Picture a routine remote maintenance session at a gas compression station. A contractor logs in via VPN to update the firmware and reconfigure PID loop parameters on a compressor control panel. It’s a pretty common task that ensures smooth running of the station. He has done it at least a dozen times before.
But this time, something’s off.
The contractor doesn't know it, but his laptop is infected with malware. Once connected, the flat network architecture and lack of protocol-level protections open the path for attackers to pivot across the OT environment. Within minutes, they disable safety alarms and access core PLCs that control gas flow. As the threat cascades, the station is forced to go offline for 36 hours, pausing operations, triggering emergency systems and response teams, and incurring huge financial losses.
This is a hypothetical situation, but it reflects the very real risk of relying on traditional VPNs for remote access to critical OT and cyber-physical systems.
VPNs Were Built for IT, Not OT
VPNs were designed for IT environments to allow trusted users to connect to corporate resources over the internet. They work by creating an encrypted tunnel between the user and the internal network. While this sounds secure, it assumes that the user is trustworthy and that once inside the network, their access should be unrestricted or, at most, controlled.
This trust model is deeply flawed in the context of OT. Unlike IT systems, OT environments are extremely sensitive to disruption, often include legacy equipment with limited security capabilities, and typically operate 24/7 to control physical processes. Introducing broad, unmanaged access to these networks, especially from third parties like contractors or OEM vendors, can create serious vulnerabilities.
When VPNs become a liability in OT
Here are just a few reasons VPNs fall short for OT environments:
- Overprivileged Access
VPNs often provide network-level access, which means once a user is connected, they can move laterally within the OT network. This violates the principle of least privilege. - Persistent Connections
VPN tunnels can remain open for long periods, creating a constant attack surface. If an attacker compromises the endpoint or credentials, they can maintain undetected access. - Lack of Session Control
VPNs do not offer granular control over user actions and lack monitoring capabilities once users are inside the tunnel. There’s no protocol filtering, no command inspection, no session recording, and no alerts. If a malicious actor or negligent technician makes a change, there’s often no way to know until the damage is done. There's no visibility into user’s activities within the OT environment, nor is there native support for session recording or audit trails. - Insecure Endpoints
VPNs extend the network perimeter to the remote device, which may not be secure. A compromised contractor laptop becomes an entry point into critical systems. - No Native Integration with OT Protocols
Traditional VPNs don’t understand or manage OT-specific protocols. This limits their ability to enforce protocol-level filtering or command restrictions. Additionally, VPNs do nothing to protect or isolate inherently insecure industrial protocols like Modbus, DNP3, or BACnet. These protocols lack built-in encryption or authentication and can easily be hijacked once exposed through a VPN tunnel. - High Operational Overhead
VPNs and jump servers are complex to manage, challenging to audit, and often expensive to scale, especially when there are multiple contractors and sites involved.
A Safer, Smarter Alternative: MetaDefender OT Access
Enter MetaDefender OT Access—a secure, policy-driven remote access solution built specifically for industrial environments. Unlike traditional VPNs, it doesn’t trust endpoints by default. Instead, it enforces strict access rules, session control, and protocol inspection tailored for OT.
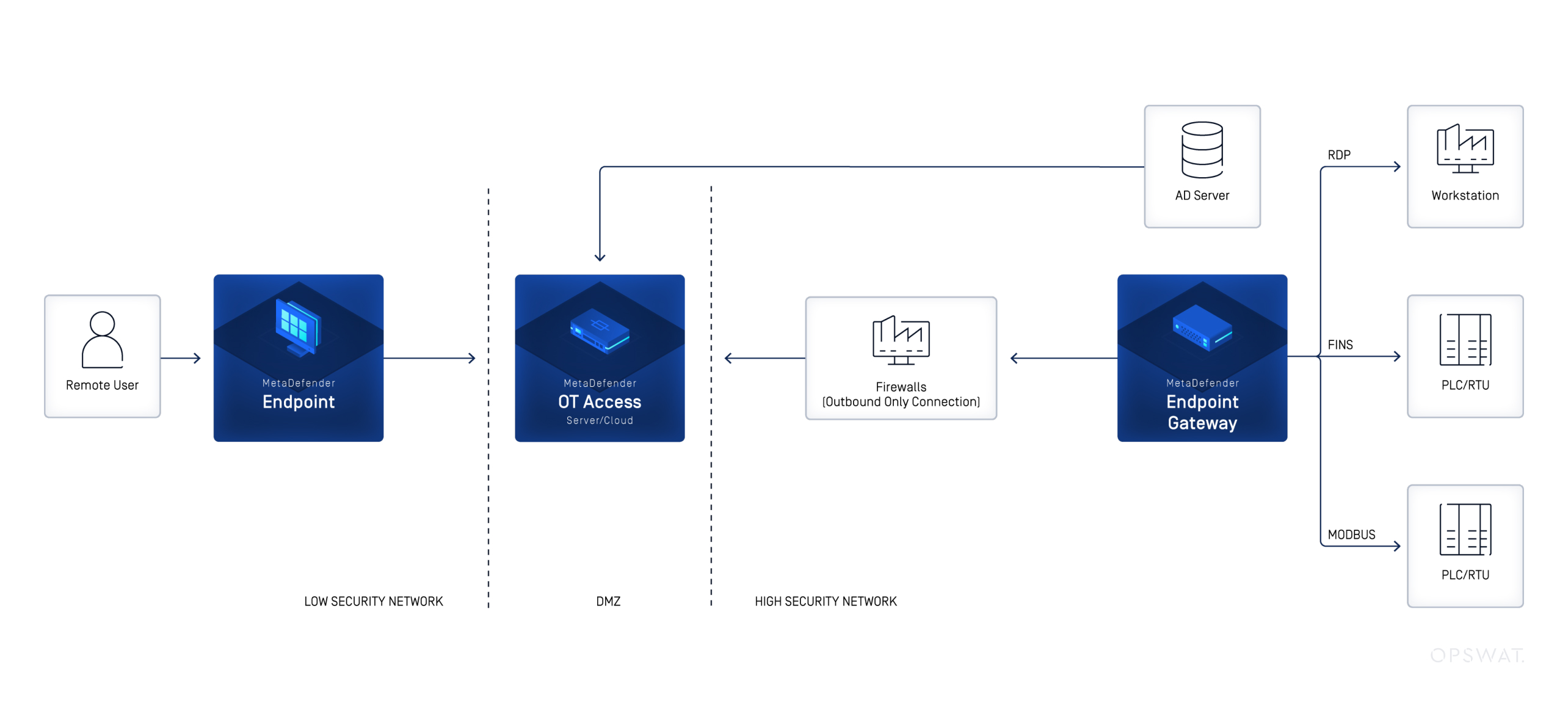
Key capabilities of MetaDefender OT Access include:
Granular RBAC (Role-Based Access Control)
Only authorized users can access specific assets, protocols, or sessions. No more open tunnels or unnecessary privileges.
Interactive Session Approval
Every access session can be granted by approval workflows, ensuring human oversight before granting access.
Full Session Recording and Auditing
MetaDefender OT Access provides a complete audit trail of remote sessions, which is critical for compliance and forensic investigations.
Protocol-Level Controls
Unlike VPNs, MetaDefender OT Access understands OT protocols and allows deep packet inspection, command filtering, and enforcement of communication boundaries.
No Direct Network Exposure
End users never directly connect to the OT network. Instead, sessions are brokered through a secure jump point, drastically reducing the attack surface.
VPNs Open the Door. MetaDefender OT Access Keeps It Guarded.
Industrial organizations can no longer afford the risks posed by VPNs in their OT environments. The attack surface is expanding, and adversaries are exploiting the weakest link-often through remote access. Regulatory frameworks such as NERC CIP, IEC 62443, and NIST 800-82 are already emphasizing stricter controls over remote access pathways.
MetaDefender OT Access offers a modern alternative, aligning with zero-trust principles and the realities of industrial networks. By replacing VPNs with a secure, observable, and policy-driven remote access solution, OT environments can stay resilient without sacrificing operational efficiency.

