With the release of MetaDefender Aether 2.3.0, OPSWAT delivers key advancements in AI-driven malware analysis, reverse engineering workflows, and behavior-based threat detection to meet these demands head-on.
This release marks a strategic leap forward — combining machine-assisted reverse engineering, expanded malware family support, and cloud and identity integrations — to equip organizations with the intelligence required to combat today’s most evasive threats.
Accelerated Reverse Engineering with AI-Powered Decompiler
MetaDefender Aether now introduces an OpenAI-powered decompiler, embedded directly into the disassembly interface. With the click of a new “Automatic RE” button, analysts can instantly generate:
- Decompiled code with inferred function names
- Contextual comments for improved code understanding
- A split-view layout for quick toggling between Disassembled and Decompiled views
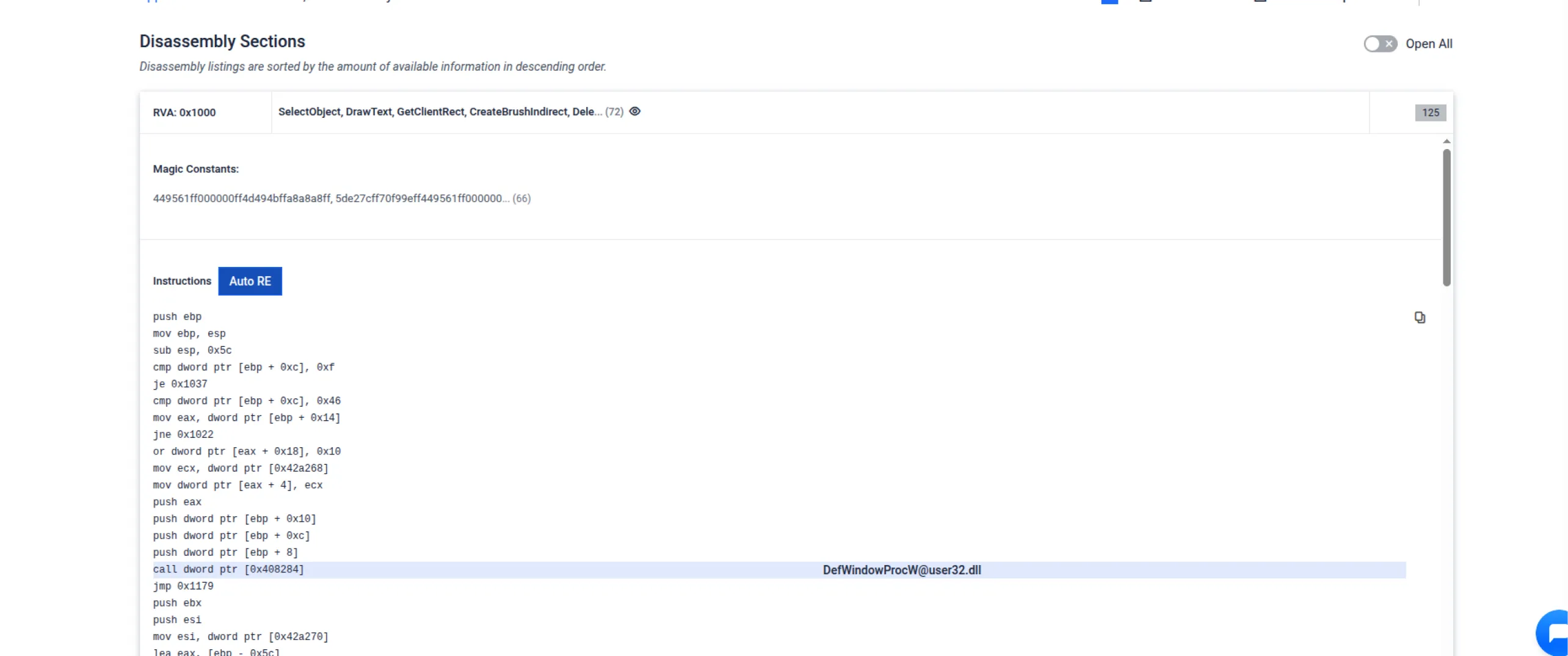
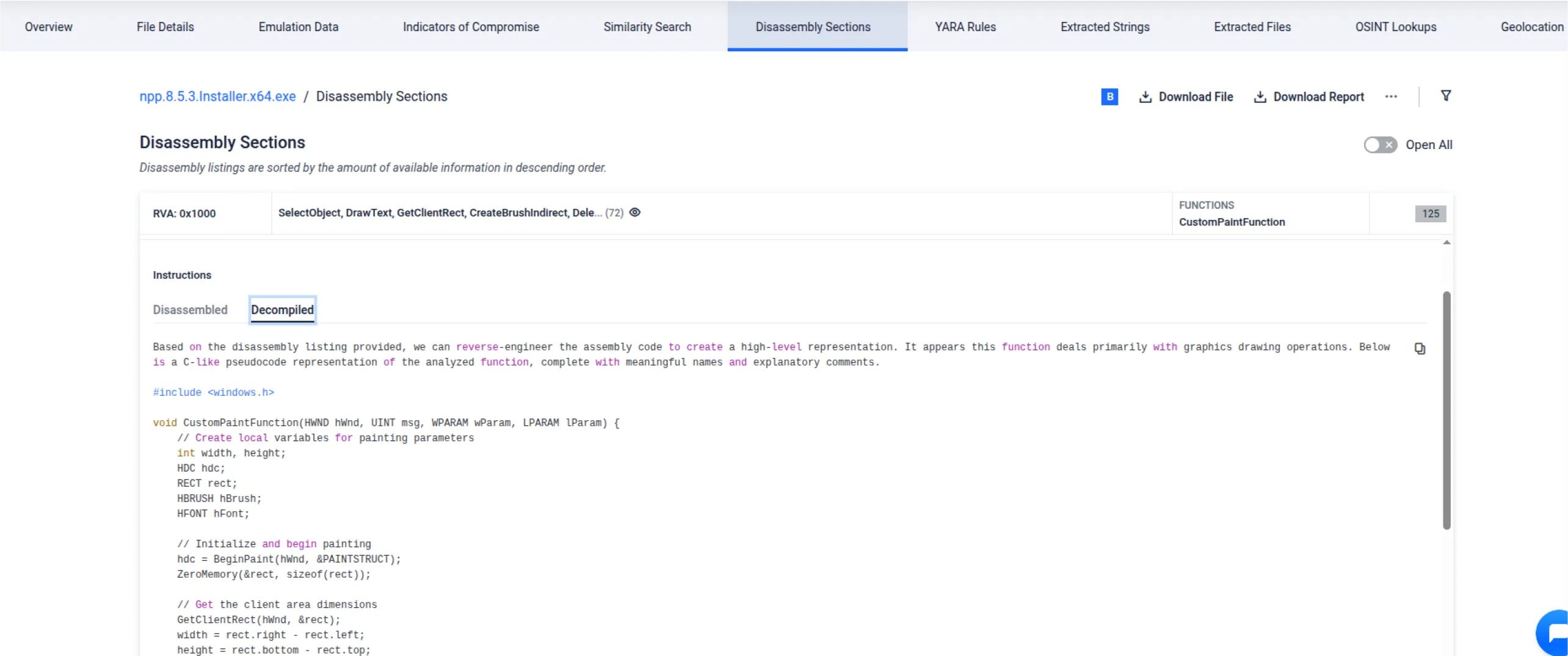
This enhancement streamlines malware reverse engineering and enables faster, more informed triage of unknown binaries — a critical capability for incident responders and threat researchers.
Enhanced Threat Indicator Classification for Faster Triage
MetaDefender Aether 2.3.0 features a revamped classification engine for behavioral threat indicators, introducing:
- Improved translation support for multilingual environments
- Refined risk categorization and severity scoring
- Advanced filtering to prioritize high-risk events
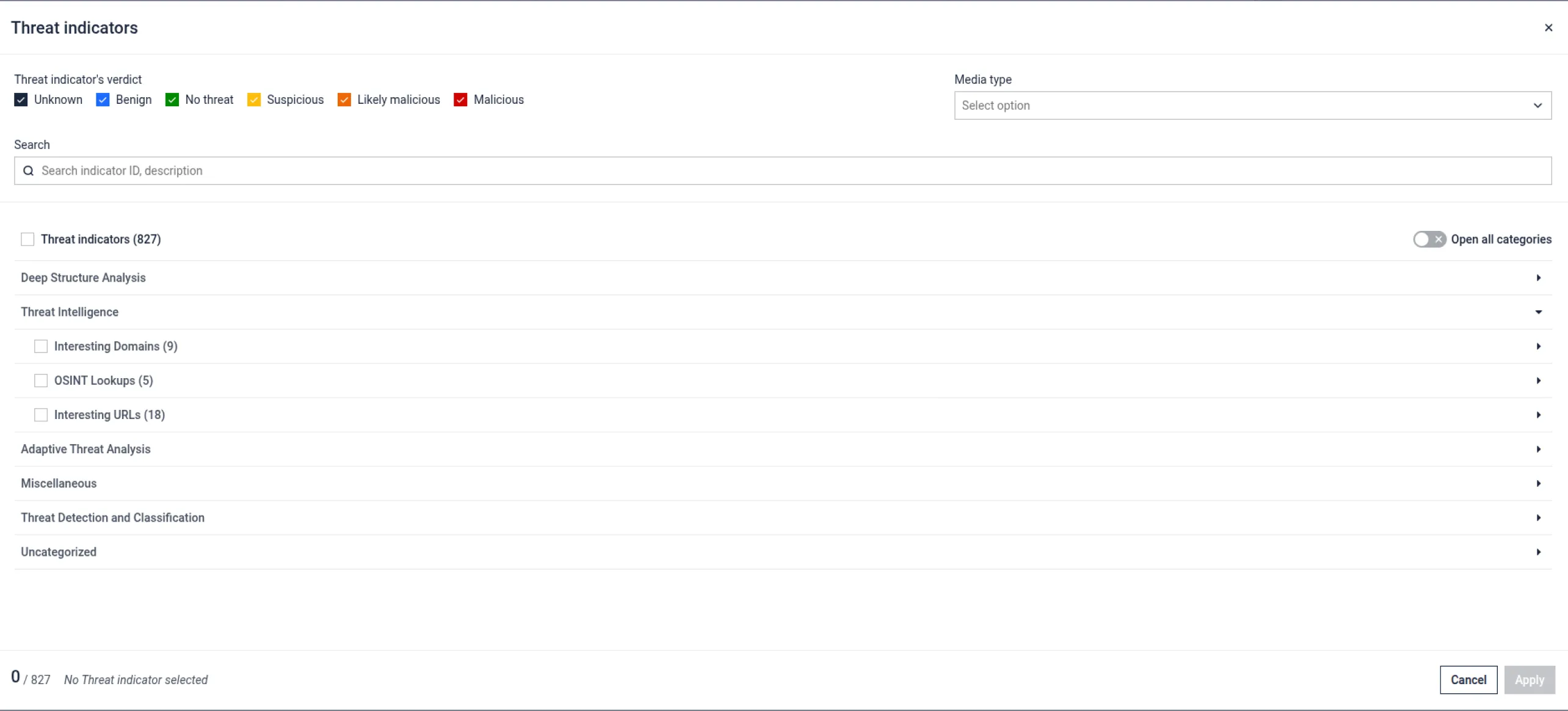
The above listed upgrades empowers analysts to focus on the most critical threats detected during dynamic execution, resulting in reduced time-to-insight.
Extended Detection for Emerging Malware Threats
With this release, MetaDefender Aether expands its detection capabilities for new malware families, evasive loaders, and advanced persistence mechanisms. Key additions include:
- Configuration extractors for XWorm, Stealc, and updated Lumma Stealer variants
- Detection enhancements for PrivateLoader, Millennium RAT, and similar advanced malware
- New signatures for API call obfuscation via hashing, and short-lived certificate abuse
This ensures broader coverage of today’s most active malware campaigns, including those leveraging anti-analysis and sandbox evasion techniques.
Improved Web Threat and Brand Detection
Phishing and browser-based threats are evolving, so too is our Detection Stack.
- A new HTML URL parser enables deep inspection of embedded URLs in emails and malicious documents
- The phishing detection engine has been renamed to Brand Detection to better reflect its expanded focus
- OCR support has been added to catch visually spoofed brand content
- Support for high-risk impersonations now includes Marvell and other global brands
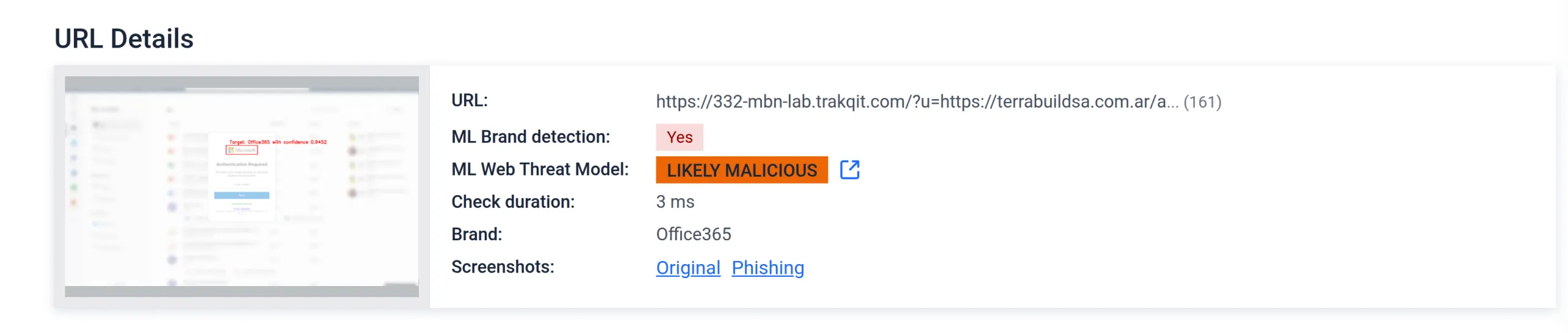
Together, these improvements enhance MetaDefender’s precision in identifying phishing campaigns, credential theft attempts, and malicious redirects that bypass traditional defenses.
Seamless Microsoft Entra (Azure AD) Integration
Organizations using Microsoft Entra ID (formerly Azure AD) can now benefit from automatic user provisioning and group mapping. This simplifies identity and access management while maintaining strong control across enterprise environments.
This integration supports secure, scalable adoption across large organizations and MSSPs.
Platform and Workflow Enhancements
MetaDefender Aether 2.3.0 also introduces multiple usability, performance, and compatibility improvements:
- Report Deletion Controls: End users can now delete their own analysis reports; administrators retain system-wide privileges
- YARA Rule Management Interface: View, filter, and tag both system-generated and custom YARA rules via a centralized interface
- Ubuntu 24.04 LTS Support: Sandbox is now compatible with Ubuntu 24.04 (CIS hardening to follow in a future update)
- Optimized string extraction for improved UTF-8 handling and efficiency in binary transforms
- Enhanced Dropbox malware extraction for analyzing second-stage payloads from phishing links
Malware Lab Enhancements for Precision Detection
MetaDefender Aether 2.3.0 further enhances capabilities with:
- Script-Based Threat Detection: Improved visibility into obfuscated JavaScript, VBA, and PowerShell
- Base64 File Extraction: Support for embedded and reverse-encoded artifacts
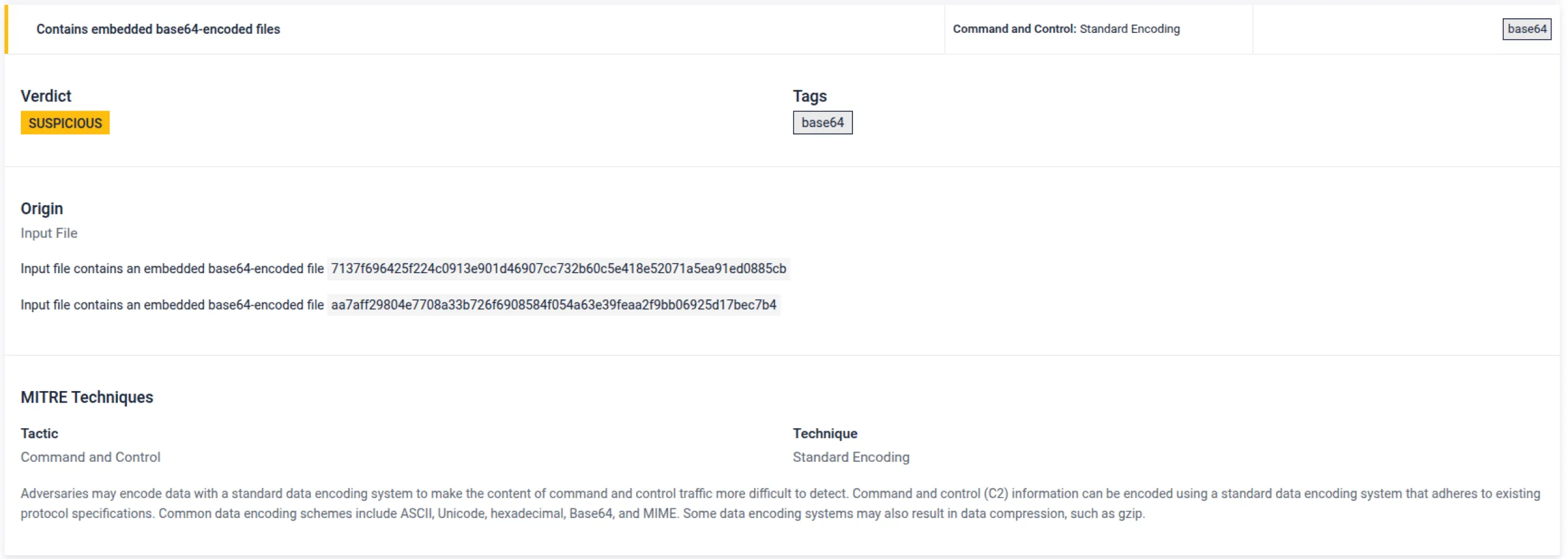
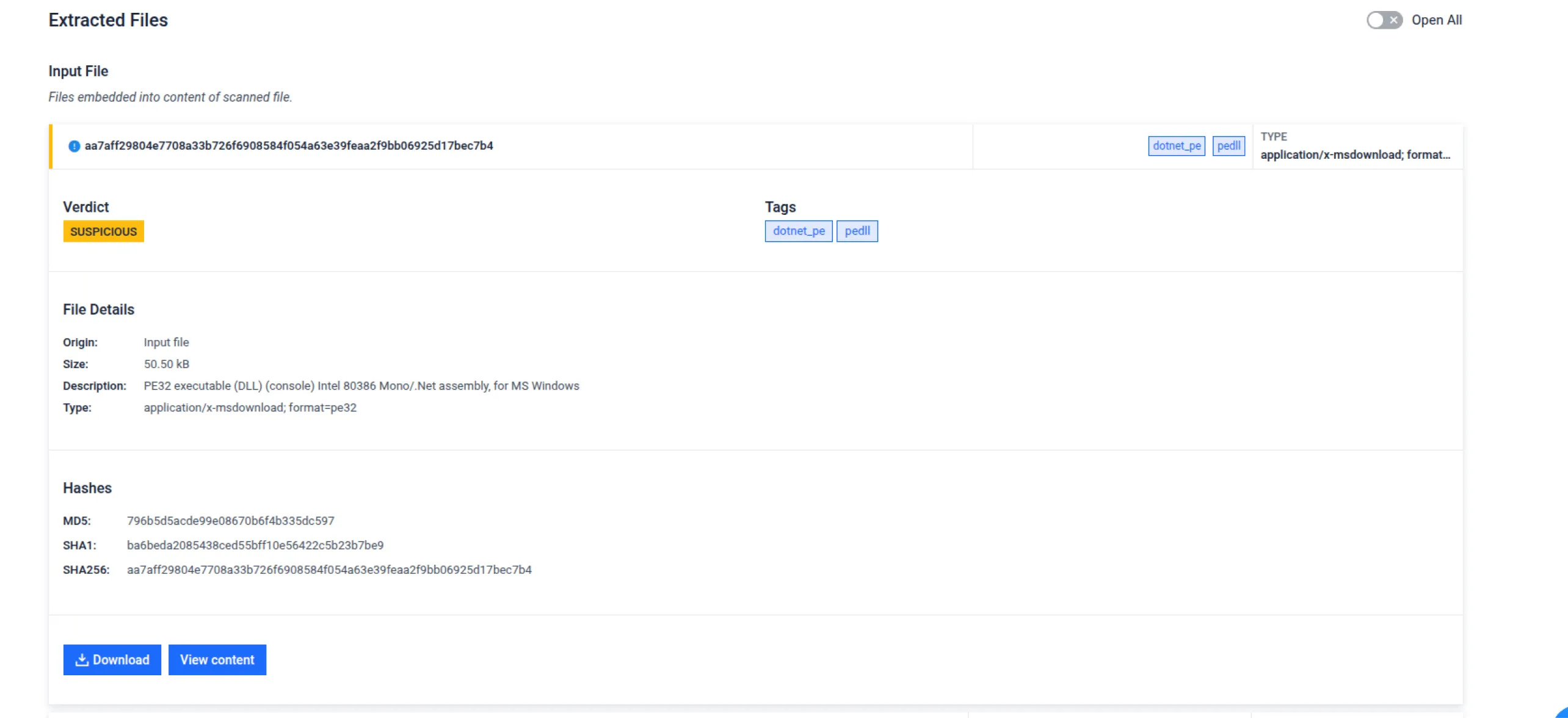
- Disassembly Precision: Improved instruction handling and string annotations for more reliable disassembly output
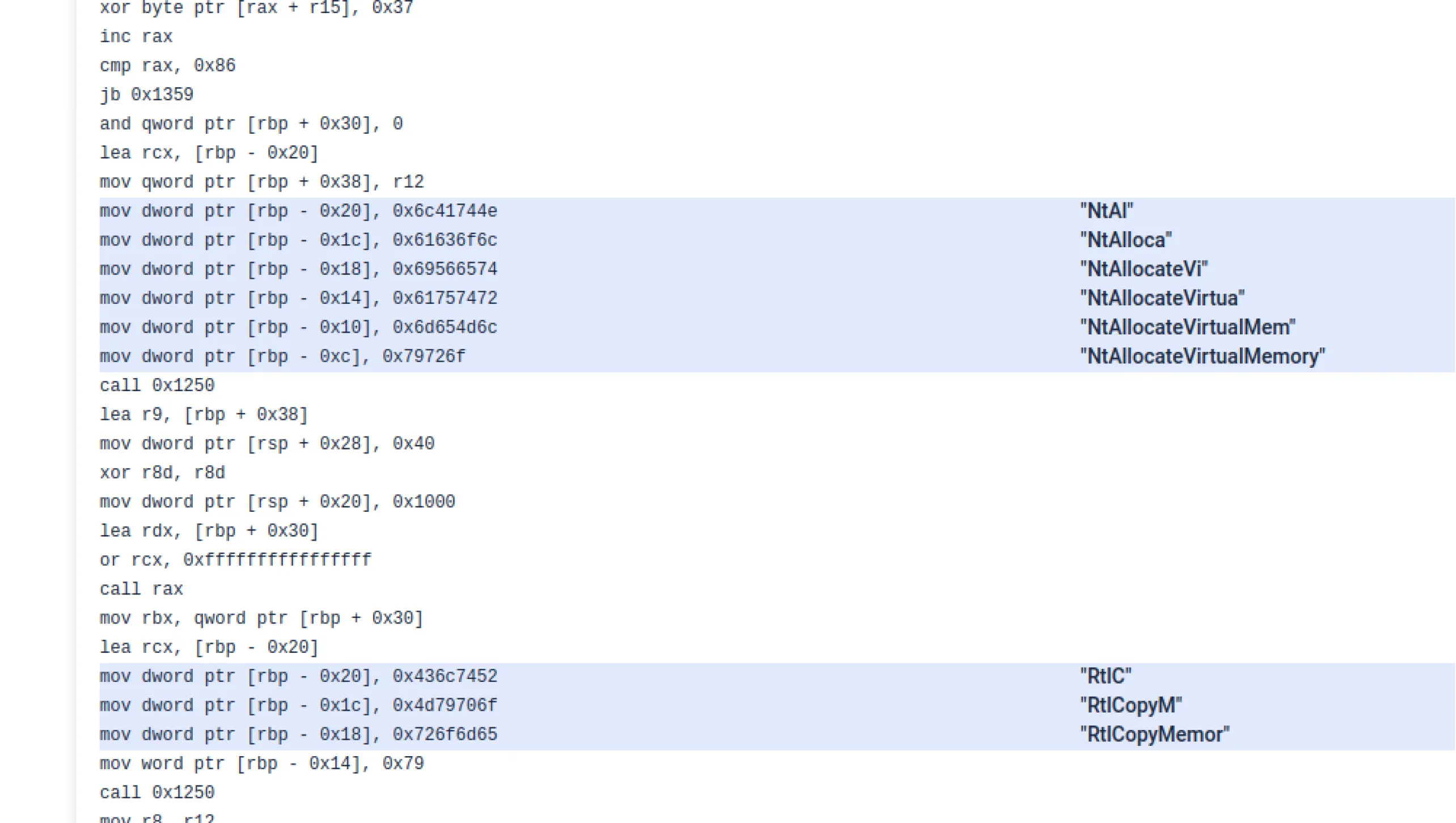
- PE Structure Analysis: 40+ new signatures to detect structural anomalies in PE headers
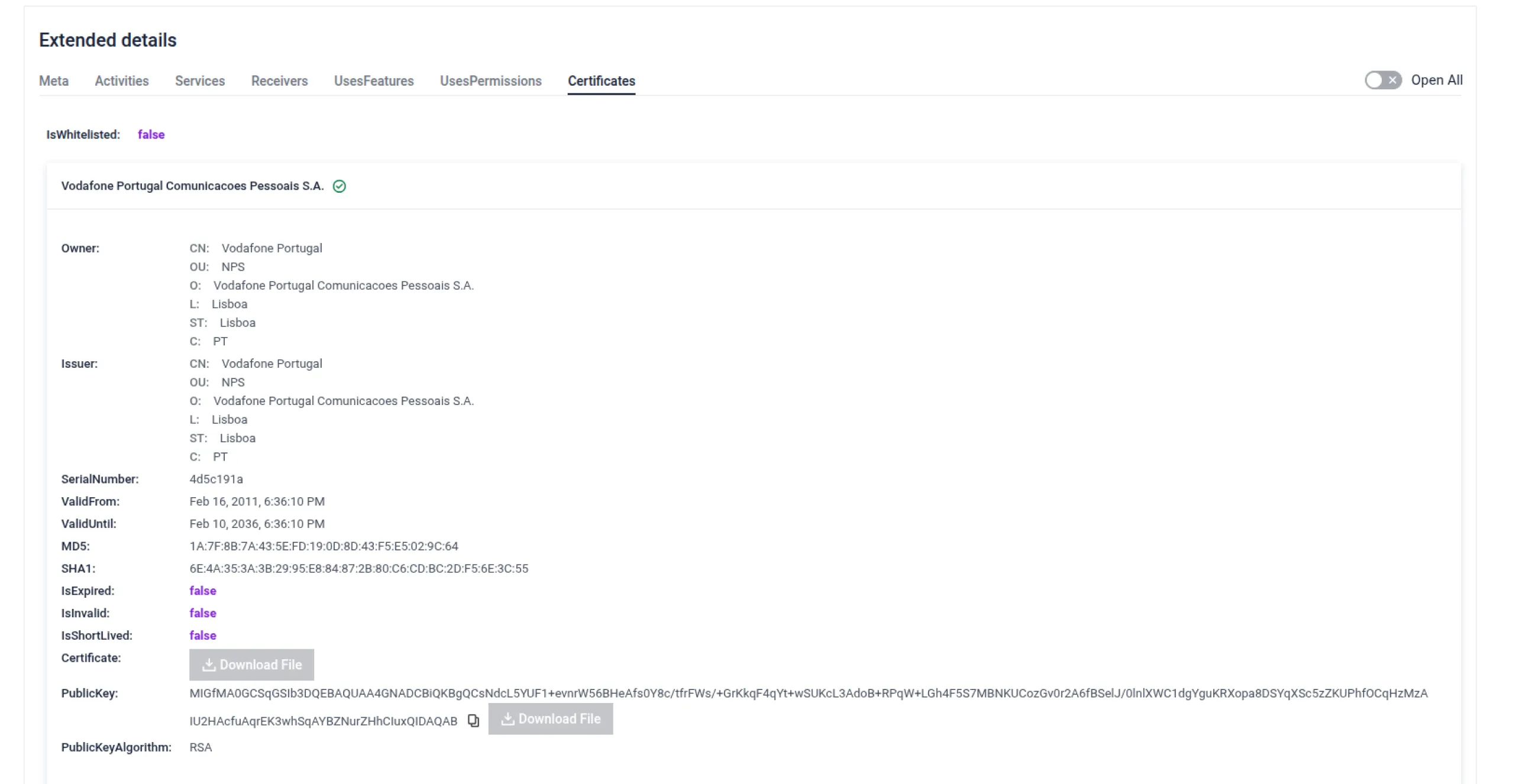
- APK Certificate Validation: Ensures APK integrity and reduces false positives in mobile threat detection
Resolved Issues and Stability Improvements
- Corrected internal server errors and user validation issues during report loading
- Fixed URL redirection loops and file type misidentification
- Addressed certificate validation edge cases to improve detection accuracy
- Eliminated zombie processes caused by sandboxed URL rendering
- Improved memory and API resource handling for enhanced system performance
A Strategic Update for Proactive Security Teams
MetaDefender Aether 2.3.0 empowers security operations with faster analysis, smarter detection, and deeper visibility into sophisticated threats. Whether deployed in enterprise environments or integrated into SOC workflows, this update reinforces OPSWAT’s mission to protect critical infrastructure through comprehensive, AI-enhanced malware analysis.
Get Started with MetaDefender Aether 2.3.0
To learn more, request a demo, or speak with an OPSWAT expert, visit: https://www.opswat.com/products/metadefender-sandbox
Stay ahead of the threat curve.

