA (National Telecommunications and Information Administration) defines seven minimum components for an SBOM:
- Supplier Details: Identifies the entity responsible for the software.
- Software and Component Name: Identifies the software component.
- Version Information: Specifies the release details of the component.
- Author Name: The person or organization (but not the tool) that created the SBOM report.
- Component Relationships: Describes dependencies and interactions among software elements.
- Timestamp: Part of the SBOM meta-information that specifies the date and time the report was produced.
- Other Unique Identifiers: Provides additional information to define the software components
Other essential components include:
- Type of SBOM: Provides context on how and why the SBOM report is needed.
- License Information: Defines the software’s usage rights.
- Cryptographic Hashes: Ensures integrity and authenticity of components.
SPDX SBOM Format
The Software Package Data Exchange (SPDX) format, developed by the Linux Foundation, is a widely used SBOM standard designed to facilitate open-source license compliance and software component tracking. It provides a structured way to document software components and their associated metadata, making it an essential tool for software transparency and security.
Additionally, SPDX is the format that has received the ISO (International Organization for Standardization) certification status, making it the format that meets standardization and quality assurance requirements.
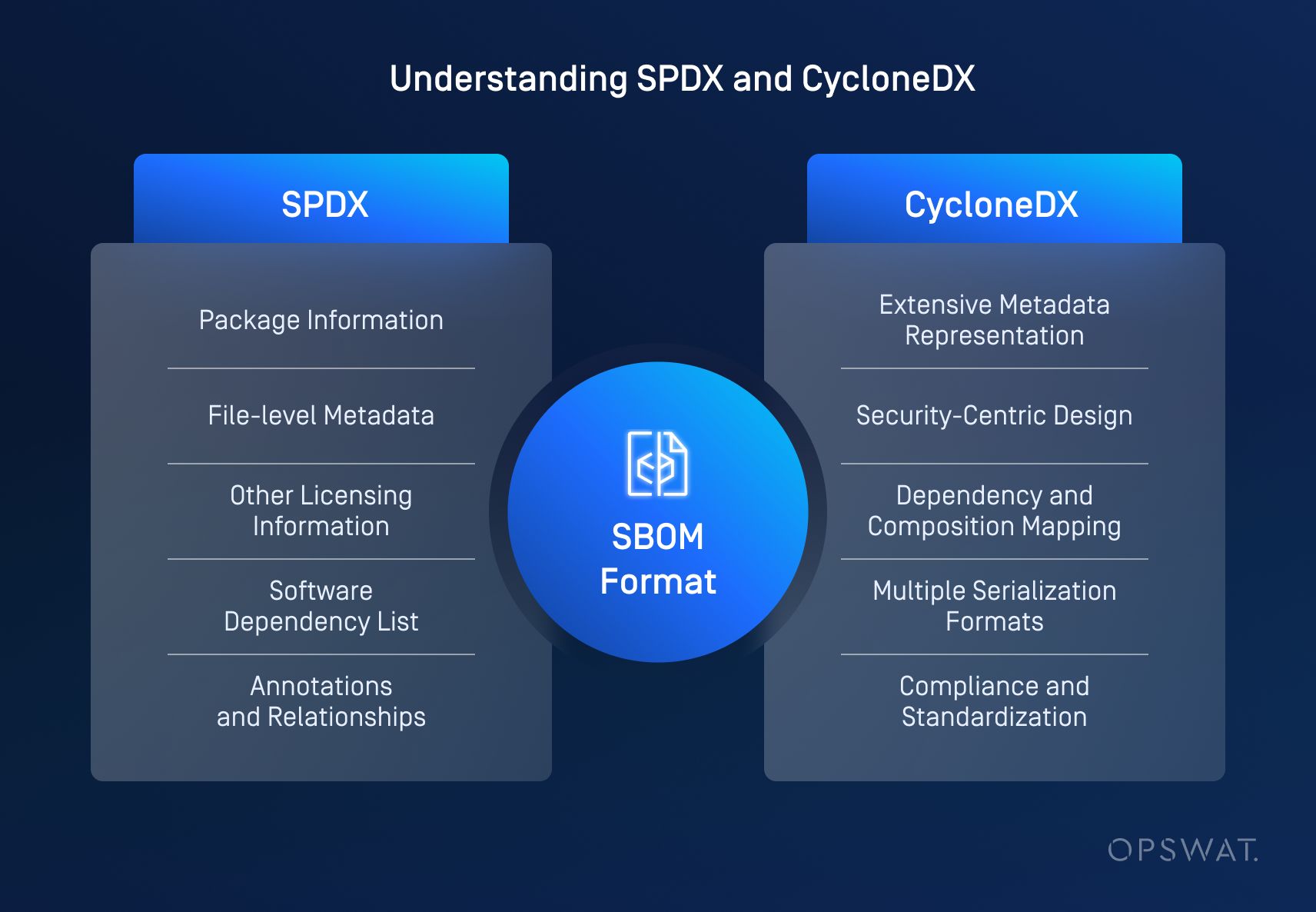
SPDX format documents contain several key elements:
Package Information
Describes the package, which can consist of one or more files – including source code, binaries, documents, etc. Other types of information include details about the original author, source, download URL, checksum, and overview licensing.
File-level Metadata
Details on the specific files, such as license, checksum, file contributors, etc.
Other Licensing Information
Ensures intellectual property management by specifying software licenses.
Software Dependency List
Documents the hierarchy of software dependencies.
Annotations and Relationships
Provides additional metadata and establishes relationships between software artifacts.
SPDX format supports multiple formats, allowing flexibility based on use case and tool compatibility:
- Tag/Value (.spdx): A simple text-based format
- JSON (.spdx.json): A lightweight, machine-readable format
- YAML (.spdx.yml): A human-friendly data serialization format
- RDF/XML (.spdx.rdf): A structured format for semantic data representation
- Spreadsheet (.xls): A tabular format useful for manual analysis
SPDX is widely adopted by major technology companies, regulatory bodies, and open-source software communities. It is commonly used for:
- Open-source software license management: Helps organizations track and comply with open-source licensing requirements.
- Security auditing: Provides insights into software components to detect vulnerabilities and manage risks.
- Regulatory compliance: Ensures adherence to industry standards and legal requirements related to software transparency.
- Software provenance tracking: Establishes a clear lineage of software components for improved accountability.
By leveraging the SPDX format, organizations can enhance supply chain security, streamline compliance efforts, and gain greater visibility into their software ecosystems.
CycloneDX SBOM Format
Developed by the OWASP Foundation, CycloneDX format provides a full-stack BOM (Bill of Materials), including SBOM, and is designed with a strong emphasis on security, vulnerability management, and comprehensive software transparency. It provides a prescriptive object model that efficiently describes complex relationships among software components, services, and dependencies.
Key features of CycloneDX format include:
Extensive Metadata Representation
Captures supplier details, licensing information, authors, tools, manufacturing processes, and so forth.
Security-Centric Design
Enables precise vulnerability identification, exploitability analysis, and support for VEX use cases.
Dependency and Composition Mapping
Represents both direct and transitive relationships between software components and services.
Multiple Serialization Formats
Supports JSON, XML, and Protocol Buffers (protobuf), ensuring broad compatibility with security tools.
Compliance and Standardization
Integrates with security standards such as OWASP ASVS, MASVS, SCVS, and SAMM, providing a machine-readable framework for compliance tracking.
With its robust architecture and security-driven approach, CycloneDX is widely adopted in cybersecurity-focused applications for vulnerability management and security monitoring. This makes CycloneDX format an essential tool for software supply chain risk management.
CycloneDX vs SPDX Formats
| Feature | SPDX | CycloneDX |
| Focus | Open-source license compliance and intellectual property | Application security and supply chain analysis |
| Features | Comprehensive metadata for software components | Lightweight, user-friendly, with a focus on essential component data and security assessment |
| Use Cases | Open-source licensing (originally), compliance audits, and software provenance | Vulnerability management, software supply chain analysis, and security monitoring |
| Adoption | Major tech companies and compliance teams | Security tool providers and cybersecurity firms, DevSecOps teams |
Importance of Software Bills of Materials
SBOMs play a crucial role in software transparency and accountability. They provide insights into the software supply chain, enabling organizations to verify the integrity of software components. This level of transparency reduces the risk of software tampering and unauthorized modifications, ultimately strengthening the trust between software producers, vendors, and end-users.
Additionally, SBOMs support incident response and software lifecycle management. When vulnerabilities are discovered, having a detailed SBOM allows security teams to quickly assess the impact and implement patches effectively. This proactive approach minimizes downtime and ensures that critical systems remain secure against emerging threats.
SBOMs in Security and Compliance
An SBOM is a critical tool for ensuring software security and regulatory compliance. By providing a comprehensive inventory of all software components, SBOMs allow organizations to track and manage vulnerabilities more effectively. They enable security teams to proactively identify and mitigate risks, ensuring that all third-party and open-source dependencies are up to date and free from known exploits. This visibility is essential as cyberthreats become more sophisticated and pervasive.
Regulatory frameworks such as NIST, ISO, Executive Order 14028 and other regional technical guides mandate stricter software transparency and security measures, making SBOMs an essential requirement for compliance. Organizations that leverage SBOMs can more easily demonstrate adherence to these standards, avoiding potential legal and financial repercussions. By maintaining accurate and up-to-date SBOMs, businesses can streamline audits, reduce compliance overhead, and ensure that software meets industry regulations.
Comparing SBOM Formats
Strengths and Weaknesses
Each SBOM format serves different purposes, making it essential to choose the right one based on specific needs.
| Feature | Strengths | Weaknesses |
| SPDX | Comprehensive and widely used. Strong focus on licensing and compliance. | Can be complex for smaller projects |
| CycloneDX | Optimized for security and vulnerability management. | Less emphasis on licensing details |
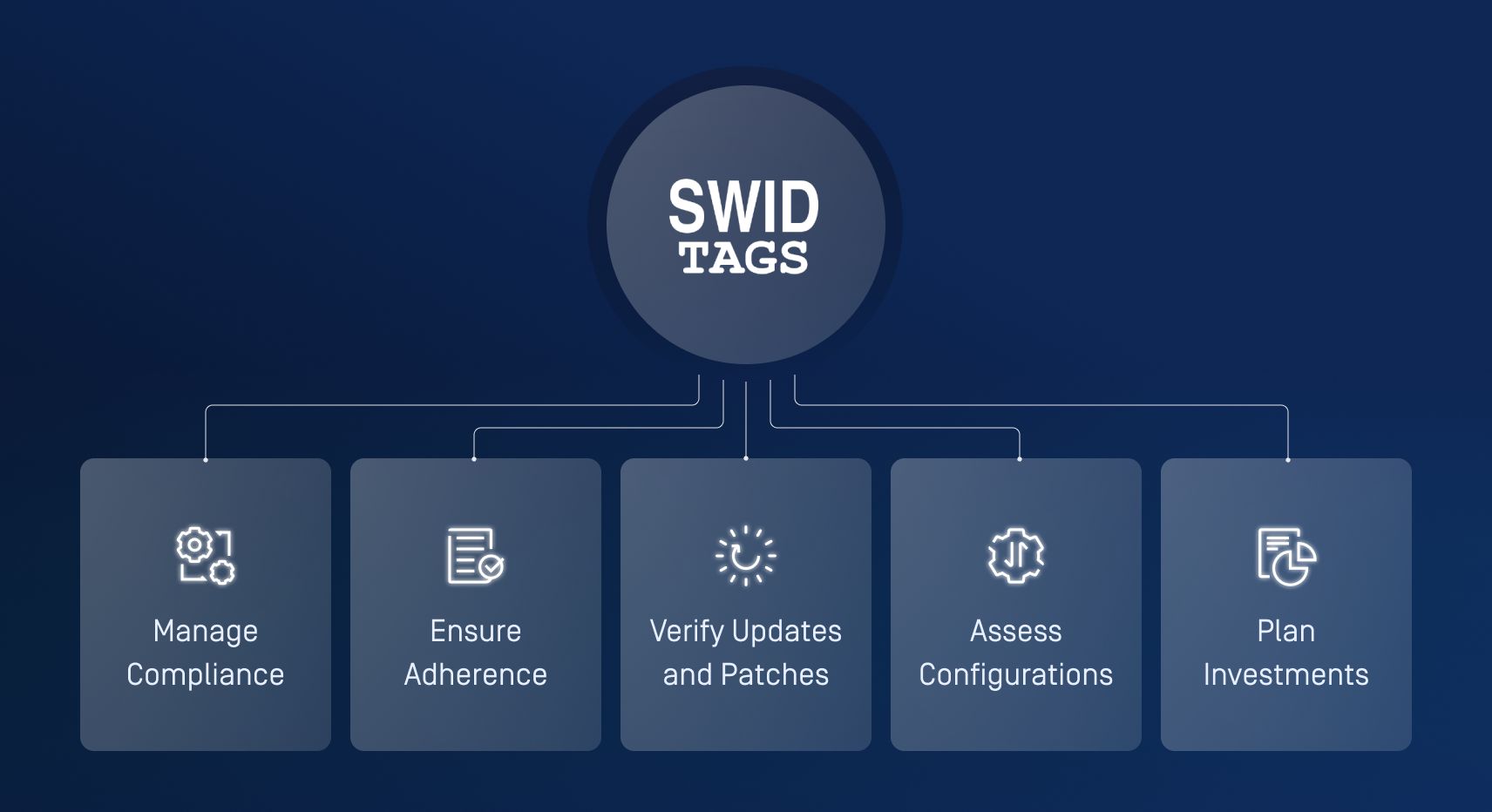
| SWID Tags | Integrated into software | Limited standardization across industries |
Conclusion
Understanding and implementing SBOMs is crucial for modern software security. By leveraging formats such as SPDX, CycloneDX, and SWID tags, organizations can enhance their software supply chain transparency and mitigate security risks.
Next Steps
Evaluate your organization's current software supply chain practices and explore SBOM formats that align with your security and compliance needs.
To learn more about securing your software supply chain with robust SBOM solutions, visit OPSWAT’s Software Supply Chain Security solution.